Carding
Professional
- Messages
- 2,871
- Reaction score
- 2,397
- Points
- 113

Tails isn't the only Linux distribution that puts data protection first. But, in my opinion, this is by far the best choice for a person who wants to preserve the confidentiality of correspondence, the security of personal data and the safety of important information from prying eyes. And since I started talking about the principles of data protection in Tails, it will be useful to list them.
- Maintaining confidentiality of information. Here everything is simple, we need to protect our information from outsiders. To do this, we will encrypt everything, use cryptographic algorithms and long keys. Some of them will even be encrypted several times. Nothing should be stored in clear text, nothing is transmitted in clear text.
- Hiding the presence of information (steganographic protection). We need to hide the very fact of storing or transmitting data. We will use hidden cryptographic containers and fill free disk space with random data that is heuristically indistinguishable from encrypted data.
- Hiding the destination of information transmission. Sometimes it may be necessary to hide not only the information itself, but also the recipient from prying eyes. Multi-layer encryption and onion routing will help us do this.
- Plausible deniability. It may be necessary to direct persistent curious people (for example, during a search) to a false trail. On top of hidden containers with important data, we will create false, but very plausible encrypted sections in which we will store a cookbook and pictures with cats from the Internet.
- The ability to refuse to transfer information, revoke your digital signatures, and so on. The OTR Protocol and the use of HMAC instead of EDS will help us do this.
- Working on a computer without traces. Anything that may remain in RAM, on the hard disk, or even in the memory of the video card must be thoroughly cleaned. Everything important should be stored only on a securely encrypted, hidden and protected medium, and the risk of leaks should be minimized.
Installation
To install Tails, we will need two flash drives. Why two? To understand what recursion is, you must first understand what recursion is. And Tails can only be installed using Tails. Download the ISO from the official website tails.boum.org. We recommend checking the image immediately using OpenPGP. detailed instructions on how to do this are available on the site. The downloaded image is recorded on the first, intermediate flash drive using Universal Usb Installer. After that, you can turn off the computer and boot from the flash drive. When the OS boots up, you will need to insert the second (main) flash drive and select Applications → Tails → Tails Installer Install by Cloning.
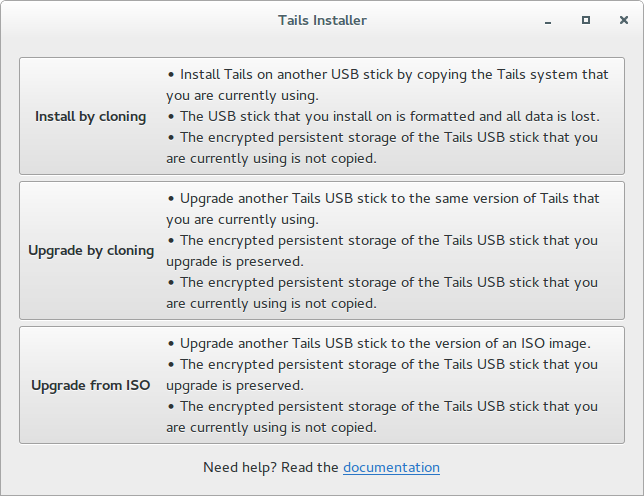
If everything worked out, then the system is ready to work.
Getting started
After booting from a working flash drive, we will need to create a permanent (persistent) protected partition, a kind of"hard disk on a flash drive". This is done via Application - > Tails - > Configure Persistence.
We restart the computer and select Use Persistence and More Options on the boot screen, then enter the password for our storage.
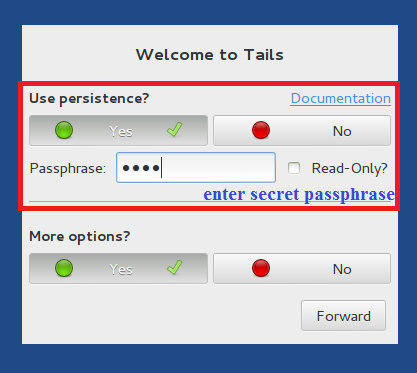
Select a region from the menu at the bottom of the screen. This is important because the tor input nodes depend on the region. You should experiment here. In my case, Denmark was the best choice.
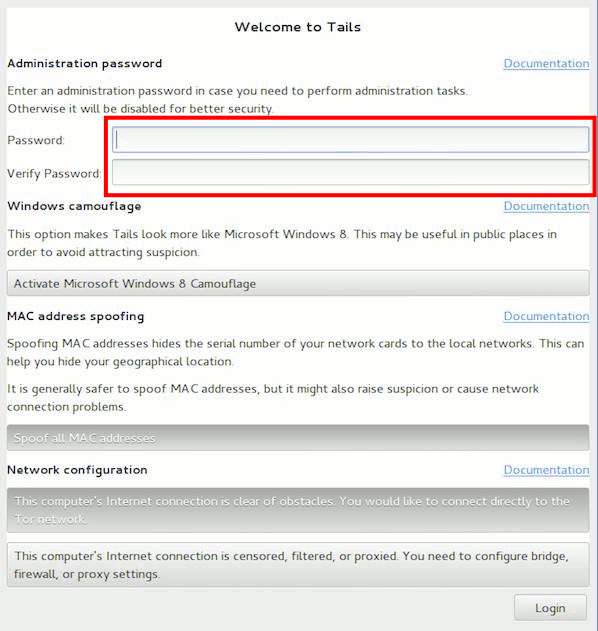
In the advanced settings menu, set a password for programs that need administrator rights. You can put any one, it works within the session and does not affect anything else.
Keep in mind that the download takes some time, and then Tails will connect to Tor for a few more minutes. You can track the process by clicking on the Onion Circuits icon in the upper-right corner of the screen.
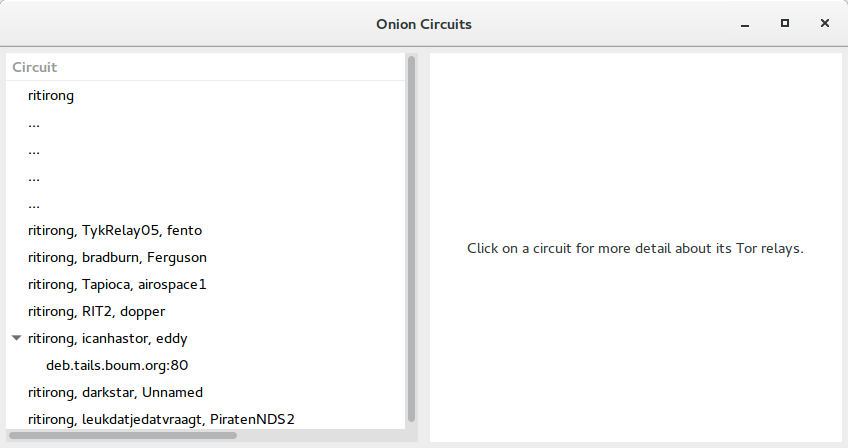
After some time, Tails will inform you about the successful connection to Tor. By default, the network is configured so that all traffic will pass through it. Now you can download everything we need to work with.
Additional SOFTWARE, saving files and settings
By default, Tails is not designed to save installed SOFTWARE, settings, or files after the computer is turned off. However, the creators have provided for the ability to store some data in a persistent partition. You can configure what will be stored in settings → Persistent.
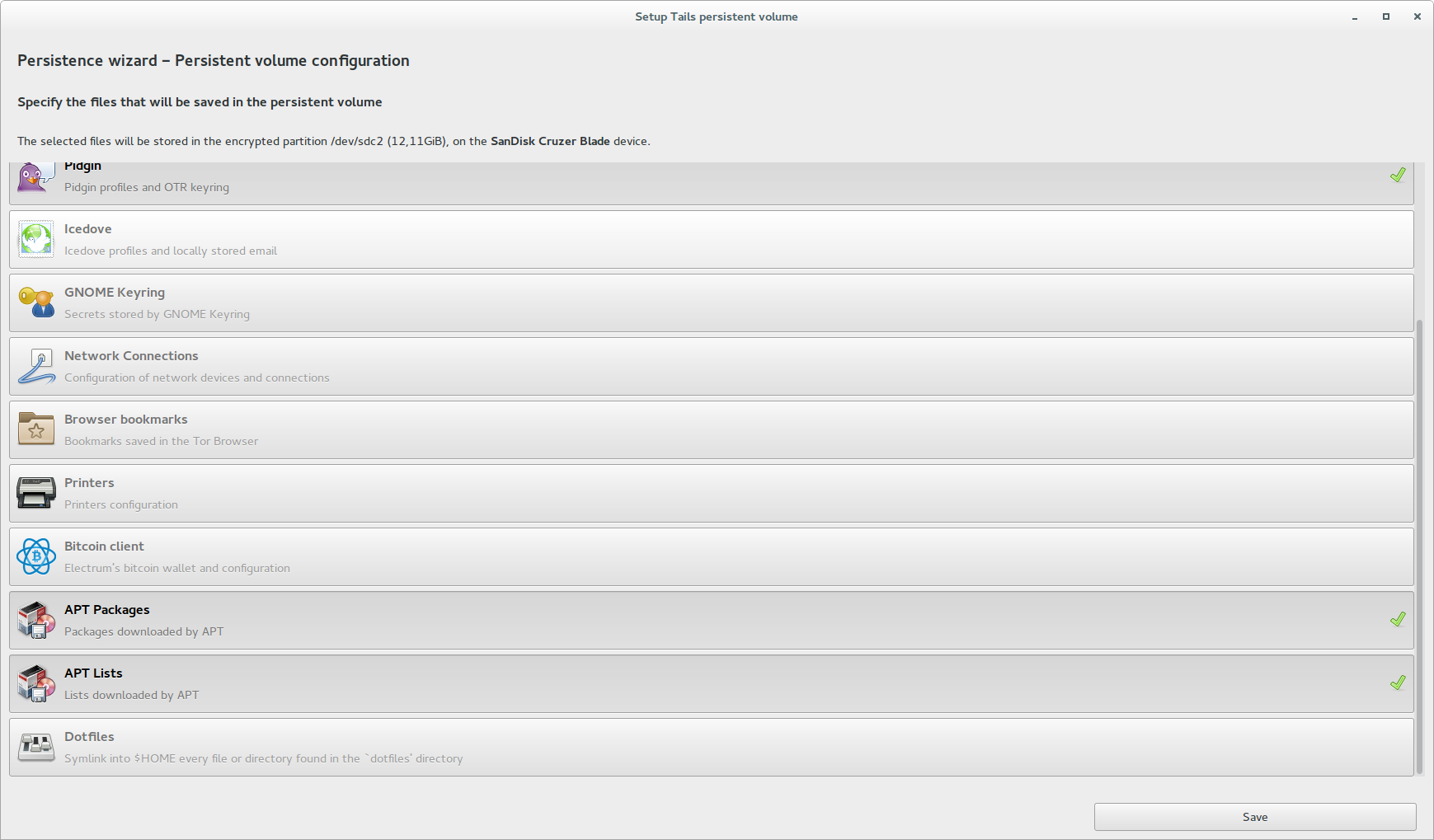
Most of the menu items are obvious, so I'll focus on the last three. The second and third from the end are responsible for storing APT packages. Tails is based on Debian, so most of the SOFTWARE we need can be installed using apt-get. Although the programs themselves will not be saved when the computer is turned off, APT packages will remain in the persistent section with the appropriate settings. This allows you to deploy all the necessary SOFTWARE during the system boot process.
The last Dotfiles menu item allows you to create a folder with files in the persistent section, links to which will be created in the tails home folder when downloading. It looks like this.
Here is an example of the structure of files in a persistent partition.
Code:
/live/persistence/TailsData_unlocked/dotfiles
├── file_a
├── folder
│ ├── file_b
│ └── subfolder
│ └── file_c
└── emptyfolderIn this scenario, the home folder will have the following link structure::
Code:
/home/amnesia
├── file_a → /live/persistence/TailsData_unlocked/dotfiles/file_a
└── folder
├── file_b → /live/persistence/TailsData_unlocked/dotfiles/folder/file_b
└── subfolder
└── file_c → /live/persistence/TailsData_unlocked/dotfiles/folder/subfolder/file_cProtecting data, discarding the tail
Our persistent partition itself is already encrypted. However, it has a significant drawback: it does not provide a plausible denial of the presence of encrypted data. To ensure a plausible deniability, I will offer a solution that differs from the recommendations of the creators of Tails. What you should do is up to you.
The creators of Tails recommend using cryptsetup, which is based on LUKS. This program allows you to create hidden sections, but this section is not completely hidden. As far as I know, it is possible to detect the header of a hidden section, which allows you to determine its presence.
Such a hidden section personally does not suit me. So I decided to use the good old TrueCrypt version 7.1 a. The header of the hidden TrueCrypt partition is indistinguishable from random data, and as far as I know, it is impossible to detect it. The binary file of the TrueCrypt program is best stored here, in the persistent section.
I will not describe in detail the process of creating a double cryptographic container, but I will note only an important nuance. Since the hidden TrueCrypt partition is truly hidden, even the program itself doesn't know it exists until you enter the correct password. Because of this, when writing files to a false partition, the hidden partition may be corrupted. To prevent this from happening, when mounting a false partition, select Mount Options → Protect hidden volume when mounting outer volume to write pictures of cats to it.
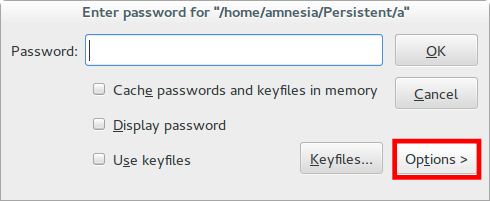
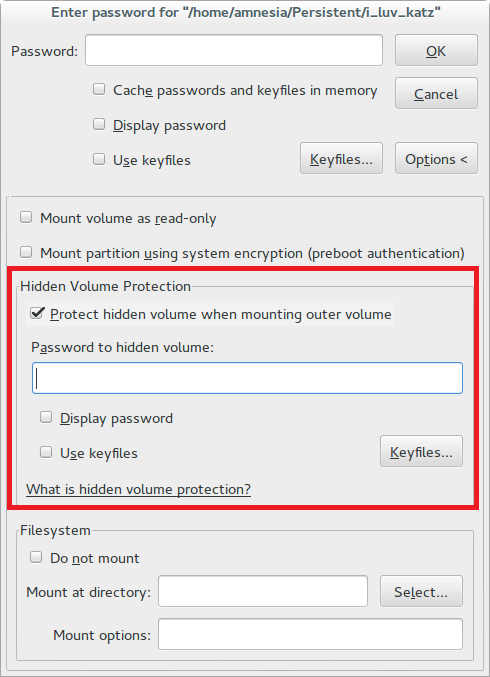
Like a lizard that throws back its tail in case of danger, we can now enter the password for the fake section if necessary and show everyone photos of seals instead of confidential information.
Communication
Now that we have secured our information, we can start transmitting it, that is, communicating. Let's start with Pidgin. It works great as an IRC client, and Tails has also been enhanced a bit. The OS includes Pidgin with the OTR Protocol plugin installed. That's what we're most interested in. Avoiding complex mathematics, we can say that this Protocol provides secure data transmission with the possibility of denial, that is, it is impossible to prove that a specific message was written by a specific person.
Before you can start communicating with someone over the OTR Protocol, you need to connect to the IRC server. At the same time, it is very important to make sure that SSL is used. Tor encrypts traffic when it is transmitted between nodes, but if you do not use SSL, your traffic will be transmitted in clear text to the tor input node and from the output node to the destination. Some Tor nodes are banned from IRC servers, so you may need to restart Tor. You can do this using the command /etc/init.d/tor restart.
After the connection to the server is established, select Buddies → New Instant Message.
In the dialog box that opens, select Not Private → Start Private Conversation.
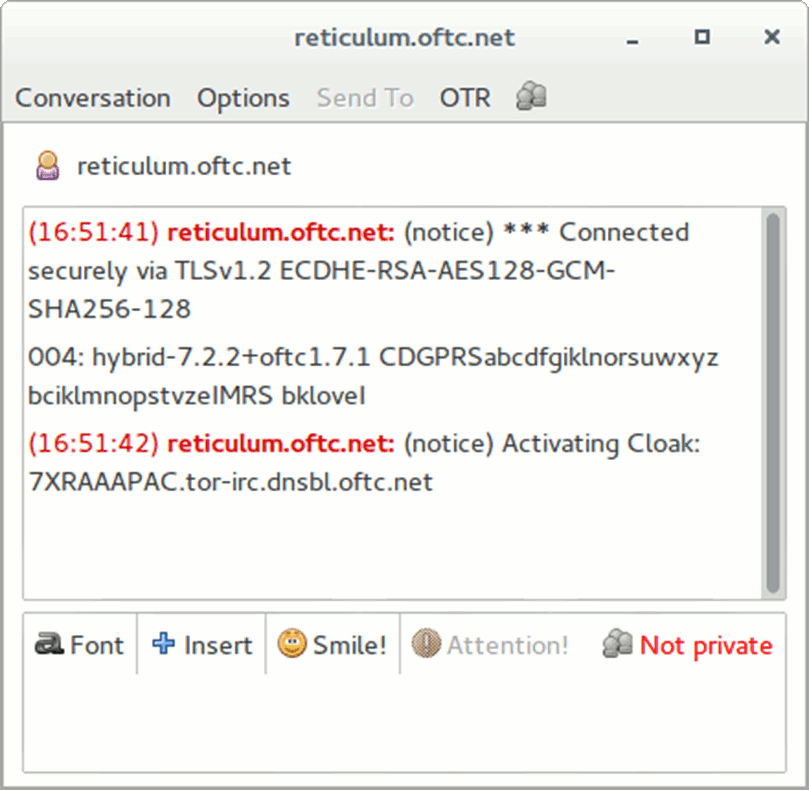
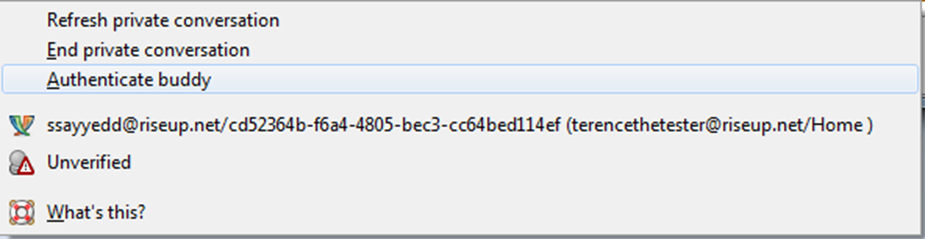
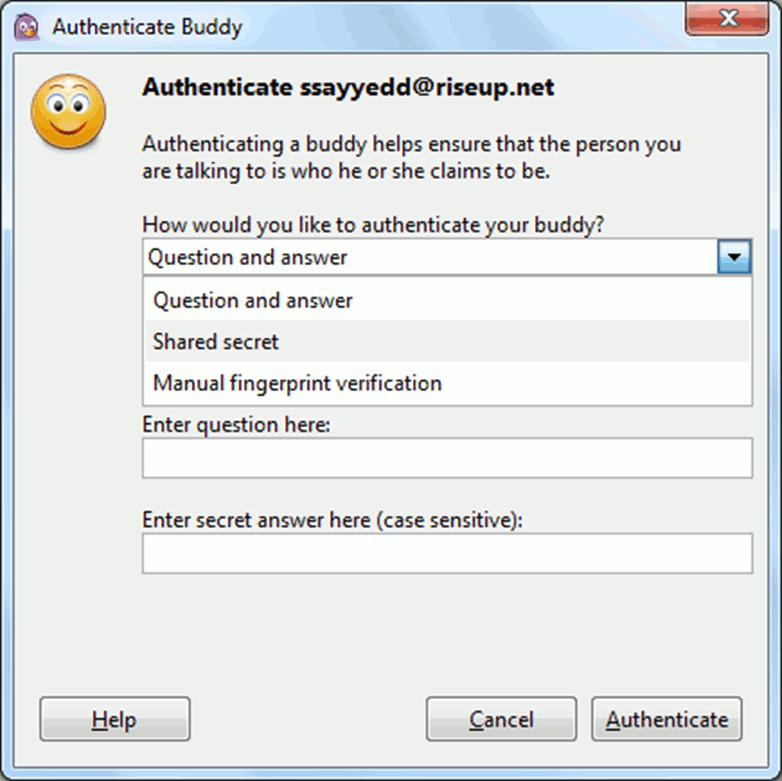
You will be offered three options for authentication: enter the answer to the secret question that you discussed with the interlocutor in advance (in this case, you must enter the same answer, spaces and case are considered); enter a common "secret" phrase; check fingerprint-this is a forty-character sequence that identifies the OTR user.
Now you can correspond using OTR. But what about voice communication? Here, alas, not everything is smooth. Since Tails routes all traffic through Tor, there are a number of problems for voice communication. First, most VoIP programs use UDP, while only TCP packets can be transmitted over Tor. Secondly, Tor does not differ in speed and packets sometimes arrive with a strong delay. So there may be delays and disconnections.
However, there is OnionPhone, a special plugin for TorChat. Mumble also does a good job, although this option is less secure. In order for Mumble to work via Tor, you need to run It with the commandtorify mumble, and also select Force TCP in the network settings of the program.
Mail in Tails can be used in the same way as in other operating systems. The standard build includes the Icedove email client. its settings and keys can be stored in the persistent section. An important caveat to keep in mind when sending emails is that subject headers are not encrypted. This is not a bug, but a feature of the Protocol implementation that you just need to know about. In addition, we recommend encrypting files sent by email.
Total
I've only described some of the features of Tails, but the basic build contains an impressive set of additional programs that you'll have to learn on your own. I recommend, for example, to look at the software for erasing file metadata - it will help you protect yourself even better.
xakep.ru
