Man
Professional
- Messages
- 3,222
- Reaction score
- 1,215
- Points
- 113
Hello friends!
Over time, the Internet has become an integral part of our daily lives. We depend on it for work, communication, entertainment and information. At the same time, more and more people are looking for ways to save on paid network access services. And one of the most common methods has become hacking WiFi networks.
Today we will look at how professional hackers do it.
Unlike access points belonging to companies, which are usually protected, it is very likely that your neighbor's home router is configured incorrectly. The term "neighborly" is mentioned here in the sense that for a successful hack you need to be in close proximity to the victim (which, in general, is not a problem if you have an external antenna). Recently, many utilities have appeared (like "Wifite"), with the help of which even an intruder without special qualifications can penetrate a nearby Wi-Fi network. Most likely, among your neighbors there are those who use a poorly configured access point. By the way, to penetrate the network, it is not necessary to be guided by malicious goals, but simply out of curiosity. In addition, having familiarized yourself with the hacking methods, you will be able to protect your own Wi-Fi network.
List of utilities used:
Getting the password to the access point
Attack scheme: in open Wi-Fi networks, packets are not encrypted, and anyone can intercept all traffic (HTTP, mail, FTP). In our case, we intercept traffic on channel 1 using the 'Airodump-ng' utility, and then analyze it in Wireshark.
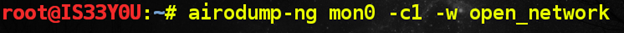
Command to intercept traffic on channel 1 in an unsecured network
As a result of the analysis, we found out that the user was connecting to a bank account.
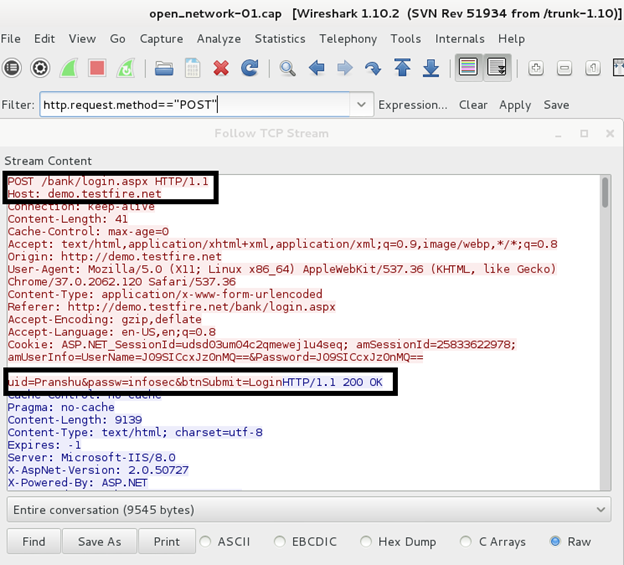
Analysis of intercepted traffic in Wireshark
However, it is unlikely that the bank's services will work via an unprotected protocol (HTTP, FTP, SMPT, etc.) due to the danger, as in the case above, of using the service via an unprotected Wi-Fi network.
Protection methods: never leave the access point "open" or unprotected. Configure the router to use a complex WPA2 key (this is discussed below). If for some reason you want to use an open access point, use the HTTPS Everywhere browser extension .
Attack Scheme: There are countless articles on attack schemes against WEP. We will not go into detail, but simply refer you to this page .
Security Methods: Instead of WEP, use WPA2 or AES.
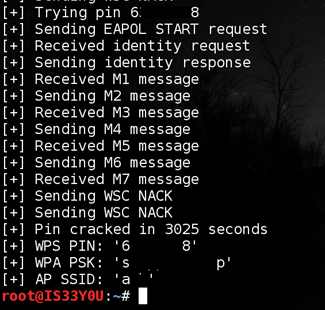
WPS PIN brute force process
Protection methods: update your router firmware. The new version should have a lockout function after several unsuccessful attempts to enter the PIN (WPS lockout policy). If your router does not have such a function, simply disable WPS.
Attack scheme: How can a hacker (or your neighbor) learn the WPS PIN? Usually, the PIN is written on the router's backing, which an attacker can examine during a "friendly" visit. In addition, the access point can remain "open" for some time, while the user configures the router or resets the settings to factory defaults. In this case, an attacker can quickly connect to the router, enter the settings panel (using standard credentials) and learn the WPS PIN.
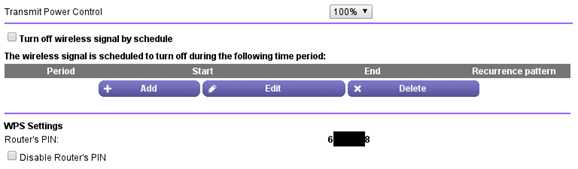
Router PIN
Once the attacker has learned the PIN, obtaining the WPA password occurs within a few seconds.
Protection methods: scrape the PIN from the router's backing and do not leave the access point "open" for a single second. Moreover, in modern routers you can change the WPS PIN in the settings panel (change the PIN periodically).
Function of generating a new PIN
That's all from me, thank you for reading...
Over time, the Internet has become an integral part of our daily lives. We depend on it for work, communication, entertainment and information. At the same time, more and more people are looking for ways to save on paid network access services. And one of the most common methods has become hacking WiFi networks.
Today we will look at how professional hackers do it.
Unlike access points belonging to companies, which are usually protected, it is very likely that your neighbor's home router is configured incorrectly. The term "neighborly" is mentioned here in the sense that for a successful hack you need to be in close proximity to the victim (which, in general, is not a problem if you have an external antenna). Recently, many utilities have appeared (like "Wifite"), with the help of which even an intruder without special qualifications can penetrate a nearby Wi-Fi network. Most likely, among your neighbors there are those who use a poorly configured access point. By the way, to penetrate the network, it is not necessary to be guided by malicious goals, but simply out of curiosity. In addition, having familiarized yourself with the hacking methods, you will be able to protect your own Wi-Fi network.
List of utilities used:
Getting the password to the access point
The choice of one or another attack method depends on the configuration of the victim's Wi-Fi network. Each security standard has its own vulnerabilities that an attacker can exploit.
Open hotspots
Open access points, although rare, are still found, which indicates either "generosity" towards neighbors, or complete ignorance in security issues (or both). It is believed that users with an unlimited channel leave their routers unprotected more often than others.Attack scheme: in open Wi-Fi networks, packets are not encrypted, and anyone can intercept all traffic (HTTP, mail, FTP). In our case, we intercept traffic on channel 1 using the 'Airodump-ng' utility, and then analyze it in Wireshark.

Command to intercept traffic on channel 1 in an unsecured network
As a result of the analysis, we found out that the user was connecting to a bank account.

Analysis of intercepted traffic in Wireshark
However, it is unlikely that the bank's services will work via an unprotected protocol (HTTP, FTP, SMPT, etc.) due to the danger, as in the case above, of using the service via an unprotected Wi-Fi network.
Protection methods: never leave the access point "open" or unprotected. Configure the router to use a complex WPA2 key (this is discussed below). If for some reason you want to use an open access point, use the HTTPS Everywhere browser extension .
IV collisions in WEP
WEP is an outdated security standard that is vulnerable to static attacks due to IV collisions. WEP creates a false sense of security, and with WPA2, it is hard to imagine anyone wanting to use outdated algorithms.Attack Scheme: There are countless articles on attack schemes against WEP. We will not go into detail, but simply refer you to this page .
Security Methods: Instead of WEP, use WPA2 or AES.
WPS PIN Selection
WPS PIN is an eight-digit number linked to the router. If the WPA password is vulnerable to a dictionary attack, the user can set a complex WPA password and, in order to avoid remembering a long passphrase, enable WPS. After transmitting the correct WPS PIN to the router, the client is then sent information about the settings, including the WPA password.Brutfors WPS PIN
The WPS standard was implemented incorrectly: firstly, the last digit of the PIN is a checksum, which means that the effective size of the WPS PIN is only 7 digits. Moreover, the registrar (router) checks the PIN in two parts. This means that the first part, consisting of 4 digits, has 10,000 possible combinations, and the second, consisting of 3 digits, has 1,000 combinations. That is, an attacker will need 11,000 attempts to pick a PIN in the worst case, which is very little. Experimenting with direct enumeration, using the 'reaver' utility, we managed to pick a WPS PIN within 6 hours.
WPS PIN brute force process
Protection methods: update your router firmware. The new version should have a lockout function after several unsuccessful attempts to enter the PIN (WPS lockout policy). If your router does not have such a function, simply disable WPS.
Other ways to get WPS PIN
If an attacker learns the PIN of a neighboring router, the effectiveness of further manipulations increases many times and, most importantly, does not require much time.Attack scheme: How can a hacker (or your neighbor) learn the WPS PIN? Usually, the PIN is written on the router's backing, which an attacker can examine during a "friendly" visit. In addition, the access point can remain "open" for some time, while the user configures the router or resets the settings to factory defaults. In this case, an attacker can quickly connect to the router, enter the settings panel (using standard credentials) and learn the WPS PIN.

Router PIN
Once the attacker has learned the PIN, obtaining the WPA password occurs within a few seconds.
Protection methods: scrape the PIN from the router's backing and do not leave the access point "open" for a single second. Moreover, in modern routers you can change the WPS PIN in the settings panel (change the PIN periodically).

Function of generating a new PIN
That's all from me, thank you for reading...
