Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,096
- Points
- 113
Experts described the large-scale structure of Kim Jong-un's cyber army.
Palo Alto Networks, in a new report, described the activities of hacker groups associated with North Korean intelligence. The groups, which are often referred to as Lazarus in public reports, work on behalf of the DPRK government, engaging in cyberespionage, financial crimes, and devastating attacks on industries around the world.
RGB is a structure made up of several divisions, each with its own goals and specializations. To date, six key groups have been identified:
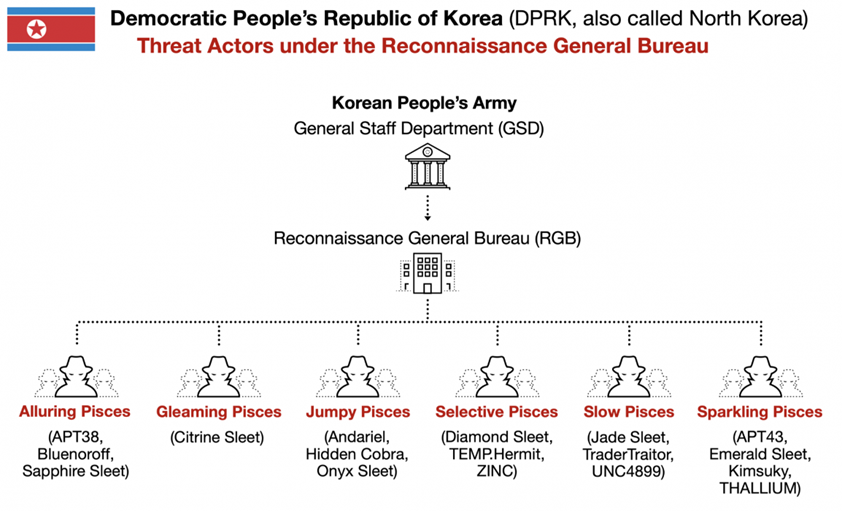
Organizational chart of North Korean groups within RGB
The report also includes an analysis of 10 newly discovered malware families developed by North Korean groups. Targeting Windows, macOS, and Linux, these programs are used for various types of attacks, such as collecting information, hacking corporate networks, and spreading ransomware.
The report also describes malware such as RustBucket, KANDYKORN, SmoothOperator, ObjCShellz, and Fullhouse. Malware covers a wide range of functions, from covert penetration of systems to data theft and management of infected devices.
One of the most notable programs is RustBucket, a multi-stage macOS malware discovered in 2023. The steps involve loading and executing multiple components, making it difficult to detect and remove. KANDYKORN is another example of a sophisticated, multi-stage attack that begins with social engineering, where the victim is tricked into running a malicious script disguised as a normal file.
Also highlighted was the SmoothOperator program, which, according to the researchers, was used to attack customers of the popular 3CX application. The malware was embedded in installation files and collected data from infected devices.
The researchers emphasize that groups controlled by RGB became known thanks to high-profile incidents such as the attack on Sony Pictures in 2014, the global WannaCry epidemic in 2017, and numerous attacks on cryptocurrency exchanges. The activities of hackers from the DPRK have been going on since 2007 and cover many industries and regions around the world.
Due to the scale and complexity of the activities of North Korean groups, in 2024 they were included in the annual MITRE ATT&CK security assessment, which analyzes their methods, tactics and the software used. Palo Alto Networks, in turn, continues to develop and improve solutions aimed at protecting companies from threats posed by these hacker groups.
The report highlights the need for a comprehensive approach to protecting organizations to minimize the risks associated with the activities of state-owned hackers, such as North Korean groups running RGB.
Source
Palo Alto Networks, in a new report, described the activities of hacker groups associated with North Korean intelligence. The groups, which are often referred to as Lazarus in public reports, work on behalf of the DPRK government, engaging in cyberespionage, financial crimes, and devastating attacks on industries around the world.
RGB is a structure made up of several divisions, each with its own goals and specializations. To date, six key groups have been identified:
- Alluring Pisces (also known as Bluenoroff) specializes in attacks on financial institutions, cryptocurrency companies, and ATMs. It is this group that is responsible for major cyber robberies.
- Gleaming Pisces (Citrine Sleet) – Attacks cryptocurrency companies and is linked to the AppleJeus campaign, which distributed fake cryptocurrency apps.
- Jumpy Pisces (Andariel) focuses on cyberespionage, but is also known for conducting ransomware attacks.
- Selective Pisces (TEMP. Hermit is aimed at media, defense and IT companies, engaged in both espionage and attacks on networks in order to destroy or compromise them.
- Slow Pisces (TraderTraitor) – known for attacks on blockchain companies and participation in supply chains, distributes malicious applications such as TraderTraitor.
- Sparkling Pisces (Kimsuky) - The main activity of this group is intelligence gathering, while funding their operations is carried out through cybercrime.

Organizational chart of North Korean groups within RGB
The report also includes an analysis of 10 newly discovered malware families developed by North Korean groups. Targeting Windows, macOS, and Linux, these programs are used for various types of attacks, such as collecting information, hacking corporate networks, and spreading ransomware.
The report also describes malware such as RustBucket, KANDYKORN, SmoothOperator, ObjCShellz, and Fullhouse. Malware covers a wide range of functions, from covert penetration of systems to data theft and management of infected devices.
One of the most notable programs is RustBucket, a multi-stage macOS malware discovered in 2023. The steps involve loading and executing multiple components, making it difficult to detect and remove. KANDYKORN is another example of a sophisticated, multi-stage attack that begins with social engineering, where the victim is tricked into running a malicious script disguised as a normal file.
Also highlighted was the SmoothOperator program, which, according to the researchers, was used to attack customers of the popular 3CX application. The malware was embedded in installation files and collected data from infected devices.
The researchers emphasize that groups controlled by RGB became known thanks to high-profile incidents such as the attack on Sony Pictures in 2014, the global WannaCry epidemic in 2017, and numerous attacks on cryptocurrency exchanges. The activities of hackers from the DPRK have been going on since 2007 and cover many industries and regions around the world.
Due to the scale and complexity of the activities of North Korean groups, in 2024 they were included in the annual MITRE ATT&CK security assessment, which analyzes their methods, tactics and the software used. Palo Alto Networks, in turn, continues to develop and improve solutions aimed at protecting companies from threats posed by these hacker groups.
The report highlights the need for a comprehensive approach to protecting organizations to minimize the risks associated with the activities of state-owned hackers, such as North Korean groups running RGB.
Source

