Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,095
- Points
- 113
Positive Technologies has identified a problem at the heart of Intel.
Mark Ermolov, a specialist at Positive Technologies, has identified a security vulnerability in Intel Software Guard Extensions (SGX) that could lead to serious consequences for users.
The vulnerability is related to a bug in the code that allows an attacker to gain full access to protected data in SGX enclaves on legacy Gemini processor-based systems and possibly some older Xeon processors that are still supported.
Ermolov said that after many years of research, experts managed to extract the SGX Fuse Key0 (Root Provisioning Key). Along with another key, the Root Sealing Key, which has also been compromised, the Root Provisioning Key is the Root-of-Trust (RoT) for SGX. An internal code error is that Intel engineers didn't clear the internal buffer in the CPU core, which contains all the fuses (including FK0) received from the Fuse Controller. This flaw opens up the possibility for an attacker to gain access to protected data in SGX.
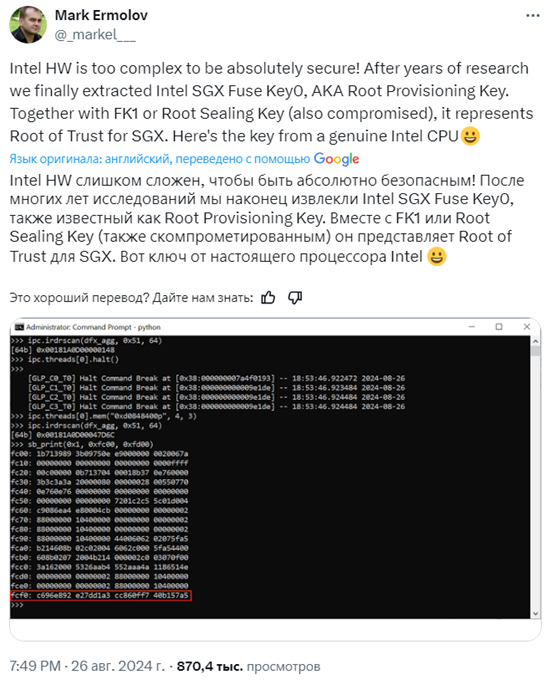
Ermolov's tweet
Although Intel has ended using the technology in client processors, many are still in service, especially in embedded systems. Access to the FK0 key gives you full control over the protected data in SGX.
Intel points out that the attack requires physical access to the vulnerable device, as well as the presence of a number of unpatched vulnerabilities on it. In particular, it is necessary that the device be affected by previous vulnerabilities such as CVE-2017-5705, CVE-2017-5706, CVE-2017-5707, and CVE-2019-0090, for which Intel has already released patches.
Despite this, many Gemini processors are still in use, especially in devices with low performance requirements. These systems, as emphasized at Johns Hopkins University, can be completely compromised, and all data used in secure SGX enclaves on Gemini processors can be insecure.
The problem lies in the software that was used to protect the SGX. Bugs in the code could allow an attacker to gain access to SGX-protected material, although it remains unclear whether this can be done remotely or requires physical access.
SGX technology was introduced in 2015 along with Skylake processors and was intended to protect critical code even from the manufacturer itself. However, serious problems were discovered shortly after launch. Despite the fact that later chips abandoned this technology, it is still used in many embedded systems, which makes the vulnerabilities relevant to a wide range of users.
Source
Mark Ermolov, a specialist at Positive Technologies, has identified a security vulnerability in Intel Software Guard Extensions (SGX) that could lead to serious consequences for users.
The vulnerability is related to a bug in the code that allows an attacker to gain full access to protected data in SGX enclaves on legacy Gemini processor-based systems and possibly some older Xeon processors that are still supported.
Ermolov said that after many years of research, experts managed to extract the SGX Fuse Key0 (Root Provisioning Key). Along with another key, the Root Sealing Key, which has also been compromised, the Root Provisioning Key is the Root-of-Trust (RoT) for SGX. An internal code error is that Intel engineers didn't clear the internal buffer in the CPU core, which contains all the fuses (including FK0) received from the Fuse Controller. This flaw opens up the possibility for an attacker to gain access to protected data in SGX.

Ermolov's tweet
Although Intel has ended using the technology in client processors, many are still in service, especially in embedded systems. Access to the FK0 key gives you full control over the protected data in SGX.
Intel points out that the attack requires physical access to the vulnerable device, as well as the presence of a number of unpatched vulnerabilities on it. In particular, it is necessary that the device be affected by previous vulnerabilities such as CVE-2017-5705, CVE-2017-5706, CVE-2017-5707, and CVE-2019-0090, for which Intel has already released patches.
Despite this, many Gemini processors are still in use, especially in devices with low performance requirements. These systems, as emphasized at Johns Hopkins University, can be completely compromised, and all data used in secure SGX enclaves on Gemini processors can be insecure.
The problem lies in the software that was used to protect the SGX. Bugs in the code could allow an attacker to gain access to SGX-protected material, although it remains unclear whether this can be done remotely or requires physical access.
SGX technology was introduced in 2015 along with Skylake processors and was intended to protect critical code even from the manufacturer itself. However, serious problems were discovered shortly after launch. Despite the fact that later chips abandoned this technology, it is still used in many embedded systems, which makes the vulnerabilities relevant to a wide range of users.
Source

