Tomcat
Professional
- Messages
- 2,689
- Reaction score
- 963
- Points
- 113

Money machines came into our lives in 1967, when the first ATM was installed in a Barclays bank branch in London. Currently, millions of people around the world use ATMs every day to withdraw cash, top up accounts, and pay for various services. People use ATMs without thinking about their hardware, software features or security. Unfortunately, ATM manufacturers and their direct consumers, banks, also pay insufficient attention to ATM security issues. This is confirmed by the increase in the number of cash thefts from ATMs using non-destructive methods - without the use of metal cutting tools and explosives.
To understand why this happens, let's first understand what an ATM is.
About hardware
An ATM is essentially a construction kit. The manufacturer completes it with a cash dispenser (dispenser), a card reader and other modules produced by various companies. The modules are placed in a housing, which usually consists of two parts - the upper one, called the cabinet or service area, and the lower one, the safe.In turn, the cabinet contains modules such as a system unit (yes, a regular system unit, sometimes even in the same case as a typical home computer), a cryptokeyboard (EPP or encrypted PIN-pad), a card reader, and so on. The service area contains everything that, in the opinion of the ATM manufacturer, makes it impossible to get to the money. Probably for this reason, the cabinet lid is plastic, and only a simple lock protects against unauthorized entry into the service area. By the way, both assembled locks and separate keys can be easily purchased on the Internet, since each manufacturer installs the same locks for their devices, and most banks, as a rule, do not think about replacing them with unique ones.
The safe is protected much better - it is a “sandwich” made of steel and concrete with two types of locks, a code (electronic or dial, sometimes electromechanical) and a key - usually lever. The safe contains devices directly related to money - a dispenser from which cash is dispensed, and a module for accepting cash.
All devices are connected to the system unit, which in this case acts as a host (as we will call it), via USB or RS232 ports (often called a COM port). Sometimes these ports are located directly on the system unit, and if there are not enough ports, a USB/COM splitter is used. On older ATM models, which, it must be said, can still be found, the connection method was used via the SDC bus.
About the software
The set of software that can be found in almost every ATM is simple:- operating system,
- Software for managing ATM modules,
- Software used to interact with the user (ATM client or operator),
- Software for communication with the processing center (which provides the information and technological aspects of the transaction),
- antivirus or software to monitor system integrity.
The vast majority of ATMs still use... Windows XP as their operating system! Despite the fact that Microsoft stopped releasing security updates for this OS in April 2014. Of course, all zero-day vulnerabilities for this system will remain unresolved. Engineers servicing ATMs often believe that if the ATM is working, then it is better not to touch it (read: not to update it). As a result, on some cache machines you can still find an unpatched critical vulnerability MS08-067, which allows remote code execution.
ATM modules are implemented on microcontrollers with real-time operating systems (RTOS), which is especially sad for the guys with IDA Pro, since static analysis is poorly applicable to such systems.
Well, this information is, in principle, enough for attackers to start hacking.
About malware
In 2009, the ATM world was rocked by the appearance of the Backdoor.Win32.Skimer Trojan: it was the first malware to target ATMs. Skimer attacked ATMs of a specific manufacturer - one of the market leaders. Using the malware, the attackers emptied the dispenser and also obtained data from plastic cards processed at the infected ATM. Since then, ATMs from different manufacturers have been repeatedly exposed to malware.In a scheme to steal money from ATMs using malware, there are four fundamental stages:
- The attacker gains access to the machine, local or remote.
- Malicious code is injected into the ATM system.
- Typically, an infection is followed by a reboot of the ATM. The system reboots, seemingly into normal mode, but at the same time finds itself under the control of a malicious program, i.e. intruders.
- The final stage, i.e. The purpose of the whole action is the theft of money.
We will focus on how malware can take over an ATM.
About the XFS standard
So, the attackers infected the ATM system unit. What's next?Here again a little clarification is needed. As already mentioned, the ATM is controlled by a Windows-based software application. In general, its task comes down to organizing the interaction of the user (client or service personnel) with the processing center, which sends commands to the ATM, and the equipment that executes these commands. Messages are exchanged with the processing center using direct connect protocols (NDC or DDC), users get to communicate with the GUI, and the corresponding service providers (a kind of gateways to these modules) are responsible for the operation of each ATM module. To broadcast commands to service providers and further to equipment, as well as to return status messages, a layer called XFS Manager is used - according to the WOSA concept .
XFS (CEN/XFS, and formerly WOSA/XFS), or eXtensions for Financial Services, is a standard that provides a client-server architecture for interfacing Windows-based financial applications with devices, particularly ATMs. The standard is aimed at unifying the operation of software with any equipment, regardless of manufacturer, and provides a common API for this purpose.
Thus, any application developed taking into account the XFS standard can manage low-level objects using only the logic described in this standard. And this application could very well be a Tyupkin backdoor or any other malicious program.
What features does XFS provide?
For example, a dispenser, the most interesting device for attackers, can dispense money without any authorization. And in some ATM models, using XFS you can programmatically open the safe and unlock the cassettes.
An example of exploitation of the MS08_067 vulnerability, which allows the execution of arbitrary code.
The video was demonstrated by experts at BlackHat Europe 2014
When applied to a card reader, XFS allows you to read and write magnetic stripe data on a bank card and even retrieve the transaction history stored on the EMV card chip.
It is impossible not to mention the cryptokeyboard – Encrypted PIN-pad (EPP). It is believed that the PIN code cannot be intercepted because it is entered on the ATM pin pad and directly inside the encryption module it turns into a PIN block (for this, the EPP cryptokeyboard contains keys, the pair for which is located in the bank’s hardware security module). However, XFS allows us to use the pin pad in two modes:
- open - for entering various numerical values, for example, the amount that needs to be issued;
- protected (safe), into which the EPP cryptokeyboard switches to enter the PIN code and encryption keys.
What about authentication and exclusive access? And you probably won’t be able to get specifications for the standard?
Unfortunately, this is not about XFS. This standard does not provide for any authentication, and exclusive access to service providers is implemented, but not for the sake of security. This is just a function of single-threaded command sending, so as not to accidentally break a delicate piece of hardware by sending two identical commands in parallel.
Do you understand, right? A standard for financial applications, it would seem, but there is nothing about security in it. Where can I get the specifications to verify this? In any search engine for the query “ATM XFS” the desired result will be one of the first in the search results.
About integrity controls
Some banks sometimes use integrity monitoring software on their ATMs that promise to prevent the execution of unauthorized code based on an approved list, control device and drive connections, as well as other theoretically useful methods of countering attacks.But we should not forget that this is, first of all, software, and, like any other software, it is not perfect. It may be vulnerable to attacks such as kiosk traversal (bypassing the full-screen restriction and gaining access to the operating system), allowlist traversal, buffer overflow, privilege escalation to SYSTEM user level, and others. As you understand, existing vulnerabilities often allow villains to gain access to the operating system and do their dirty deeds.
About undocumented features
Bad guys can also use modified utilities originally provided by ATM developers or manufacturers to check the functionality of the devices. One of the functions of such utilities is testing the operation of the dispenser, including the dispensing of banknotes. To conduct such a test, the engineer needs to confirm his legitimacy by opening the safe door or somehow manipulating the dispenser cassettes. The logic is simple - if you can open the safe, then you have the key, i.e. you are a licensed engineer or collector. But replacing a couple of bytes in the utility with the “correct” ones allows you to “test” the output without any checks.Another way to get rich is to change the denomination of issued banknotes, again using a diagnostic utility. As a result, the attacker receives money from the cassette with the highest denomination (for example, 100 dollars or euros), and the ATM software thinks that it is dispensing the smallest denomination available (fives or tens). Thus, on a card with a balance of several hundred, you can get several thousand.
About black box attacks
Another type of attack that is increasingly being covered in news feeds is the so-called black box attack. On video recordings of surveillance systems, it looks like this: the attacker opens the service area, connects his magic box to the ATM, closes the office and leaves. A little later, people who look like customers come to the ATM and get a lot of money from the ATM, a lot. Of course, attackers do not abandon their useful device; they are sure to take it away after the goal is achieved. The result is revealed, as a rule, after a few days: bank employees, seeing empty cassettes and logs that do not contain relevant records, clutch their heads in an attempt to understand what happened.But there is no magic in this - by connecting a specially programmed microcomputer to the dispenser instead of the host, attackers bypass any security measures implemented on the host - antiviruses, integrity monitoring tools, including full disk encryption, etc.
About the insecurity of communications
As mentioned above, USB, RS232 or SDC can be used as a data transfer channel between the system unit and devices. Perhaps nothing will stop attackers from sending the necessary commands directly to the device port, bypassing its service provider. The interfaces are standard; often no specific drivers are needed for them. There is also no authorization involved, which essentially makes these insecure proprietary protocols easy pickings - just listen and repeat. The result is direct control of ATM modules, the use of undocumented capabilities (for example, by changing the modules’ firmware for this purpose). In addition, attackers can use a software or hardware traffic analyzer by installing it directly on the port of a device of interest, for example, a card reader, in order to obtain transmitted data. And such an analyzer will be quite difficult to detect.Direct control of the dispenser allows you to empty the ATM cassettes, while there will be no entries in the logs maintained by the ATM software.

Typical packet - a command to dispense one banknote from the first dispenser cassette
To the uninitiated, it looks like magic. In this magic, as in every trick, there are three acts, or actions: collecting money from a cassette, opening the shutter (the curtain from behind which the money “peeks out”) and presenting the money to the client.
Hardware skimmers are a thing of the past. A direct connection allows you to read and write the magnetic stripe of a bank card. As a direct connection, you can also use ready-made software traffic analyzers, which are easy to find on the Internet. As one of my acquaintances told me, in one rather large bank all ATMs were used as skimmers - the attackers, having discovered a vulnerability in the bank’s network, installed a USB sniffer utility on the ATMs, with which they collected all plastic card data in clear text for five years! Who knows, maybe your card has been there too.
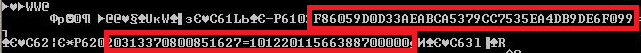
Intercepted Track2 card data
About the network
The connection between ATMs and the processing center can be secured in various ways. For example, using hardware or software VPN, or using SSL/TLS encryption, through firewalling, as well as MAC authentication implemented in xDC protocols. However, all these measures sometimes seem so complicated to banks that no network protection is used at all.In such cases, an attacker can carry out a “man in the middle” attack, as a result of which both the bank card data and all the money from the ATM will be in his hands. To implement this, remote access to the device is required. It is obtained, as a rule, using any vulnerable services accessible from the Internet, as well as social engineering tools. Physical access to network equipment, including the ATM's Ethernet cable, will also work.
On the way to the real processing center, a fake one appears, which sends commands to the ATM software to issue banknotes. Moreover, you can withdraw money using any card, even an expired one with a zero balance, the main thing is that the fake processing “knows” it. Both a homemade product that supports communication with an ATM using xDC protocols, and simulators of processing centers, originally intended to check network settings (another “gift” to the villains from the vendor), can be used as a fake processing center.
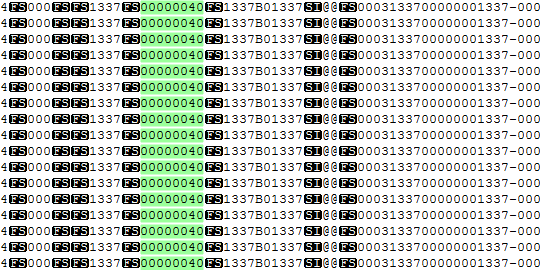
Commands to dispense 40 banknotes from the fourth cassette, sent from counterfeit processing and stored in the ATM software logs. Looks almost real
Where do attackers find ATMs that can be attacked through the network? Do they scan all the networks around them or buy information on underground forums?
It turns out that you can simply write the correct query to the search engine www.shodan.io (this Internet of Things scanner is well known to experts). The data collected by this scanner is usually sufficient for such attacks.
Or you can simply carefully examine ATMs in shopping and office centers.

Sometimes, to access the ATM system you don’t even need to open it - communications are located outside
Who is to blame and what to do
This part is usually the saddest, and here's why.When we discover vulnerabilities in the process of analyzing the security of ATMs, we, of course, send a notification to the vendor describing the shortcomings and how to eliminate them. And often the answers are puzzling:
“The vulnerabilities are essentially normal specifications of the card readers and not unexpected. As long as the ATM is running within normal parameters, these problems cannot possibly occur .”
(Translation: “The vulnerabilities relate to standard technical parameters of card readers and are not unexpected. As long as the ATM operates within standard parameters, such problems cannot occur.”)
"However this vulnerability is inherent in the USB technology and is expected to be mitigated by the use of appropriate physical controls on access to the ATM top box."
(Translation: “However, this vulnerability is inherent to USB technology and should be mitigated by implementing appropriate measures to physically restrict access to the top compartment of the ATM.”)
“We regret informing you that we had decided to stop producing this model more than 3 years ago and warranties for our distributors have been expired.”
(Translation: "We regret to inform you that we decided to discontinue production of this model more than 3 years ago and the warranty for our distributors has expired.")
Indeed, why should vendors be concerned that out-of-warranty ATMs are still in use by banks around the world, and their physical security often leaves much to be desired? Unfortunately, the reality is that manufacturers are only interested in selling new products, but not in eliminating shortcomings in existing systems, and banks are not able to cope with current problems on their own due to the lack of necessary competencies.
Fortunately, some manufacturers understand the dangers of unauthorized use of ATMs and are releasing security updates. Two-way authentication and cryptography are used as measures to counter attacks on the dispenser (but it should be remembered that not all cryptography is properly implemented cryptography).
However, as reality shows, existing compensation measures can protect an ATM from malware, but they are powerless against black boxes or network attacks. A huge number of security flaws and vulnerabilities, the exploitation of which does not require any specific knowledge, makes money machines a desirable target for those seeking illicit enrichment.
There is an exit
However, ATM manufacturers can reduce the risk of attacks on ATMs.- First, the XFS standard should be revised with an emphasis on security, and two-way authentication between devices and legitimate software should be introduced, which will reduce the likelihood of unauthorized withdrawal of money using Trojans and direct control of ATM modules by attackers.
- Secondly, it is necessary to implement “trusted issuance” to eliminate the possibility of attacks involving the spoofing of the processing center.
- Thirdly, it is necessary to implement cryptographic protection and check the integrity of transmitted data between all ATM devices.
Force those who sell ATMs and software to make them secure. Vulnerabilities must be eliminated by the manufacturer as soon as possible, and they must be informed about this more often. To counteract ATM hacking, it is necessary to activate all available security measures. A completed PCI DSS self-check sheet is not a silver bullet and will certainly not protect ATMs from attacks, or the bank from financial and reputational losses. Proactive protection, including regular ATM security analysis and penetration testing, is better (and often significantly cheaper) than incidents and their investigations.
Remember, the enemy does not sleep.
All the best to you and your safety!
PS: No ATMs were damaged during the preparation of this text.
PPS: A review of financial device security issues is not a tutorial.
