Detailed Analysis of Your JCOP Card Issue
Your card's
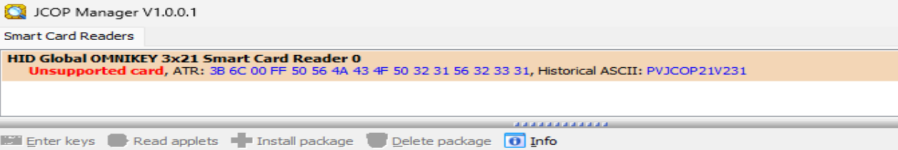
ATR (3B 66 00 FF 50 56 44 43 4F 50 32 31 56 32 33 31) with historical bytes
PVJCOP21V231 is
completely valid and correct for what the card actually is: an older-generation NXP JCOP card running
JCOP v2.3.1 (specifically a variant of the discontinued JCOP21 series, often with ~36K EEPROM). This is
not a defect, fake, or "wrong" ATR — it's the factory/default identifier for that OS version. The card is accurately reporting its identity.
The problem is purely a
tool compatibility mismatch:
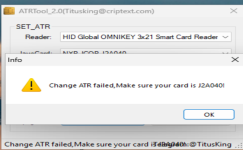
- Tools like JCOP Manager v1.0.0.1 (an older, unofficial/community tool) and ATRTool 2.0 (often bundled with scripts for JCOP personalization) were designed primarily for newer JCOP versions on the J2Axxx chip family (e.g., J2A040 with JCOP v2.4.1 or v2.4.2, 40K EEPROM).
- These tools perform internal checks for specific identifiers (chip type, OS version, or pre-personalization flags) tied to J2A040/JCOP 2.4.x. When they detect an older JCOP21 v2.3.x, they flag it as "unsupported" and refuse operations like ATR modification.
- The explicit error "Change ATR failed. Make sure your card is J2A040!" is a hard-coded check in ATRTool — it literally verifies for J2A040 compatibility before allowing changes.
Why This Happens Even with "Reputable" Sellers Like Bodno
The JCOP21-36K series (older chips) was officially discontinued by NXP years ago. The intended replacement is the
J2A040 (40K EEPROM, JCOP v2.4.x OS on SmartMX hardware), marketed as a drop-in upgrade with better crypto accelerators, more memory, and full compatibility with modern tools.
However, in the retail market (Amazon, AliExpress, Mercado Livre, etc.):
- Many sellers (including well-rated ones like Bodno) label cards as "J2A040 Chip Java JCOP Cards" or "JCOP21-40K replacement for discontinued JCOP21-36K."
- In reality, a significant portion of these are rebranded older JCOP21 stock (v2.3.x, ~36K EEPROM) or Chinese-compatible clones running similar but not identical COS (Card Operating System).
- This is common because old stock is cheaper to source, and the cards are functionally similar for basic Java Card applet use. But they differ in:
- Internal OS commands for personalization (e.g., ATR changes require vendor-specific APDUs that vary by version).
- Default ATR historical bytes (older: "PVJCOP21Vxxx"; newer J2A040: often "JCOP v241" or customizable like "JCOP76j2r3").
- Tool support (newer versions have proprietary extensions for easy ATR/init via tools like ATRTool).
Customer reviews on similar listings frequently report the exact same "unsupported card" or failed ATR change issues, even from high-rated sellers. Your card from Bodno matches this pattern perfectly.
Key Differences: JCOP21 v2.3.1 vs. True J2A040 (JCOP v2.4.x)
| Feature | Your Card (JCOP21 v2.3.1 / PVJCOP21V231) | True J2A040 (JCOP v2.4.1/v2.4.2) |
|---|
| EEPROM Size | Typically ~36K | 40K |
| Java Card Version | 2.2.x | 2.2.2 or 3.0.x |
| GlobalPlatform | 2.1.1 or earlier | 2.2.1+ |
| Default ATR Historical | "PVJCOP21V231" (or similar v2.3) | Customizable, e.g., "JCOP v241" |
| Crypto Support | Basic DES/RSA, optional AES/ECC | Enhanced coprocessor (faster AES/ECC) |
| ATR Change Ease | Limited/vendor-specific, often locked | Easy via tools or APDU scripts |
| Tool Compatibility | Older/generic tools only | Full support in ATRTool, JCOP Manager, etc. |
| Status | Discontinued, leftover stock/clones | Official replacement (though now also phasing to J3xxx) |
Your card works fine as a generic Java Card but lacks the specific internal hooks that ATRTool/JCOP Manager expect for J2A040.
Can You Change the ATR on Your Card?
- Probably not easily (or at all) with your current tools/setup.
- On older JCOP21 versions, full ATR modification (beyond historical bytes) is often restricted to pre-personalization phase or requires proprietary NXP APDU commands that aren't exposed in public tools.
- Even historical bytes changes may fail if the card is already "fused" or locked.
- True J2A040 cards allow reliable ATR changes via:
- ATRTool scripts.
- Direct APDUs (e.g., vendor-specific like C0 D6 01 37 ... for cold reset historical bytes).
- GlobalPlatform API calls from a privileged applet.
Recommendations and Alternatives
- If you need ATR changes or easy tool support:
- Return the card if possible and buy from sellers who explicitly confirm true J2A040/JCOP v2.4.x (look for listings mentioning "original NXP chip," "JCOP v2.4.1," or providing sample ATR like 3B F8 ... JCOP76j2r3).
- Newer replacements: Look for JCOP4 J3Rxxx or J3A/J3H series (80K–180K, Java Card 3.0.5, fully customizable ATR).
- Work with your current card(it's still usable!):
- Use generic Java Card toolsthat don't rely on JCOP-specific checks:
- GlobalPlatformPro (GPP): Free, open-source (github.com/martinpaljak/GlobalPlatformPro). Supports applet install/delete on most JCOP versions via standard GlobalPlatform commands.
- pyApduTool or jcardsim (for simulation).
- NXP's official JCOP Tools (if you can obtain them via NXP developer program — requires registration).
- For basic operations: Authenticate with default transport keys (often 404142...4F or seller-provided), then install applets manually.
- ATR changes: Unlikely without custom scripts — try community forums like javacardos.com for v2.3.1-specific APDUs.
In summary, your card is
genuine but outdated — not defective. The error is expected behavior from tools built for the newer replacement chips that sellers often mislabel. If your project requires specific ATR emulation or seamless tool use, source a verified modern JCOP variant. Otherwise, switch to more flexible tools and proceed! If you share more details (e.g., what you're trying to achieve with the card), I can suggest specific commands or alternatives.