Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,494
- Points
- 113
34 companies in critical industries were supported by the Sponsor.
Researchers from ESET have discovered a new campaign of the hacker group Charming Kitten (Phosphorus, TA453, APT35, APT42). During the campaign, which lasted from March 2021 to June 2022, 34 organizations in various countries were attacked. Hackers used previously unknown malware called "Sponsor".
Features of Malicious Sponsor Code
Sponsor is a backdoor written in C++ that, once launched, creates a service managed by a configuration file. The file contains the encrypted addresses of the C2 servers, their communication intervals, and the RC4 decryption key. One notable feature is Sponsor's ability to hide its configuration files on the victim's disk, allowing it to successfully evade detection.
Goals and methods of attack
Among the main goals are organizations in the areas of public administration, healthcare, financial services, engineering, manufacturing, technology, law, and telecommunications. Organizations in Israel, Brazil, and the United Arab Emirates were most actively attacked.
For initial access to the target networks, hackers exploited the CVE-2021-26855 vulnerability in Microsoft Exchange. Then, various open-source tools were used to further infiltrate and exfiltrate data, which facilitate data theft, system monitoring, and network penetration, as well as help attackers maintain access to compromised computers.
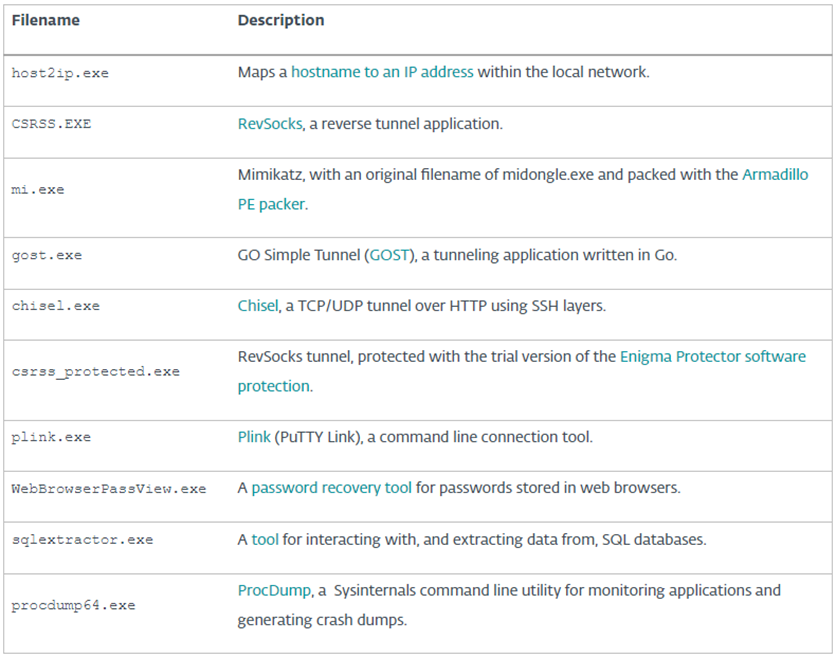
Open source tools used in the Charming Kitten campaign
Before installing Sponsor, hackers placed packages of files on the victim's computer, which recorded the necessary configuration files with names like config.txt, node.txt and error.txt to mix them with regular files and avoid arousing suspicion.
Supported commands and versions
Sponsor is capable of executing a number of commands, including sending a process ID, executing specific commands on the host, and communicating with the management server. ESET experts also discovered a second version of Sponsor with an additional layer of masking, which makes the version look like a standard update tool.
Prevention and security measures
Although the IP addresses used in this campaign are no longer active, ESET has shared complete indicators of Compromise (IoC) to help protect against possible future threats that may use some of the tools or infrastructure involved in this campaign. The detected campaign is a reminder of the need for constant monitoring and updating of security systems, especially for organizations working in critical areas.
Researchers from ESET have discovered a new campaign of the hacker group Charming Kitten (Phosphorus, TA453, APT35, APT42). During the campaign, which lasted from March 2021 to June 2022, 34 organizations in various countries were attacked. Hackers used previously unknown malware called "Sponsor".
Features of Malicious Sponsor Code
Sponsor is a backdoor written in C++ that, once launched, creates a service managed by a configuration file. The file contains the encrypted addresses of the C2 servers, their communication intervals, and the RC4 decryption key. One notable feature is Sponsor's ability to hide its configuration files on the victim's disk, allowing it to successfully evade detection.
Goals and methods of attack
Among the main goals are organizations in the areas of public administration, healthcare, financial services, engineering, manufacturing, technology, law, and telecommunications. Organizations in Israel, Brazil, and the United Arab Emirates were most actively attacked.
For initial access to the target networks, hackers exploited the CVE-2021-26855 vulnerability in Microsoft Exchange. Then, various open-source tools were used to further infiltrate and exfiltrate data, which facilitate data theft, system monitoring, and network penetration, as well as help attackers maintain access to compromised computers.

Open source tools used in the Charming Kitten campaign
Before installing Sponsor, hackers placed packages of files on the victim's computer, which recorded the necessary configuration files with names like config.txt, node.txt and error.txt to mix them with regular files and avoid arousing suspicion.
Supported commands and versions
Sponsor is capable of executing a number of commands, including sending a process ID, executing specific commands on the host, and communicating with the management server. ESET experts also discovered a second version of Sponsor with an additional layer of masking, which makes the version look like a standard update tool.
Prevention and security measures
Although the IP addresses used in this campaign are no longer active, ESET has shared complete indicators of Compromise (IoC) to help protect against possible future threats that may use some of the tools or infrastructure involved in this campaign. The detected campaign is a reminder of the need for constant monitoring and updating of security systems, especially for organizations working in critical areas.

