Tomcat
Professional
- Messages
- 2,689
- Reaction score
- 963
- Points
- 113
Seven years ago – in 2009 – we encountered a completely new type of attack on banks. Instead of infecting the computers of thousands of users around the world, cybercriminals focused directly on ATMs - infecting them with malware called Skimer. And now, seven years later, Kaspersky Lab's Global Research and Analysis Team (GREAT) and Penetration Testing Team were investigating one incident. During the investigation, a new, improved version of Skimer was discovered.
Once launched, the malware checks the file system. If it is FAT32, it places the netmgr.dll file in the C:WindowsSystem32 folder. If the NTFS file system is used, the same file is placed in the NTFS stream corresponding to the XFS service executable. Most likely, the file is placed in an NTFS file stream in order to complicate forensic analysis.
After successful installation, the sample modifies the entry point of the XFS service executable (SpiService.exe) to add a call (LoadLibrary) to the netmgr.dll file it installed on the system. This file is also protected by Themida packer.
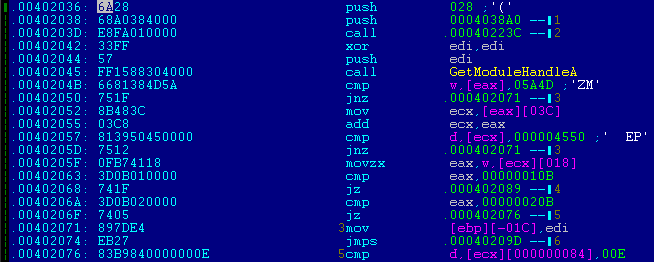
Entry point of SpiService.exe before infection

SpiService.exe entry point after infection
After successful installation, the ATM reboots. The malicious library is loaded into the SpiService.exe address space thanks to a new LoadLibrary call, giving it full access to XFS.
Once the magic card is inserted, the malware is ready to interact with two different types of cards, each with their own functions:
Below is a list of the most important functions:
During its operation, the malware also creates the following files or NTFS file streams (depending on the file system). These files are used by the malicious program at various stages of its operation, incl. when recording configuration, recording data read from cards and logging activity:

Main window
The following video details the scenario of interaction between money mules and an infected ATM (as described above).
[youtube
]
The important detail in this case is the hard-coded data on track 2: a card with this data must be inserted into the ATM to activate the malware. As a preventative measure, banks can search their processing systems for corresponding card numbers and detect potentially infected ATMs or money mules, as well as block attempts to activate malware.
We also recommend regular anti-virus scanning, whitelisting technologies, effective device control policies, full-disk encryption and password protection of the ATM BIOS system, allowing booting only from the hard drive, and isolating the ATM network from all other internal banking networks.
Currently, Kaspersky Lab has identified 49 variants of this malware, with 37 variants targeting ATMs from the same manufacturer. The latest version of the malware was discovered in early May 2016.
All described samples are detected by Kaspersky Lab products as Backdoor.Win32.Skimer. SpiService.exe files modified by the malware are detected as Trojan.Win32.Patched.rb.
The investigation is still ongoing. We have already shared the full report with various law enforcement agencies, Computer Emergency Response Teams (CERTs), financial institutions, and clients of Kaspersky Lab's threat intelligence service (Kaspersky Lab Threat Intelligence-Service). For more detailed information, you can contact intelreports@kaspersky.com
e563e3113918a59745e98e2a425b4e81 a7441033925c390ddfc360b545750ff4
C:WindowsTempattrib4
C:WindowsTempmk32
C:WindowsTemp:attrib1
C:WindowsTemp:attrib4
C:WindowsTemp:mk32
C:WindowsTemp pt
pt
C:WindowsSystem32netmgr.dll
******548965875*=************ ********
******487470138*=********************
******487470139*=**** ****************
******000000000*=*******************
***** *602207482*=*******************
******518134828*=***************** ***
******650680551*=*******************
******466513969*=********* ************
Infects like viruses
Cybercriminals often disguise their malware using packaging programs to make it more difficult to analyze. The criminals behind Skimer also used this technique. They used the legally sold Themida packager, which packages both the infector and the dropper.Once launched, the malware checks the file system. If it is FAT32, it places the netmgr.dll file in the C:WindowsSystem32 folder. If the NTFS file system is used, the same file is placed in the NTFS stream corresponding to the XFS service executable. Most likely, the file is placed in an NTFS file stream in order to complicate forensic analysis.
After successful installation, the sample modifies the entry point of the XFS service executable (SpiService.exe) to add a call (LoadLibrary) to the netmgr.dll file it installed on the system. This file is also protected by Themida packer.

Entry point of SpiService.exe before infection

SpiService.exe entry point after infection
After successful installation, the ATM reboots. The malicious library is loaded into the SpiService.exe address space thanks to a new LoadLibrary call, giving it full access to XFS.
Functionality
Unlike Tyupkin, which used a "magic" code and the malware was only active at certain times, Skimer only "wakes up" when a "magic" card (with certain data on Track 2) is inserted into the ATM , see infection indicators at the end of the posting).Once the magic card is inserted, the malware is ready to interact with two different types of cards, each with their own functions:
- Card type 1 – command request via interface
- Card Type 2 - Execute command hardcoded on track 2
Below is a list of the most important functions:
- Show detailed information about the malware installation;
- Issue cash – 40 bills from the specified cassette;
- Start collecting data from inserted cards;
- Print collected card data;
- Perform self-removal;
- Enable debug mode;
- Perform an update (the updated malicious code is written to the card).
During its operation, the malware also creates the following files or NTFS file streams (depending on the file system). These files are used by the malicious program at various stages of its operation, incl. when recording configuration, recording data read from cards and logging activity:
| C:WindowsTempattrib1 | card data collected from network traffic or card reader; |
| C:WindowsTempattrib4 | log data from various APIs responsible for exchanging information with the keyboard (essentially a log of data such as PIN codes entered); |
| C:WindowsTempmk32 | same as attrib4; |
| C:WindowsTemp:attrib1 | htfs stream, with similar contents of the file attrib1; |
| C:WindowsTemp:attrib4 | htfs stream, with similar contents of the file attrib4; |
| C:WindowsTemp:mk32 | htfs stream, with similar contents of the mk32 file; |
| C:WindowsTemp | money mule activity log. |

Main window
The following video details the scenario of interaction between money mules and an infected ATM (as described above).
[youtube
Conclusions
During our team's recent investigations into ATM hacking incidents, we discovered Tyupkin, Carbanak, and black box attacks. The evolution of Backdoor.Win32.Skimer shows that attackers are interested in the development of these malicious families, since ATMs are a very convenient mechanism for cybercriminals to withdraw funds.The important detail in this case is the hard-coded data on track 2: a card with this data must be inserted into the ATM to activate the malware. As a preventative measure, banks can search their processing systems for corresponding card numbers and detect potentially infected ATMs or money mules, as well as block attempts to activate malware.
We also recommend regular anti-virus scanning, whitelisting technologies, effective device control policies, full-disk encryption and password protection of the ATM BIOS system, allowing booting only from the hard drive, and isolating the ATM network from all other internal banking networks.
Currently, Kaspersky Lab has identified 49 variants of this malware, with 37 variants targeting ATMs from the same manufacturer. The latest version of the malware was discovered in early May 2016.
All described samples are detected by Kaspersky Lab products as Backdoor.Win32.Skimer. SpiService.exe files modified by the malware are detected as Trojan.Win32.Patched.rb.
The investigation is still ongoing. We have already shared the full report with various law enforcement agencies, Computer Emergency Response Teams (CERTs), financial institutions, and clients of Kaspersky Lab's threat intelligence service (Kaspersky Lab Threat Intelligence-Service). For more detailed information, you can contact intelreports@kaspersky.com
Appendix I: Infection Indicators
Hashes
354 84d750f13e763eae758a5f243133e563e3113918a59745e98e2a425b4e81 a7441033925c390ddfc360b545750ff4
File names
C:WindowsTempattrib1C:WindowsTempattrib4
C:WindowsTempmk32
C:WindowsTemp:attrib1
C:WindowsTemp:attrib4
C:WindowsTemp:mk32
C:WindowsTemp
C:WindowsSystem32netmgr.dll
Track 2 data
******446987512*=*************************548965875*=************ ********
******487470138*=********************
******487470139*=**** ****************
******000000000*=*******************
***** *602207482*=*******************
******518134828*=***************** ***
******650680551*=*******************
******466513969*=********* ************
