Man
Professional
- Messages
- 3,221
- Reaction score
- 1,187
- Points
- 113
Greetings, friends!
Let's imagine a situation: you set a password on your smartphone. It doesn't matter what kind: 6-digit, text, a picture or even hidden clicks on areas of the screen.
Do you think it's impenetrable? Nope. There are plenty of ways to find out, and it's not necessary to look over your shoulder. Attackers can steal your passwords in plain sight, even when cameras are watching.
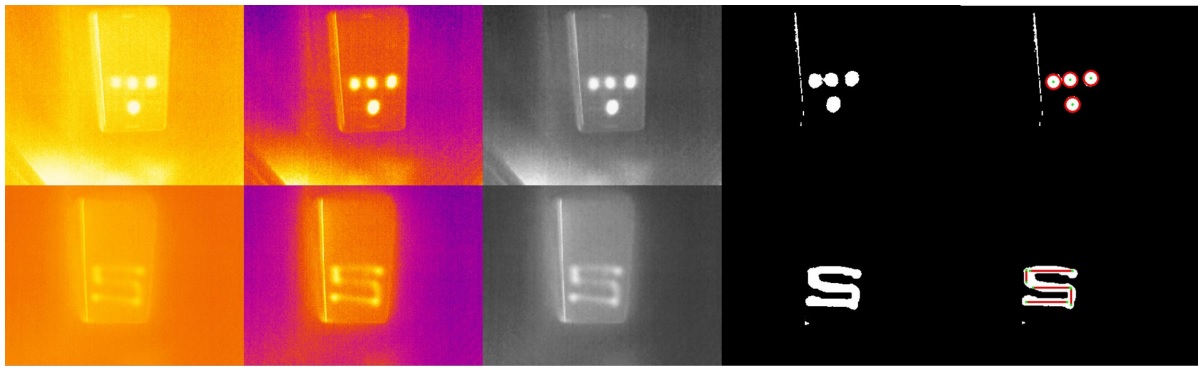
You entered the password, then simply put away your smartphone. Scientists from the University of Stuttgart, together with colleagues from the Ludwig Maximilian University of Munich, have proven that this is not safe.
Armed with a compact thermal imager, the scientists were able to read the entered password from the smartphone screen. 15 seconds after entering, the four-digit PIN code was recognized in 90% of cases. And the graphic key could be guessed almost always, even after 30 seconds.
If you hide a thermal imager in your sleeve or disguise it as a toy, no one will even think that a person passing by a smartphone was scanning the code.
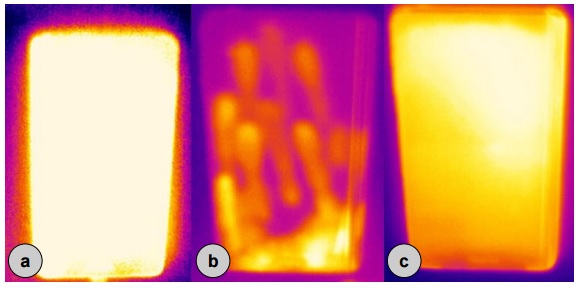
Scientists suggested protecting themselves with random swipes on the screen (b). Among the hardware methods are increasing the display brightness for a few seconds (a) or a sharp increase in the load on the processor (c). In a thermal imager, this looks like this:
Today, even an amateur camera or a good smartphone can do this. It won’t be hard to pretend that you’re not taking a photo of your colleague’s smartphone at lunch, but of your food for Instagram.
This method is best at recognizing traces of graphic key input, a little more difficult – PIN code or alphanumeric password. If it is not a word, phrase or date of birth, there will be too many options for the order of letters and numbers.

The more complex the graphic key, the easier it is to recognize, say researchers. It is enough to sit next to the victim at a distance of up to 5 meters and simply film the unlocking process.
The video is then uploaded to a special app. It analyzes your finger movements and offers up to five possible keys. In 95% of cases, one of these keys is correct.
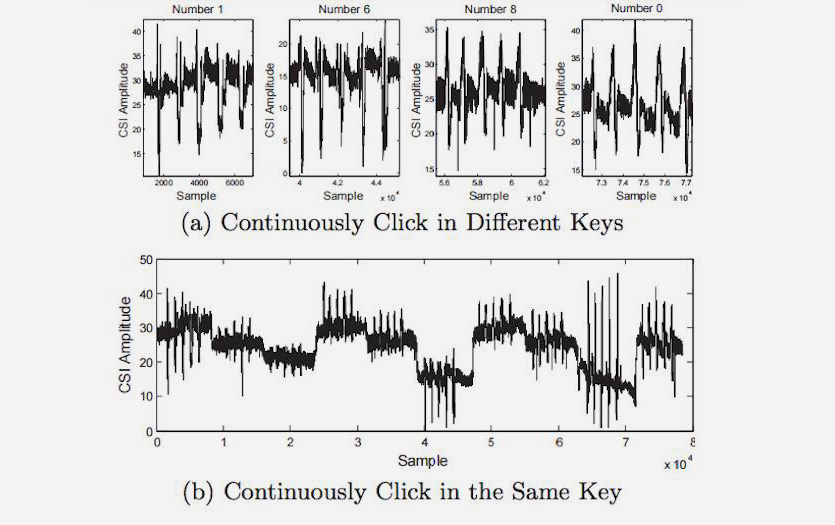
Former SpringSource CTO Adrian Collier has revealed how to intercept a PIN code using Wi-Fi signal analysis. He calls the technology WindTalker.
Collier found that finger movements on the screen affected the Wi-Fi signal. If an attacker created an access point, he would be able to track this micro-interference.
In an experiment, Collier managed to hack into an account on Alipay, Alibaba's payment system. The app gave him three password options, and one of them worked.
The accuracy of the method is 68%. The more data, the more accurate the analysis. The more attempts the application allows, the greater the chance of entering the correct password.
The experiment was conducted by employees of the Stevens Institute of Technology and Binghamton University (USA). They developed a scanner that monitors electromagnetic radiation from sensors in smart watches and trackers. Data from the scanner was transmitted via Bluetooth.
The scanning results were processed in an application that identifies up to 5,000 key movements. To create the algorithm, two dozen users, two models of smart watches and a fitness bracelet with a standard nine-axis accelerometer were involved.
The password was recognized 80% of the time on the first try, and 90% on the second (if the user enters the same combination twice). The more sensors a wearable device has (gyroscopes, magnetometers, accelerometers), the higher the accuracy. The position of the hand does not affect it.
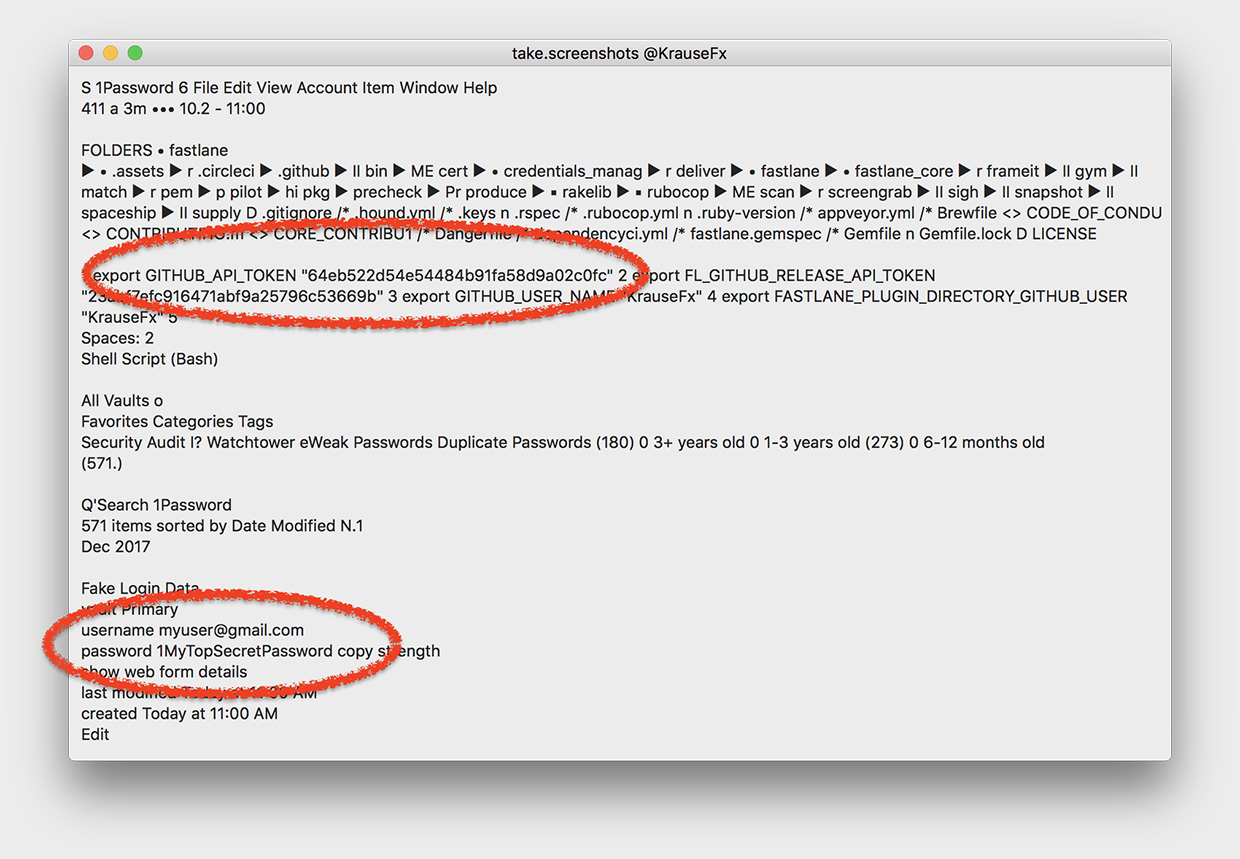
Your computer can technically take a screenshot at any time, including when you enter your password. The possibility was discovered back in November 2017 by Fastlane Tools founder Felix Krause.
The screenshot is made by the CGWindowListCreateImage function. It does not require permission from the user.
A virus that takes screenshots can run in the background. It will still have access to literally every pixel.
The intercepted data allows you to log into other people's accounts, see downloaded files, etc. In addition, the application allows you to forcibly delete the user's cookies, forcing him to re-authorize.
Previously, the tool allowed intercepting even iCloud passwords. But Apple developers have already fixed this.
Other methods of intercepting traffic (including passwords) also exist. Even if these are passwords from HTTPS resources. The main thing is that the victim's device is in the same Wi-Fi network as the hacker's device.
 Thank you for reading the article.
Thank you for reading the article.
Source
Let's imagine a situation: you set a password on your smartphone. It doesn't matter what kind: 6-digit, text, a picture or even hidden clicks on areas of the screen.
Do you think it's impenetrable? Nope. There are plenty of ways to find out, and it's not necessary to look over your shoulder. Attackers can steal your passwords in plain sight, even when cameras are watching.
A simple thermal imager is enough

You entered the password, then simply put away your smartphone. Scientists from the University of Stuttgart, together with colleagues from the Ludwig Maximilian University of Munich, have proven that this is not safe.
Armed with a compact thermal imager, the scientists were able to read the entered password from the smartphone screen. 15 seconds after entering, the four-digit PIN code was recognized in 90% of cases. And the graphic key could be guessed almost always, even after 30 seconds.
If you hide a thermal imager in your sleeve or disguise it as a toy, no one will even think that a person passing by a smartphone was scanning the code.
Scientists suggested protecting themselves with random swipes on the screen (b). Among the hardware methods are increasing the display brightness for a few seconds (a) or a sharp increase in the load on the processor (c). In a thermal imager, this looks like this:

It is possible to calculate the password from oil traces
A high-resolution camera can take a high-quality photo that can identify oily fingerprints on a smartphone screen. Back in 2010, experts at the University of Pennsylvania described this method.Today, even an amateur camera or a good smartphone can do this. It won’t be hard to pretend that you’re not taking a photo of your colleague’s smartphone at lunch, but of your food for Instagram.
This method is best at recognizing traces of graphic key input, a little more difficult – PIN code or alphanumeric password. If it is not a word, phrase or date of birth, there will be too many options for the order of letters and numbers.
In general, the Android pattern key is the most insecure

The more complex the graphic key, the easier it is to recognize, say researchers. It is enough to sit next to the victim at a distance of up to 5 meters and simply film the unlocking process.
The video is then uploaded to a special app. It analyzes your finger movements and offers up to five possible keys. In 95% of cases, one of these keys is correct.
Your password may leak your Wi-Fi network

Former SpringSource CTO Adrian Collier has revealed how to intercept a PIN code using Wi-Fi signal analysis. He calls the technology WindTalker.
Collier found that finger movements on the screen affected the Wi-Fi signal. If an attacker created an access point, he would be able to track this micro-interference.
In an experiment, Collier managed to hack into an account on Alipay, Alibaba's payment system. The app gave him three password options, and one of them worked.
The accuracy of the method is 68%. The more data, the more accurate the analysis. The more attempts the application allows, the greater the chance of entering the correct password.
Fitness tracker or smartwatch movements also “give up” the password
If a hacker installs a special scanner near your workplace, ATM or terminal, he will be able to obtain your password or PIN code by tracking your hand movements on a fitness tracker or smartwatch.The experiment was conducted by employees of the Stevens Institute of Technology and Binghamton University (USA). They developed a scanner that monitors electromagnetic radiation from sensors in smart watches and trackers. Data from the scanner was transmitted via Bluetooth.
The scanning results were processed in an application that identifies up to 5,000 key movements. To create the algorithm, two dozen users, two models of smart watches and a fitness bracelet with a standard nine-axis accelerometer were involved.
The password was recognized 80% of the time on the first try, and 90% on the second (if the user enters the same combination twice). The more sensors a wearable device has (gyroscopes, magnetometers, accelerometers), the higher the accuracy. The position of the hand does not affect it.
Even screenshots will give away your password

Your computer can technically take a screenshot at any time, including when you enter your password. The possibility was discovered back in November 2017 by Fastlane Tools founder Felix Krause.
The screenshot is made by the CGWindowListCreateImage function. It does not require permission from the user.
A virus that takes screenshots can run in the background. It will still have access to literally every pixel.
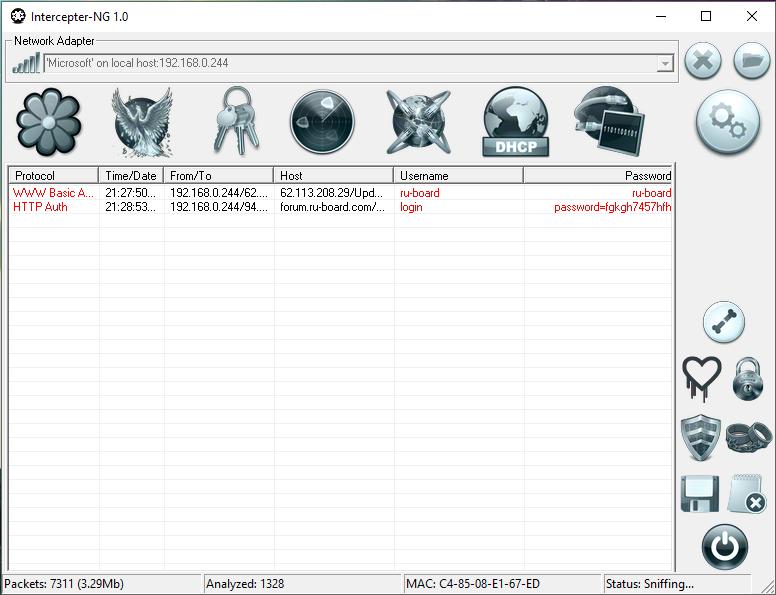
Let's move on to real hacking. MITM attacks
MITM (Man-in-the-middle) – attacks of the “man in the middle” type. Most often, sniffers like Intercepter-NG are used to intercept passwords and cookies using this type of attack.The intercepted data allows you to log into other people's accounts, see downloaded files, etc. In addition, the application allows you to forcibly delete the user's cookies, forcing him to re-authorize.

Previously, the tool allowed intercepting even iCloud passwords. But Apple developers have already fixed this.
Other methods of intercepting traffic (including passwords) also exist. Even if these are passwords from HTTPS resources. The main thing is that the victim's device is in the same Wi-Fi network as the hacker's device.
Source

