CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 724
- Points
- 113
A new way to compromise the popular OS is now available to every hacker.
Before we could tell you about the "Looney Tunables" vulnerability, which is tracked under the identifier CVE-2023-4911 , a PoC exploit has already appeared on the Internet, which allows you to successfully exploit this vulnerability in a real attack. Moreover, the complexity of using the vulnerability is extremely low — even a novice hacker can handle it.
Looney Tunables allows attackers to gain superuser rights on Linux systems by exploiting the buffer overflow flaw. The security flaw affects standard installations of Debian 12 and 13, Ubuntu 22.04 and 23.04, and Fedora 37 and 38.
Cybercriminals can exploit the vulnerability by using the maliciously created environment variable "GLIBC_TUNABLES", processed by the dynamic loader "ld.so", to achieve execution of arbitrary code with root rights when running binaries with SUID permission.
One of the PoC exploits, which has already been confirmed by vulnerability expert Will Dormann, was published by independent security researcher Peter Geissler under the pseudonym "blasty".
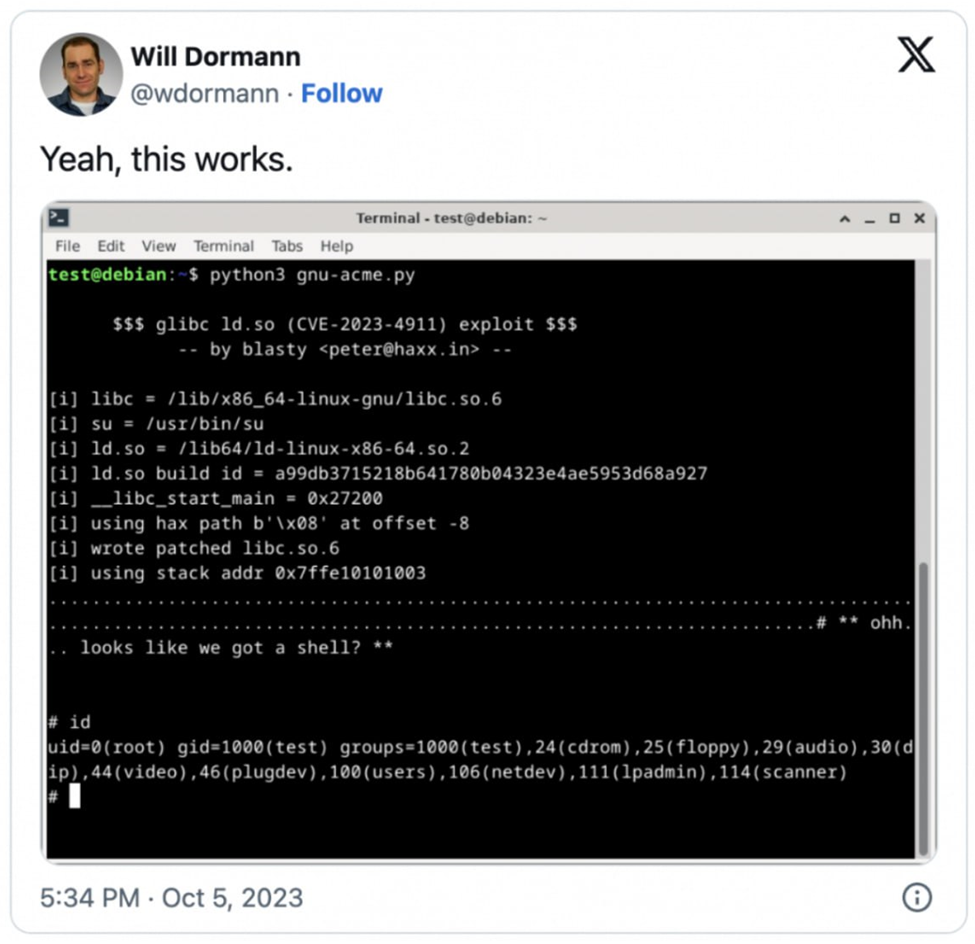
Other researchers are also simultaneously developing and publishing their own exploits for CVE-2023-4911 on GitHub and other sites.
"Our successful exploitation, leading to full root access in major distributions such as Fedora, Ubuntu, and Debian, underscores the severity and widespread nature of this vulnerability," said Abbasi, product manager for Qualys ' threat research division, said in a statement on October 3. It was Qualys experts who first identified this vulnerability.
Administrators should act immediately and secure their controlled Linux installations as soon as possible due to the significant threat posed by Looney Tunables.
Before we could tell you about the "Looney Tunables" vulnerability, which is tracked under the identifier CVE-2023-4911 , a PoC exploit has already appeared on the Internet, which allows you to successfully exploit this vulnerability in a real attack. Moreover, the complexity of using the vulnerability is extremely low — even a novice hacker can handle it.
Looney Tunables allows attackers to gain superuser rights on Linux systems by exploiting the buffer overflow flaw. The security flaw affects standard installations of Debian 12 and 13, Ubuntu 22.04 and 23.04, and Fedora 37 and 38.
Cybercriminals can exploit the vulnerability by using the maliciously created environment variable "GLIBC_TUNABLES", processed by the dynamic loader "ld.so", to achieve execution of arbitrary code with root rights when running binaries with SUID permission.
One of the PoC exploits, which has already been confirmed by vulnerability expert Will Dormann, was published by independent security researcher Peter Geissler under the pseudonym "blasty".

Other researchers are also simultaneously developing and publishing their own exploits for CVE-2023-4911 on GitHub and other sites.
"Our successful exploitation, leading to full root access in major distributions such as Fedora, Ubuntu, and Debian, underscores the severity and widespread nature of this vulnerability," said Abbasi, product manager for Qualys ' threat research division, said in a statement on October 3. It was Qualys experts who first identified this vulnerability.
Administrators should act immediately and secure their controlled Linux installations as soon as possible due to the significant threat posed by Looney Tunables.

