Man
Professional
- Messages
- 3,223
- Reaction score
- 1,150
- Points
- 113
Key members of the criminal group were detained in Europe.
After a successful operation to destroy the infrastructure of the well-known hacker group LockBit in February of this year, dubbed "LockBit Leak Week", the authorities continue to fight cybercriminals. Recently, four more suspects associated with the now-collapsed LockBit ransomware empire were arrested.
The first arrest was made by the French gendarmerie. The suspected developer of LockBit was detained while on vacation in a country that has an extradition agreement with France. The identity of the arrested person is not disclosed in accordance with French law. The country where the detention took place is also not indicated. However, a message appeared on the hacked LockBit blog that the detainee was facing serious charges in France in connection with the case against the organized crime group LockBit.
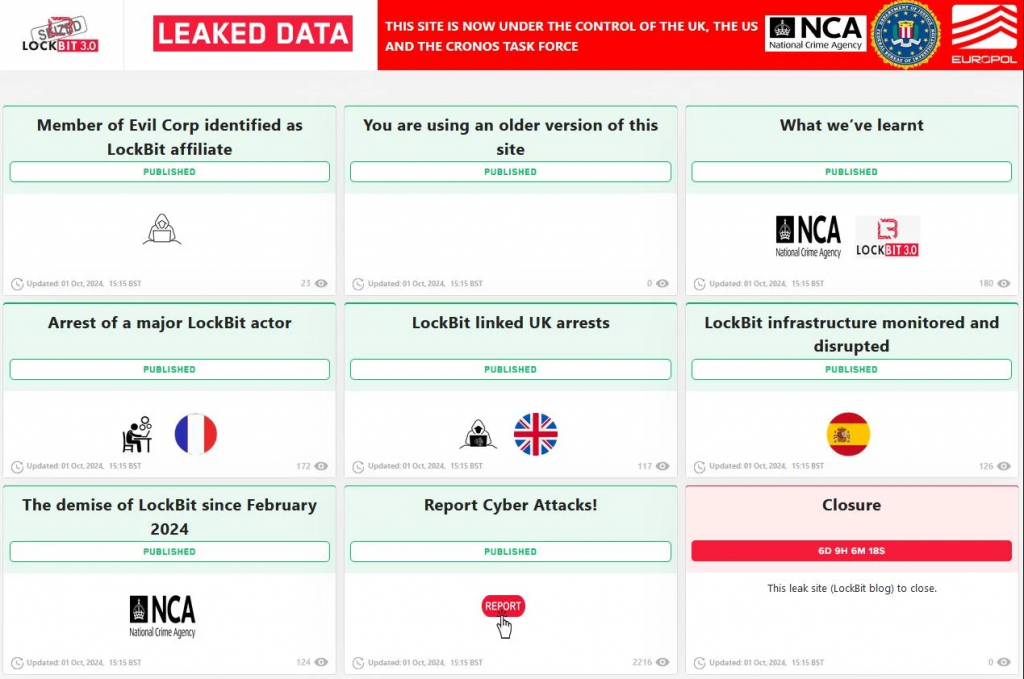
The leaked blog LockBit, which is under the control of Operation Kronos, is back up and running to report four arrests of alleged gang accomplices
The arrest took place in August, the same month two more people were detained in the UK. One is suspected of having ties to an affiliate of LockBit, the other of money laundering. Britain's National Crime Agency (NCA) did not disclose the identities of the suspects, but said the data to identify them came from an analysis of information seized during a February operation against the group.
The Spanish Civil Guard also took part in the operation, arresting at Madrid airport a man believed to be a "key suspect." The detainee is believed to be the owner of a so-called "bulletproof" hosting service, one of the key elements of the infrastructure of cybercriminals like LockBit.
During Operation Kronos, a global law enforcement collaboration to dismantle the LockBit group, nine servers belonging to the criminals' infrastructure were accessed and seized. The obtained information is currently being analyzed to go after the main members and affiliates of the ransomware group.
While these arrests are a significant success in the fight against LockBit, they represent only a small part of the group's overall membership. Very few arrests have been made in the entire history of LockBit, and many suspects still remain at large.
Recent law enforcement successes include the arrest of a father and son in Ukraine suspected of links to LockBit, as well as the detention in the United States of 20-year-old Ruslan Magomedovich Astamirov, suspected of carrying out at least five attacks using the LockBit ransomware.
One of the most significant discoveries of Operation Kronos was the confirmation of suspicions that LockBit retained stolen data even after the ransom was paid by the victims. An analysis of the source code of LockBit's tools showed that they were designed in such a way that data is never completely deleted.
In the control panel for LockBit affiliates, there was an option to delete the victim's data. However, the researchers found that the "Yes" button in the deletion confirmation window was actually sending a request to LockBit's headquarters, which could approve or deny the request to delete the victim's data.
Even if the request was approved, each file had to be deleted manually by the LockBit administrator by sequentially entering the ID of each folder. Only suspect Dmitry Khoroshev had the ability to actually delete the data, and the affiliate could never know if the data was actually destroyed.
Moreover, the authorities claim that LockBit has not deleted any data since 2022. This discovery once again confirms that paying a ransom to cybercriminals does not guarantee the safety of data stolen during an attack.
Source
After a successful operation to destroy the infrastructure of the well-known hacker group LockBit in February of this year, dubbed "LockBit Leak Week", the authorities continue to fight cybercriminals. Recently, four more suspects associated with the now-collapsed LockBit ransomware empire were arrested.
The first arrest was made by the French gendarmerie. The suspected developer of LockBit was detained while on vacation in a country that has an extradition agreement with France. The identity of the arrested person is not disclosed in accordance with French law. The country where the detention took place is also not indicated. However, a message appeared on the hacked LockBit blog that the detainee was facing serious charges in France in connection with the case against the organized crime group LockBit.

The leaked blog LockBit, which is under the control of Operation Kronos, is back up and running to report four arrests of alleged gang accomplices
The arrest took place in August, the same month two more people were detained in the UK. One is suspected of having ties to an affiliate of LockBit, the other of money laundering. Britain's National Crime Agency (NCA) did not disclose the identities of the suspects, but said the data to identify them came from an analysis of information seized during a February operation against the group.
The Spanish Civil Guard also took part in the operation, arresting at Madrid airport a man believed to be a "key suspect." The detainee is believed to be the owner of a so-called "bulletproof" hosting service, one of the key elements of the infrastructure of cybercriminals like LockBit.
During Operation Kronos, a global law enforcement collaboration to dismantle the LockBit group, nine servers belonging to the criminals' infrastructure were accessed and seized. The obtained information is currently being analyzed to go after the main members and affiliates of the ransomware group.
While these arrests are a significant success in the fight against LockBit, they represent only a small part of the group's overall membership. Very few arrests have been made in the entire history of LockBit, and many suspects still remain at large.
Recent law enforcement successes include the arrest of a father and son in Ukraine suspected of links to LockBit, as well as the detention in the United States of 20-year-old Ruslan Magomedovich Astamirov, suspected of carrying out at least five attacks using the LockBit ransomware.
One of the most significant discoveries of Operation Kronos was the confirmation of suspicions that LockBit retained stolen data even after the ransom was paid by the victims. An analysis of the source code of LockBit's tools showed that they were designed in such a way that data is never completely deleted.
In the control panel for LockBit affiliates, there was an option to delete the victim's data. However, the researchers found that the "Yes" button in the deletion confirmation window was actually sending a request to LockBit's headquarters, which could approve or deny the request to delete the victim's data.
Even if the request was approved, each file had to be deleted manually by the LockBit administrator by sequentially entering the ID of each folder. Only suspect Dmitry Khoroshev had the ability to actually delete the data, and the affiliate could never know if the data was actually destroyed.
Moreover, the authorities claim that LockBit has not deleted any data since 2022. This discovery once again confirms that paying a ransom to cybercriminals does not guarantee the safety of data stolen during an attack.
Source
