Friend
Professional
- Messages
- 2,675
- Reaction score
- 1,064
- Points
- 113
The study reveals time-based attacks that actually work.
A new study presented at the DEF CON conference reveals best practices for attacks on web servers that use timing dependencies. Attacks allow you to detect hidden vulnerabilities, bypass defenses, and gain access to private server areas without the need for complex settings.
Basic techniques of timing attacks
The study focuses on three key techniques:
Detection of hidden attack surfaces: in the course of the study, a technique was developed that allows you to find hidden parameters, HTTP headers, and other elements that can be used for further attacks. This is achieved by measuring the server's response time to various requests, where small changes in latency can indicate the presence of hidden parameters or even vulnerabilities.
In particular, the author used the Param Miner tool, which performs mass scanning of parameters based on response time. For example, a server that processes the commonconfig header may respond with a 5 ms delay if the header value is not a valid JSON. This indicates the possibility of further exploitation of this feature.
Server-side injections: Timing analysis has proven effective in detecting various types of injections, such as SQL injections, JSON injections, and server-side parameter contamination. For example, an example of blind SQL injection was presented, where the use of classic payloads allowed us to identify a vulnerability based on changing the response time.
A JSON injection attack was also demonstrated. When a request with an incorrect JSON structure returned a response with a small delay, this allowed the researcher to draw a conclusion about a possible vulnerability in the error handling system on the server.
Detection of incorrect reverse proxy configurations: One of the most significant discoveries in the study was the use of timing analysis to detect SSRF (Server-Side Request Forgery) through incorrectly configured reverse proxies. For example, it was discovered that servers that route requests based on the Host header may be vulnerable to SSRF. The researcher demonstrated how the Host header can be used to bypass restrictions and gain access to the company's internal systems.
A new approach called Scoped SSRF was proposed, where proxy servers only allow redirection to certain subdomains, which makes the vulnerability less obvious and difficult to detect. However, the use of timing analysis allowed us to identify such vulnerabilities by determining whether the server sent DNS requests to the specified domains.
Technical details of the implementation
To achieve such results, the following techniques were applied:
Two-packet synchronization: One of the key innovations was the use of two-packet synchronization to eliminate network noise. In HTTP / 2, you can send two requests in a single TCP packet, ensuring that they arrive at the server at the same time. The response time is compared by the order in which responses are returned, which allows you to determine which request was processed longer.
However, this technique has its own "pitfall" - the so-called "sticky query order" problem. Due to the nature of TLS, one request will still be decrypted first, which may distort the analysis results. To combat this effect, an additional ping frame was used, which allows you to even out the processing time of requests on the server.
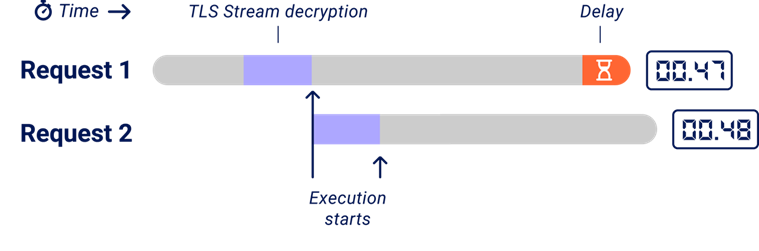
Delay between processing requests
Overcoming server noise: despite eliminating network noise, there is still a problem of server-side noise, which can occur due to load, interaction with other systems, and other factors. To minimize noise, the researcher recommended using the shortest possible code paths and avoiding caching. Moreover, in some cases, DoS attacks (such as CPDoS) can help reduce noise from other users.
Large-scale scanning and automation: Various automation approaches were used to scan 30,000 sites. For example, a list of subdomains was created based on known data and a check for the possibility of bypassing security via alternative routes. The process involved double - checking each host to identify differences in responses.
The study demonstrates that timing attacks can be applied to a wide range of real-world systems, and their potential is still far from exhausted. The researcher plans to further improve the Param Miner and Turbo Intruder tools to make attacks even faster and more effective. New research areas are also being considered, including amplifying delay signals and reducing noise, which may open up new opportunities for exploiting vulnerabilities.
Source
A new study presented at the DEF CON conference reveals best practices for attacks on web servers that use timing dependencies. Attacks allow you to detect hidden vulnerabilities, bypass defenses, and gain access to private server areas without the need for complex settings.
Basic techniques of timing attacks
The study focuses on three key techniques:
Detection of hidden attack surfaces: in the course of the study, a technique was developed that allows you to find hidden parameters, HTTP headers, and other elements that can be used for further attacks. This is achieved by measuring the server's response time to various requests, where small changes in latency can indicate the presence of hidden parameters or even vulnerabilities.
In particular, the author used the Param Miner tool, which performs mass scanning of parameters based on response time. For example, a server that processes the commonconfig header may respond with a 5 ms delay if the header value is not a valid JSON. This indicates the possibility of further exploitation of this feature.
Server-side injections: Timing analysis has proven effective in detecting various types of injections, such as SQL injections, JSON injections, and server-side parameter contamination. For example, an example of blind SQL injection was presented, where the use of classic payloads allowed us to identify a vulnerability based on changing the response time.
A JSON injection attack was also demonstrated. When a request with an incorrect JSON structure returned a response with a small delay, this allowed the researcher to draw a conclusion about a possible vulnerability in the error handling system on the server.
Detection of incorrect reverse proxy configurations: One of the most significant discoveries in the study was the use of timing analysis to detect SSRF (Server-Side Request Forgery) through incorrectly configured reverse proxies. For example, it was discovered that servers that route requests based on the Host header may be vulnerable to SSRF. The researcher demonstrated how the Host header can be used to bypass restrictions and gain access to the company's internal systems.
A new approach called Scoped SSRF was proposed, where proxy servers only allow redirection to certain subdomains, which makes the vulnerability less obvious and difficult to detect. However, the use of timing analysis allowed us to identify such vulnerabilities by determining whether the server sent DNS requests to the specified domains.
Technical details of the implementation
To achieve such results, the following techniques were applied:
Two-packet synchronization: One of the key innovations was the use of two-packet synchronization to eliminate network noise. In HTTP / 2, you can send two requests in a single TCP packet, ensuring that they arrive at the server at the same time. The response time is compared by the order in which responses are returned, which allows you to determine which request was processed longer.
However, this technique has its own "pitfall" - the so-called "sticky query order" problem. Due to the nature of TLS, one request will still be decrypted first, which may distort the analysis results. To combat this effect, an additional ping frame was used, which allows you to even out the processing time of requests on the server.

Delay between processing requests
Overcoming server noise: despite eliminating network noise, there is still a problem of server-side noise, which can occur due to load, interaction with other systems, and other factors. To minimize noise, the researcher recommended using the shortest possible code paths and avoiding caching. Moreover, in some cases, DoS attacks (such as CPDoS) can help reduce noise from other users.
Large-scale scanning and automation: Various automation approaches were used to scan 30,000 sites. For example, a list of subdomains was created based on known data and a check for the possibility of bypassing security via alternative routes. The process involved double - checking each host to identify differences in responses.
The study demonstrates that timing attacks can be applied to a wide range of real-world systems, and their potential is still far from exhausted. The researcher plans to further improve the Param Miner and Turbo Intruder tools to make attacks even faster and more effective. New research areas are also being considered, including amplifying delay signals and reducing noise, which may open up new opportunities for exploiting vulnerabilities.
Source
