Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,493
- Points
- 113
Lecturer: Payne
(19:15:46) Payne: Greetings. Topic of the lecture: "Security and configuration of the virtual machine."
(19:16:13) Payne: The lecture includes the following parts:
1. General characteristics of privacy and security.
2. Structural adjustment of a virtual machine: programs and parameters.
3. Financial turnover, taking into account the properties of anonymity in the network.
(19:16:49) Payne: It’s customary to start from the basics, first of all, we will consider the fundamental rules of behavior in the field of Internet activity.
(19:17:13) Payne: Security.
It is necessary to be guided by a number of rules, violating which is strictly not recommended:
(19:17:29) Payne: Stop the dissemination of any personal information. The location and composition of the family, details, e-mails, social networks, specific nicknames that match the Instagram account, information about work activities and subscriber numbers should not leave the boundaries of a pure operating system and mind.
(19:18:16) Payne: Regardless of the person interested, buddy or colleague - anyone may not be the one who wants to be seen, I am no exception. It is important to be aware of what we intend to do and remember: “The personal must remain personal, the working must be working.” It applies not only to people, but also to Internet resources, from which the conclusion follows.
(19:18:52) Payne: Do not resort to the use of personal phone numbers, e-mails and social networks to register accounts on gray sites or stores. Mobile and Internet service providers, as well as e-mail companies, in most cases will simply issue information at the request of the competent services.
(19:19:20) Payne: Registration of mail that requires the adoption of an SMS code for activation is carried out using virtual online activators, for example: https://sms-activate.ru/. There are dozens of similar services; finding them will not be difficult. The forum has services, including for receiving messages to real numbers of English-speaking countries.
(19:20:00) Payne: Uncompromising rejection of activities in all countries of the post-Soviet space. It is much easier to track a resident who is in direct physical and administrative reach, which is once again confirmed by statistics and observations.
(19:20:27) Payne: This means that the use of this kind of material, shops and services is prohibited, dictated by common sense, and not by any code of honor.
(19:20:59) Payne: For the same reason, parcels are received through intermediaries and dummies. It is strongly discouraged to involve personal identification data in the characteristic process of the circulation of goods and finances in any form.
(19:21:37) Payne: Communication tools and correspondence histories corresponding to them should not be in open form on the main operating system. Inside a virtual machine? permissible. Skype, WhatsApp, Viber messengers and others like them are nonsense, due to the track record of leaks and vulnerabilities discovered that look like backdoors.
(19:22:36) Payne: Regarding Jabber, it’s important to use only servers that have a sufficient level of trust and reputation, and if possible to protect the communication space, if possible, enable OTR encryption. In the PSI + client, there are plugins, for Pidgin it is downloaded separately.
(19:23:26) Payne: By the way, making contacts in the public domain is fraught with spam, hacking attempts and possible fake accounts that are similar to your own, which in the future can add to your worries. There is such a need - additional ones are created.
(19:24:11) Payne: Methods for storing virtual machine images and information must have their own levels of protection. First of all, physical media: hard disk, SSD (both external and internal) or an ordinary flash drive. A removable drive is also convenient because in a critical situation it can be quickly physically removed or rendered unusable.
(19:24:44) Payne: Two characteristics play a significant role in choosing a device: volume and speed. There is little memory, so the choice is solely at your own discretion, a convenient minimum? 32GB.
(19:25:33) Payne: Speed is a consequence of the type of storage device and the characteristics of a computer. SSDs are definitely faster than hard drives, but the cost is clearly higher. For removable drives, the USB connection method is also significant: versions 3.0 and 3.1 win compared to v2.0 - for a simple definition of the version, you can see the color of the ports, with 3.0+ it is blue.
(19:26:21) Payne: When it comes to drive settings, it's mostly encryption. When choosing a specialized program, you can stop at Veracrypt; BitLocker and similar solutions are not recommended. Veracrypt is a fork of Truecrypt due to the closure of the latter and the doubt that arose on this basis.
(19:27:02) Payne: A container is created or the entire drive is encrypted, then confidential information is placed inside, in order to view which you need to decrypt (unmount) the password. To prevent the risk of capturing a password from RAM, hibernation is turned off, - instructions according to the operating system on the Internet.
(19:27:42) Payne: In addition, the program has the ability to create a hidden operating system. In case of emergency it will be possible to issue a password from the main one, existing in parallel, while the hidden one will continue to store files. Containers with a double bottom work in approximately the same way. Detailed manuals are in the main working conference on the forum and in the program help, in addition, the functionality is intuitive.
(19:28:27) Payne: For each site, account and container, passwords must be unique. The use of identical passwords often results in the loss of all accounts at once, since when draining one database the information from it can be used on other sites. There is no insurance against the sale or hacking of the database of any store of material, leaks from popular resources and subsequently banal brute force attacks by the enemy.
(19:29:05) Payne: The KeePass or equivalent can serve as a password manager. Needless to say, “qwerty54321” is not a strong password at all.
(19:29:28) Payne: However, it’s appropriate to inform about the convenient function of two-factor authentication. 2FA is an additional degree of protection implemented by generating code passwords every 30 seconds, which will not be superfluous to use where possible. For example, Authy or OTP applications are suitable.
(19:30:01) Payne: A separate virtual machine is created as a preventive measure to infect the virus. In order not to establish control over the device or to intercept passwords directly from the system, the installation of dubious and unverified programs is performed in a pre-prepared virtual system.
(19:30:42) Payne: It is recommended to periodically make backup copies of the most important data, which must be encrypted separately from the working system.
(19:31:16) Payne: To summarize the general conclusion on the first part, you can do this: neglect and half measures in matters of security have negative consequences. It’s not as troublesome to observe basic hygiene rules as getting caught because of naivety or losing money due to account theft.
(19:31:58) Payne: Setting up a virtual machine.
Virtualization software - VMware and VritualBox, where the latter version also works on Linux, and the solution for macOS is Parallels Desktop. The set of virtual machine settings does not change depending on the main system, just like the choice of an option for work does not matter.
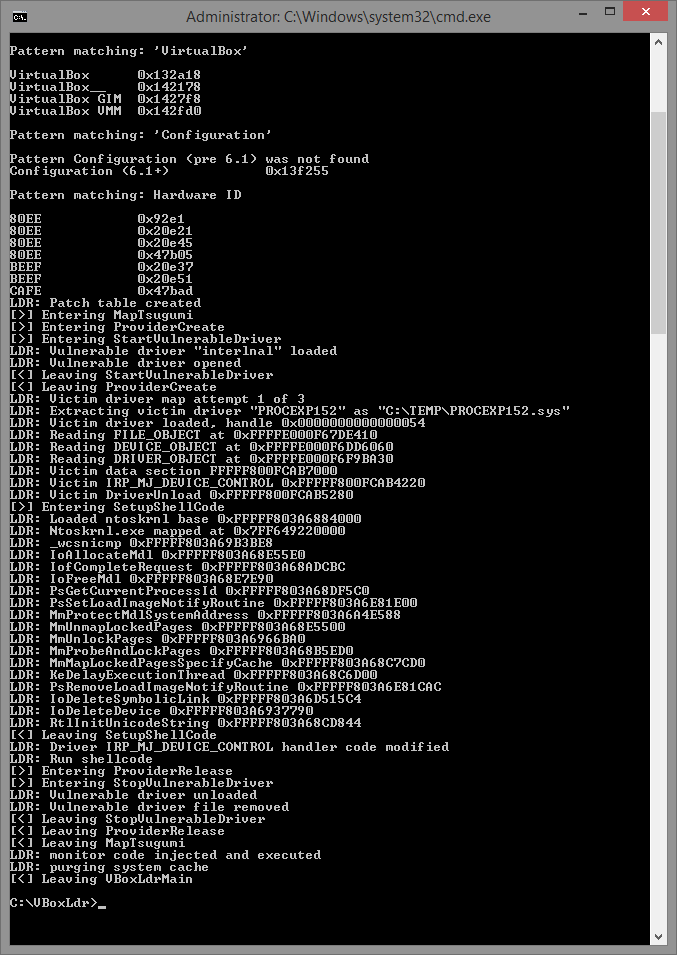
(19:32:37) Payne: Almost always in bios / uefi virtualization extensions are enabled, but some manufacturers disable them by default. The method of getting into this interface differs from the main system and computer model, so it’s worth using a search engine, virtualization, in the main, appears as VT, AMD-V or V. Extensions.
(19:33:18) Payne: A virtual machine has two fundamental functions: everyday use and work. Combining is not forbidden, however, the craft provides for constant changes of ip-addresses, a number of programs and parameters, so it is possible to make individual assemblies for different purposes.
(19:34:06) Payne: 1. The working arsenal includes the following:
VPN An encrypted connection from the user to the server through which the network is connected. In order to avoid conflicts with other IP accesses, it is installed on the main system. It is optimal to choose a service of third world countries; there can be no talk of a post-Soviet space; commercial service should not keep logging.
(19:34:52) Payne: You can create a VPN yourself by internally configuring a server dedicated to this purpose. A whole lecture could be given under the instructions, and their breakthrough network, for these reasons, will not be covered. After connecting, the IP address must change.
(19:35:20) Payne: The function of blocking traffic in case of unintentional disconnection of IP access for the purpose of insurance against disclosing a real IP address in VPN clients is called KillSwitch (or similar) and is contained in many clients, and it is implemented in Windows by creating rules in Firewall Properties: Outbound connections> Block of three tabs; then Outbound Rules> Program> Networking Application> Allow the connection. There are special programs on the network.
(19:36:33) Payne: A set of common browsers: Firefox, Chrome, Safari, TOR Browser and others. As for the latter, forums and material stores often have mirrors in the .onion zone, which must be opened through a torus. To prevent leakage of the real IP address, disable WebRTC technology in browsers: https://bit.ly/2F2BTLW.
(19:37:39) Payne: - In order to mask the IP address for work, SOCKS proxies and SSH tunnels are used. Present in the format ip-port + login-password (not always). These network protocols use different connection methods, for the initiation of which you should install a kit from Proxifier for socks and Bitvise or PuTTY for tunnels, respectively.
(19:38:21) Payne: The “Resolve hostnames through proxy” checkbox in the “Name Resolutions” item is turned on in the Proxifier, directly the socks are added in the “Proxy Servers” tab. When using Proxifier in conjunction with Bitvise or PuTTY for SSH, a rule is added to “Rules” on the label of the desired client, where the first or second item is selected in Action; the Sox should be of the form 127.0.0.1:8081/8080 without a password.
(19:39:11) Payne: Other settings come down to correlating input fields in clients and information about IP access - ip, ports, logins and passwords. There are plenty of guides on the aforementioned clients in the network and on the forum, so we won’t get acquainted in detail.
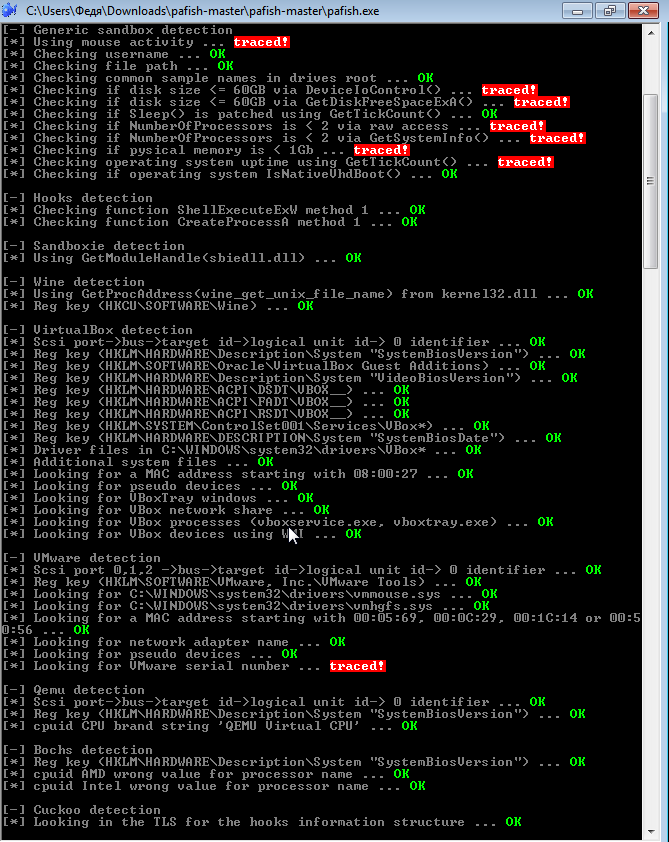
(19:39:45) Payne: - Antidetect? a program that uniquely works on the Internet, replacing browser fingerprints, for example, Linken Sphere. If there is a virtual machine, it is optional, although from a security point of view, tools should be stored in an isolated area. Use at will, on this subject there will be a lecture in the future.
(19:40:31) Payne: - Convenient text editor for recording. Freedom of choice is provided here, but if you raise the question with an edge, you can give a few examples: Notepad ++, RightNote, Standard Notes, CherryTree. At the same time, as with passwords and backups, it is definitely not worth keeping information in the cloud storage.
(19:41:04) Payne: The final connection sequence in the minimum acceptable configuration will be as follows: main system> VPN> encrypted storage area> virtual system> SOCKS / SSH> Internet.
(19:41:47) Payne: The chain is variable and can be supplemented in every way by introducing new links. For example, the last two items can be replaced with remote desktops: ... virtual system> VNC / RDP / dedicated server> Internet. Is it possible to supplement with antidetect, building a series of VPN? in sum, maneuvering is limited only by imagination.
(19:42:48) Payne: 2. The spectrum of parameters originates in the antifraud system. Antifraud - a system designed to evaluate financial transactions on the Internet for fraud. In fact, it is at the center of rules, filters, and lists. Knowledge of the internal kitchen in the future will be of help to overcome the "barrier" of antifraud systems.
(19:43:36) Payne: There are two categories to distinguish from the set of rules included in the system: IP-address and digital fingerprints. It is necessary to investigate their contents in order to have an idea of the mechanism of substitution of visibility - camouflage and from what perspective the future "buyer" will be evaluated.
(19:44:02) Payne: A) IP address.
(19:44:13) Payne: Black Lists or Black Lists. Such databases are formed by various companies that monitor IP addresses that carry out DDoS attacks, spam and other dark activities. Then, Internet providers, postal services, payment systems, banks and shops use them to check visitors. Consequently, an attempt to place an order with a dirty IP address will usually end in failure: TOR, public VPNs and proxy services are dotted with black lists.
(19:45:05) Payne: In addition, sometimes subnets of certain Internet providers become victims of prejudice based on the range of addresses previously involved in fraudulent activity.
(19:45:38) Payne: ISP and Hostname, or ISP and hostname. Thanks to flashy headings in names such as "proxy", "hidden", "vpn", intentions can be set to conceal and mask traffic,? one of the business cards of a typical scammer.
(19:46:20) Payne: Also, there are services that provide corporate or private provisioning services of virtual servers on remote access. By analogy with the previous paragraph, the IP address belonging to such a provider and specific systems (servers) contradict the pattern of the average buyer.
(19:46:58) Payne: In simple terms, a virtual server, for example, Amazon’s remote desktop — is not presentable, a VPN service, proxying or tunneling traffic — is reprehensible.
(19:47:39) Payne: In addition, there are providers who are in the high-risk zone from the point of view of many anti-fraud systems, which are often treated with increased attention. Examples from experience: rr, myfairpoint, frontier. Conversely, a few solid ones: qwest, charter, cox, att, verizon, comcast. In light of this, even the absence of black lists does not guarantee a result.
(19:48:22) Payne: DNS or domain name system? the connecting element of the site name and IP address on which this site is located. A kind of appendage and match with the IP address is not required; personal DNS should not leak. The decisive factor is usually not, but matching countries DNS and IP-address is without a doubt a plus.
(19:48:59) Payne: Sometimes it’s absent on SOCKS or SSH, then you can:
• register in the network adapter in the network control center and system sharing;
• register in the settings of the router (router);
• bundled with a VPN as one of the links in the chain.
(19:49:46) Payne: - Two-way ping - the approximate time of the client-server route. When establishing characteristic indicators (mainly over 40ms), the IP address is classified as a tunnel, which through the prism of antifraud systems can be one of the indicators of a potentially fraudulent operation.
(19:50:32) Payne: Unfortunately, without ownership of IP access at the administrator level, this cannot be resolved locally, which is why the following options remain:
• replacement of IP access (SOCKS / SSH);
• changing the link going to it in the connection chain, for example, changing the VPN server, - as an option, it does not always help;
• if you have administrative rights, you must prohibit ICMP traffic, instructions according to the system can be found on the network.
(19:51:49) Payne: Open ports: 80, 81, 1080, 3128, 8123, 8080, 8081 and so on. They testify to the use of proxy means, while at the same time being a double-edged sword. Firstly, a significant number of these addresses are just the web admin interface of the router. Secondly, contrary to the statements of sites for checking anonymity, a lot of pure traffic is generated from the IP addresses of the above types.
(19:52:47) Payne: Most of the properties of an IP address are essentially not “bad” or “good”. Proxies, VPNs, servers, and specific ISPs can be associated with a corporation, university, mobile operator, or other legitimate use of tools, whether it’s a personal purchase at work or operations from legal entities. faces.
(19:53:20) Payne: In this case, the traffic of groups of people is transmitted through one Internet access point, for example, to use a firewall or to increase productivity. It follows that a radical policy of containing all suspicious elements will inadvertently cause the suffering of ordinary users.
(19:54:08) Payne: In essence, this means: a) purchases from one IP address by different payment methods are possible, b) IP-addresses branded as “proxies” can be effective and c) there is a whole carriage for risk assessment and a small cart of other rules. Abstracts are confirmed experimentally.
(19:54:46) Payne: A set of measures for calculating the probability of using a proxy is called "proxyScore". “RiskScore” - as the name implies, a risk assessment when analyzing a transaction in general or an IP address in particular. Are designated within 0-100, respectively, than the value is higher? the worse. Mostly verification services are integrated into material stores, and on the forum and on the network you can find private representatives.
(19:55:48) Payne: The inherent variability of the evaluation criteria should be noted. Blacklists, ISPs and other attributes are changed daily, and also directly depend on specific anti-fraud systems, dozens of which should not have the same device and algorithms. For these reasons, it is extremely important to keep personal statistics.
(19:56:39) Payne: B) Digital fingerprints.
Fingerprint is a unique cast of browser and operating system settings. The receiving mechanism is actively used by antifraud systems both for assessing transaction risks and for simple tracking, because it allows you to recognize a client regardless of changing IP address, clearing cookies, and with a strong system and some settings.
(19:57:11) Payne: From a security point of view, it represents a set of methods that identify a user against the background of others. Including, therefore, the principle of isolation of the working environment is declared: it is one thing to assign a unique identifier to an anonymous observer for the purpose of advertising tracking, and completely different to the “buyer”.
(19:57:58) Payne: So, chronic use of a single configuration in the work will inevitably lead to recognition of the client, which can cause refusals to conduct transactions along with suspicious fingerprints. Very often, a data collection and analysis scenario includes:
(19:58:34) Payne: User Agent Along with the IP address, the first information that the site receives about the user when they visit it? browser name and version, device type, operating system and language. In order to be organic, you need to consider the language properties of the selected masking if the IP address is English? same system and browser.
(19:58:54) BruseLee left the room.
(19:59:19) Payne: One of the standards of analytical processes? statistical coincidence of illegal acts with a specific operating system or browser. You can illustrate this: for example, obviously suspicious proxies for the most part are based on Linux, which affects the attitude to the operating system itself.
(20:00:10) Payne: The more bona fide traffic is generated from the operating system or browser in the world, the more blurry the black to white ratio is, which means camouflage will be more natural. A vivid example? line of Windows, macOS, iOS, Android. Browsers: Chrome, Firefox, Safari, IE, Edge. As with blacklists, analytical materials are collected in real time and depend on the service.
(20:01:20) Payne: Passive OS Fingerprint. A fingerprint is formed from the parameters of data transmission to the network that are typical of operating systems: size, packet lifetime, and others. Mismatch of fingerprints of the traffic IP-address and User-Agent (for example, the packet was sent by Linux, and the Windows client)? flaw in the user's portrait.
(20:02:01) Payne: Because server-side configuration is the easiest way to smooth corners? change of IP access. Of the standard means, WiFi distribution from the required device can help you out through an emulator or neglect, provided that a compliant antifraud system is not crucial in the overall picture.
(20:02:54) Payne: - Screen resolution, window size, scaling. Uniqueization parameters simultaneously involved in risk assessment. Extremely rare indicators distinguish the user, and unnatural for the User-Agent due to the use of anti-detectors or emulators may raise suspicions: the phone does not have computer permission.
(20:03:43) Payne: Time & time zone. The time and time zone of the operating system must correspond to the location of the IP address, because the roughness in the disguise can sow doubt. Acting intensively from one locality, to prevent identification, it is worth setting the deviation in seconds between local and system time.
(20:04:23) Payne: - Fonts of the operating system. Font definition via Flash or JavaScript is a standard technique for user uniqueization. Operating systems have them by default, and the general list is replenished by installing programs with their own fonts: various kinds of Office, Adobe PDF, and so on.
(20:05:05) Payne: Extensions & Plugins? browser extensions and plugins installed. They can be detected by good antifraud systems by requesting the presence of certain id in the browser and fixing the display changes on the page. The simple “AdBlock” is unlikely to have a significant impact, but the tools to falsify the “User-Agent” and fingerprints against a serious opponent can play a trick.
(20:06:02) Payne: • Flash Player. A plugin for playing audio and video Flash-format sites, as well as one of the unique mechanisms. To some extent, openness gives the impression of honesty, and yet it is not necessary to install it, since accessing Adobe Flash provides information about the browser and operating system.
(20:06:45) Payne: Moreover, for today Flash the old module is turned off by default for many security reasons, due to the decline in popularity among users. However, it may be required to display the Flash content of certain sites, which will be notified accordingly.
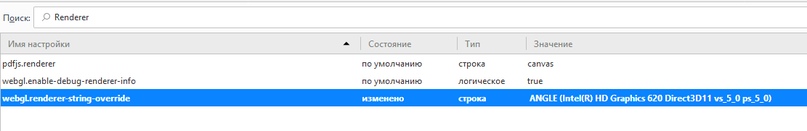
(20:07:28) Payne:? HTML5 Canvas (Canvas Fingerprint) and WebGL. Invisible rendering of elements by GPU resources with effects superimposed on them: text for Canvas and 3D object for WebGL. After processing, the data is converted to a hash code and attached to a common fingerprint for subsequent user identification.
(20:08:17) Payne: Fonts, versions of the GPU drivers, color depth, filtering, lighting and shadows, textures, and so on - to produce a personalized result, the hardware and software features of the device are used, where are each of the fragments? variable, and as a result, the existence of distinctive signs is understandable.
(20:09:08) Payne:? AudioContext Fingerprint. Evaluation of browser playback of low-frequency audio signal, similar to Canvas and WebGL, proceeds covertly taking into account the characteristics of the operating system and user equipment. Far from the most common method.
(20:09:49) Payne: Filling of the fingerprint are: bitrate, decibel value, number of input and output channels, output delay, sampling frequency, operation time and others, based on the antifraud system. It is possible to correct the print by modifying the parameters in the Virtual Audio Cable program or analogs.
(20:10:46) Payne: - Cookie. A small piece of data from a specific site stored in the operating system for authorization and settings. If there are cookies in the session, the site uniquely identifies the user, therefore, changing the disguise, you need to get rid of them.
(20:11:20) Payne: - Personal data of a mimicking personality: addresses, contact information, payment methods. Association by, for example, email between different accounts in the same store is a compromising attribute.
(20:11:50) Payne: To summarize. Is it smart to protect yourself from collecting a number of fingerprints by disabling the JavaScript programming language in the browser with which they are extracted? no way out. In this case, many sites will cease to function correctly, and there is no need to talk about strict compliance with the template of a respectable buyer.
(20:12:42) Payne: That's why camouflage is used, purposefully changing the components of prints: a device for User-Agent, plug-ins for the browser, fonts for the operating system, by this principle. Nevertheless, it is important not to upset the delicate balance, too unique settings will lead to recognition.
(20:13:29) Payne: It’s ironic, but even prohibiting tracking in browser settings (doNotTrack) or disabling cookies are parameters that highlight the user in and of themselves. Add to this atypical fonts or plugins, and we already have the opposite effect, a recognizable fingerprint.
(20:14:11) Payne: On the other hand, the antifraud system is a tool for forecasting risks, but the main task of any store is to securely receive and maximize profits. Stores are able to control algorithms so that the antifraud system does not respond to every “zilch”, substituting honest buyers with a hot hand.
(20:15:02) Payne: For any reason, whether it is a low-risk assortment or maximizing profits, stores set their own combinations of rules and an acceptable threshold for anomalies in prints. So, individual checks may be absent, and errors may not be taken into account, for example, AudioContext or some blacklists, and on the contrary, somewhere they will poke on all fronts.
(20:15:55) Payne: Examples of sites for checking the characteristics of an IP address and operating system (checkers):
• whoer.net;
• whatleaks.com;
• browserleaks.com;
• 2ip.ru/privacy/;
• ip-score.com;
• maxmind.com;
• f.vision.
Repeatedly checking proxyScore, riskScore, Black List indicators sometimes provokes IP address pollution, you should not overdo it.
(20:16:41) Payne: Financial turnover.
Cryptocurrencies are an integral part of the profession. Most accepted have passed the test of time and the community: Bitcoin, Ethereum, Litecoin. The use of cryptocurrencies is technically possible, perhaps better implemented or more profitable in terms of investments at your own peril and risk.
(20:17:28) Payne: It is noteworthy that, contrary to popular belief about cryptocurrencies as a “anonymous” payment system, they do not give carte blanche in the matter of financial transactions, this is a myth. Anonymity is the inability to establish the source, but due to the availability of cryptocurrency transactions in open form, the source address is the source, which allows you to track the cash flow vector.
(20:18:12) Payne: On closer inspection, the prerogative of cryptocurrencies is confidentiality, lack of personal data during registration and transactions. It is necessary to distinguish between “anonymity” and “confidentiality”, while not taking into account the carelessness of “medium-sized fish”.
(20:18:47) Payne: You can confuse the tracks by regularly changing the sending and receiving addresses (provided by many wallets), passing funds through various exchangers, cryptocurrencies or mixers. Mixer - transaction anonymization service. In practice, the technology of crushing customer funds into small parts and subsequent mixing with parts of other customers. The choice of mixers and exchangers, based on reviews and reputation.
(20:19:38) Payne: There are two types of cryptocurrency wallets: “hot” and “cold”. Hot - anyone who needs access to the Internet: exchanges, online wallets, exchangers. So, in fact, the funds are located on the servers, and the client only gets access to them? I recall the news about the loss of funds after hacking exchanges.
(20:20:07) Payne: Cold? The concept of local storage, which does not require constant access to the Internet. Despite the vulnerability of hot to hacking, they are convenient for frequent and small transactions, and the idea of cold is to safely store funds.
(20:20:47) Payne: Recommended Wallets:
• Bitcoin Core;
• Electrum;
• Blockchain.
It is worth emphasizing that dealing with cryptocurrencies leaves the probability of losing funds due to external factors: depreciation, hacking of the exchange, exchange fraud.
(20:21:18) Payne: In relation to fiat currencies (USD, EUR, RUB, UAH and so on) and operations from official exchanges, wallets or exchangers, the incognito behavior model is applied. The history of customer actions is preserved, so IP addresses, personal information and device fingerprints should not be involved in the financial turnover process.
(20:21:43) Payne: Instead, you can use:
? Virtual machines and SMS activation services.
(20:22:16) Payne: Wallets, exchanges, and credit card accounts for dummies (drops). They can block or steal, it’s better not to delay such funds and periodically replace them. The corresponding services for verifying accounts and selling cards are on the forum.
(20:22:46) Payne: Many exchangers conduct cash transactions. Courier services are suitable for both withdrawal and deposit.
? Terminals Entering pre-registered confidential wallets.
(20:23:08) Payne: An informal rule of cooperation with users in this field of activity? Guarantor Service. Saves nerve cells and finances.
(20:23:25) Payne: That's all. Optionally, a review of the lecture can be sent here.
We pass to questions, put "?".
(20:24:27) Serrwrtet: 1. What is the fingerprint of proxy services? How critical is using a Linux fingerprint proxy?
2. How critical is it to use socks without your own DNS?
(20:26:20) Payne: 1. Specifically, there is no such imprint. But in the name of the provider may appear the trigger word "proxy" or in a passive fingerprint. About both points was in a lecture, more attentively. Too critical - uncritical if the antifraud system is not from the breed of the toughest.
2. It is uncritical for the same reason, but in this case it should either not be determined at all, or not be Russian or similarly suspicious.
(20:26:31) bloomberg7:
1) what is the difference between tunnels and Soxes?
2) Is it true that the sphere burns with many antifrauds?
3) Does Anitfrod provide a site for Marchant?
4) A lot of user identification methods, how to deal with it and how to find out which what is the antifraud that pays attention to?
5) if you work with the logs, then you do not need to bathe with the settings, just copy everything that the victim has?
(20:29:12) Payne:
1. The fact that these are different connection protocols.
2. Depends on the settings of the sphere itself; I repeat, there will be a lecture on antidetects, and ask there
3. Shops can both write their own and rent a third-party one, there is no definite answer.
4. How to deal is described in the prints themselves and in the quote: “That's why camouflage is used to purposefully change the components of the prints: a device for User-Agent, browser plug-ins, fonts for the operating system - by this principle. Nevertheless, it’s important not to break fragile balance, too unique settings will lead to recognition. ", - I repeat, more carefully. Also, there are antidetects, various kinds of remote accesses, emulators and so on.
5. Well, the victim may not have all the necessary data, also, something may leak somewhere, so I would not call the approach after the sleeves acceptable.
(20:29:18) Rarka_: Where do I see DNS on the Sox or not and the second question is whether the macadress antifraud is burning
(20:29:45) Payne: 1. I gave a list of sites to check the characteristics
2. Through the browser - no
(20:30:00) id666: Payne: where is it better to buy a proxy? (price / quality ratio) and which type is better to use?
(20:30:35) Payne: SOCKS5. Material stores near the end of training will be in the main working conference
(20:31:18) macpru: What about contacting vendors from the forum thru telegram or jabber? Also best to use in virtual?
(20:32:06) Payne: Yes and yes. Jabber better. Telegram only on fake number, in virtual.
(20:32:55) id666: Payne: will there be a separate topic for logs?
(20:33:23) Payne: id666 Specify in the list of lectures in the topic of training, I do not make a schedule, I can not say)
(20:34:02) macpru: if one can always change virual within intervals of 6 months with the same system with every indentity change?
(20:34:13) macpru: or does it all rely on the system?
(20:34:20) ShadowConsult: will we touch on all of this from today's lecture in practice? When using a sphere, do you need a lot of settings, can you configure VPN and TP, or is it all generated in it?
(20:34:59) macpru: i meant will identity change as you change your virtuals?
(20:37:16) Payne: ShadowConsult and why not? With any drive, you will touch the fingerprints, depending on the antifraud system, somewhere more, somewhere less. As you gain experience and the number of maganizas, go through everything. Scope - browser, it does not generate IP-access as a VPN, and SOCKS / SSH.
macpru Didn't get your question. How to change fingerprints? By change their details, like system to USER-AGENT or fonts to system. There is some fingerprints, based on computer and system configuration, so just reinstall virtual machine won't always help. Idk try to ask again in other words.
(20:38:27) usbnet: I write again, for some reason the toad does not plow with the clipboard
(20:38:33) usbnet: wanted to copy
(20:38:52) macpru: I got the answer thank you.
(20:39:11) bloomberg7: how to find out which of the merchants in the shop and which of the merchants is the weaker antifraud, because they are somehow classified?
(20:39:33) bloomberg7: as I understand it through trial and error?
(20:40:34) usbnet: 1. regarding the encryption of the machine, are there any differences in performance if you use a separate removable drive and the main hard drive?
2. At the beginning, the moment was mentioned about not disclosing any personal information, and not storing the data. Did you mention this when working through a virtual machine? after all, working with the virtual machine will not cause any problems, and draining data from the main OS
(20:40:40) Payne: 1. In the future we’ll tell you, now the topic is to configure a virtual machine
2. At least the approximate stability of the antifraud system can be deduced purely logically: a ballpoint pen store will not have an Amazon antifraud system, like Amazon or any other world-famous store with thousands of purchases per day, it will not have an antifraud store with socks; more details - experience, of course.
(20:40:47) Payne: This is the answer of bloomberg7
(20:42:07) Payne: usbnet 1. If, for example, a removable SSD, and the main HDD - differences in speed. In short, it depends on the drives themselves, the principal ones do not.
2. It is always relevant in this field of activity. Outside of her, it’s a personal matter.
(20:42:20) id666: Payne: will we get detailed step-by-step instructions for setting up a working PC in the future, or will we have to shovel, think out and read everything ourselves?
(20:43:29) usbnet: 3. And which option is the best for encryption, in the main conference there are 4 encryption options, which is better to choose for someone who just at the beginning (at the moment I encrypted the main OS and the whole drive)
(20:43:47) net23: I have a virtual activation key asking where to get it?
(20:44:07) Payne: No need to think through anything, everything has already been voiced. But if this answer did not suit you, I will say this: we do not provide step-by-step instructions from the category "how to install a browser" or "how to install an operating system." Examine the information, understand the essence of the terminology - understand the principles of work. According to the functionality of some leadership programs, there is in the main working conference, the rest is just surfing, you can say.
(20:45:14) Payne: usbnet That at the moment is enough. The best, in my humble opinion, encrypted external drive.
net23 KMSAuto activator, for example.
(20:45:19) Rarka_: The question about ports was raised, I don’t really care where I look at them in ip
(20:45:38) Payne: Sites for checking the characteristics of the IP address and system were given in the lecture on them.
(20:46:16) stic_: Question about AudioContext Fingerprint, I haven’t heard about it before, so I’m wondering if you need to install Virtual Audio Cable ”or an analogue and on the basis of and on the virtual machine where will we drive it from?
(20:46:46) stic_: based on additional security when surfing, for example
(20:47:50) Payne: No, not to be fired, but to change. To put there - from where the network is connected, go out from the virtual - and put it on it. This is not the most popular fingerprinting system, so you should not go in cycles. And on the basis of security, an extension to the browser will be sufficient, generating a fingerprint at random.
(20:50:28) Kto-to: The sphere, as it were, separates the data from my computer and the data that is in the sphere
(20:51:40) Payne: It’s as if generating new, but the idea is in the right direction. The sphere is antidetect, now the lecture is not about that and in the future a whole lecture will be reserved for antidetects, more details there.
(20:51:57) Payne: Now I definitely say goodbye. All the best.
(19:15:46) Payne: Greetings. Topic of the lecture: "Security and configuration of the virtual machine."
(19:16:13) Payne: The lecture includes the following parts:
1. General characteristics of privacy and security.
2. Structural adjustment of a virtual machine: programs and parameters.
3. Financial turnover, taking into account the properties of anonymity in the network.
(19:16:49) Payne: It’s customary to start from the basics, first of all, we will consider the fundamental rules of behavior in the field of Internet activity.
(19:17:13) Payne: Security.
It is necessary to be guided by a number of rules, violating which is strictly not recommended:
(19:17:29) Payne: Stop the dissemination of any personal information. The location and composition of the family, details, e-mails, social networks, specific nicknames that match the Instagram account, information about work activities and subscriber numbers should not leave the boundaries of a pure operating system and mind.
(19:18:16) Payne: Regardless of the person interested, buddy or colleague - anyone may not be the one who wants to be seen, I am no exception. It is important to be aware of what we intend to do and remember: “The personal must remain personal, the working must be working.” It applies not only to people, but also to Internet resources, from which the conclusion follows.
(19:18:52) Payne: Do not resort to the use of personal phone numbers, e-mails and social networks to register accounts on gray sites or stores. Mobile and Internet service providers, as well as e-mail companies, in most cases will simply issue information at the request of the competent services.
(19:19:20) Payne: Registration of mail that requires the adoption of an SMS code for activation is carried out using virtual online activators, for example: https://sms-activate.ru/. There are dozens of similar services; finding them will not be difficult. The forum has services, including for receiving messages to real numbers of English-speaking countries.
(19:20:00) Payne: Uncompromising rejection of activities in all countries of the post-Soviet space. It is much easier to track a resident who is in direct physical and administrative reach, which is once again confirmed by statistics and observations.
(19:20:27) Payne: This means that the use of this kind of material, shops and services is prohibited, dictated by common sense, and not by any code of honor.
(19:20:59) Payne: For the same reason, parcels are received through intermediaries and dummies. It is strongly discouraged to involve personal identification data in the characteristic process of the circulation of goods and finances in any form.
(19:21:37) Payne: Communication tools and correspondence histories corresponding to them should not be in open form on the main operating system. Inside a virtual machine? permissible. Skype, WhatsApp, Viber messengers and others like them are nonsense, due to the track record of leaks and vulnerabilities discovered that look like backdoors.
(19:22:36) Payne: Regarding Jabber, it’s important to use only servers that have a sufficient level of trust and reputation, and if possible to protect the communication space, if possible, enable OTR encryption. In the PSI + client, there are plugins, for Pidgin it is downloaded separately.
(19:23:26) Payne: By the way, making contacts in the public domain is fraught with spam, hacking attempts and possible fake accounts that are similar to your own, which in the future can add to your worries. There is such a need - additional ones are created.
(19:24:11) Payne: Methods for storing virtual machine images and information must have their own levels of protection. First of all, physical media: hard disk, SSD (both external and internal) or an ordinary flash drive. A removable drive is also convenient because in a critical situation it can be quickly physically removed or rendered unusable.
(19:24:44) Payne: Two characteristics play a significant role in choosing a device: volume and speed. There is little memory, so the choice is solely at your own discretion, a convenient minimum? 32GB.
(19:25:33) Payne: Speed is a consequence of the type of storage device and the characteristics of a computer. SSDs are definitely faster than hard drives, but the cost is clearly higher. For removable drives, the USB connection method is also significant: versions 3.0 and 3.1 win compared to v2.0 - for a simple definition of the version, you can see the color of the ports, with 3.0+ it is blue.
(19:26:21) Payne: When it comes to drive settings, it's mostly encryption. When choosing a specialized program, you can stop at Veracrypt; BitLocker and similar solutions are not recommended. Veracrypt is a fork of Truecrypt due to the closure of the latter and the doubt that arose on this basis.
(19:27:02) Payne: A container is created or the entire drive is encrypted, then confidential information is placed inside, in order to view which you need to decrypt (unmount) the password. To prevent the risk of capturing a password from RAM, hibernation is turned off, - instructions according to the operating system on the Internet.
(19:27:42) Payne: In addition, the program has the ability to create a hidden operating system. In case of emergency it will be possible to issue a password from the main one, existing in parallel, while the hidden one will continue to store files. Containers with a double bottom work in approximately the same way. Detailed manuals are in the main working conference on the forum and in the program help, in addition, the functionality is intuitive.
(19:28:27) Payne: For each site, account and container, passwords must be unique. The use of identical passwords often results in the loss of all accounts at once, since when draining one database the information from it can be used on other sites. There is no insurance against the sale or hacking of the database of any store of material, leaks from popular resources and subsequently banal brute force attacks by the enemy.
(19:29:05) Payne: The KeePass or equivalent can serve as a password manager. Needless to say, “qwerty54321” is not a strong password at all.
(19:29:28) Payne: However, it’s appropriate to inform about the convenient function of two-factor authentication. 2FA is an additional degree of protection implemented by generating code passwords every 30 seconds, which will not be superfluous to use where possible. For example, Authy or OTP applications are suitable.
(19:30:01) Payne: A separate virtual machine is created as a preventive measure to infect the virus. In order not to establish control over the device or to intercept passwords directly from the system, the installation of dubious and unverified programs is performed in a pre-prepared virtual system.
(19:30:42) Payne: It is recommended to periodically make backup copies of the most important data, which must be encrypted separately from the working system.
(19:31:16) Payne: To summarize the general conclusion on the first part, you can do this: neglect and half measures in matters of security have negative consequences. It’s not as troublesome to observe basic hygiene rules as getting caught because of naivety or losing money due to account theft.
(19:31:58) Payne: Setting up a virtual machine.
Virtualization software - VMware and VritualBox, where the latter version also works on Linux, and the solution for macOS is Parallels Desktop. The set of virtual machine settings does not change depending on the main system, just like the choice of an option for work does not matter.
(19:32:37) Payne: Almost always in bios / uefi virtualization extensions are enabled, but some manufacturers disable them by default. The method of getting into this interface differs from the main system and computer model, so it’s worth using a search engine, virtualization, in the main, appears as VT, AMD-V or V. Extensions.
(19:33:18) Payne: A virtual machine has two fundamental functions: everyday use and work. Combining is not forbidden, however, the craft provides for constant changes of ip-addresses, a number of programs and parameters, so it is possible to make individual assemblies for different purposes.
(19:34:06) Payne: 1. The working arsenal includes the following:
VPN An encrypted connection from the user to the server through which the network is connected. In order to avoid conflicts with other IP accesses, it is installed on the main system. It is optimal to choose a service of third world countries; there can be no talk of a post-Soviet space; commercial service should not keep logging.
(19:34:52) Payne: You can create a VPN yourself by internally configuring a server dedicated to this purpose. A whole lecture could be given under the instructions, and their breakthrough network, for these reasons, will not be covered. After connecting, the IP address must change.
(19:35:20) Payne: The function of blocking traffic in case of unintentional disconnection of IP access for the purpose of insurance against disclosing a real IP address in VPN clients is called KillSwitch (or similar) and is contained in many clients, and it is implemented in Windows by creating rules in Firewall Properties: Outbound connections> Block of three tabs; then Outbound Rules> Program> Networking Application> Allow the connection. There are special programs on the network.
(19:36:33) Payne: A set of common browsers: Firefox, Chrome, Safari, TOR Browser and others. As for the latter, forums and material stores often have mirrors in the .onion zone, which must be opened through a torus. To prevent leakage of the real IP address, disable WebRTC technology in browsers: https://bit.ly/2F2BTLW.
(19:37:39) Payne: - In order to mask the IP address for work, SOCKS proxies and SSH tunnels are used. Present in the format ip-port + login-password (not always). These network protocols use different connection methods, for the initiation of which you should install a kit from Proxifier for socks and Bitvise or PuTTY for tunnels, respectively.
(19:38:21) Payne: The “Resolve hostnames through proxy” checkbox in the “Name Resolutions” item is turned on in the Proxifier, directly the socks are added in the “Proxy Servers” tab. When using Proxifier in conjunction with Bitvise or PuTTY for SSH, a rule is added to “Rules” on the label of the desired client, where the first or second item is selected in Action; the Sox should be of the form 127.0.0.1:8081/8080 without a password.
(19:39:11) Payne: Other settings come down to correlating input fields in clients and information about IP access - ip, ports, logins and passwords. There are plenty of guides on the aforementioned clients in the network and on the forum, so we won’t get acquainted in detail.
(19:39:45) Payne: - Antidetect? a program that uniquely works on the Internet, replacing browser fingerprints, for example, Linken Sphere. If there is a virtual machine, it is optional, although from a security point of view, tools should be stored in an isolated area. Use at will, on this subject there will be a lecture in the future.
(19:40:31) Payne: - Convenient text editor for recording. Freedom of choice is provided here, but if you raise the question with an edge, you can give a few examples: Notepad ++, RightNote, Standard Notes, CherryTree. At the same time, as with passwords and backups, it is definitely not worth keeping information in the cloud storage.
(19:41:04) Payne: The final connection sequence in the minimum acceptable configuration will be as follows: main system> VPN> encrypted storage area> virtual system> SOCKS / SSH> Internet.
(19:41:47) Payne: The chain is variable and can be supplemented in every way by introducing new links. For example, the last two items can be replaced with remote desktops: ... virtual system> VNC / RDP / dedicated server> Internet. Is it possible to supplement with antidetect, building a series of VPN? in sum, maneuvering is limited only by imagination.
(19:42:48) Payne: 2. The spectrum of parameters originates in the antifraud system. Antifraud - a system designed to evaluate financial transactions on the Internet for fraud. In fact, it is at the center of rules, filters, and lists. Knowledge of the internal kitchen in the future will be of help to overcome the "barrier" of antifraud systems.
(19:43:36) Payne: There are two categories to distinguish from the set of rules included in the system: IP-address and digital fingerprints. It is necessary to investigate their contents in order to have an idea of the mechanism of substitution of visibility - camouflage and from what perspective the future "buyer" will be evaluated.
(19:44:02) Payne: A) IP address.
(19:44:13) Payne: Black Lists or Black Lists. Such databases are formed by various companies that monitor IP addresses that carry out DDoS attacks, spam and other dark activities. Then, Internet providers, postal services, payment systems, banks and shops use them to check visitors. Consequently, an attempt to place an order with a dirty IP address will usually end in failure: TOR, public VPNs and proxy services are dotted with black lists.
(19:45:05) Payne: In addition, sometimes subnets of certain Internet providers become victims of prejudice based on the range of addresses previously involved in fraudulent activity.
(19:45:38) Payne: ISP and Hostname, or ISP and hostname. Thanks to flashy headings in names such as "proxy", "hidden", "vpn", intentions can be set to conceal and mask traffic,? one of the business cards of a typical scammer.
(19:46:20) Payne: Also, there are services that provide corporate or private provisioning services of virtual servers on remote access. By analogy with the previous paragraph, the IP address belonging to such a provider and specific systems (servers) contradict the pattern of the average buyer.
(19:46:58) Payne: In simple terms, a virtual server, for example, Amazon’s remote desktop — is not presentable, a VPN service, proxying or tunneling traffic — is reprehensible.
(19:47:39) Payne: In addition, there are providers who are in the high-risk zone from the point of view of many anti-fraud systems, which are often treated with increased attention. Examples from experience: rr, myfairpoint, frontier. Conversely, a few solid ones: qwest, charter, cox, att, verizon, comcast. In light of this, even the absence of black lists does not guarantee a result.
(19:48:22) Payne: DNS or domain name system? the connecting element of the site name and IP address on which this site is located. A kind of appendage and match with the IP address is not required; personal DNS should not leak. The decisive factor is usually not, but matching countries DNS and IP-address is without a doubt a plus.
(19:48:59) Payne: Sometimes it’s absent on SOCKS or SSH, then you can:
• register in the network adapter in the network control center and system sharing;
• register in the settings of the router (router);
• bundled with a VPN as one of the links in the chain.
(19:49:46) Payne: - Two-way ping - the approximate time of the client-server route. When establishing characteristic indicators (mainly over 40ms), the IP address is classified as a tunnel, which through the prism of antifraud systems can be one of the indicators of a potentially fraudulent operation.
(19:50:32) Payne: Unfortunately, without ownership of IP access at the administrator level, this cannot be resolved locally, which is why the following options remain:
• replacement of IP access (SOCKS / SSH);
• changing the link going to it in the connection chain, for example, changing the VPN server, - as an option, it does not always help;
• if you have administrative rights, you must prohibit ICMP traffic, instructions according to the system can be found on the network.
(19:51:49) Payne: Open ports: 80, 81, 1080, 3128, 8123, 8080, 8081 and so on. They testify to the use of proxy means, while at the same time being a double-edged sword. Firstly, a significant number of these addresses are just the web admin interface of the router. Secondly, contrary to the statements of sites for checking anonymity, a lot of pure traffic is generated from the IP addresses of the above types.
(19:52:47) Payne: Most of the properties of an IP address are essentially not “bad” or “good”. Proxies, VPNs, servers, and specific ISPs can be associated with a corporation, university, mobile operator, or other legitimate use of tools, whether it’s a personal purchase at work or operations from legal entities. faces.
(19:53:20) Payne: In this case, the traffic of groups of people is transmitted through one Internet access point, for example, to use a firewall or to increase productivity. It follows that a radical policy of containing all suspicious elements will inadvertently cause the suffering of ordinary users.
(19:54:08) Payne: In essence, this means: a) purchases from one IP address by different payment methods are possible, b) IP-addresses branded as “proxies” can be effective and c) there is a whole carriage for risk assessment and a small cart of other rules. Abstracts are confirmed experimentally.
(19:54:46) Payne: A set of measures for calculating the probability of using a proxy is called "proxyScore". “RiskScore” - as the name implies, a risk assessment when analyzing a transaction in general or an IP address in particular. Are designated within 0-100, respectively, than the value is higher? the worse. Mostly verification services are integrated into material stores, and on the forum and on the network you can find private representatives.
(19:55:48) Payne: The inherent variability of the evaluation criteria should be noted. Blacklists, ISPs and other attributes are changed daily, and also directly depend on specific anti-fraud systems, dozens of which should not have the same device and algorithms. For these reasons, it is extremely important to keep personal statistics.
(19:56:39) Payne: B) Digital fingerprints.
Fingerprint is a unique cast of browser and operating system settings. The receiving mechanism is actively used by antifraud systems both for assessing transaction risks and for simple tracking, because it allows you to recognize a client regardless of changing IP address, clearing cookies, and with a strong system and some settings.
(19:57:11) Payne: From a security point of view, it represents a set of methods that identify a user against the background of others. Including, therefore, the principle of isolation of the working environment is declared: it is one thing to assign a unique identifier to an anonymous observer for the purpose of advertising tracking, and completely different to the “buyer”.
(19:57:58) Payne: So, chronic use of a single configuration in the work will inevitably lead to recognition of the client, which can cause refusals to conduct transactions along with suspicious fingerprints. Very often, a data collection and analysis scenario includes:
(19:58:34) Payne: User Agent Along with the IP address, the first information that the site receives about the user when they visit it? browser name and version, device type, operating system and language. In order to be organic, you need to consider the language properties of the selected masking if the IP address is English? same system and browser.
(19:58:54) BruseLee left the room.
(19:59:19) Payne: One of the standards of analytical processes? statistical coincidence of illegal acts with a specific operating system or browser. You can illustrate this: for example, obviously suspicious proxies for the most part are based on Linux, which affects the attitude to the operating system itself.
(20:00:10) Payne: The more bona fide traffic is generated from the operating system or browser in the world, the more blurry the black to white ratio is, which means camouflage will be more natural. A vivid example? line of Windows, macOS, iOS, Android. Browsers: Chrome, Firefox, Safari, IE, Edge. As with blacklists, analytical materials are collected in real time and depend on the service.
(20:01:20) Payne: Passive OS Fingerprint. A fingerprint is formed from the parameters of data transmission to the network that are typical of operating systems: size, packet lifetime, and others. Mismatch of fingerprints of the traffic IP-address and User-Agent (for example, the packet was sent by Linux, and the Windows client)? flaw in the user's portrait.
(20:02:01) Payne: Because server-side configuration is the easiest way to smooth corners? change of IP access. Of the standard means, WiFi distribution from the required device can help you out through an emulator or neglect, provided that a compliant antifraud system is not crucial in the overall picture.
(20:02:54) Payne: - Screen resolution, window size, scaling. Uniqueization parameters simultaneously involved in risk assessment. Extremely rare indicators distinguish the user, and unnatural for the User-Agent due to the use of anti-detectors or emulators may raise suspicions: the phone does not have computer permission.
(20:03:43) Payne: Time & time zone. The time and time zone of the operating system must correspond to the location of the IP address, because the roughness in the disguise can sow doubt. Acting intensively from one locality, to prevent identification, it is worth setting the deviation in seconds between local and system time.
(20:04:23) Payne: - Fonts of the operating system. Font definition via Flash or JavaScript is a standard technique for user uniqueization. Operating systems have them by default, and the general list is replenished by installing programs with their own fonts: various kinds of Office, Adobe PDF, and so on.
(20:05:05) Payne: Extensions & Plugins? browser extensions and plugins installed. They can be detected by good antifraud systems by requesting the presence of certain id in the browser and fixing the display changes on the page. The simple “AdBlock” is unlikely to have a significant impact, but the tools to falsify the “User-Agent” and fingerprints against a serious opponent can play a trick.
(20:06:02) Payne: • Flash Player. A plugin for playing audio and video Flash-format sites, as well as one of the unique mechanisms. To some extent, openness gives the impression of honesty, and yet it is not necessary to install it, since accessing Adobe Flash provides information about the browser and operating system.
(20:06:45) Payne: Moreover, for today Flash the old module is turned off by default for many security reasons, due to the decline in popularity among users. However, it may be required to display the Flash content of certain sites, which will be notified accordingly.
(20:07:28) Payne:? HTML5 Canvas (Canvas Fingerprint) and WebGL. Invisible rendering of elements by GPU resources with effects superimposed on them: text for Canvas and 3D object for WebGL. After processing, the data is converted to a hash code and attached to a common fingerprint for subsequent user identification.
(20:08:17) Payne: Fonts, versions of the GPU drivers, color depth, filtering, lighting and shadows, textures, and so on - to produce a personalized result, the hardware and software features of the device are used, where are each of the fragments? variable, and as a result, the existence of distinctive signs is understandable.
(20:09:08) Payne:? AudioContext Fingerprint. Evaluation of browser playback of low-frequency audio signal, similar to Canvas and WebGL, proceeds covertly taking into account the characteristics of the operating system and user equipment. Far from the most common method.
(20:09:49) Payne: Filling of the fingerprint are: bitrate, decibel value, number of input and output channels, output delay, sampling frequency, operation time and others, based on the antifraud system. It is possible to correct the print by modifying the parameters in the Virtual Audio Cable program or analogs.
(20:10:46) Payne: - Cookie. A small piece of data from a specific site stored in the operating system for authorization and settings. If there are cookies in the session, the site uniquely identifies the user, therefore, changing the disguise, you need to get rid of them.
(20:11:20) Payne: - Personal data of a mimicking personality: addresses, contact information, payment methods. Association by, for example, email between different accounts in the same store is a compromising attribute.
(20:11:50) Payne: To summarize. Is it smart to protect yourself from collecting a number of fingerprints by disabling the JavaScript programming language in the browser with which they are extracted? no way out. In this case, many sites will cease to function correctly, and there is no need to talk about strict compliance with the template of a respectable buyer.
(20:12:42) Payne: That's why camouflage is used, purposefully changing the components of prints: a device for User-Agent, plug-ins for the browser, fonts for the operating system, by this principle. Nevertheless, it is important not to upset the delicate balance, too unique settings will lead to recognition.
(20:13:29) Payne: It’s ironic, but even prohibiting tracking in browser settings (doNotTrack) or disabling cookies are parameters that highlight the user in and of themselves. Add to this atypical fonts or plugins, and we already have the opposite effect, a recognizable fingerprint.
(20:14:11) Payne: On the other hand, the antifraud system is a tool for forecasting risks, but the main task of any store is to securely receive and maximize profits. Stores are able to control algorithms so that the antifraud system does not respond to every “zilch”, substituting honest buyers with a hot hand.
(20:15:02) Payne: For any reason, whether it is a low-risk assortment or maximizing profits, stores set their own combinations of rules and an acceptable threshold for anomalies in prints. So, individual checks may be absent, and errors may not be taken into account, for example, AudioContext or some blacklists, and on the contrary, somewhere they will poke on all fronts.
(20:15:55) Payne: Examples of sites for checking the characteristics of an IP address and operating system (checkers):
• whoer.net;
• whatleaks.com;
• browserleaks.com;
• 2ip.ru/privacy/;
• ip-score.com;
• maxmind.com;
• f.vision.
Repeatedly checking proxyScore, riskScore, Black List indicators sometimes provokes IP address pollution, you should not overdo it.
(20:16:41) Payne: Financial turnover.
Cryptocurrencies are an integral part of the profession. Most accepted have passed the test of time and the community: Bitcoin, Ethereum, Litecoin. The use of cryptocurrencies is technically possible, perhaps better implemented or more profitable in terms of investments at your own peril and risk.
(20:17:28) Payne: It is noteworthy that, contrary to popular belief about cryptocurrencies as a “anonymous” payment system, they do not give carte blanche in the matter of financial transactions, this is a myth. Anonymity is the inability to establish the source, but due to the availability of cryptocurrency transactions in open form, the source address is the source, which allows you to track the cash flow vector.
(20:18:12) Payne: On closer inspection, the prerogative of cryptocurrencies is confidentiality, lack of personal data during registration and transactions. It is necessary to distinguish between “anonymity” and “confidentiality”, while not taking into account the carelessness of “medium-sized fish”.
(20:18:47) Payne: You can confuse the tracks by regularly changing the sending and receiving addresses (provided by many wallets), passing funds through various exchangers, cryptocurrencies or mixers. Mixer - transaction anonymization service. In practice, the technology of crushing customer funds into small parts and subsequent mixing with parts of other customers. The choice of mixers and exchangers, based on reviews and reputation.
(20:19:38) Payne: There are two types of cryptocurrency wallets: “hot” and “cold”. Hot - anyone who needs access to the Internet: exchanges, online wallets, exchangers. So, in fact, the funds are located on the servers, and the client only gets access to them? I recall the news about the loss of funds after hacking exchanges.
(20:20:07) Payne: Cold? The concept of local storage, which does not require constant access to the Internet. Despite the vulnerability of hot to hacking, they are convenient for frequent and small transactions, and the idea of cold is to safely store funds.
(20:20:47) Payne: Recommended Wallets:
• Bitcoin Core;
• Electrum;
• Blockchain.
It is worth emphasizing that dealing with cryptocurrencies leaves the probability of losing funds due to external factors: depreciation, hacking of the exchange, exchange fraud.
(20:21:18) Payne: In relation to fiat currencies (USD, EUR, RUB, UAH and so on) and operations from official exchanges, wallets or exchangers, the incognito behavior model is applied. The history of customer actions is preserved, so IP addresses, personal information and device fingerprints should not be involved in the financial turnover process.
(20:21:43) Payne: Instead, you can use:
? Virtual machines and SMS activation services.
(20:22:16) Payne: Wallets, exchanges, and credit card accounts for dummies (drops). They can block or steal, it’s better not to delay such funds and periodically replace them. The corresponding services for verifying accounts and selling cards are on the forum.
(20:22:46) Payne: Many exchangers conduct cash transactions. Courier services are suitable for both withdrawal and deposit.
? Terminals Entering pre-registered confidential wallets.
(20:23:08) Payne: An informal rule of cooperation with users in this field of activity? Guarantor Service. Saves nerve cells and finances.
(20:23:25) Payne: That's all. Optionally, a review of the lecture can be sent here.
We pass to questions, put "?".
(20:24:27) Serrwrtet: 1. What is the fingerprint of proxy services? How critical is using a Linux fingerprint proxy?
2. How critical is it to use socks without your own DNS?
(20:26:20) Payne: 1. Specifically, there is no such imprint. But in the name of the provider may appear the trigger word "proxy" or in a passive fingerprint. About both points was in a lecture, more attentively. Too critical - uncritical if the antifraud system is not from the breed of the toughest.
2. It is uncritical for the same reason, but in this case it should either not be determined at all, or not be Russian or similarly suspicious.
(20:26:31) bloomberg7:
1) what is the difference between tunnels and Soxes?
2) Is it true that the sphere burns with many antifrauds?
3) Does Anitfrod provide a site for Marchant?
4) A lot of user identification methods, how to deal with it and how to find out which what is the antifraud that pays attention to?
5) if you work with the logs, then you do not need to bathe with the settings, just copy everything that the victim has?
(20:29:12) Payne:
1. The fact that these are different connection protocols.
2. Depends on the settings of the sphere itself; I repeat, there will be a lecture on antidetects, and ask there
3. Shops can both write their own and rent a third-party one, there is no definite answer.
4. How to deal is described in the prints themselves and in the quote: “That's why camouflage is used to purposefully change the components of the prints: a device for User-Agent, browser plug-ins, fonts for the operating system - by this principle. Nevertheless, it’s important not to break fragile balance, too unique settings will lead to recognition. ", - I repeat, more carefully. Also, there are antidetects, various kinds of remote accesses, emulators and so on.
5. Well, the victim may not have all the necessary data, also, something may leak somewhere, so I would not call the approach after the sleeves acceptable.
(20:29:18) Rarka_: Where do I see DNS on the Sox or not and the second question is whether the macadress antifraud is burning
(20:29:45) Payne: 1. I gave a list of sites to check the characteristics
2. Through the browser - no
(20:30:00) id666: Payne: where is it better to buy a proxy? (price / quality ratio) and which type is better to use?
(20:30:35) Payne: SOCKS5. Material stores near the end of training will be in the main working conference
(20:31:18) macpru: What about contacting vendors from the forum thru telegram or jabber? Also best to use in virtual?
(20:32:06) Payne: Yes and yes. Jabber better. Telegram only on fake number, in virtual.
(20:32:55) id666: Payne: will there be a separate topic for logs?
(20:33:23) Payne: id666 Specify in the list of lectures in the topic of training, I do not make a schedule, I can not say)
(20:34:02) macpru: if one can always change virual within intervals of 6 months with the same system with every indentity change?
(20:34:13) macpru: or does it all rely on the system?
(20:34:20) ShadowConsult: will we touch on all of this from today's lecture in practice? When using a sphere, do you need a lot of settings, can you configure VPN and TP, or is it all generated in it?
(20:34:59) macpru: i meant will identity change as you change your virtuals?
(20:37:16) Payne: ShadowConsult and why not? With any drive, you will touch the fingerprints, depending on the antifraud system, somewhere more, somewhere less. As you gain experience and the number of maganizas, go through everything. Scope - browser, it does not generate IP-access as a VPN, and SOCKS / SSH.
macpru Didn't get your question. How to change fingerprints? By change their details, like system to USER-AGENT or fonts to system. There is some fingerprints, based on computer and system configuration, so just reinstall virtual machine won't always help. Idk try to ask again in other words.
(20:38:27) usbnet: I write again, for some reason the toad does not plow with the clipboard
(20:38:33) usbnet: wanted to copy
(20:38:52) macpru: I got the answer thank you.
(20:39:11) bloomberg7: how to find out which of the merchants in the shop and which of the merchants is the weaker antifraud, because they are somehow classified?
(20:39:33) bloomberg7: as I understand it through trial and error?
(20:40:34) usbnet: 1. regarding the encryption of the machine, are there any differences in performance if you use a separate removable drive and the main hard drive?
2. At the beginning, the moment was mentioned about not disclosing any personal information, and not storing the data. Did you mention this when working through a virtual machine? after all, working with the virtual machine will not cause any problems, and draining data from the main OS
(20:40:40) Payne: 1. In the future we’ll tell you, now the topic is to configure a virtual machine
2. At least the approximate stability of the antifraud system can be deduced purely logically: a ballpoint pen store will not have an Amazon antifraud system, like Amazon or any other world-famous store with thousands of purchases per day, it will not have an antifraud store with socks; more details - experience, of course.
(20:40:47) Payne: This is the answer of bloomberg7
(20:42:07) Payne: usbnet 1. If, for example, a removable SSD, and the main HDD - differences in speed. In short, it depends on the drives themselves, the principal ones do not.
2. It is always relevant in this field of activity. Outside of her, it’s a personal matter.
(20:42:20) id666: Payne: will we get detailed step-by-step instructions for setting up a working PC in the future, or will we have to shovel, think out and read everything ourselves?
(20:43:29) usbnet: 3. And which option is the best for encryption, in the main conference there are 4 encryption options, which is better to choose for someone who just at the beginning (at the moment I encrypted the main OS and the whole drive)
(20:43:47) net23: I have a virtual activation key asking where to get it?
(20:44:07) Payne: No need to think through anything, everything has already been voiced. But if this answer did not suit you, I will say this: we do not provide step-by-step instructions from the category "how to install a browser" or "how to install an operating system." Examine the information, understand the essence of the terminology - understand the principles of work. According to the functionality of some leadership programs, there is in the main working conference, the rest is just surfing, you can say.
(20:45:14) Payne: usbnet That at the moment is enough. The best, in my humble opinion, encrypted external drive.
net23 KMSAuto activator, for example.
(20:45:19) Rarka_: The question about ports was raised, I don’t really care where I look at them in ip
(20:45:38) Payne: Sites for checking the characteristics of the IP address and system were given in the lecture on them.
(20:46:16) stic_: Question about AudioContext Fingerprint, I haven’t heard about it before, so I’m wondering if you need to install Virtual Audio Cable ”or an analogue and on the basis of and on the virtual machine where will we drive it from?
(20:46:46) stic_: based on additional security when surfing, for example
(20:47:50) Payne: No, not to be fired, but to change. To put there - from where the network is connected, go out from the virtual - and put it on it. This is not the most popular fingerprinting system, so you should not go in cycles. And on the basis of security, an extension to the browser will be sufficient, generating a fingerprint at random.
(20:50:28) Kto-to: The sphere, as it were, separates the data from my computer and the data that is in the sphere
(20:51:40) Payne: It’s as if generating new, but the idea is in the right direction. The sphere is antidetect, now the lecture is not about that and in the future a whole lecture will be reserved for antidetects, more details there.
(20:51:57) Payne: Now I definitely say goodbye. All the best.