Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,579
- Points
- 113
ATTENTION! THE FORUM DO NOT COMMIT AND DO NOT RECOMMEND THAT YOU COMMIT ILLEGAL ACTIONS OR GAIN UNAUTHORIZED ACCESS TO THE SYSTEMS. THIS ARTICLE AIMS TO POINT OUT PROBLEMS WITH SYSTEMS AND WARN USERS AND INSTITUTIONS AGAINST POTENTIAL ATTACKS.

Probably everyone who has ever withdrawn money from an ATM, hearing the pleasant noise of the dispenser, thought about how to get more of them. And no wonder, back in the 90s, after reviewing "Terminator 2", where John Connor hacks ATM using a laptop, some began to dream about how to repeat his atrocities. Despite the fact that terminators and Skynet have not yet been invented, attacks on ATMs are a reality. Today we will look at the most well-known methods of hacking ATM in the smallest nuances.
First, let's look at how the ATM works. In fact, it is a safe with a computer connected to the network. At the bottom, in the safe, money is stored in special cassettes. The safe is equipped with a mechanism for feeding bills, which is called a dispenser, which issues money from cassettes.
A service area is located above the safe, where a screen and keyboard are installed, which is called a "PINpad". Behind them is a computer. Sometimes it is an ordinary system unit, and sometimes even in such a case as a regular home computer. There is also service equipment: a card reader, a receipt printer, and security systems. All devices are connected to the system unit that performs the host function. Ports can be located directly on the system unit, and if they are not enough, a USB splitter is used.
The ATM is connected to the bank via a secure communication channel, usually using the NDC/DDC protocols (specifications at the bottom of the article) or X.25 (in general cases).
Money is stored in cassettes, on average, these cassettes are from four to six. There are approximately 2,500 banknotes in each cassette. Each cassette is set up for a banknote of its own denomination: instead of fifty-ruble notes, you will not be able to charge five-thousandth ones.
Some ATMs can accept money. Accepted bills are sent to a separate cassette. Usually, the ATM will not issue them, even if the main cash registers run out of money.
In the service area, there is everything that, in the opinion of the ATM manufacturers, does not allow you to get to the money. Probably, for this reason, the lid is most often plastic, and only a simple lock protects against unauthorized entry. By the way, both assembled locks and separate keys can be easily purchased online, since each manufacturer installs identical locks for their devices, and most banks, as a rule, do not think about replacing them with unique ones. Attackers can also make keys themselves or use very simple ones helpers tools.
Opening the ATM service area on PHDays
The safe is much better protected – it is a Cabinet made of steel and concrete with two types of locks: a combination lock (electronic or limbic, sometimes electromechanical) and a key lock (usually a lever lock). In the safe there are devices that are directly related to money – a dispenser from which cash is issued, and a module for receiving cash. Often, the safe is equipped with sensors. They report tilt, noise, and temperature rise.
The list of SOFTWARE installed at the ATM is small:
As mentioned above, probably 60% of ATMs still use Windows as their operating system. Yes, not just Windows, but Windows XP. Microsoft has not released updates for this OS since April 2014. Of course, all 0-days for Windows XP remain unresolved. Often, employees who serve ATMs believe that if the ATM is working, it is better to "leave it alone". For this reason, some ATMs still have the ability to detect, for example , an UN-patched critical vulnerability MS08-067, which allows remote code execution.
ATM modules are implemented on microcontrollers with real-time operating systems (RTOS). static analysis is poorly applicable to such systems.
At any given time, the ATM is in one of the following operating modes:
The first character of this string is the state type (indicated by the letters A..Z and some characters (,’.?)), it defines the aggregate. The remaining 24 characters are 8 decimal 3-digit numbers, each of which is a specific state setting (screen number to display, state transition conditions, list of actions). There can be any number of States of the same type.
In service mode
When the service mode starts, the ATM automatically starts executing state 000. This is usually state A (Card read state). In this state, the ATM displays a screen with an invitation to insert a card and switches the card reader to receive mode. The state is also responsible for reading the map and branching depending on the results of this operation.
Below is an example of the configuration of a typical state A:
000A001001011008004002001104
000 - room state
A - type state (Card read state)
001 -screen room (Screen number)
001 -number state, which go in case of successful card reading
011 -number state, which go in the event of an error reading the card
008 -the condition of reading 1
004 -condition read 2
002 -condition read 3
001 -the return card (immediately after reading or at the completion of the operation)
104 - transfer state, if the card is unknown to the Bank
Let's go through the parameters in more detail:
State type -everything is clear here: after determining the state type, the application knows how to interpret further parameters.
Screen number - is a link to a line with a text description of the screen that is displayed during the operation of this state.
Not every state has a screen.
The screen can have a number from 000 to 999. Screens that differ by 100 are usually reserved for different languages. So screen 010 and screen 210 are probably multilingual versions of the same screen. I'll tell you more about the screens later.
Transition state number in case of successful map reading - what state the application will start executing if the map is recognized and the data is read successfully.
In addition to States and screens, the ATM has another important configuration parameter-the financial institution table. The table of financial institutions contains data about which cards belong to which Bank, how to correctly parse data read from map tracks, and what to do next depending on this data. For example, if the card is local, then you can run one scenario, if the card is a third-party Bank, then you need to prohibit the branch of the scenario with mobile payments and balance verification.
Transition state number in case of problems with reading the map - if the map couldn't be read according to any of the suggested conditions - go to the state specified in this parameter. As a rule, this is the J (close state) state where we give the card away, show the screen with a suggestion to pick it up, and activate the timer after which the card retention mechanism will be launched. State J is also the last state in the event of a successful transaction.
Conditions for reading the card (3 consecutive parameters) are bitmasks that indicate the track numbers to be read and interaction with the chip, if any.
For example, Read Chip, Read Track 2 and Track 1, Read Track 1. If at least one of the conditions is triggered, then the other conditions are not met and the card is considered read. If none of the conditions are met, the card is considered unread.
The condition for the return of the card - the ATM can return the cards immediately after reading, or it can do it at the end after all operations are completed.
The rest of the states are arranged in a similar way:
Going through all these States, the application sooner or later reaches the state of interaction with the host-state I (Transaction Request State). On this state, a request is generated from the data collected on previous States and sent to the server. The request is an ATM ID (Logical Unit Number), data from map tracks, data about previous transactions, data from the amount buffers, pin block, and function key presses (FDK buffer). Data is separated by a separator character. The server application receives the request and analyzes the Fdk buffer – it is from the contents of this buffer that the host understands what the ATM wants. After that, depending on the decision made, it sends a response containing:
Upon completion of the required actions, the application sends a confirmation to the host and goes to the specified state. As a rule, this is the already known state J. In case of any failure, the application sends a message about the failure to the host and waits for a new Transaction Reply with the transition to the new state.
The ATM screen is a field of 32x16 cells. The screen can contain both graphic information and text information that is positioned relative to the cells. Fonts can be double-height.
The screen description is a string of text interspersed with control characters, such as screen clearing, cursor positioning, and font size. In most modern banks today, text is used only when entering amounts, and in other cases the screen is just a whole picture. However, there are also fully text-based screens.
Example of a screen displaying an image from the image table (\0c\1bP2018\1b\5c)
These are the screens that the state parameters refer to.
A set of States, screens, FIT, and timers is called an ATM script. Each scenario has its own number. After loading the ATM and connecting it to the network, it sends a message to the host with its ID and configuration number. If the configuration needs to be updated the host switches the ATM to "Out of Service" mode and starts loading the necessary parameters of the new configuration. The last parameter is the configuration number. Similarly, keys for pin block encryption, for dipping, and master keys are loaded.
What to do with chip cards if the chip couldn't be read depends on the script settings. You may be offered a narrower range of services, or you may simply refuse to serve them. The same applies to cards issued by other banks.
As we can see, an ATM is a constructor, sometimes with crooked hardware and outdated SOFTWARE. It is no wonder that such a system will sooner or later fall victim to logical attacks.
There is no reception against scrap
Sometimes logical attacks do not require complex hardware and SOFTWARE, just a screwdriver or a small crowbar is enough.
The first attack we studied is very simple. It is based on the sequence of actions laid down in the ATM. So, after receiving a positive response from the Bank about issuing the amount, the ATM gives a command to the dispenser and starts counting out the required number of banknotes, the reader is given a command to return the card to the client. Until the customer picks it up, the money is waiting in the delivery tray, and the flap of the tray will be closed. But if the fraudster holds the card, it gets stuck in the reader. And the money is already in the delivery device, only the door is closed. Using a screwdriver or crowbar, scammer squeezes out the flap of the tray and gets the money. At the same time, the ATM sends a report to the Bank about a failed transaction and the debited amount is returned to the account. As a result, the criminal takes the money, but the card is also in his hands. But in fact, the withdrawal of money from the ATM was not recorded and there was no debiting from the account.
The behavior when a card is detected that is not collected is fully configurable the ATM can either capture it or leave it in the path. The same applies to issuing a card before/after money, at the beginning/end of work, or during a power outage. What to do if an invalid PIN is entered, a false PIN is entered (if any), when the counter of invalid pins is reset, whether a card capture is necessary-everything is decided by the host. If the host does not instruct the ATM to capture the card, it will not capture it, even if it is ten times fake, stolen, or lost.
Simple and logical? What is not a logical attack? Until 2016, most banks worked like clockwork. But time passed and the vulnerability was fixed. Nevertheless, even now there are both banks that have not heard anything about this, and outdated machines. The world is very big…
Getting more complicated: black box
To implement such an attack, attackers drill a hole in the ATM's front panel to get to the USB bus or directly to the dispenser's cable. Having gained access to the cable, an attacker can connect the dispenser to his device, which is programmed to send commands to issue bills. Attacks of this type are called Black Box attacks.

ATM with a drilled hole in the service area
Let's start by using the service utilities and their modified versions, which were originally provided by ATM manufacturers to check the health of devices. One of the functions of such utilities is to test the operation of the dispenser, including issuing banknotes. To perform such a test, the engineer needs to confirm his legitimacy by opening the safe door or by manipulating the dispenser cassettes in some way. The logic is simple – if you can open the safe, then you have a key, i.e. you are a licensed engineer or collector. But no one canceled the release of new versions of IDA Pro, and replacing a couple of bytes in the utility with the "correct" ones allows you to" test " the output without any checks.
How does the attack work? An attacker opens or drills an ATM, connects the dispenser to their laptop, and leaves the crime scene, leaving the device plugged in. A laptop with drivers installed for the ATM dispenser and a PATCHED kdiag utility that does not require confirmation of opening the lid, issues a command to issue money at the operator's command. To organize remote operator access, a USB GPRS modem is connected to the laptop. The OS used is Windows, version XP or 7 for better compatibility with drivers.
Software from ATMDesk is also freely available.
Another way to get rich for intruders is to change the denomination of the issued banknotes, again using the diagnostic utility. As a result, the attacker receives money with the largest face value (for example, 100 dollars or euros) from the cash register, and the ATM SOFTWARE thinks that it issues the smallest of the available face values. Thus, a card with a balance of several hundred can get several thousand.
An insufficiently reliable NCR protection system is used in half of ATMs. Another 19% of machines do not have any protection measures against Black Box attacks at all.
XFS
XFS (CEN/XFS, formerly WOSA/XFS), or eXtensions for Financial Services, is a standard that provides a client-server architecture for interacting financial applications on the Windows platform with devices, in particular, for ATMs. The standard aims to unify the work of SOFTWARE with any hardware, regardless of the manufacturer, and provides a common API for this purpose.
If the ATM is managed by a Windows-based system, the task of software observation is to organize the interaction of the user (client or service personnel) with the processing center, which sends commands to the ATM, and manages the equipment that executes these commands. Messages are exchanged with the processing center using protocols (NDC/DDC or X. 25), the user works through the GUI, and the corresponding service providers are responsible for the operation of each ATM module (a kind of gateway to these modules). To transmit commands to service providers and further to equipment, as well as to return status messages, a level called XFS Manager is used-according to the WOSA concept. Any major ATM manufacturer (Wincor, NCR, Diebold) has its own implementation of both XFS and banking applications. However, there is alternative software on the market that meets all standards and is not tied to a specific vendor.
There are several implementations of XFS managers (including open source ones) written in C++, and theoretically libraries of service providers written for one Manager should also be suitable for all others, but in fact sometimes a library written by a specific vendor for a specific XFS Manager works only with this Manager. There is also Java XFS with its own libraries that are not compatible with classic managers.
Thus, any application developed with the XFS standard in mind can manage low-level objects using only the logic described in this standard. And this application may well be a Tyupkin backdoor or any other malicious program.
For example, a dispenser, which is the most interesting device for intruders, can issue money without any authorization. And in some models of ATMs, you can use XFS to programmatically open the safe and unlock the cassettes.
As applied to the card reader, XFS allows you to read and write data on the magnetic stripe of a Bank card and even get the transaction history stored on the EMV card chip.
We should also mention the encrypted PIN – pad (EPP). It is assumed that the PIN cannot be intercepted, because it is entered on the ATM pin pad and directly inside the encryption module turns into a pin block (for this purpose, the EPP cryptographic key contains keys that are paired in the Bank's hardware security module). However, XFS allows us to use a pin pad in two modes:
You may ask, but what about authentication and exclusive access? And surely you can't get the specifications for the standard? Unfortunately, this is not about XFS. This standard does not provide for any authentication, and exclusive access to service providers is implemented, but not for security reasons. This is just a single-threaded command sending function, so that you don't accidentally break a delicate piece of hardware by sending two identical commands in parallel.
All specifications can be found here. Google will tell you even more about XFS.
If you are interested, the SDK can be found here.
XFS manager 3 with the wsxfs.DLL library download
Integrity monitoring tools
Some banks sometimes use software integrity controls on their ATMs that promise to prevent unauthorized code execution based on a whitelist, control device and storage connections, and other ways to counter attacks.
But we should not forget that this is, first of all, software, and it, like any other SOFTWARE, is not perfect. It may be vulnerable to attacks such as going outside the kiosk (bypassing the full-screen mode restriction and gaining access to the operating system), bypassing whitelists, buffer overflow, raising privileges to the SYSTEM user level, and others. As you can see, often existing vulnerabilities allow villains to gain access to the operating system and do their dirty deeds.
Malware
On one of the russian-language closed carder forums vendors, rumors about the possibility of emptying ATMs have been floating around since mid-2008, but only in 2009, when analysts were able to obtain the first samples of malware, the financial world was stirred by the appearance of the Trojan Backdoor.Win32.Skimer: this was the first known malware that targets ATMs. Skimer attacked Wincor Nixdorf ATMs. The cybercriminals used the malware to empty the dispenser and obtain data from plastic cards processed at the infected ATM.
Since then, a lot of water has flowed, and ATMs of various manufacturers have repeatedly been exposed to malware. Entire families of such malicious programs have emerged.
There are four main stages in the scheme of stealing money from ATMs using malware:
There are several different ways to classify ATM Malware (ATM malware). In terms of functionality, all such programs can be divided into two types: virtual skimmers and Direct Dispense utilities.
The purpose of skimmers is to steal the data of a bank card and the transaction being carried out, and, if possible, even a PIN code, if the encryption keys of the PIN keyboard were previously compromised.
Direct cash withdrawal utilities have a feature popularly known as jackpotting, which allows attackers to perform unauthorized withdrawal of money from an ATM without the need to authorize the transaction on the Bank's side. At the same time, there is malicious software that combines the functionality of a skimmer and jackpotting.
Over the past 10 years, more than 30 different malware families for ATMs have been discovered. Let's look at some of the most popular and significant ones and try to highlight the common features and unique differences of each one.

Ploutus
Ploutus is the malware family with the highest number of detected samples. Most of them were registered in Mexico. Ploutus is a typical example of direct search malware. To download the malware, attackers must have access to USB ports or a CD drive.
As an example, we can cite one of the recent modifications, Ploutus-D, which was initially focused on Diebold ATMs, which are widely distributed in the United States. However, the malware interacts with the ATM via the KAL Kalignite multi-vendor platform, and after a simple modification of the Ploutus-D code, it can also be used to attack ATMs of other manufacturers.

Skimer
Skimer is one of the first Trojans for ATMs. Functionally, this malware fully justifies its name and is essentially a virtual skimming device that copies data from the magnetic stripe of a Bank card.
In addition, Skimer is a backdoor and can be used for unauthorized withdrawal of money from an ATM. If the attacker knows the key to activate the program, the malware displays a menu from which you can issue money from each of the four dispenser cassettes.
Most other ATM malware families operate on a similar principle. Attackers must provide themselves with physical access to the ATM's service area in order to connect an external drive with malware. After the malware is introduced into the system, the attacker must enter a unique code to activate the cash withdrawal process.
Tyupkin
The real glory came to malware for ATMs with the appearance of the Tyupkin Trojan, whose activity was first recorded in 2014. Since then, many ATMs around the world have been attacked.
A distinctive feature of Tyupkin is its ability to limit the time of its activity to certain hours and days of the week. Some of the first varieties of Tyupkin could initially only be launched on Sunday and Monday nights.
In addition, the Trojan has a self-defense function. Immediately before cash withdrawal, Tyupkin disables all network connections so that if suspicious activity is detected on the Bank's side, the monitoring service will not be able to turn off the ATM, thereby interrupting the fraudulent operation.
Alice
The principle of operation of Alice is the same as that of many other ATM malware. The installation requires physical access to the ATM system. After starting, Alice asks for an access code to continue working. If you enter the correct activation code, the malware gets access to the banknote dispenser and allows you to issue cash.

Cutlet Maker
In 2017, cybercriminals started selling ATM Malware-as-a-Service on the darknet. For $ 5,000, anyone can purchase a package of ready-to-use Cutlet Maker malware and video instructions on opening an ATM. Those who bought the service need to choose a suitable ATM (the authors of malware recommend Wincor Nixdorf), use the instructions for hacking its service part, download the malware and pay the service organizers for its activation to start the process of issuing money.

Cutlet Maker Interface
In the case of Cutlet Maker, the potential user of the service may have minimal knowledge about the target of the attack. This example shows how such schemes reduce the entry threshold to this type of crime and lead to a significant increase in the number of cybercriminals.
FASTCash
FASTCash is a unique tool that the North Korean hacker group Lazarus used to attack financial institutions in more than 20 countries around the world. In total, several tens of millions of dollars were stolen in 2016-2018.
A special feature of FASTCash is the mechanism of its operation and orientation to the IBM AIX OS. Hackers introduced the Trojan into a legitimate process on the application server of processing systems that control transactions in the ATM network and run under AIX.
After the server was compromised, the Trojan was able to create fake ISO 8583 messages (a standard describing the transmission process and format of financial messages of systems that process Bank card data), generating a response confirming a fraudulent cash withdrawal operation at ATMs. It should be noted that in all cases, successful attacks were possible due to the fact that financial organizations used outdated versions of AIX-without the necessary security updates.

How FastCash works
This is another example of a targeted attack on financial institutions, in this case through processing systems. At the same time, the level of complexity and development of FASTCash is very high and cannot be compared with any other” standard " ATM Malware.
ATMitch
Studying malware showed that after installing under the name tv.dll, ATMitch a remote connection to the ATM is opened from inside the Bank using the Remote Desktop Connection Protocol. Then the malware searches for the file command.txt, which must be created by the attacker and located in the same folder as the malware itself. If a file is detected, ATMitch reads its single-character content and executes the corresponding command:
The researchers write that the XFS standard library is used to control the ATM. In other words, malware works on any ATM that supports the XFS library, and the vast majority of them do. It is worth noting that in the file tv.dll there was only one Russian-language resource, which on the one hand indicates the low competence of programmers, on the other hand, about the domestic origin of the malware.
As we can see, in the vast majority of cases, even relatively complex ATM malware uses standard XFS libraries for its work. And why bother when working with these libraries is well documented, and the libraries themselves are publicly available? In this case, writing such malware does not require complex technical skills, and often even a novice programmer can easily cope with the task.
ATM Malware can potentially bring significant benefits to attackers. In the 10 years since the first malicious program designed specifically for attacks on ATMs was introduced, more than 30 families of malware in this category have been detected, with varying degrees of complexity and functionality.
The full collection of ATM malware binaries can be found here. Reviews and short descriptions of the main instances are available here.
Exiting kiosk mode
It is assumed that the user interacts with only one application, which displays information on the ATM screen and processes the data received from the user. This application works in kiosk mode, which means that the user's capabilities are limited: they can't run third-party programs or work with the OS in any way at all. Exiting kiosk mode is an attack aimed at bypassing the established restrictions and executing commands in the ATM OS.
The attack scenario looks like this:
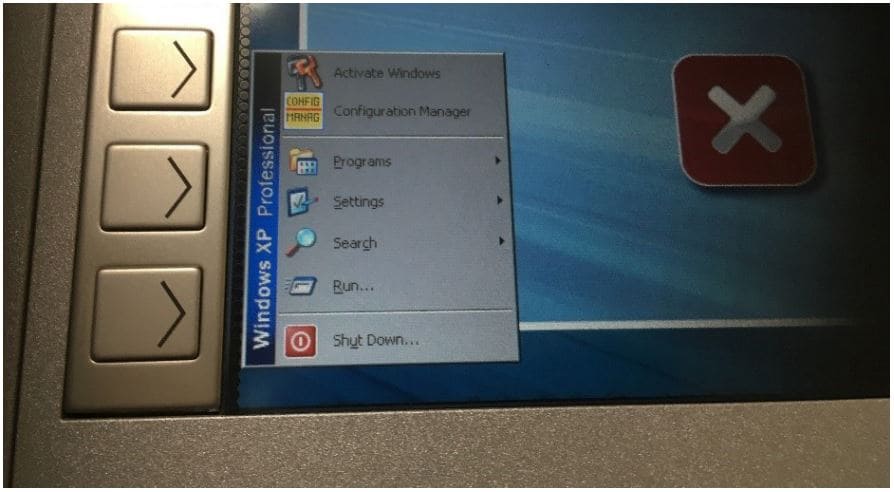
Vulnerabilities that allow you to bypass kiosk mode can also be contained in the SOFTWARE installed for additional protection. For example, two ATMs used software for video recording and monitoring security events. The app window was hidden, but during research, it turned out that it opens when you hover the mouse cursor over the corner of the monitor screen. The application had a file editing function, through which you could access the Windows Explorer application, and then - to any SOFTWARE on your computer, for example, Internet Explorer, FAR Manager.
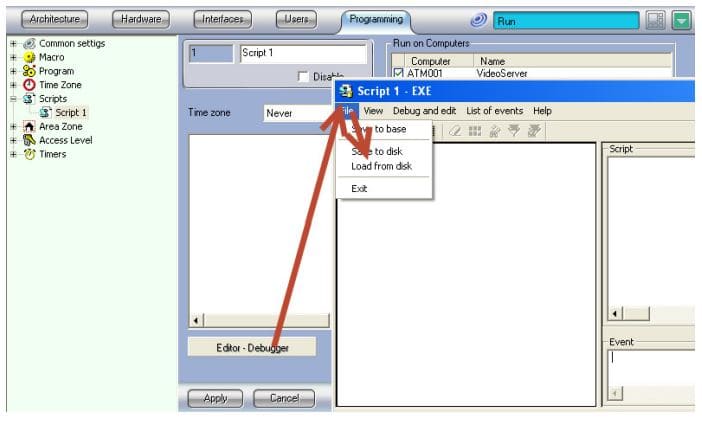
Exiting the kiosk mode in Intellect software.
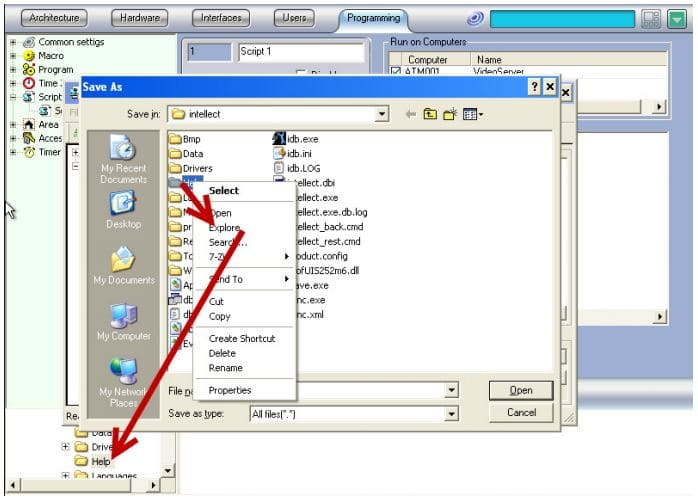
Connecting to a hard disk
Direct access to the ATM's hard drive is possible in 92% of cases.
You can bypass the installed security features and gain control over the dispenser by connecting it to the ATM's hard drive. Consider potential attack scenarios.
The easiest way is to connect directly to the hard drive. If the disk contents are not encrypted, an attacker can write malicious software containing commands for interacting with the dispenser to it. Then you need to add this program to the application Control whitelist-just make changes to the configuration files. Further, when the ATM is loaded in working ("protected") mode, the security SOFTWARE will start and function, but the intruder will be able to execute arbitrary code using malware. An attacker can even disable security features altogether, such as deleting files from Yandex.disk.
In addition, an attacker can steal sensitive information from the disk, for example, copy a separate application or a complete disk image, and then use modified versions for further attacks.
An attacker can download from an external storage medium and gain access to the file system. The boot order is set in the BIOS settings, which must be password protected. However, in 23% of ATMs, the password for accessing the BIOS was predictable, and in 8% it was not required at all. In one case, it was not possible to choose an administrator password, but for access with user privileges, the password was not required, and the user could change the download order. Another ATM was able to load the OS over the network using the Intel Boot Agent, bypassing the BIOS boot priorities.
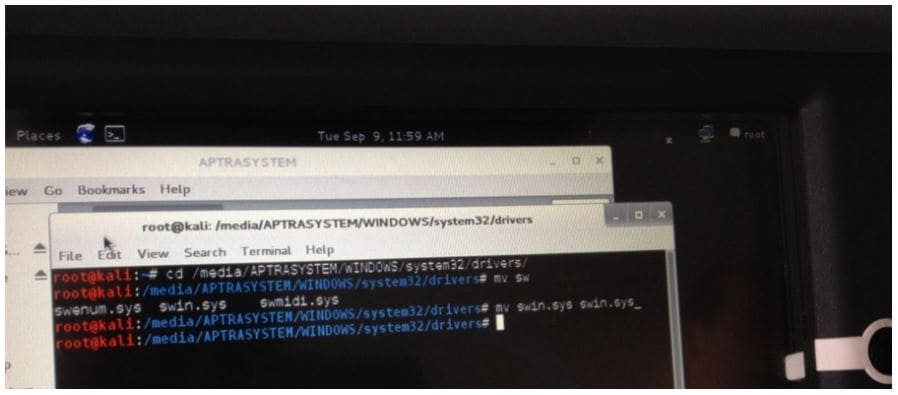
After booting from their own storage media, the attacker gets the opportunity to connect the original hard drive and continue the attack in the same ways as in the case of direct connection to the disk. The figure below shows how to rename the McAfee Solidcore for APTRA driver stored on the ATM's hard disk after booting the OS from an external storage device. As a result, the McAfee Solidcore SOFTWARE will not start when the ATM is loaded in operating mode.
Insecure firmware and facial recognition
In the latest versions of XFS and new ATM models, black box protection is provided in the form of encryption of communications between the ATM host and the dispenser. We decided to figure out how this happens using the example of the NCR USB S1 dispenser Board.
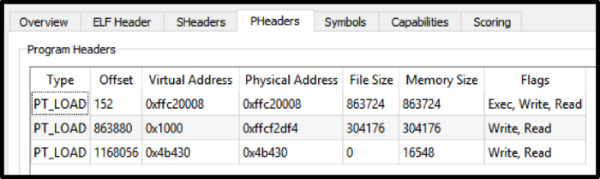
The firmware is an ELFfile for the NXP ColdFire processor (Motorola 68040) running on VxWorks v5. 5. 1.
There are two main sections of interest in the ELF file .text and .data. One of them contains code that runs all the main time (let's call it the main firmware) when the dispenser is connected to the system unit at the top of the ATM. The second one contains the bootloader code packaged using zlib (its local name is USB Secure Bootloader), which is responsible for filling in the firmware and running the main code. Also in the file, the characters remained uncut: take it and look for something interesting.
If you divide the code into the main components, you will get the following scheme (in order of subordination):

Since there is a lot of code in the firmware, it was decided to start by searching for all possible services, and then look at where the tasks are transferred.
As a result, we found the following services that should just do what we were looking for:
1) DispTranService (Dispenser Transaction Service): working with encrypted commands, forming bundles of banknotes, and authentication. You can say that the most interesting thing is here.

2) securityService: after authentication on the dispenser side, a session key is generated, which is sent to it in encrypted form at the request of the computer. This key will encrypt all important commands - issuing, forming a bundle of banknotes.
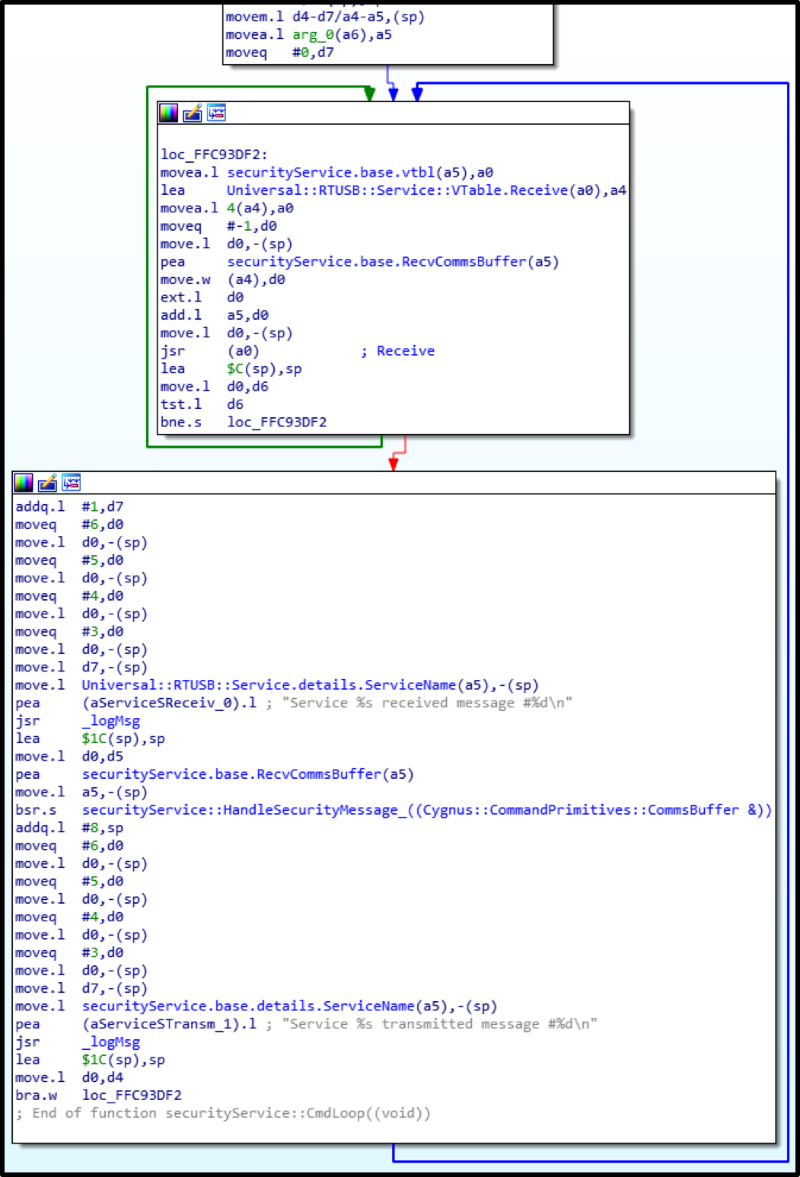
Subsequently, another service caught my eye: UsbDownloadService. Its task is to switch to bootloader when the dispenser is connected to a computer and the dispenser's firmware version does not match the one stored on the ATM's computer, in order to fill in the firmware that the OS should work with (located in the vendor's SOFTWARE folder on the computer). This service can also provide information about the firmware version.
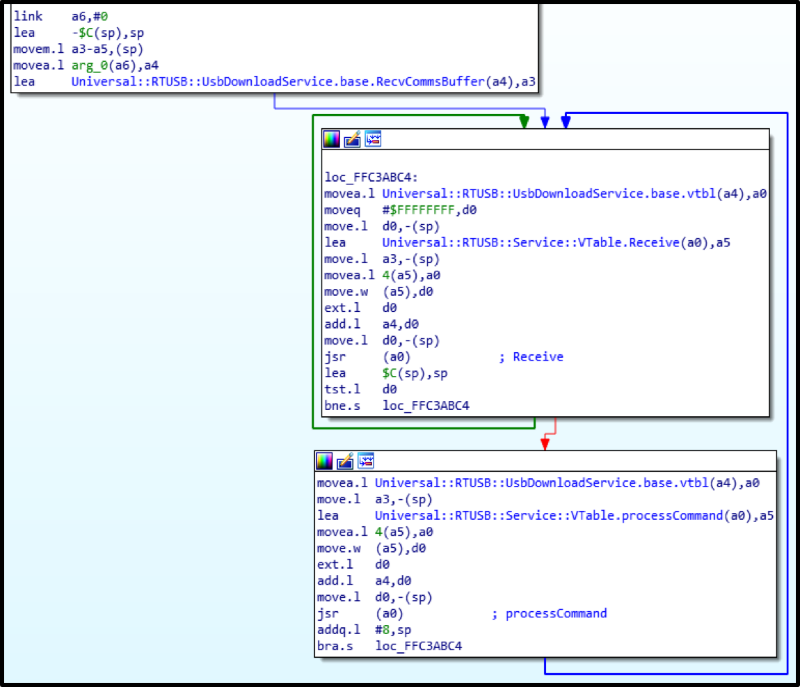
Physical authentication is implemented at the highest level and protects the ATM FROM simply sending commands to issue via USB without authorization. In this case, it means that only when the safe with money is open, you need to perform one of the following actions: remove and insert the lower cassette, switch the toggle switch on the back wall of the dispenser rack.
But all this is required ONLY IF the access level is set to the maximum, that is, physical. There are three of them: USB (0), logical (1) and physical (2). The other two are used by service providers and developers to debug and test the firmware. Well, the physical one is highly recommended by the vendor to be used by default.
The following describes a critical vulnerability that was fixed by the vendor at the time of publication of the article, but does not mean that it is automatically installed on all existing ATMs, which allowed you to execute any dispenser commands, including cash withdrawal, if you have access to the service area, but without access to the safe (for example, through a hole made in the ATM's front panel).
It turned out that UsbDownloadService accepts commands that do not require encryption.
As already mentioned, in the section .here lies the packaged loader code, which has not aroused interest for a long time.
While the presence of the bootloader was a mystery, the question remained open: how does the software on the computer fill the firmware? After all, nothing of the kind could be found in the main firmware.
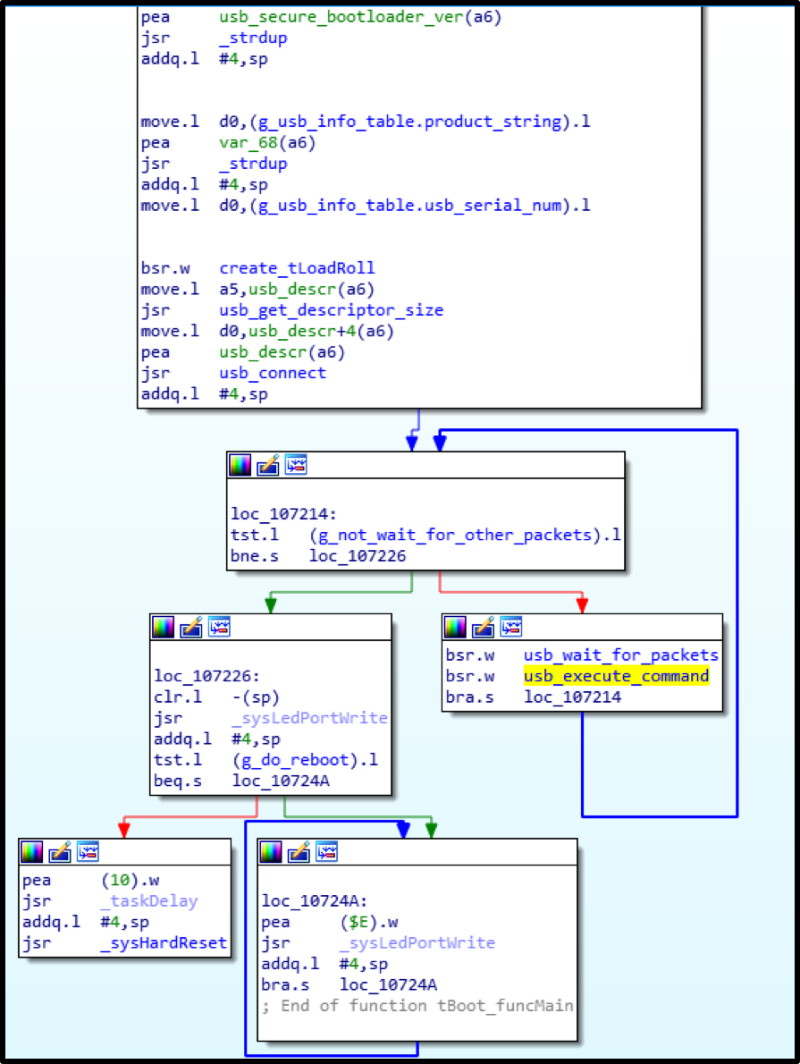
So, the bootloader is unpacked, loaded into IDA at offset 0x100000 -now you can explore... Only there are no characters!
It doesn't matter: comparing the main firmware with the bootloader code, reading the controller's datasheet and a certain picture begins to emerge.
It turned out that the firmware fill, although it looks protected, is not really protected. All you need to know is how to fill it correctly.
Quite a lot of effort and time was spent on fully understanding this process (for more information, see the report "Blackbox is dead-Long live Blackbox!" at the Black Hat 2018 conference in Las Vegas). What is the cost of re-soldering NVRAM memory, filling it with a backup in order to "bricked-up" the entire controller…
The result is the following algorithm for filling the firmware into the dispenser:
1) Generate a pair of RSA keys and upload the public key to the controller.
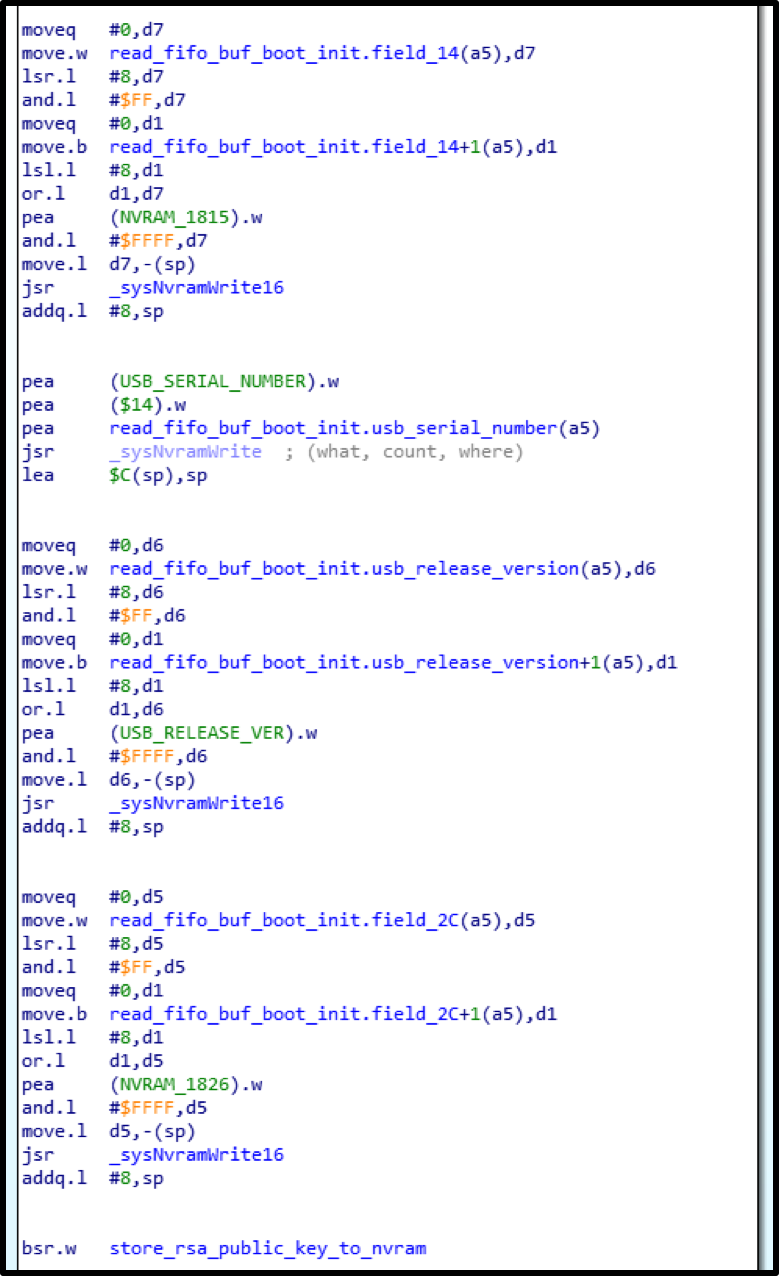
2) write sequentially the .data and .text sections from ELF to their physical addresses from the section headers.
3) Calculate SHA-1 from the recorded data, encrypt the hash with a private key, send it to the controller.

4) Calculate and send the sum of all recorded firmware words.
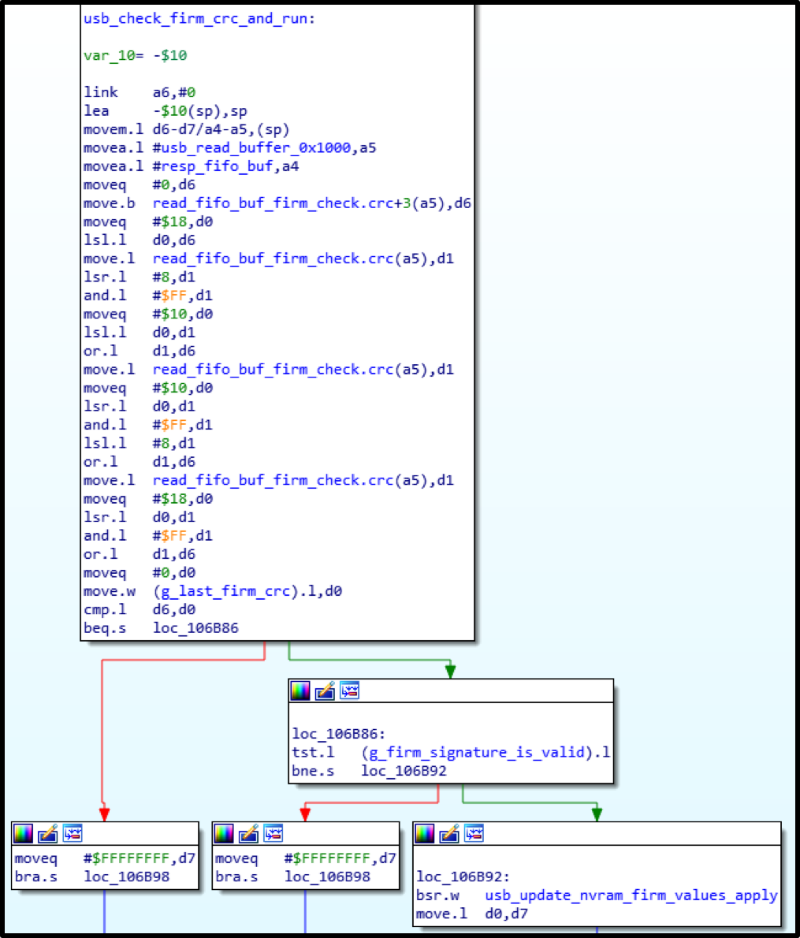
After that, if everything is calculated and recorded successfully, the main firmware will load.
It turned out that when recording firmware, there is only one restriction: the firmware version must be at least the current one. But after all, no one prevents us from replacing the firmware version in its data itself.
As a result, my special firmware with antisecurityfixes was uploaded and successfully launched!
By this time, the main firmware code was well studied, and commands for issuing banknotes were found. Now you can send them unencrypted, and the dispenser will be happy to accept them.

After everything experienced during the research (for example, a "bricked-up" real ATM), the result was so pleasant and compensating for the efforts that the algorithm wanted to be repeated with another large vendor.

The most real ATM began to buzz hard and willingly shared with us fresh crisp banknotes (in this case, vendor "wrappers"). No magic was used: just a laptop, a brain, and a USB cord.
We have once again seen that, guided by the principle of security through obscurity, it is impossible to provide proper protection. The proprietary nature of the code or firmware does not mean that an attacker will not get access to it at one point and take advantage of the vulnerabilities found. Everything necessary for the implementation of self-serving goals can be acquired if you have a certain amount of money.
CVE list:
FaceDancer21 is a mandatory tool for payment system pentesters. You can use it to emulate different USB devices. For example, you can create a device with a specific ID and bypass the list of allowed connected devices, determine what types of devices the USB port supports, which is useful when working with ATMs, and fuzz. which is convenient for searching for 0day in USB drivers. True to its name, FaceDancer allows you not only to change the device ID, but also to mask "hosts" as separate USB devices and Vice versa. But that's not all. The main advantage of the device is that it opens access to the USB bus using high-level programming languages through libraries in Python, C and Ruby. Knowing the API, a malicious user can easily gain access to the ATM host by spoofing the controller ID, and directly control peripheral devices inside the ATM, for example, a money dispenser, identifying themselves as legitimate devices that are allowed to work with the dispenser and thus bypass protection.
We will definitely write an article about the use of this wonderful device.
Carbanak. External attacks.
Financial institutions and banks are as full of holes as swiss cheese. According to Positive Technologies, 100% of banks are registered: web application vulnerabilities, network security flaws, and server configuration flaws. In 58% of banks, deficiencies in account and password management were identified. 22% of banks managed to overcome the network perimeter as part of external penetration testing. In 25% of banks, the nodes used to manage ATMs were compromised. In 17% of banks, card processing systems that allow manipulating the balance on card accounts of intruders are not sufficiently protected. The statistics are impressive.
An overview of compromising financial institutions is beyond the scope of this article we will definitely write about this separately.
Ten most common vulnerabilities on the network perimeter in banks.
In this section, we will focus on remote ATM operation.
As you already understood, knowing the API, you can gain control over the ATM host computer and directly control various peripheral devices installed inside the ATM Cabinet — a card reader, a PIN-code keypad, a touch screen, a banknote dispenser, etc.
But do not forget about the vulnerabilities of the ATM operating system, and Windows will have enough of them for many years to come.
At the Black Hat conference, Positive Technologies researchers demonstrated how long it would take attackers to install a microcomputer in an ATM service area to use it as a sniffer-an interceptor of the PIN code and credit card number-or a hardware skimmer that leaves no traces on the ATM's appearance. It took two minutes to unlock the ATM case, integrate the microcomputer, disguise it, and connect it to the Internet.
In preparation for the presentation, the Raspberry Pi was programmed to control the ATM peripheral modules. A Wi-Fi adapter was connected to the microcomputer, which could be connected from any device, for example, from a smartphone. Commands to issue money to the dispenser were sent via a specially implemented web interface. As an example, the issue of several banknotes was shown, and after some refinement of the sent code, the ATM immediately parted with all the pledged banknotes.
Needless to say, during the experiment, the ATM issued bills without leaving any records in its computer, and the ATM's built-in video camera, although it worked, was controlled using the Raspberry Pi, just like other devices inside the captured ATM.
Naturally, after such a fiery demonstration, back in 2014, hacker groups also became interested in ATMs.
Information about the activities of the group, called Cobalt, appeared only recently: in November 2016, the group-IB report was released. In it, Cobalt's activities are primarily associated with the previously known Buhtrap campaign. It is this group that is allegedly behind the theft of more than 1.8 billion rubles from Russian Bank accounts in 2015-2016. It is also assumed that some of the group members have moved to Cobalt, or even the core of Buhtrap has switched its attention to ATMs.
According to Group-IB, Buhtrap is the first criminal group that started using a network worm to defeat the entire Bank's infrastructure. As the main vector of penetration into the corporate network, the group used phishing mailings on behalf of the Bank of Russia or its representatives, and in a number of attacks, the distribution of malicious software through exploits was recorded, in particular using the Metel group infrastructure.
In 2016, there was a tendency for criminals to use publicly available utilities, software for legitimate penetration tests, in particular Cobalt Strike, and standard operating system functions. A significant example is the sensational attacks of the Carbanak group in 2016, which also targeted banks in Russia and Eastern Europe. This group used similar tools, as well as Metasploit. By the way, the source code of the Carbanak tool is still publicly available. Can be found here and here.
Targeted attacks using social engineering techniques and phishing emails with malicious code have become a real trend in recent years. As a rule, organizations (be it a Bank, an industrial Corporation, an IT company, or any other company) pay special attention to the implementation of continuous business processes, and to protect against attacks, they purchase and implement various expensive solutions. However, it is possible to close only some of the gaps on the perimeter with varying success, and the weakest link in the organization of protection, as always, is the person.
At the same time, attackers are increasingly using quite common and well-known tools, for example, software for conducting legitimate penetration tests or embedded OS functionality. Cobalt is another proof of this.
The attack example discussed in this report confirms this trend. Here, criminals used commercial Cobalt Strike software to conduct penetration tests, and in particular the multifunctional beacon Trojan that is part of it. The Beacon agent is the main payload and is a powerful Trojan. For remote management, the well-known legitimate Ammyy Admin SOFTWARE was also used, which anyone can download from the manufacturer's website. Other common tools were also used, for example: Mimikatz, PsExec, SoftPerfect Network Scanner, TeamViewer…
The General sequence of actions was as follows::
Mailings with malware -> penetration into the organization's network (opening an email from an untrusted source and running the attached file by an employee) ->> infection of the workstation ->>> pinning on the workstation through excessive user privileges ->>>> network research and attack development ->>>>> scanning the local network(the network was not provided with effective segmentation - > > > > > preparation for theft - > > > > > > > compromise of key resources (identifying computers of employees responsible for ATM operation - > > > > > > > ATM infection->>>>>>>>> stealing money from ATMs
(drops collect bills without any manipulation of the ATM).
Given the vulnerabilities of ATMs that we wrote about above, it is quite natural that one of the possible attack vectors on a Bank may be the compromise of its ATMs.
Network and MITM
To carry out attacks at the network level, an attacker first needs access to the network to which the ATM is connected. If the attacker is an employee of a Bank or provider, then they can gain access remotely. In other cases, a physical presence is required to open the service area, disconnect the Ethernet cable from the ATM, and connect your device to or instead of a modem. The attacker will then be able to connect to this device and conduct attacks on available network services or man-in-the-middle attacks. Sometimes the modem is located outside the ATM, and in order to connect to the network cable, you do not even need to have access to the service area.
The "last mile" of communication between an ATM and a processing center is rich in a wide variety of technologies that can serve as an entry point for a carder. Interaction can be carried out via a wired (telephone line or Ethernet) or wireless (Wi-Fi, cellular communication: CDMA, GSM, UMTS, LTE) communication method. Security mechanisms may include:
A study by the information security company Positive Technologies shows that an attack with spoofing processing is possible in 27% of ATMs. That is, in more than one out of five cases.
Another 58% of ATMs allow you to intercept data between the ATM and the processing center. The attack is possible due to the transmission of the full Track2 value in clear text and the lack of encryption in the interaction between the ATM and processing at the application level, since almost many ATMs use the NDC and DDC protocols, which do not provide for data encryption. By connecting to the ATM network and intercepting network traffic, an attacker can get information about payment cards.
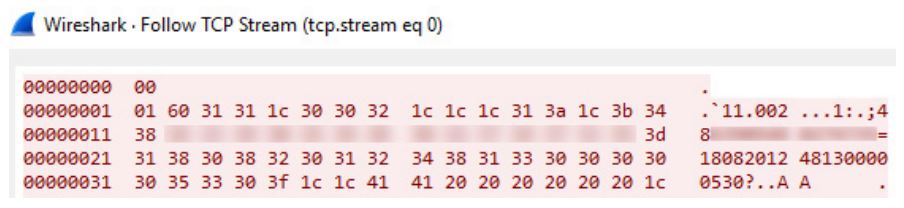
Interception of Track2 data in clear form.
If you want to understand in detail how the ATM works, an ATM emulator is available on github with the implementation of communication with processing via the NDC Protocol.
Documentation on the NDC Protocol, as well as NCR ATM maintenance, working with EMV, and much more can be found here.
Aptra Advance Supervisor NDC Guide
Aptra Advance Reference NDC Manual
How do attackers test their methods?
As we wrote above, almost all SOFTWARE can be found in open sources absolutely free of charge. You can also easily get documentation, examples, and descriptions. And in the presence of all this, even a novice can write a simple malware.
But how do attackers test all this?
It turns out that this isn't a problem either. On the Internet and very cheap, you can buy a completely working Used ATM without any sub-assumptions and documents at a price from $ 2000-15000. ATMs get to online Resellers either after they are debited from banks, or after the equipment of bankrupt organizations is sold. A lot of financial equipment was exported and is still being exported from the DPR and LPR, where the equipment is almost “ownerless” and if you have a fully working ATM with pre-installed software from one of the Ukrainian banks, you can buy it for “pennies” at all. Not only ATMs, but also Bank servers were seen on sale. However, the dispenser controller Board with firmware can be purchased not only in Donetsk, but also on eBay.

NCR USB S1 Dispenser controller
Result
Some manufacturers understand what an attack on an ATM can be fraught with, and issue security updates. And two-way authentication and cryptography are used as measures to counter attacks on the dispenser. But keep in mind that not all cryptography is properly implemented cryptography.
As reality shows, the existing compensation measures can protect the ATM from malware, but they are powerless against black box or network attacks. A huge number of security flaws and vulnerabilities that do not require any specific knowledge to exploit, make money machines a desirable target for those who want to get rich illegally, even if they do not have special training or experience with financial systems.
ATTENTION! THE FORUM DO NOT COMMIT AND DO NOT RECOMMEND THAT YOU COMMIT ILLEGAL ACTIONS OR GAIN UNAUTHORIZED ACCESS TO THE SYSTEMS. THIS ARTICLE AIMS TO POINT OUT PROBLEMS WITH SYSTEMS AND WARN USERS AND INSTITUTIONS AGAINST POTENTIAL ATTACKS.
The article uses materials from Diebold-Nixdorf, Positive Technologies, Talos Security, Kaspersky Lab, Vladimir Kononovich and Alexey Stennikov. Many thanks to the authors for their material and research.

Probably everyone who has ever withdrawn money from an ATM, hearing the pleasant noise of the dispenser, thought about how to get more of them. And no wonder, back in the 90s, after reviewing "Terminator 2", where John Connor hacks ATM using a laptop, some began to dream about how to repeat his atrocities. Despite the fact that terminators and Skynet have not yet been invented, attacks on ATMs are a reality. Today we will look at the most well-known methods of hacking ATM in the smallest nuances.
First, let's look at how the ATM works. In fact, it is a safe with a computer connected to the network. At the bottom, in the safe, money is stored in special cassettes. The safe is equipped with a mechanism for feeding bills, which is called a dispenser, which issues money from cassettes.
A service area is located above the safe, where a screen and keyboard are installed, which is called a "PINpad". Behind them is a computer. Sometimes it is an ordinary system unit, and sometimes even in such a case as a regular home computer. There is also service equipment: a card reader, a receipt printer, and security systems. All devices are connected to the system unit that performs the host function. Ports can be located directly on the system unit, and if they are not enough, a USB splitter is used.
The ATM is connected to the bank via a secure communication channel, usually using the NDC/DDC protocols (specifications at the bottom of the article) or X.25 (in general cases).
Money is stored in cassettes, on average, these cassettes are from four to six. There are approximately 2,500 banknotes in each cassette. Each cassette is set up for a banknote of its own denomination: instead of fifty-ruble notes, you will not be able to charge five-thousandth ones.
Some ATMs can accept money. Accepted bills are sent to a separate cassette. Usually, the ATM will not issue them, even if the main cash registers run out of money.
In the service area, there is everything that, in the opinion of the ATM manufacturers, does not allow you to get to the money. Probably, for this reason, the lid is most often plastic, and only a simple lock protects against unauthorized entry. By the way, both assembled locks and separate keys can be easily purchased online, since each manufacturer installs identical locks for their devices, and most banks, as a rule, do not think about replacing them with unique ones. Attackers can also make keys themselves or use very simple ones helpers tools.
The safe is much better protected – it is a Cabinet made of steel and concrete with two types of locks: a combination lock (electronic or limbic, sometimes electromechanical) and a key lock (usually a lever lock). In the safe there are devices that are directly related to money – a dispenser from which cash is issued, and a module for receiving cash. Often, the safe is equipped with sensors. They report tilt, noise, and temperature rise.
The list of SOFTWARE installed at the ATM is small:
- Operating system. Thanks to a strong lobby on the part of Microsoft, most ATMs run Windows OS of various modifications. Although you can find machines that are usually older, running QNX or AIX.
- Module management software
- SOFTWARE used for interaction with the user (ATM client or operator)
- SOFTWARE for communication with the processing center (which provides information and technological aspects of the transaction)
- antivirus or system integrity monitoring SOFTWARE
As mentioned above, probably 60% of ATMs still use Windows as their operating system. Yes, not just Windows, but Windows XP. Microsoft has not released updates for this OS since April 2014. Of course, all 0-days for Windows XP remain unresolved. Often, employees who serve ATMs believe that if the ATM is working, it is better to "leave it alone". For this reason, some ATMs still have the ability to detect, for example , an UN-patched critical vulnerability MS08-067, which allows remote code execution.
ATM modules are implemented on microcontrollers with real-time operating systems (RTOS). static analysis is poorly applicable to such systems.
At any given time, the ATM is in one of the following operating modes:
- Power Up-Download
- Offline - there Is no connection to the server or a connection is in progress
- Supervisor - mode for the collector or service engineer
- Out of service - the ATM is faulty, the money has run out, or the Bank has switched it to this mode
- In service -the main mode of operation
The first character of this string is the state type (indicated by the letters A..Z and some characters (,’.?)), it defines the aggregate. The remaining 24 characters are 8 decimal 3-digit numbers, each of which is a specific state setting (screen number to display, state transition conditions, list of actions). There can be any number of States of the same type.
In service mode
When the service mode starts, the ATM automatically starts executing state 000. This is usually state A (Card read state). In this state, the ATM displays a screen with an invitation to insert a card and switches the card reader to receive mode. The state is also responsible for reading the map and branching depending on the results of this operation.
Below is an example of the configuration of a typical state A:
000A001001011008004002001104
000 - room state
A - type state (Card read state)
001 -screen room (Screen number)
001 -number state, which go in case of successful card reading
011 -number state, which go in the event of an error reading the card
008 -the condition of reading 1
004 -condition read 2
002 -condition read 3
001 -the return card (immediately after reading or at the completion of the operation)
104 - transfer state, if the card is unknown to the Bank
Let's go through the parameters in more detail:
State type -everything is clear here: after determining the state type, the application knows how to interpret further parameters.
Screen number - is a link to a line with a text description of the screen that is displayed during the operation of this state.
Not every state has a screen.
The screen can have a number from 000 to 999. Screens that differ by 100 are usually reserved for different languages. So screen 010 and screen 210 are probably multilingual versions of the same screen. I'll tell you more about the screens later.
Transition state number in case of successful map reading - what state the application will start executing if the map is recognized and the data is read successfully.
In addition to States and screens, the ATM has another important configuration parameter-the financial institution table. The table of financial institutions contains data about which cards belong to which Bank, how to correctly parse data read from map tracks, and what to do next depending on this data. For example, if the card is local, then you can run one scenario, if the card is a third-party Bank, then you need to prohibit the branch of the scenario with mobile payments and balance verification.
Transition state number in case of problems with reading the map - if the map couldn't be read according to any of the suggested conditions - go to the state specified in this parameter. As a rule, this is the J (close state) state where we give the card away, show the screen with a suggestion to pick it up, and activate the timer after which the card retention mechanism will be launched. State J is also the last state in the event of a successful transaction.
Conditions for reading the card (3 consecutive parameters) are bitmasks that indicate the track numbers to be read and interaction with the chip, if any.
For example, Read Chip, Read Track 2 and Track 1, Read Track 1. If at least one of the conditions is triggered, then the other conditions are not met and the card is considered read. If none of the conditions are met, the card is considered unread.
The condition for the return of the card - the ATM can return the cards immediately after reading, or it can do it at the end after all operations are completed.
The rest of the states are arranged in a similar way:
- There are states for reading the sum from the keyboard and placing it in a special internal buffer;
- There are states for reading the pin code with a pin pad and then receiving the pin block in a special buffer;
- There are states for checking the entered data (for example, if the amount entered is less than the minimum amount, then redirects to the state with an error message).);
- There are states for selecting using side keys (the so-called FDK) and putting the characters of these keys (ABCD FGHI) in a special 8-byte buffer;
- There are states for zeroing and pre-setting buffers.
Going through all these States, the application sooner or later reaches the state of interaction with the host-state I (Transaction Request State). On this state, a request is generated from the data collected on previous States and sent to the server. The request is an ATM ID (Logical Unit Number), data from map tracks, data about previous transactions, data from the amount buffers, pin block, and function key presses (FDK buffer). Data is separated by a separator character. The server application receives the request and analyzes the Fdk buffer – it is from the contents of this buffer that the host understands what the ATM wants. After that, depending on the decision made, it sends a response containing:
- ID of the action to be performed;
- number of the screen to display during this action;
- contents of the receipt, if the receipt needs to be printed;
- the state that you need to go to after completing the action.
Upon completion of the required actions, the application sends a confirmation to the host and goes to the specified state. As a rule, this is the already known state J. In case of any failure, the application sends a message about the failure to the host and waits for a new Transaction Reply with the transition to the new state.
The ATM screen is a field of 32x16 cells. The screen can contain both graphic information and text information that is positioned relative to the cells. Fonts can be double-height.
The screen description is a string of text interspersed with control characters, such as screen clearing, cursor positioning, and font size. In most modern banks today, text is used only when entering amounts, and in other cases the screen is just a whole picture. However, there are also fully text-based screens.
Example of a screen displaying an image from the image table (\0c\1bP2018\1b\5c)
These are the screens that the state parameters refer to.
A set of States, screens, FIT, and timers is called an ATM script. Each scenario has its own number. After loading the ATM and connecting it to the network, it sends a message to the host with its ID and configuration number. If the configuration needs to be updated the host switches the ATM to "Out of Service" mode and starts loading the necessary parameters of the new configuration. The last parameter is the configuration number. Similarly, keys for pin block encryption, for dipping, and master keys are loaded.
What to do with chip cards if the chip couldn't be read depends on the script settings. You may be offered a narrower range of services, or you may simply refuse to serve them. The same applies to cards issued by other banks.
As we can see, an ATM is a constructor, sometimes with crooked hardware and outdated SOFTWARE. It is no wonder that such a system will sooner or later fall victim to logical attacks.
There is no reception against scrap
Sometimes logical attacks do not require complex hardware and SOFTWARE, just a screwdriver or a small crowbar is enough.
The first attack we studied is very simple. It is based on the sequence of actions laid down in the ATM. So, after receiving a positive response from the Bank about issuing the amount, the ATM gives a command to the dispenser and starts counting out the required number of banknotes, the reader is given a command to return the card to the client. Until the customer picks it up, the money is waiting in the delivery tray, and the flap of the tray will be closed. But if the fraudster holds the card, it gets stuck in the reader. And the money is already in the delivery device, only the door is closed. Using a screwdriver or crowbar, scammer squeezes out the flap of the tray and gets the money. At the same time, the ATM sends a report to the Bank about a failed transaction and the debited amount is returned to the account. As a result, the criminal takes the money, but the card is also in his hands. But in fact, the withdrawal of money from the ATM was not recorded and there was no debiting from the account.
The behavior when a card is detected that is not collected is fully configurable the ATM can either capture it or leave it in the path. The same applies to issuing a card before/after money, at the beginning/end of work, or during a power outage. What to do if an invalid PIN is entered, a false PIN is entered (if any), when the counter of invalid pins is reset, whether a card capture is necessary-everything is decided by the host. If the host does not instruct the ATM to capture the card, it will not capture it, even if it is ten times fake, stolen, or lost.
Simple and logical? What is not a logical attack? Until 2016, most banks worked like clockwork. But time passed and the vulnerability was fixed. Nevertheless, even now there are both banks that have not heard anything about this, and outdated machines. The world is very big…
Getting more complicated: black box
To implement such an attack, attackers drill a hole in the ATM's front panel to get to the USB bus or directly to the dispenser's cable. Having gained access to the cable, an attacker can connect the dispenser to his device, which is programmed to send commands to issue bills. Attacks of this type are called Black Box attacks.

ATM with a drilled hole in the service area
Let's start by using the service utilities and their modified versions, which were originally provided by ATM manufacturers to check the health of devices. One of the functions of such utilities is to test the operation of the dispenser, including issuing banknotes. To perform such a test, the engineer needs to confirm his legitimacy by opening the safe door or by manipulating the dispenser cassettes in some way. The logic is simple – if you can open the safe, then you have a key, i.e. you are a licensed engineer or collector. But no one canceled the release of new versions of IDA Pro, and replacing a couple of bytes in the utility with the "correct" ones allows you to" test " the output without any checks.
How does the attack work? An attacker opens or drills an ATM, connects the dispenser to their laptop, and leaves the crime scene, leaving the device plugged in. A laptop with drivers installed for the ATM dispenser and a PATCHED kdiag utility that does not require confirmation of opening the lid, issues a command to issue money at the operator's command. To organize remote operator access, a USB GPRS modem is connected to the laptop. The OS used is Windows, version XP or 7 for better compatibility with drivers.
Software from ATMDesk is also freely available.
Another way to get rich for intruders is to change the denomination of the issued banknotes, again using the diagnostic utility. As a result, the attacker receives money with the largest face value (for example, 100 dollars or euros) from the cash register, and the ATM SOFTWARE thinks that it issues the smallest of the available face values. Thus, a card with a balance of several hundred can get several thousand.
An insufficiently reliable NCR protection system is used in half of ATMs. Another 19% of machines do not have any protection measures against Black Box attacks at all.
XFS
XFS (CEN/XFS, formerly WOSA/XFS), or eXtensions for Financial Services, is a standard that provides a client-server architecture for interacting financial applications on the Windows platform with devices, in particular, for ATMs. The standard aims to unify the work of SOFTWARE with any hardware, regardless of the manufacturer, and provides a common API for this purpose.
If the ATM is managed by a Windows-based system, the task of software observation is to organize the interaction of the user (client or service personnel) with the processing center, which sends commands to the ATM, and manages the equipment that executes these commands. Messages are exchanged with the processing center using protocols (NDC/DDC or X. 25), the user works through the GUI, and the corresponding service providers are responsible for the operation of each ATM module (a kind of gateway to these modules). To transmit commands to service providers and further to equipment, as well as to return status messages, a level called XFS Manager is used-according to the WOSA concept. Any major ATM manufacturer (Wincor, NCR, Diebold) has its own implementation of both XFS and banking applications. However, there is alternative software on the market that meets all standards and is not tied to a specific vendor.
There are several implementations of XFS managers (including open source ones) written in C++, and theoretically libraries of service providers written for one Manager should also be suitable for all others, but in fact sometimes a library written by a specific vendor for a specific XFS Manager works only with this Manager. There is also Java XFS with its own libraries that are not compatible with classic managers.
Thus, any application developed with the XFS standard in mind can manage low-level objects using only the logic described in this standard. And this application may well be a Tyupkin backdoor or any other malicious program.
For example, a dispenser, which is the most interesting device for intruders, can issue money without any authorization. And in some models of ATMs, you can use XFS to programmatically open the safe and unlock the cassettes.
As applied to the card reader, XFS allows you to read and write data on the magnetic stripe of a Bank card and even get the transaction history stored on the EMV card chip.
We should also mention the encrypted PIN – pad (EPP). It is assumed that the PIN cannot be intercepted, because it is entered on the ATM pin pad and directly inside the encryption module turns into a pin block (for this purpose, the EPP cryptographic key contains keys that are paired in the Bank's hardware security module). However, XFS allows us to use a pin pad in two modes:
- open – for entering various numeric values, such as the amount to be issued;
- secure, where the EPP cryptographic key switches to enter the pin code and encryption keys.
You may ask, but what about authentication and exclusive access? And surely you can't get the specifications for the standard? Unfortunately, this is not about XFS. This standard does not provide for any authentication, and exclusive access to service providers is implemented, but not for security reasons. This is just a single-threaded command sending function, so that you don't accidentally break a delicate piece of hardware by sending two identical commands in parallel.
All specifications can be found here. Google will tell you even more about XFS.
If you are interested, the SDK can be found here.
XFS manager 3 with the wsxfs.DLL library download
Integrity monitoring tools
Some banks sometimes use software integrity controls on their ATMs that promise to prevent unauthorized code execution based on a whitelist, control device and storage connections, and other ways to counter attacks.
But we should not forget that this is, first of all, software, and it, like any other SOFTWARE, is not perfect. It may be vulnerable to attacks such as going outside the kiosk (bypassing the full-screen mode restriction and gaining access to the operating system), bypassing whitelists, buffer overflow, raising privileges to the SYSTEM user level, and others. As you can see, often existing vulnerabilities allow villains to gain access to the operating system and do their dirty deeds.
Malware
On one of the russian-language closed carder forums vendors, rumors about the possibility of emptying ATMs have been floating around since mid-2008, but only in 2009, when analysts were able to obtain the first samples of malware, the financial world was stirred by the appearance of the Trojan Backdoor.Win32.Skimer: this was the first known malware that targets ATMs. Skimer attacked Wincor Nixdorf ATMs. The cybercriminals used the malware to empty the dispenser and obtain data from plastic cards processed at the infected ATM.
Since then, a lot of water has flowed, and ATMs of various manufacturers have repeatedly been exposed to malware. Entire families of such malicious programs have emerged.
There are four main stages in the scheme of stealing money from ATMs using malware:
- An attacker gains access to the machine, either locally or remotely.
- Malicious code is being injected into the ATM system.
- As a rule, the infection is followed by a reboot of the ATM. The system reboots, seemingly, to normal mode, but at the same time it is under the control of a malicious program, i.e. intruders.
- The final stage is theft of money.
There are several different ways to classify ATM Malware (ATM malware). In terms of functionality, all such programs can be divided into two types: virtual skimmers and Direct Dispense utilities.
The purpose of skimmers is to steal the data of a bank card and the transaction being carried out, and, if possible, even a PIN code, if the encryption keys of the PIN keyboard were previously compromised.
Direct cash withdrawal utilities have a feature popularly known as jackpotting, which allows attackers to perform unauthorized withdrawal of money from an ATM without the need to authorize the transaction on the Bank's side. At the same time, there is malicious software that combines the functionality of a skimmer and jackpotting.
Over the past 10 years, more than 30 different malware families for ATMs have been discovered. Let's look at some of the most popular and significant ones and try to highlight the common features and unique differences of each one.

Ploutus
Ploutus is the malware family with the highest number of detected samples. Most of them were registered in Mexico. Ploutus is a typical example of direct search malware. To download the malware, attackers must have access to USB ports or a CD drive.
As an example, we can cite one of the recent modifications, Ploutus-D, which was initially focused on Diebold ATMs, which are widely distributed in the United States. However, the malware interacts with the ATM via the KAL Kalignite multi-vendor platform, and after a simple modification of the Ploutus-D code, it can also be used to attack ATMs of other manufacturers.

Skimer
Skimer is one of the first Trojans for ATMs. Functionally, this malware fully justifies its name and is essentially a virtual skimming device that copies data from the magnetic stripe of a Bank card.
In addition, Skimer is a backdoor and can be used for unauthorized withdrawal of money from an ATM. If the attacker knows the key to activate the program, the malware displays a menu from which you can issue money from each of the four dispenser cassettes.
Most other ATM malware families operate on a similar principle. Attackers must provide themselves with physical access to the ATM's service area in order to connect an external drive with malware. After the malware is introduced into the system, the attacker must enter a unique code to activate the cash withdrawal process.
Tyupkin
The real glory came to malware for ATMs with the appearance of the Tyupkin Trojan, whose activity was first recorded in 2014. Since then, many ATMs around the world have been attacked.
A distinctive feature of Tyupkin is its ability to limit the time of its activity to certain hours and days of the week. Some of the first varieties of Tyupkin could initially only be launched on Sunday and Monday nights.
In addition, the Trojan has a self-defense function. Immediately before cash withdrawal, Tyupkin disables all network connections so that if suspicious activity is detected on the Bank's side, the monitoring service will not be able to turn off the ATM, thereby interrupting the fraudulent operation.
Alice
The principle of operation of Alice is the same as that of many other ATM malware. The installation requires physical access to the ATM system. After starting, Alice asks for an access code to continue working. If you enter the correct activation code, the malware gets access to the banknote dispenser and allows you to issue cash.

Cutlet Maker
In 2017, cybercriminals started selling ATM Malware-as-a-Service on the darknet. For $ 5,000, anyone can purchase a package of ready-to-use Cutlet Maker malware and video instructions on opening an ATM. Those who bought the service need to choose a suitable ATM (the authors of malware recommend Wincor Nixdorf), use the instructions for hacking its service part, download the malware and pay the service organizers for its activation to start the process of issuing money.

Cutlet Maker Interface
In the case of Cutlet Maker, the potential user of the service may have minimal knowledge about the target of the attack. This example shows how such schemes reduce the entry threshold to this type of crime and lead to a significant increase in the number of cybercriminals.
FASTCash
FASTCash is a unique tool that the North Korean hacker group Lazarus used to attack financial institutions in more than 20 countries around the world. In total, several tens of millions of dollars were stolen in 2016-2018.
A special feature of FASTCash is the mechanism of its operation and orientation to the IBM AIX OS. Hackers introduced the Trojan into a legitimate process on the application server of processing systems that control transactions in the ATM network and run under AIX.
After the server was compromised, the Trojan was able to create fake ISO 8583 messages (a standard describing the transmission process and format of financial messages of systems that process Bank card data), generating a response confirming a fraudulent cash withdrawal operation at ATMs. It should be noted that in all cases, successful attacks were possible due to the fact that financial organizations used outdated versions of AIX-without the necessary security updates.

How FastCash works
This is another example of a targeted attack on financial institutions, in this case through processing systems. At the same time, the level of complexity and development of FASTCash is very high and cannot be compared with any other” standard " ATM Malware.
ATMitch
Studying malware showed that after installing under the name tv.dll, ATMitch a remote connection to the ATM is opened from inside the Bank using the Remote Desktop Connection Protocol. Then the malware searches for the file command.txt, which must be created by the attacker and located in the same folder as the malware itself. If a file is detected, ATMitch reads its single-character content and executes the corresponding command:
- O’ – open the dispenser
- ‘D’ – issue money
- ‘I’ – Initialize XFS Library
- ‘U’ - Unblock XFS
- ‘S’ –Installation
- ‘E’ - Output
- ‘G’ – Get the dispenser ID
- ‘L’ – Set the dispenser ID
- ‘C’ - Cancel
The researchers write that the XFS standard library is used to control the ATM. In other words, malware works on any ATM that supports the XFS library, and the vast majority of them do. It is worth noting that in the file tv.dll there was only one Russian-language resource, which on the one hand indicates the low competence of programmers, on the other hand, about the domestic origin of the malware.
As we can see, in the vast majority of cases, even relatively complex ATM malware uses standard XFS libraries for its work. And why bother when working with these libraries is well documented, and the libraries themselves are publicly available? In this case, writing such malware does not require complex technical skills, and often even a novice programmer can easily cope with the task.
ATM Malware can potentially bring significant benefits to attackers. In the 10 years since the first malicious program designed specifically for attacks on ATMs was introduced, more than 30 families of malware in this category have been detected, with varying degrees of complexity and functionality.
The full collection of ATM malware binaries can be found here. Reviews and short descriptions of the main instances are available here.
Exiting kiosk mode
It is assumed that the user interacts with only one application, which displays information on the ATM screen and processes the data received from the user. This application works in kiosk mode, which means that the user's capabilities are limited: they can't run third-party programs or work with the OS in any way at all. Exiting kiosk mode is an attack aimed at bypassing the established restrictions and executing commands in the ATM OS.
The attack scenario looks like this:
- An attacker connects a device to the ATM's USB or PS/2 interface to emulate the keyboard and user input, for example, based on Raspberry Pi, Teensy, or BeagleBone. At the next stage, the attack can be fully automated or connected to this device remotely.
- Then the attacker gets access to the OS. In all cases, it was possible to do this using hot keys, since there were no restrictions on entering information, or not all possible combinations were provided.
- The final step is to bypass security measures designed to prevent the execution of extraneous code, and get the opportunity to send a command to the dispenser.

Vulnerabilities that allow you to bypass kiosk mode can also be contained in the SOFTWARE installed for additional protection. For example, two ATMs used software for video recording and monitoring security events. The app window was hidden, but during research, it turned out that it opens when you hover the mouse cursor over the corner of the monitor screen. The application had a file editing function, through which you could access the Windows Explorer application, and then - to any SOFTWARE on your computer, for example, Internet Explorer, FAR Manager.

Exiting the kiosk mode in Intellect software.

Connecting to a hard disk
Direct access to the ATM's hard drive is possible in 92% of cases.
You can bypass the installed security features and gain control over the dispenser by connecting it to the ATM's hard drive. Consider potential attack scenarios.
The easiest way is to connect directly to the hard drive. If the disk contents are not encrypted, an attacker can write malicious software containing commands for interacting with the dispenser to it. Then you need to add this program to the application Control whitelist-just make changes to the configuration files. Further, when the ATM is loaded in working ("protected") mode, the security SOFTWARE will start and function, but the intruder will be able to execute arbitrary code using malware. An attacker can even disable security features altogether, such as deleting files from Yandex.disk.
In addition, an attacker can steal sensitive information from the disk, for example, copy a separate application or a complete disk image, and then use modified versions for further attacks.
An attacker can download from an external storage medium and gain access to the file system. The boot order is set in the BIOS settings, which must be password protected. However, in 23% of ATMs, the password for accessing the BIOS was predictable, and in 8% it was not required at all. In one case, it was not possible to choose an administrator password, but for access with user privileges, the password was not required, and the user could change the download order. Another ATM was able to load the OS over the network using the Intel Boot Agent, bypassing the BIOS boot priorities.
After booting from their own storage media, the attacker gets the opportunity to connect the original hard drive and continue the attack in the same ways as in the case of direct connection to the disk. The figure below shows how to rename the McAfee Solidcore for APTRA driver stored on the ATM's hard disk after booting the OS from an external storage device. As a result, the McAfee Solidcore SOFTWARE will not start when the ATM is loaded in operating mode.

Insecure firmware and facial recognition
In the latest versions of XFS and new ATM models, black box protection is provided in the form of encryption of communications between the ATM host and the dispenser. We decided to figure out how this happens using the example of the NCR USB S1 dispenser Board.
The firmware is an ELFfile for the NXP ColdFire processor (Motorola 68040) running on VxWorks v5. 5. 1.
There are two main sections of interest in the ELF file .text and .data. One of them contains code that runs all the main time (let's call it the main firmware) when the dispenser is connected to the system unit at the top of the ATM. The second one contains the bootloader code packaged using zlib (its local name is USB Secure Bootloader), which is responsible for filling in the firmware and running the main code. Also in the file, the characters remained uncut: take it and look for something interesting.
If you divide the code into the main components, you will get the following scheme (in order of subordination):
- A thread that receives USB packets and distributes them to services.
- Services are the main performing units, each of them has its own role and each has its own tasks (classes).
- Classes-here these are tasks that a particular service can perform using controllers.
- Controllers are actually "workers" that validate tasks sent to them, perform them, and generate response packets.

Since there is a lot of code in the firmware, it was decided to start by searching for all possible services, and then look at where the tasks are transferred.
As a result, we found the following services that should just do what we were looking for:
1) DispTranService (Dispenser Transaction Service): working with encrypted commands, forming bundles of banknotes, and authentication. You can say that the most interesting thing is here.

2) securityService: after authentication on the dispenser side, a session key is generated, which is sent to it in encrypted form at the request of the computer. This key will encrypt all important commands - issuing, forming a bundle of banknotes.

Subsequently, another service caught my eye: UsbDownloadService. Its task is to switch to bootloader when the dispenser is connected to a computer and the dispenser's firmware version does not match the one stored on the ATM's computer, in order to fill in the firmware that the OS should work with (located in the vendor's SOFTWARE folder on the computer). This service can also provide information about the firmware version.

Physical authentication is implemented at the highest level and protects the ATM FROM simply sending commands to issue via USB without authorization. In this case, it means that only when the safe with money is open, you need to perform one of the following actions: remove and insert the lower cassette, switch the toggle switch on the back wall of the dispenser rack.

But all this is required ONLY IF the access level is set to the maximum, that is, physical. There are three of them: USB (0), logical (1) and physical (2). The other two are used by service providers and developers to debug and test the firmware. Well, the physical one is highly recommended by the vendor to be used by default.
The following describes a critical vulnerability that was fixed by the vendor at the time of publication of the article, but does not mean that it is automatically installed on all existing ATMs, which allowed you to execute any dispenser commands, including cash withdrawal, if you have access to the service area, but without access to the safe (for example, through a hole made in the ATM's front panel).
It turned out that UsbDownloadService accepts commands that do not require encryption.
As already mentioned, in the section .here lies the packaged loader code, which has not aroused interest for a long time.

While the presence of the bootloader was a mystery, the question remained open: how does the software on the computer fill the firmware? After all, nothing of the kind could be found in the main firmware.

So, the bootloader is unpacked, loaded into IDA at offset 0x100000 -now you can explore... Only there are no characters!
It doesn't matter: comparing the main firmware with the bootloader code, reading the controller's datasheet and a certain picture begins to emerge.

It turned out that the firmware fill, although it looks protected, is not really protected. All you need to know is how to fill it correctly.
Quite a lot of effort and time was spent on fully understanding this process (for more information, see the report "Blackbox is dead-Long live Blackbox!" at the Black Hat 2018 conference in Las Vegas). What is the cost of re-soldering NVRAM memory, filling it with a backup in order to "bricked-up" the entire controller…
The result is the following algorithm for filling the firmware into the dispenser:
1) Generate a pair of RSA keys and upload the public key to the controller.

2) write sequentially the .data and .text sections from ELF to their physical addresses from the section headers.

3) Calculate SHA-1 from the recorded data, encrypt the hash with a private key, send it to the controller.

4) Calculate and send the sum of all recorded firmware words.

After that, if everything is calculated and recorded successfully, the main firmware will load.
It turned out that when recording firmware, there is only one restriction: the firmware version must be at least the current one. But after all, no one prevents us from replacing the firmware version in its data itself.
As a result, my special firmware with antisecurityfixes was uploaded and successfully launched!
By this time, the main firmware code was well studied, and commands for issuing banknotes were found. Now you can send them unencrypted, and the dispenser will be happy to accept them.

After everything experienced during the research (for example, a "bricked-up" real ATM), the result was so pleasant and compensating for the efforts that the algorithm wanted to be repeated with another large vendor.

The most real ATM began to buzz hard and willingly shared with us fresh crisp banknotes (in this case, vendor "wrappers"). No magic was used: just a laptop, a brain, and a USB cord.
We have once again seen that, guided by the principle of security through obscurity, it is impossible to provide proper protection. The proprietary nature of the code or firmware does not mean that an attacker will not get access to it at one point and take advantage of the vulnerabilities found. Everything necessary for the implementation of self-serving goals can be acquired if you have a certain amount of money.
CVE list:
- CVE-2017-17668 (NCR S1 Dispenser),
- CVE-2018-5717 (NCR S2 Dispenser).
FaceDancer21 is a mandatory tool for payment system pentesters. You can use it to emulate different USB devices. For example, you can create a device with a specific ID and bypass the list of allowed connected devices, determine what types of devices the USB port supports, which is useful when working with ATMs, and fuzz. which is convenient for searching for 0day in USB drivers. True to its name, FaceDancer allows you not only to change the device ID, but also to mask "hosts" as separate USB devices and Vice versa. But that's not all. The main advantage of the device is that it opens access to the USB bus using high-level programming languages through libraries in Python, C and Ruby. Knowing the API, a malicious user can easily gain access to the ATM host by spoofing the controller ID, and directly control peripheral devices inside the ATM, for example, a money dispenser, identifying themselves as legitimate devices that are allowed to work with the dispenser and thus bypass protection.
We will definitely write an article about the use of this wonderful device.
Carbanak. External attacks.
Financial institutions and banks are as full of holes as swiss cheese. According to Positive Technologies, 100% of banks are registered: web application vulnerabilities, network security flaws, and server configuration flaws. In 58% of banks, deficiencies in account and password management were identified. 22% of banks managed to overcome the network perimeter as part of external penetration testing. In 25% of banks, the nodes used to manage ATMs were compromised. In 17% of banks, card processing systems that allow manipulating the balance on card accounts of intruders are not sufficiently protected. The statistics are impressive.
An overview of compromising financial institutions is beyond the scope of this article we will definitely write about this separately.
Ten most common vulnerabilities on the network perimeter in banks.
In this section, we will focus on remote ATM operation.
As you already understood, knowing the API, you can gain control over the ATM host computer and directly control various peripheral devices installed inside the ATM Cabinet — a card reader, a PIN-code keypad, a touch screen, a banknote dispenser, etc.
But do not forget about the vulnerabilities of the ATM operating system, and Windows will have enough of them for many years to come.
At the Black Hat conference, Positive Technologies researchers demonstrated how long it would take attackers to install a microcomputer in an ATM service area to use it as a sniffer-an interceptor of the PIN code and credit card number-or a hardware skimmer that leaves no traces on the ATM's appearance. It took two minutes to unlock the ATM case, integrate the microcomputer, disguise it, and connect it to the Internet.
In preparation for the presentation, the Raspberry Pi was programmed to control the ATM peripheral modules. A Wi-Fi adapter was connected to the microcomputer, which could be connected from any device, for example, from a smartphone. Commands to issue money to the dispenser were sent via a specially implemented web interface. As an example, the issue of several banknotes was shown, and after some refinement of the sent code, the ATM immediately parted with all the pledged banknotes.
Needless to say, during the experiment, the ATM issued bills without leaving any records in its computer, and the ATM's built-in video camera, although it worked, was controlled using the Raspberry Pi, just like other devices inside the captured ATM.
Naturally, after such a fiery demonstration, back in 2014, hacker groups also became interested in ATMs.
Information about the activities of the group, called Cobalt, appeared only recently: in November 2016, the group-IB report was released. In it, Cobalt's activities are primarily associated with the previously known Buhtrap campaign. It is this group that is allegedly behind the theft of more than 1.8 billion rubles from Russian Bank accounts in 2015-2016. It is also assumed that some of the group members have moved to Cobalt, or even the core of Buhtrap has switched its attention to ATMs.
According to Group-IB, Buhtrap is the first criminal group that started using a network worm to defeat the entire Bank's infrastructure. As the main vector of penetration into the corporate network, the group used phishing mailings on behalf of the Bank of Russia or its representatives, and in a number of attacks, the distribution of malicious software through exploits was recorded, in particular using the Metel group infrastructure.
In 2016, there was a tendency for criminals to use publicly available utilities, software for legitimate penetration tests, in particular Cobalt Strike, and standard operating system functions. A significant example is the sensational attacks of the Carbanak group in 2016, which also targeted banks in Russia and Eastern Europe. This group used similar tools, as well as Metasploit. By the way, the source code of the Carbanak tool is still publicly available. Can be found here and here.
Targeted attacks using social engineering techniques and phishing emails with malicious code have become a real trend in recent years. As a rule, organizations (be it a Bank, an industrial Corporation, an IT company, or any other company) pay special attention to the implementation of continuous business processes, and to protect against attacks, they purchase and implement various expensive solutions. However, it is possible to close only some of the gaps on the perimeter with varying success, and the weakest link in the organization of protection, as always, is the person.
At the same time, attackers are increasingly using quite common and well-known tools, for example, software for conducting legitimate penetration tests or embedded OS functionality. Cobalt is another proof of this.
The attack example discussed in this report confirms this trend. Here, criminals used commercial Cobalt Strike software to conduct penetration tests, and in particular the multifunctional beacon Trojan that is part of it. The Beacon agent is the main payload and is a powerful Trojan. For remote management, the well-known legitimate Ammyy Admin SOFTWARE was also used, which anyone can download from the manufacturer's website. Other common tools were also used, for example: Mimikatz, PsExec, SoftPerfect Network Scanner, TeamViewer…
The General sequence of actions was as follows::
Mailings with malware -> penetration into the organization's network (opening an email from an untrusted source and running the attached file by an employee) ->> infection of the workstation ->>> pinning on the workstation through excessive user privileges ->>>> network research and attack development ->>>>> scanning the local network(the network was not provided with effective segmentation - > > > > > preparation for theft - > > > > > > > compromise of key resources (identifying computers of employees responsible for ATM operation - > > > > > > > ATM infection->>>>>>>>> stealing money from ATMs
(drops collect bills without any manipulation of the ATM).
Given the vulnerabilities of ATMs that we wrote about above, it is quite natural that one of the possible attack vectors on a Bank may be the compromise of its ATMs.
Network and MITM
To carry out attacks at the network level, an attacker first needs access to the network to which the ATM is connected. If the attacker is an employee of a Bank or provider, then they can gain access remotely. In other cases, a physical presence is required to open the service area, disconnect the Ethernet cable from the ATM, and connect your device to or instead of a modem. The attacker will then be able to connect to this device and conduct attacks on available network services or man-in-the-middle attacks. Sometimes the modem is located outside the ATM, and in order to connect to the network cable, you do not even need to have access to the service area.
The "last mile" of communication between an ATM and a processing center is rich in a wide variety of technologies that can serve as an entry point for a carder. Interaction can be carried out via a wired (telephone line or Ethernet) or wireless (Wi-Fi, cellular communication: CDMA, GSM, UMTS, LTE) communication method. Security mechanisms may include:
- hardware or software tools for VPN support (both standard, built-in OS, and from third-party vendors);
- SSL/TLS (both specific to the specific ATM model, and from third-party vendors);
- encryption;
- message authentication.
A study by the information security company Positive Technologies shows that an attack with spoofing processing is possible in 27% of ATMs. That is, in more than one out of five cases.
Another 58% of ATMs allow you to intercept data between the ATM and the processing center. The attack is possible due to the transmission of the full Track2 value in clear text and the lack of encryption in the interaction between the ATM and processing at the application level, since almost many ATMs use the NDC and DDC protocols, which do not provide for data encryption. By connecting to the ATM network and intercepting network traffic, an attacker can get information about payment cards.

Interception of Track2 data in clear form.
If you want to understand in detail how the ATM works, an ATM emulator is available on github with the implementation of communication with processing via the NDC Protocol.
Documentation on the NDC Protocol, as well as NCR ATM maintenance, working with EMV, and much more can be found here.
Aptra Advance Supervisor NDC Guide
Aptra Advance Reference NDC Manual
How do attackers test their methods?
As we wrote above, almost all SOFTWARE can be found in open sources absolutely free of charge. You can also easily get documentation, examples, and descriptions. And in the presence of all this, even a novice can write a simple malware.
But how do attackers test all this?
It turns out that this isn't a problem either. On the Internet and very cheap, you can buy a completely working Used ATM without any sub-assumptions and documents at a price from $ 2000-15000. ATMs get to online Resellers either after they are debited from banks, or after the equipment of bankrupt organizations is sold. A lot of financial equipment was exported and is still being exported from the DPR and LPR, where the equipment is almost “ownerless” and if you have a fully working ATM with pre-installed software from one of the Ukrainian banks, you can buy it for “pennies” at all. Not only ATMs, but also Bank servers were seen on sale. However, the dispenser controller Board with firmware can be purchased not only in Donetsk, but also on eBay.

NCR USB S1 Dispenser controller
Result
Some manufacturers understand what an attack on an ATM can be fraught with, and issue security updates. And two-way authentication and cryptography are used as measures to counter attacks on the dispenser. But keep in mind that not all cryptography is properly implemented cryptography.
As reality shows, the existing compensation measures can protect the ATM from malware, but they are powerless against black box or network attacks. A huge number of security flaws and vulnerabilities that do not require any specific knowledge to exploit, make money machines a desirable target for those who want to get rich illegally, even if they do not have special training or experience with financial systems.
ATTENTION! THE FORUM DO NOT COMMIT AND DO NOT RECOMMEND THAT YOU COMMIT ILLEGAL ACTIONS OR GAIN UNAUTHORIZED ACCESS TO THE SYSTEMS. THIS ARTICLE AIMS TO POINT OUT PROBLEMS WITH SYSTEMS AND WARN USERS AND INSTITUTIONS AGAINST POTENTIAL ATTACKS.
The article uses materials from Diebold-Nixdorf, Positive Technologies, Talos Security, Kaspersky Lab, Vladimir Kononovich and Alexey Stennikov. Many thanks to the authors for their material and research.

