Man
Professional
- Messages
- 3,222
- Reaction score
- 1,213
- Points
- 113
Many of you consider this OS to be almost the ideal of anonymity. Today I will disappoint you 
Salute to all, dear friends!
Lately I have been getting a lot of questions about Kodachi Linux. Based on your questions, it seems that for some reason you consider it to be an almost ideal way to maintain your anonymity. I hasten to disappoint you, this is NOT true.
Now I'll tell you why...
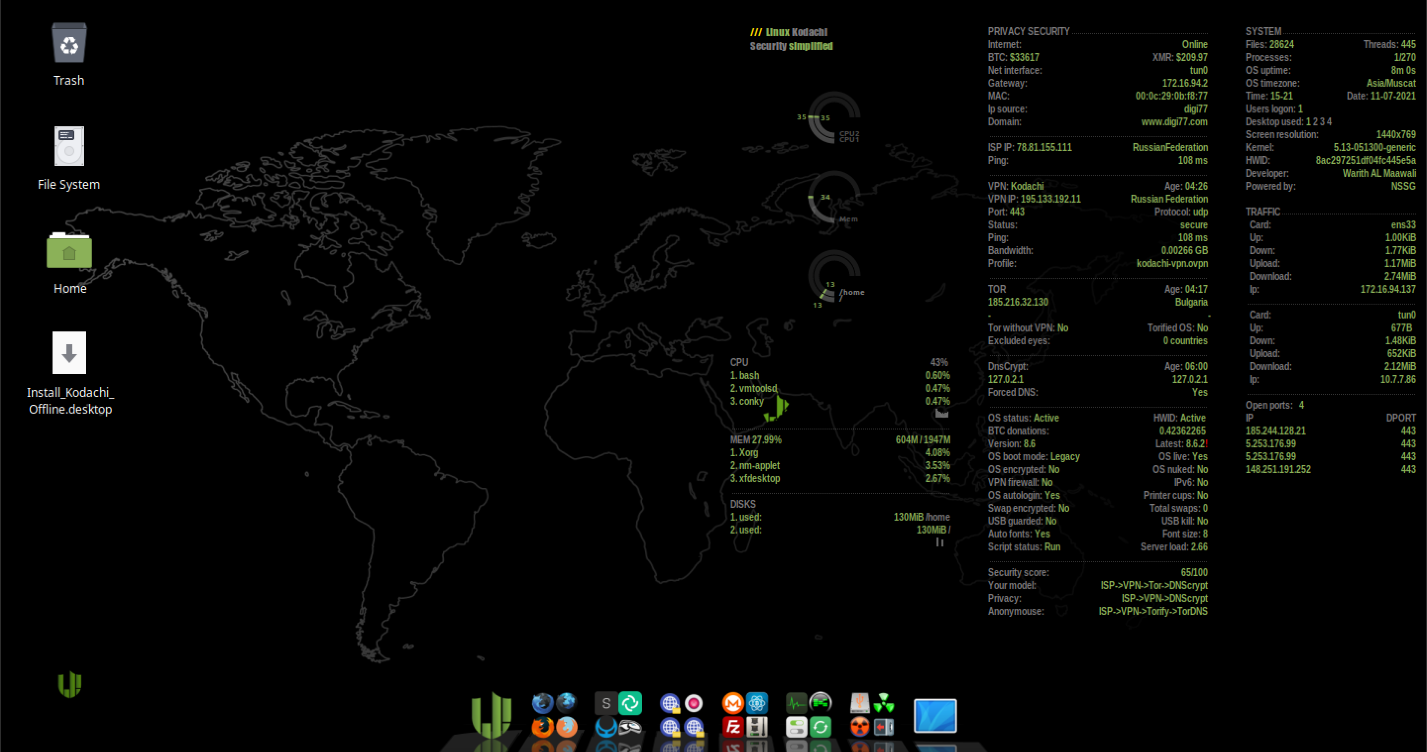
Here we are immediately greeted by the desktop with a bunch of shortcuts on the bottom panel and the Conca system monitor, which displays all active anonymization tools enabled on our machine. In general, there are no complaints about the conca itself, it is really a very convenient module for those who like to monitor all indicators.
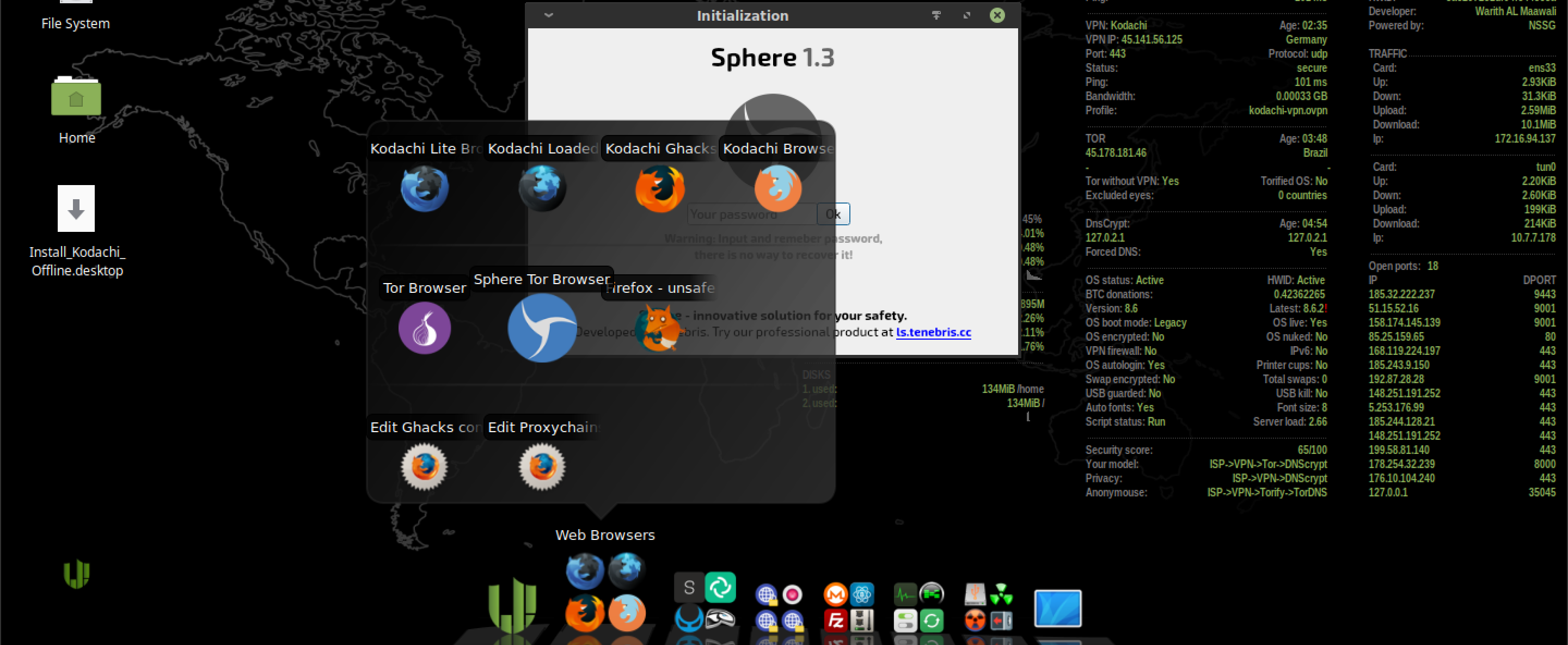
Below we have a huge number of integrated utilities, divided into categories. The first is browsers. And here I immediately want to spit in the face of the developers for having Sphere. For those who are not in the know - this is a pseudo-anonymous surfing tool, which is a proprietary development of people sitting on the ZPkh of uncles in uniform.
Well, screw it, the sphere. Next on the list we have the SecurityApps section. Here we have various utilities for working with crypto containers, passwords and encryption. Everyone's favorite MAT for clearing metadata and the Firetools sandbox.

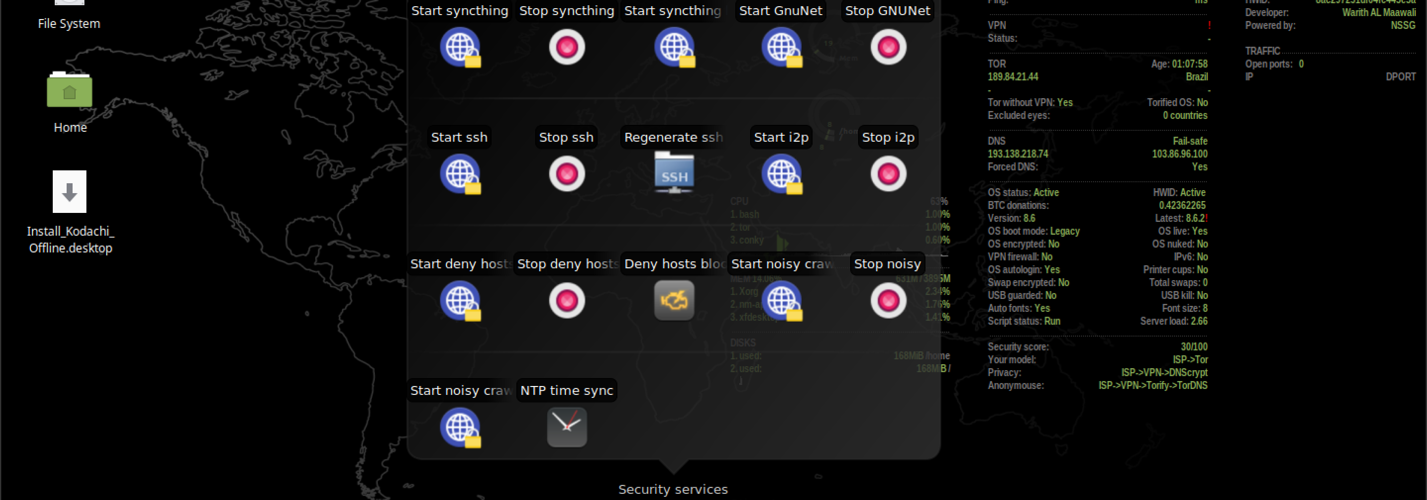
Security services include various Noisy variants for generating random DNS and HTTP requests, Synchating exchanger, utilities for connecting to i2p and GNU networks, and SSH scripts.
In "Miscellaneous" the developers have thrown in a hodgepodge of stuff from Libra to Filezilla. There is everything that might be useful to those who intend to use this system on a regular basis. Crypto storage, players, torrent client. However, it would be better to replace Terminator with Tilix.

By the way, since we're in the terminal, let's check if there are any open ports in the system by default.
We enter:
ss -tulpn
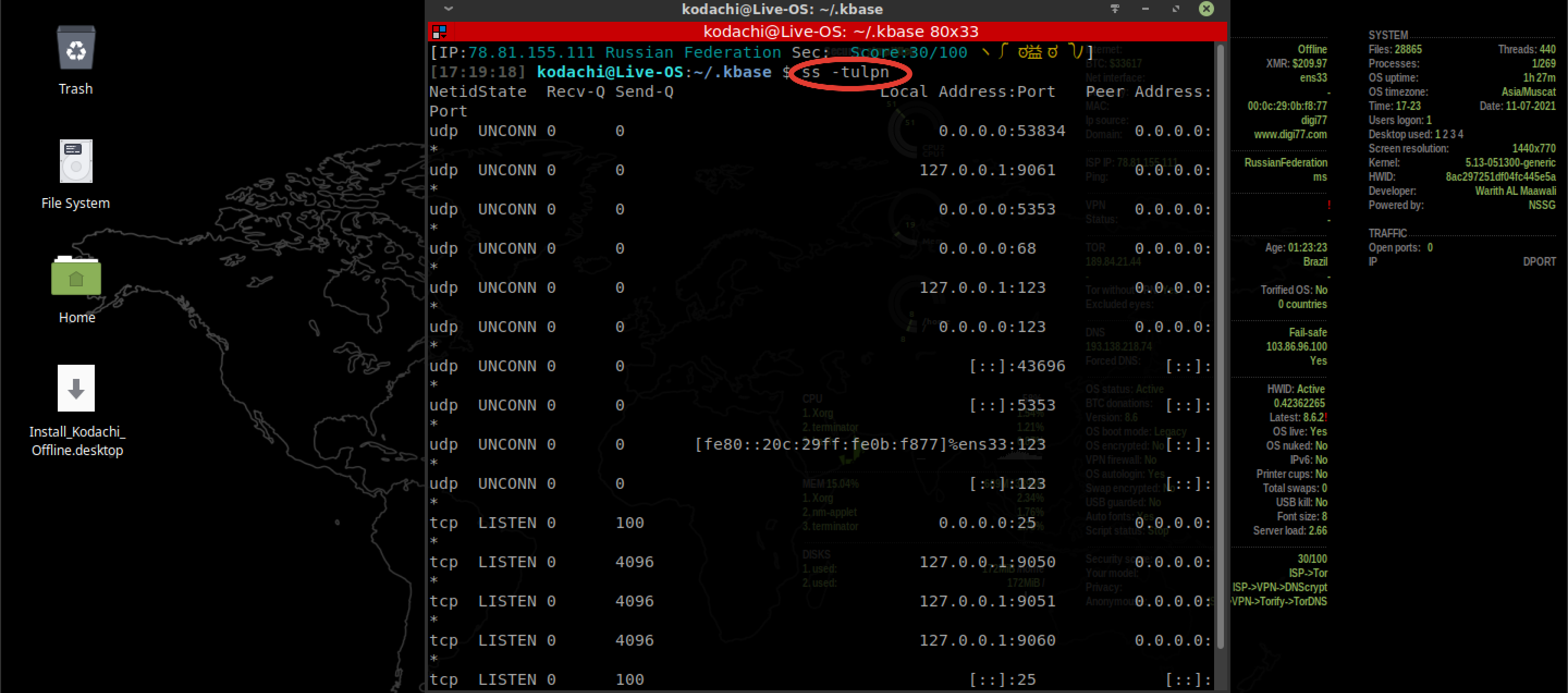
Um... What the hell is this, excuse me? Even if we discard the ones tapped on local IPs from the entire list, there are still quite a few potential holes.
And this is a security-oriented distribution? Well, well. Let's look at the state of ports open to everyone and everything in IP networks (i.e. those that hang on zero IP) without leaving the cash register.
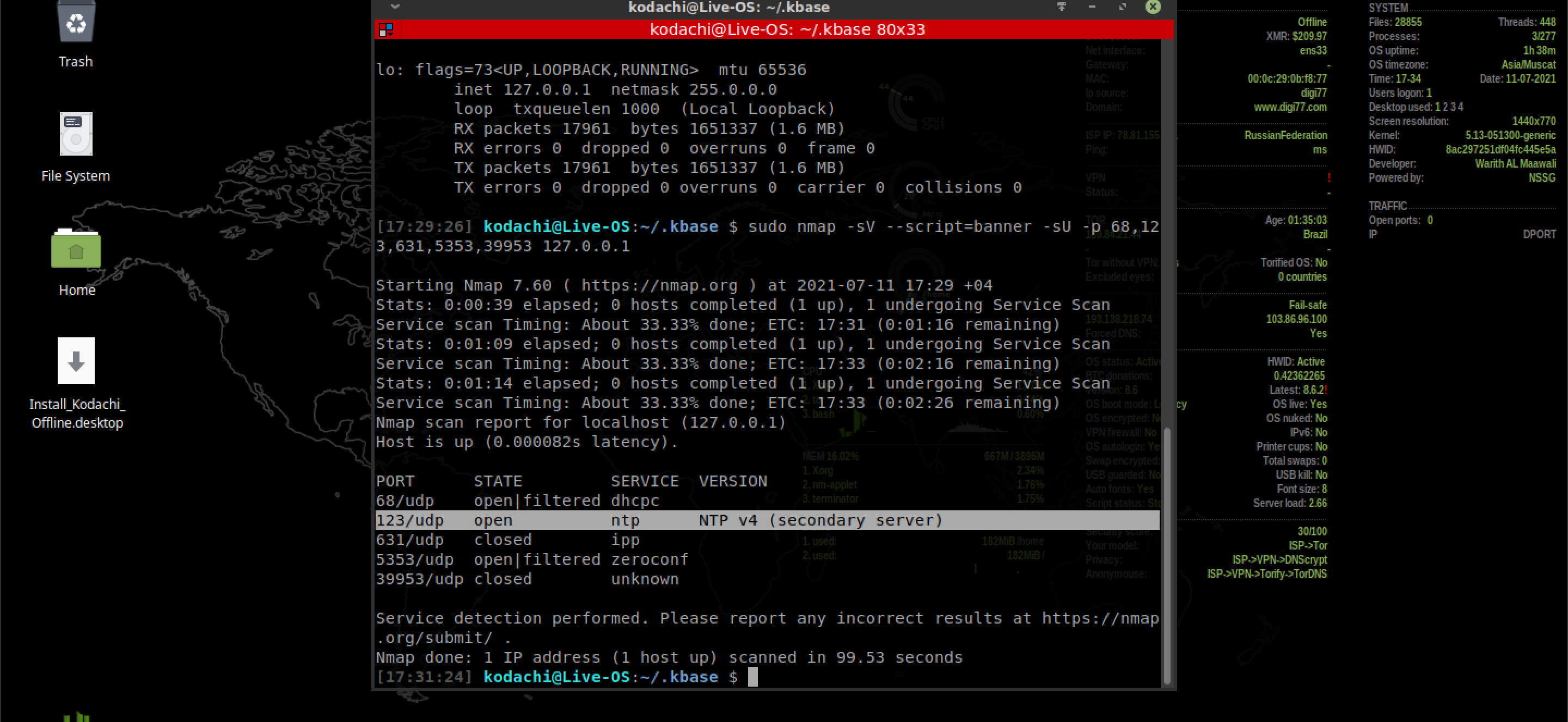
Yeah. Not only are the ports easily scanned, but one of them is open without any filtering. I think there's no need to explain why by default in any security-oriented distribution such holes should be completely closed?
Okay, I'll leave the terminal to be on the safe side. Let's go back to the panel. I missed the Kodachi dashboard shortcut. Let's see what we have here. Aha, this is where they hide the famous set of VPN services - Haidmi, Nord, Proton. I don't even know which of this list is the biggest embarrassment. Are there really people left in our time who fall for the age-old myth of the anonymity of VPN services? (I'm not talking about VPN servers that you set up yourself)
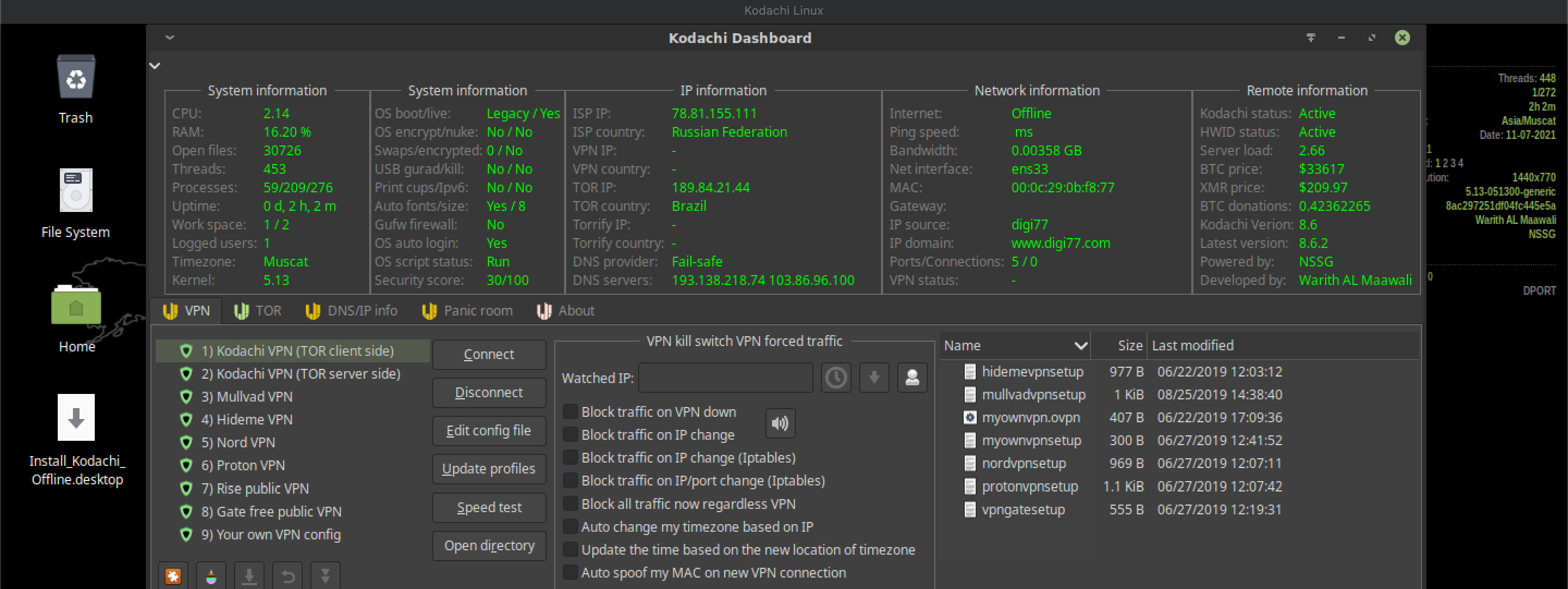
What is the FSB Sphere worth alone? In addition, the author himself has repeatedly stated that before loading, the OS collects a ton of metadata from the hardware. That is why it is recommended to use it on a virtual machine. But not on the open and free VirtualBox, because there it slows down terribly due to nasty optimization, but on a commercial version, which in turn is also wildly proprietary.
The author also strongly recommends using VPN services. Considering that VPNs are now spying on everyone and, as you already understood, do not provide the required level of anonymity, such a solution is also very questionable.
There is nothing to say about open ports. This is just an incredible mess. Even if you don't perceive it as a backdoor, it is obvious that the set of specific ports in itself instantly gives the attacker an idea of what OS you are working on.
And what are these ports used for? Personally, I don't understand. Just as I don't understand the choice of the kernel of the developers, who for some reason took Ubuntu as a basis.
This is a miserable piece of crap, stuffed to the brim with unnecessary shortcuts and reminiscent of a Windows XP-based beast on which someone's mother unknowingly installed Amigo.
And I won't even mention the mangled interface. How could they have done such a bad job of the shell in an attempt to make it look like Gnome? Because of all these bells and whistles, it's practically impossible to find a previously opened and minimized application.
This is truly a distribution that lives up to its name. For those who don't know, Kodachi is translated from Japanese as a small, short sword.Apparently as short as the developer's dick and as small as his alter ego.
Take care of yourself and your data, use proven Unix solutions, such as Whonix, and remember that the best operating system is the one you have configured and tweaked with your own hands, rather than entrusting this task to developers. After all, Linux is not Windows. And with some effort, you can make a virtually ideal anonymous distribution. The main thing is to have hands in the right place.
That's all for today. Thank you for your attention!
Salute to all, dear friends!
Lately I have been getting a lot of questions about Kodachi Linux. Based on your questions, it seems that for some reason you consider it to be an almost ideal way to maintain your anonymity. I hasten to disappoint you, this is NOT true.
Now I'll tell you why...
So, Kodachi Linux
Kodachi is one of the worst Linux distributions that humanity has ever seen. Literally everything is bad about it: from its resource-hungry nature and inappropriate amount of bugs to its ugly interface, which has a fair amount of proprietary software with closed source code under the hood, which in turn is especially amusing, considering how the developers boast about the highest degree of anonymity of this OS.- You can download the latest Kodachi Linux image from https://www.digi77.com .
- Don't be scared by the ugly domain, it's an official site

Therefore, we suggest doing without unnecessary preludes and immediately moving on to the Kodachi workspace, launching it in Live mode.The image can be installed on a virtual machine, a flash drive or an external HDD. We will not describe in detail the algorithm for installing and launching this OS. There are already enough instructions on the Internet in the style of low-intellectual clicking "Next-Next".

Here we are immediately greeted by the desktop with a bunch of shortcuts on the bottom panel and the Conca system monitor, which displays all active anonymization tools enabled on our machine. In general, there are no complaints about the conca itself, it is really a very convenient module for those who like to monitor all indicators.
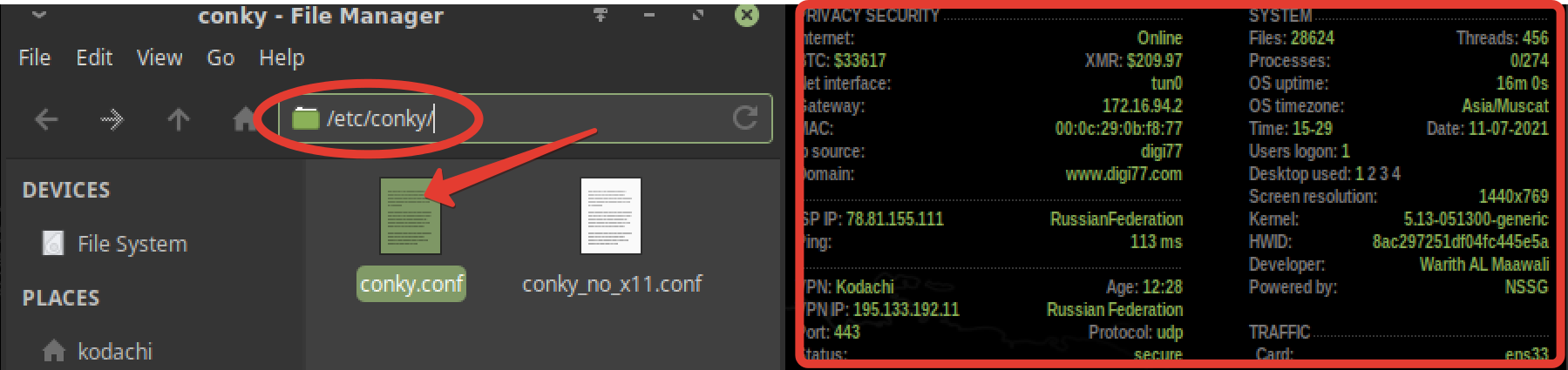
The config for detailed settings is located in /etc/.

Below we have a huge number of integrated utilities, divided into categories. The first is browsers. And here I immediately want to spit in the face of the developers for having Sphere. For those who are not in the know - this is a pseudo-anonymous surfing tool, which is a proprietary development of people sitting on the ZPkh of uncles in uniform.
And if we take into account the fact that the last update for this piece of crap was released in 2018 and users on the Internet write about problems with installing add-ons due to the lack of a timely update even on the paid version, the decision to integrate this product into the system immediately raises a number of specific questions.Advertisements of this G could be seen more than once on the vast expanses of such sales platforms as the magazine "Hacker" and Yandex.Zen. At one time, with its help, many seasoned carders and gray miners operating in the CIS and neighboring countries were put behind bars.

Well, screw it, the sphere. Next on the list we have the SecurityApps section. Here we have various utilities for working with crypto containers, passwords and encryption. Everyone's favorite MAT for clearing metadata and the Firetools sandbox.

Security services include various Noisy variants for generating random DNS and HTTP requests, Synchating exchanger, utilities for connecting to i2p and GNU networks, and SSH scripts.

In "Miscellaneous" the developers have thrown in a hodgepodge of stuff from Libra to Filezilla. There is everything that might be useful to those who intend to use this system on a regular basis. Crypto storage, players, torrent client. However, it would be better to replace Terminator with Tilix.

By the way, since we're in the terminal, let's check if there are any open ports in the system by default.
We enter:
ss -tulpn

Um... What the hell is this, excuse me? Even if we discard the ones tapped on local IPs from the entire list, there are still quite a few potential holes.
And this is a security-oriented distribution? Well, well. Let's look at the state of ports open to everyone and everything in IP networks (i.e. those that hang on zero IP) without leaving the cash register.

Yeah. Not only are the ports easily scanned, but one of them is open without any filtering. I think there's no need to explain why by default in any security-oriented distribution such holes should be completely closed?
Okay, I'll leave the terminal to be on the safe side. Let's go back to the panel. I missed the Kodachi dashboard shortcut. Let's see what we have here. Aha, this is where they hide the famous set of VPN services - Haidmi, Nord, Proton. I don't even know which of this list is the biggest embarrassment. Are there really people left in our time who fall for the age-old myth of the anonymity of VPN services? (I'm not talking about VPN servers that you set up yourself)
Kodachi by default uses its VPN servers, which are maintained by the developers of this OS. And therefore all user IDs are transferred directly to their good or not so good hands.Despite the fact that VPN itself is a very cool thing, great for creating virtual networks and encrypting traffic of a certain class, it is extremely poorly suited for anonymity. At least because you, as a user of the system, are assigned a unique identifier.

What conclusions can be drawn based on what we saw?
Well, first of all, it would be a stretch to call this system anonymous. It contains too much proprietary software with closed source code.What is the FSB Sphere worth alone? In addition, the author himself has repeatedly stated that before loading, the OS collects a ton of metadata from the hardware. That is why it is recommended to use it on a virtual machine. But not on the open and free VirtualBox, because there it slows down terribly due to nasty optimization, but on a commercial version, which in turn is also wildly proprietary.
The author also strongly recommends using VPN services. Considering that VPNs are now spying on everyone and, as you already understood, do not provide the required level of anonymity, such a solution is also very questionable.
There is nothing to say about open ports. This is just an incredible mess. Even if you don't perceive it as a backdoor, it is obvious that the set of specific ports in itself instantly gives the attacker an idea of what OS you are working on.
And what are these ports used for? Personally, I don't understand. Just as I don't understand the choice of the kernel of the developers, who for some reason took Ubuntu as a basis.
And I won't even mention the mangled interface. How could they have done such a bad job of the shell in an attempt to make it look like Gnome? Because of all these bells and whistles, it's practically impossible to find a previously opened and minimized application.
Conclusion
Overall, the feeling of working with the Kodachi operating system was, to put it mildly, not very good. Too many pseudo-safe show-offs that do not justify themselves in practice.This is truly a distribution that lives up to its name. For those who don't know, Kodachi is translated from Japanese as a small, short sword.
Take care of yourself and your data, use proven Unix solutions, such as Whonix, and remember that the best operating system is the one you have configured and tweaked with your own hands, rather than entrusting this task to developers. After all, Linux is not Windows. And with some effort, you can make a virtually ideal anonymous distribution. The main thing is to have hands in the right place.
That's all for today. Thank you for your attention!
