Friend
Professional
- Messages
- 2,675
- Reaction score
- 1,052
- Points
- 113
Hackers servers in the US, UK and Germany were confiscated.
The FBI eliminated servers and sites associated with the activities of the RADAR/DISPOSESSOR ransomware group. The operation was carried out jointly with partners from the UK and Germany.
As a result, law enforcement agencies confiscated servers and domains that were used by hackers to carry out attacks. In particular, 3 servers in the US, 3 servers in the UK, 18 servers in Germany, as well as several domains (radar[.]tld, disposessor[.]com, cybernewsint[.] com and others). The sites served both to coordinate attacks and to create false news and video platforms.
Since August 2023, the DISPOSESSOR group, led by a cybercriminal named Brain, has attacked small and medium-sized businesses in various countries, including the United States, Argentina, Australia, Germany and others. A total of 43 companies were affected. Hackers penetrated networks through vulnerabilities, weak passwords and lack of multi-factor authentication, stole data and encrypted victims devices, depriving them of access to information.
After the attack, if the company did not get in touch, the criminals themselves contacted employees via email or calls, threatening to publish the stolen data. The attackers also sent links to the platforms where the stolen files were uploaded, increasing the pressure on the victims. Instead of screenshots with the stolen information, hackers attached small videos to the leak page, where they clearly demonstrate directories with stolen data.
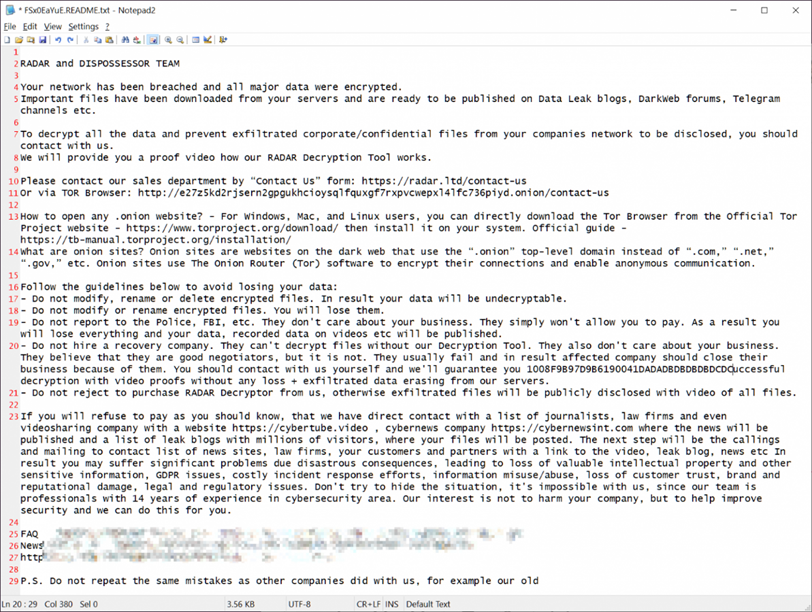
RADAR/ DISPOSESSOR Ransom
The FBI urged anyone affected by the actions of DISPOSESSOR to contact the Internet Crime Complaint Center (IC3) or the FBI's 1-800-CALL hotline.
Previously, the Disposessor group acted as a ransomware group, spreading stolen data stolen during attacks by other ransomware programs, such as LockBit. Subsequently, hackers resold the data on various underground forums. In June 2024, criminals began using the leaked LockBit 3.0 cryptographer, which significantly increased the scale of their attacks. Some researchers believe that the group was created by former LockBit members, which was confirmed by hackers themselves, but it is impossible to verify the authenticity of their words.
Source
The FBI eliminated servers and sites associated with the activities of the RADAR/DISPOSESSOR ransomware group. The operation was carried out jointly with partners from the UK and Germany.
As a result, law enforcement agencies confiscated servers and domains that were used by hackers to carry out attacks. In particular, 3 servers in the US, 3 servers in the UK, 18 servers in Germany, as well as several domains (radar[.]tld, disposessor[.]com, cybernewsint[.] com and others). The sites served both to coordinate attacks and to create false news and video platforms.
Since August 2023, the DISPOSESSOR group, led by a cybercriminal named Brain, has attacked small and medium-sized businesses in various countries, including the United States, Argentina, Australia, Germany and others. A total of 43 companies were affected. Hackers penetrated networks through vulnerabilities, weak passwords and lack of multi-factor authentication, stole data and encrypted victims devices, depriving them of access to information.
After the attack, if the company did not get in touch, the criminals themselves contacted employees via email or calls, threatening to publish the stolen data. The attackers also sent links to the platforms where the stolen files were uploaded, increasing the pressure on the victims. Instead of screenshots with the stolen information, hackers attached small videos to the leak page, where they clearly demonstrate directories with stolen data.

RADAR/ DISPOSESSOR Ransom
The FBI urged anyone affected by the actions of DISPOSESSOR to contact the Internet Crime Complaint Center (IC3) or the FBI's 1-800-CALL hotline.
Previously, the Disposessor group acted as a ransomware group, spreading stolen data stolen during attacks by other ransomware programs, such as LockBit. Subsequently, hackers resold the data on various underground forums. In June 2024, criminals began using the leaked LockBit 3.0 cryptographer, which significantly increased the scale of their attacks. Some researchers believe that the group was created by former LockBit members, which was confirmed by hackers themselves, but it is impossible to verify the authenticity of their words.
Source
