Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,494
- Points
- 113
Leaked last year, the LockBit 3.0 constructor served as the start of a real ransomware cyberpandemy.
Kaspersky Lab recently revealed cases of its customers being infected with LockBit ransomware with significant changes in the ransom requirements.
Instead of the usual ransom text, the attackers used a new message on behalf of the previously unknown group "NATIONAL HAZARD AGENCY". It immediately indicated a fixed amount for decrypting data of $ 3 million, as well as contacts for communicating with intruders via the Tox protocol or email.
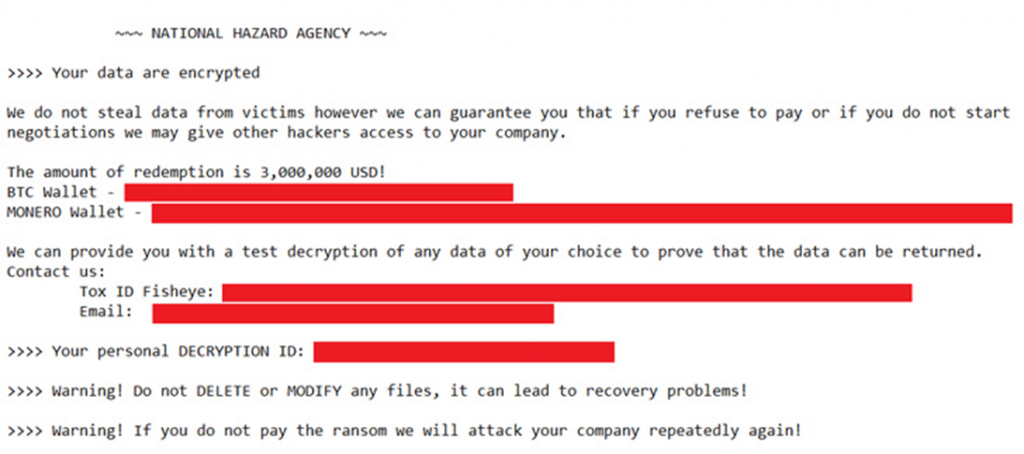
Ransomware Ransom Note from NATIONAL HAZARD AGENCY
Many other cybercriminals who took advantage of last year's LockBit 3.0 constructor leak do the same, such as hackers Bl00dy and Buhti.
Experts have already found 396 different LockBit samples, of which 312 were created using the merged builder. In 77 cases, the ransomware note did not even mention the LockBit group itself.
Many modifications mainly relied on the standard configuration of the builder. Only occasionally did hackers change some minor parameters, which indicates that most of the attackers were in a hurry or lazy.
A leak of malware creation tools is always dangerous, because it allows cybercriminals of any level to create and distribute their own versions of known threats.
Companies should be especially vigilant after such incidents and pay close attention to protecting corporate networks, timely software updates, and data backups.
Kaspersky Lab recently revealed cases of its customers being infected with LockBit ransomware with significant changes in the ransom requirements.
Instead of the usual ransom text, the attackers used a new message on behalf of the previously unknown group "NATIONAL HAZARD AGENCY". It immediately indicated a fixed amount for decrypting data of $ 3 million, as well as contacts for communicating with intruders via the Tox protocol or email.

Ransomware Ransom Note from NATIONAL HAZARD AGENCY
Many other cybercriminals who took advantage of last year's LockBit 3.0 constructor leak do the same, such as hackers Bl00dy and Buhti.
Experts have already found 396 different LockBit samples, of which 312 were created using the merged builder. In 77 cases, the ransomware note did not even mention the LockBit group itself.
Many modifications mainly relied on the standard configuration of the builder. Only occasionally did hackers change some minor parameters, which indicates that most of the attackers were in a hurry or lazy.
A leak of malware creation tools is always dangerous, because it allows cybercriminals of any level to create and distribute their own versions of known threats.
Companies should be especially vigilant after such incidents and pay close attention to protecting corporate networks, timely software updates, and data backups.

