Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
The malicious downloader has received a new method of distribution and stealth.
Attackers have started using a new tactic to spread Latrodectus malware through phishing campaigns, disguising it as notifications from Microsoft Azure and Cloudflare. This mechanism makes it more difficult for mail security systems to detect malicious emails.
Latrodectus (Unidentified 111, IceNova) is a malware downloader that is used to download additional EXE and DLL files or execute commands. Latrodectus was analyzed by experts from ProofPoint and Team Cymru.
According to security researcher ProxyLife and the Cryptolaemus group, Latrodectus ' latest campaign uses a fake Cloudflare captcha to bypass security systems. Hackers start spreading through phishing emails with responses in the chain, where they insert malicious links or attachments into the correspondence.
Phishing emails contain PDF attachments or embedded URLs that start a chain of attacks leading to the installation of Latrodectus malware. When you click on the "Download document" button, users are taken to a fake security check page from Cloudflare, where they are asked to solve a simple mathematical problem. This method is designed to prevent anti-virus scanners from tracking the entire attack path, and malware is activated only for the real user.
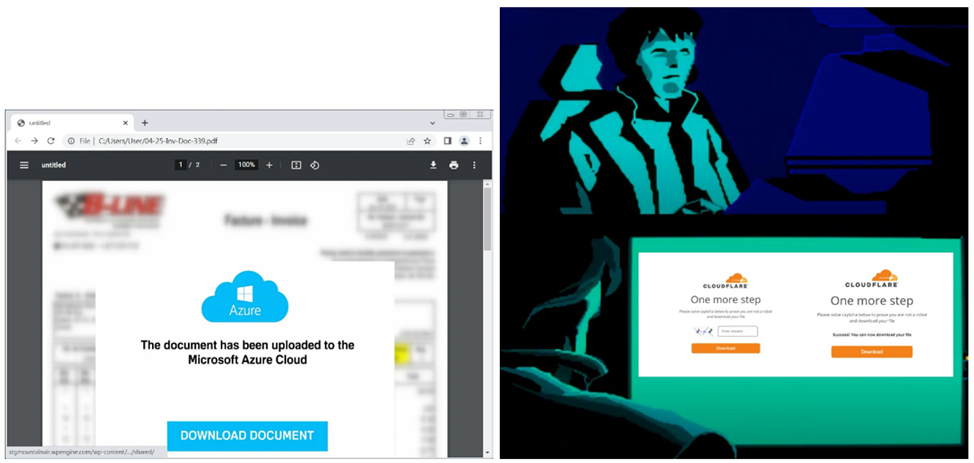
PDF document allegedly hosted in the Microsoft Azure cloud (left) and fake (right)
When you enter the correct answer, a JavaScript file is loaded that disguises itself as a document that contains obfuscated code. The code loads an MSI file from a hard-coded URL. After installing the MSI file, a DLL file is placed in the %AppData%\Custom_update folder, which is then activated via "rundll32.exe".
Latrodectus runs in the background, waiting for additional modules to be installed or commands to be executed. So far, Latrodectus has delivered Lumma and Danabot infostilers. Given that Latrodectus is linked to IcedID and is used for primary access to corporate networks, the infection may lead to a wider range of malware in the future, such as Cobalt Strike, and we may also see partnerships with ransomware groups.
In case of infection, it is important to immediately disconnect the affected device from the network and check the network for unusual activity.
Attackers have started using a new tactic to spread Latrodectus malware through phishing campaigns, disguising it as notifications from Microsoft Azure and Cloudflare. This mechanism makes it more difficult for mail security systems to detect malicious emails.
Latrodectus (Unidentified 111, IceNova) is a malware downloader that is used to download additional EXE and DLL files or execute commands. Latrodectus was analyzed by experts from ProofPoint and Team Cymru.
According to security researcher ProxyLife and the Cryptolaemus group, Latrodectus ' latest campaign uses a fake Cloudflare captcha to bypass security systems. Hackers start spreading through phishing emails with responses in the chain, where they insert malicious links or attachments into the correspondence.
Phishing emails contain PDF attachments or embedded URLs that start a chain of attacks leading to the installation of Latrodectus malware. When you click on the "Download document" button, users are taken to a fake security check page from Cloudflare, where they are asked to solve a simple mathematical problem. This method is designed to prevent anti-virus scanners from tracking the entire attack path, and malware is activated only for the real user.

PDF document allegedly hosted in the Microsoft Azure cloud (left) and fake (right)
When you enter the correct answer, a JavaScript file is loaded that disguises itself as a document that contains obfuscated code. The code loads an MSI file from a hard-coded URL. After installing the MSI file, a DLL file is placed in the %AppData%\Custom_update folder, which is then activated via "rundll32.exe".
Latrodectus runs in the background, waiting for additional modules to be installed or commands to be executed. So far, Latrodectus has delivered Lumma and Danabot infostilers. Given that Latrodectus is linked to IcedID and is used for primary access to corporate networks, the infection may lead to a wider range of malware in the future, such as Cobalt Strike, and we may also see partnerships with ransomware groups.
In case of infection, it is important to immediately disconnect the affected device from the network and check the network for unusual activity.

