Tomcat
Professional
- Messages
- 2,689
- Reaction score
- 979
- Points
- 113
Hi all. Carder is with you.
For example, someone uses a change of IP in order to create a multi-account.
And someone, of course, uses it for shady purposes.
It doesn't matter what you do, you all have the same problems.
Everyone seems to know how to change this IP, but only a few know how to change it correctly; many have huge problems with this. There is a belief that you should only use private VPNs and proxies, which no one knows about. Go to any hacker chat and ask where to buy a proxy, and the answer will be: “We won't tell you, this is a super private service. ” And in fact, when a newbie arrives, he doesn't really understand what to do, but the fact is that even the person who seems to say that he understands what IP address to choose, he himself actually doesn't really understand it . And alas, this is not the problem of this person, this is the problem of the fact that in our time there are no clear criteria for checking the IP address. Therefore, the only option that we can use with you to assess the quality of an IP address is special checkers whose main purpose is to check it. Such checkers specialize in checking IP addresses and anti-fraud systems (anti-fraud systems). But there is a small problem.
These anti-fraud systems in most cases will not want to communicate with just anyone. Well that's a fact. And therefore, basically they either put a very high price tag on their services, or they work only with confirmed legal entities, that is, they will not even want to work with individuals.
But there are still some good services, I'll show you one of them, it's paid, a subscription costs $45. I won't give a link so that you don't consider it an advertisement; anyone who needs it will find it themselves. This service has two linked anti-fraud systems, the IP DATA system and the IP QULITY SCORE system.
You may ask why there are no such free services? There are huge difficulties with the free mode. These difficulties come from Southeast Asia. They consist in the fact that any free service is simply stupidly destroyed by guests from India, Vietnam, Indonesia and so on, everyone who is engaged in shadow activities begins to rush there in droves and such services constantly lie unable to withstand the load. Paid subscriptions weed out 98% of freeloaders.
So, let's move on to practice. What can we see from our IP address?
I'll switch to the service I talked about at the beginning. It will help us determine which proxy and VPN we use.
Let's go to the service. I already have a subscription there:
On it we can check our own or someone else's IP address. But our main task now is to learn how to determine whether we are using a high-quality proxy or VPN service or not.
Almost not a day goes by without you asking me in PM which proxy or VPN service to use. Someone is shouting that it is better to use a proxy from 911, whoever knows the topic. “Everything works fine for me, I load goods from them without any problems.” Another will look at him and say: “You're not a very smart person, I use another service, super duper straight from the USA and everything is fine with carding, hacking and fraud. “Therefore, I would like to immediately explain this matter. For each goal and user, it is necessary that the complexity of the tasks that he wants to cope with is clearly established. We understand perfectly well that if we work with some Russian affiliate and fraud it, then it will allow you to work with some proxies, no questions asked. And if you want to enter some product on Amazon, then Amazon will tell you: “Get out of here with your proxies, I'm not going to work with you, why are you hiding your identity”? The same applies to qiwi wallets, they are banned for the same reason. Therefore, it is necessary for everyone to have a clear understanding in their head that there are different goals and these different goals can be achieved with different resources. In some cases, a regular public proxy downloaded from some free distribution site, which has already been used by schoolchildren more than once, will suit you, but it may work for you. We will consider the most complex options. The options are ideal, because it makes no sense for us to rely on crap, right? Right. So, someone says proxy 911 is better, someone else shouts that another service is better, a third generally rubs in about the next service, a fourth shouts mobile proxies are better. What to do in this situation? How to understand? You are a newbie, you come to a hacker chat and think: “So who should I listen to? How many people - so many opinions. How can I find out the truth?” Let's get to the bottom of it. I found one of the proxy selling services:
I'll take the first one I come across that's on sale, copy the IP address into the checker and start checking it to see if I should buy it:
I paste the address into the checker and now I can read information about it:
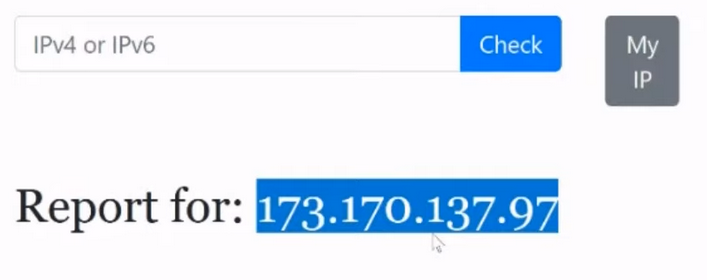
We see his statistics:
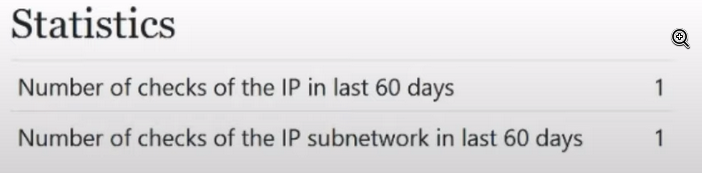
What do these statistics mean? The first line shows us how often this ip has been checked over the last 60 days, and the second line shows how often its subnet has been checked over the last 60 days. Why is this important to us and why do we need to pay attention to the IP address itself and its subnet? Will explain. Firstly, the number is 60 days. Where did this come from? The number of 60 days was taken from publicly available sources and from other anti-fraud systems; this value was chosen as the standard for storing information. Not only storing information about the IP address, but also storing information about browser fingerprints, incidents, and so on.
In the world, for those who do not know, the ipv4 protocol is currently used, which is limited to 4 billion-plus IP addresses; technically there cannot be more of them, in any way. Only when the whole world switches to the ipv6 protocol, then there will be around 4 quadrillion IP addresses, but this will not happen very soon, apparently. Therefore, we understand that we have only 4 billion IP addresses, and there are more than 10 billion users of the same Internet network, by user I mean devices. What to do in this situation? There are NAT networks for this, everyone knows about them. But, most importantly, the IP addresses in the world are in such a big concrete mixer. Imagine how on TV on a Sunday morning they spin a tray, there are such reels and there are a bunch of different balls, and then they pull out a ball and maybe you'll win something someday. The situation is approximately the same with IP addresses. All IP addresses in the world belong to the American company RIPE. It has offshoots, subsidiaries that operate and are set up to operate under certain laws in some parts of the world, but basically everything is owned by one company. And when RIPE wants to issue IP addresses to a legal entity:
In this case, Charter Communications will first give him an autonomous network:
This is a pool of these IP addresses. And here it is not necessary that the IP addresses will be in order. This could be 173.168
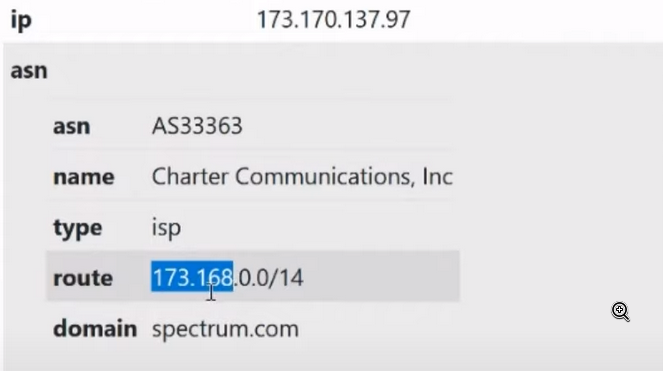
And the next subnet could be 222, 223 and so on. The bottom line is that these subnets are constantly mixed, and the IP address that today belongs to, for example, Voronezh, tomorrow will belong to Pyongyang, for example. Therefore, our check for the last 60 days in this case allows us to find out whether this IP address was interested in over the last 60 days. Accordingly, if we are here:
We see the value 2, which means we can understand that someone has already checked this IP. If we see any value, 10 or more, it means most likely that this IP has become publicly available and fellow schoolchildren are already in full swing using it to earn money for beer. Therefore, the first thing we pay attention to is statistics, if we see a number greater than one, maximum two, if more, then I do not recommend using this IP address, it means someone was already interested in it before you and most likely he saw that this IP address no one was interested in it before and took advantage of it, so be careful.
The next point is the subnet:

Why do we need this? Now pay attention to this IP address:

Imagine that instead of the value 97 we could have the value 96, 95, maybe even 254. What does this mean? This means our subnet. You need to pay attention to the subnet very carefully, now I'll explain why. There are quite a few proxy services on the Internet that, in order to provide services and sell IP addresses for rent, enter into an agreement with Internet providers and the providers simply provide them with an entire subnet. Accordingly, imagine that you want to register an Amazon account for driving in and you will have an IP address with a subnet of 97, and after 30 minutes someone bought a new proxy, and there will already be 98, and after another 30 minutes someone bought it there too will be 101 for example. Thanks to this, the antifraud system analyzes IP addresses not only by the addresses themselves, but also by subnetworks. Thanks to this subnet check, you can understand when the proxy got into some kind of trouble, became infected with a network worm, or actually ended up being sold as a
pro. Therefore, suspicious activity from a subnet is also very important.
So we definitely pay attention to it the next time you see that the IP value is here:

exceeds 2, then I categorically do not recommend using this proxy or VPN.
Let's now move on to anti-fraud systems. We present 2 systems in this case:
IP DATA is a simple system compared to the IPQUALITYSCORE system, but it still has a place, it is really important to us because quite a large number of resources are connected to it, and ideally, of course, this is what large players in the Internet market do. They connect a huge number of anti-fraud systems to collect data from different sources. Imagine sitting like a spider and collecting data from various sources into your webs. There's a fly ran by, and there's a flea jumped. You are already aware of everything that is happening around, and if we have only one web, it will not be very good. Therefore, it is the large number of connected anti-fraud systems that play a truly important role.
I'll move on to decrypt the data. They may seem completely boring and unimportant to some, but I assure you that by the time you read my post you will understand the value of this data.
The first thing that greets us. We are greeted by ip:

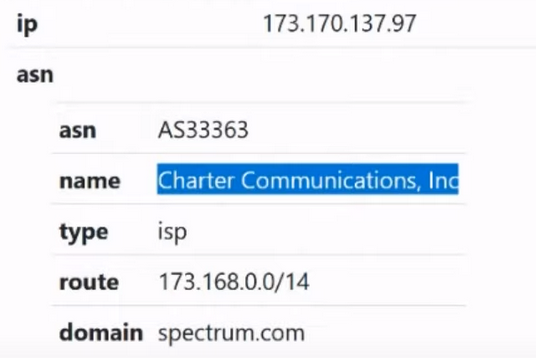
We are familiar with him. Next we have ASN:

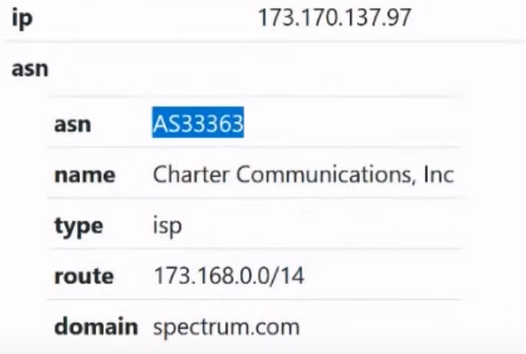
Autonomous network. Previously called BGP (Border Gateway Protocol). This autonomous network has its own number:
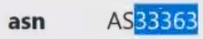
In this case, our number is 33363. This means that when the legal entity of the company (in this case we have the company Charter Communication):
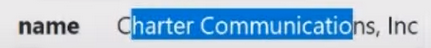
contacted the RIPE company in order to obtain IP addresses and provide Internet services in order to organize a network for a large enterprise, such as a concern. And they were given an autonomous network with the following number: 33363.
Next we have the ISP type:

This stands for Internet Service Provider.
Next we have our subnet:
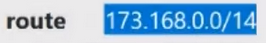
And the domain of the rental company:
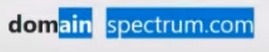
In principle, in this case, it makes no sense to pay attention to anything other than type . There is no particularly important information for us here.
Let's go below:
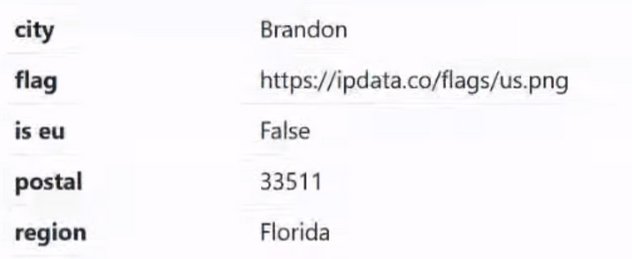
Everything is clear here. The city and flag are indicated if anyone is interested in looking. Next point:

Is eu checks whether the IP address is in the European Union. If we go to the same Google from a US or European IP address, then different amounts of data will be collected from us. This is all due to the difference in personal data policies in the European Union and the United States. Therefore, in principle, theoretically this can help us, but in practice we understand perfectly well that if we buy a proxy or VPN from Switzerland, it is unlikely to end up in the USA.
Next we have the postal code:

The postal code will definitely be useful to us if we are engaged in carding.
Next we have the region:

In this case it is the state.
If above we looked at more regional data, then the next paragraph already carries directly interesting information. These are threats :
In this case, our IP is clean in this regard, everything is fine:
If we see False, it means it is not visible to antifraud systems like TOR, proxy or any other threat. This is good. We can work with this IP. Let's go further:

Here we see information about the currency, we don't really need this information, we already know what currency is used in the USA. But why is this information here? Not always in countries that have territorial affiliation, if we take colonies for example, the currency coincides with the parent country. Let me give you an example: Tahiti, French Polynesia, is under the jurisdiction of France, but the currency there is not the euro. I'll take Mauritius, Mauritius is also under France and there are no euros there either. And there are such moments, they are specific. It is clear that if we choose the USA, then we will have the USD dollar everywhere, but it is still necessary to mention this nuance.
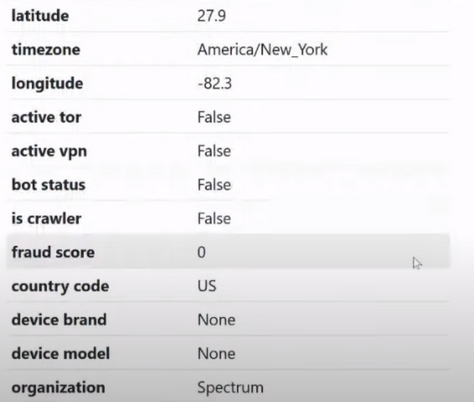
Next we have the items latitude and longitude (width and longitude):
In fact, for the average user the points are useless, but the points are incredibly useful for those who are trying to deceive anti-fraud systems, which are based on triangulation of surrounding Wi-Fi networks. This is quite important. Also, the latitude and longitude parameters can be used to replace geolocation manually, for example, as a default location in Windows.
Further. Time zone (time zone or other regional parameter):
Very important. Extremely important. The parameters are simple, but these simple parameters are used by a very large number of beginners. When a person cards for example in the USA, but he lives in another country, he checks the IP and his IP is -0500:

He still sets himself the same time zone, that is, -5 hours from the prime meridian, but still his time does not match. Why is this happening? Because in the USA, for example, there is a transition to summer and winter time, and therefore checkers can show you information without this transition. And this will really be a problem, that is, it is not clear who to believe. You can go to some checker site where this point is not taken into account and, accordingly, your time will differ by 1 hour, that is, for example, it will not be 11:14:
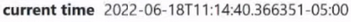
and 12:14. And thanks to this, you may have problems with the fact that this behavior will already be anomalous for anti-fraud systems. Therefore, for all its apparent simplicity, be sure to pay attention to the regional parameters, time, time zone, and whether the state in which you are going to enter, in that city, has a transition to winter and summer time. This is extremely important. On the computer we also set the time indicated in the IP.
Let's go below:

I think these parameters are clear to everyone.
Now let's move on to the IPQUALITYSCORE block. This block gives us much more interesting information and we will now get acquainted with it. Some information is duplicated:
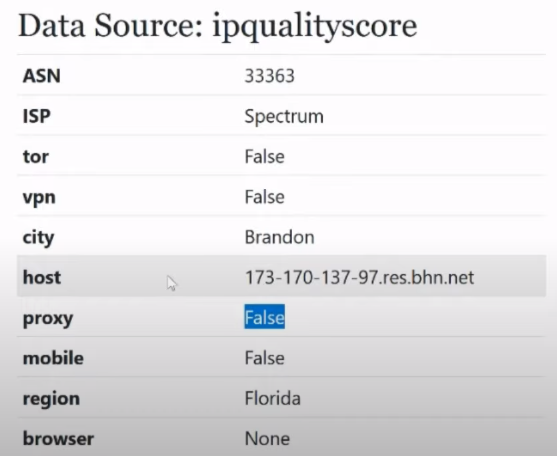
We see the ASN already familiar to us:

We see the already familiar ISP item:

Next we see the definition of TOR , VPN , city, host:

And a very important parameter that works much better in ipqualityscore than in ipdata , and better than in other anti-fraud systems, is the proxy parameter:

The proxy parameter, you will encounter it many times. If you see True here, it means you are 100% using a bad IP address, which is visible as a proxy for ipqualityscore .
Let's go lower. Mobile Item:

Some users who use LTE IP addresses may sometimes see that they have a mobile IP address. This is purely statistical information that is practically not used in anti-fraud systems. Maybe some anti-fraud system will want to use this, but in essence we can always identify a mobile device and in this case it makes no sense for us to check its IP address, because this mobile device can be connected to a router, to a hot spot. That it is True, that it is False, usually we will not extract any interesting information from this.
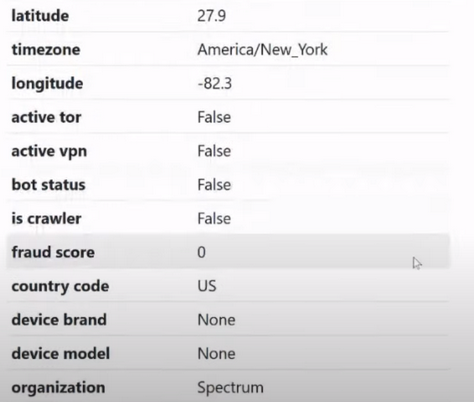
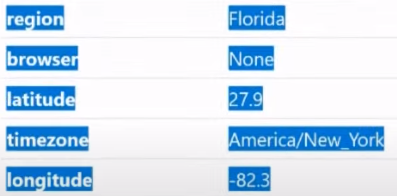
Next we have regional parameters:
Next we see another block regarding active TOR and active VPN :

That is, are they currently active with us?
Next, we check the status of the bot:

Bot status means whether there is any automatic activity from this IP address. For example, automatic requests to a search engine, automatic registrations, and so on and so forth. If the ip has received bot status, then even making a request on Google will be problematic; it will constantly train you with the help of chimneys, pedestrian crossings and traffic lights in the form of a captcha.
The next item is crawler:

It checks whether this IP is used to collect information. In this case, it is False.
And we move on to one of the most important parameters fraud score :

Fraud score literally translates as a fraud rating, how suspicious our IP address is. Oddly enough, quite a large number of checkers focus specifically on the Fraud Score parameter . From 0 to 100.
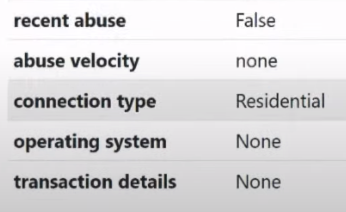
0 is the ideal IP, and 100 is the worst. In principle, this is easy to say, but the fact is that fraud score is not a completely independent parameter, because it also has 2 very good friends. These 2 friends are present in the ipquality score only in expensive tariff plans, for some reason they were not included in the cheap ones. And here they are: Recent abuse and abuse velocity:
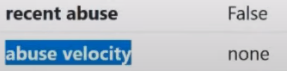
What does this mean? I'll start from the bottom, the abuse velocity item :
Abuse velocity allows us to determine whether complaints have been received at our IP address. Number of complaints. We can have the value none here, meaning there were no complaints at all. But there can be a value of low , middle and high . This means that some scoundrel has taken our IP and is doing bad things with it in different services. If you do something bad in one service, you will receive one complaint; if you do something bad in several services, you will receive more complaints. And if there are not 1 such scoundrels, but 2, 3 or more, this especially applies to the fantastic method of monetizing IP addresses that Asians came up with. Imagine that the monetization of the IP address that they buy for 30-40 cents occurs on the maximum possible scale, that is, everything that can be registered on it is registered, starting from games, ending with dating, porn sites, everything possible, they squeeze it out to the maximum.
So, the abuse velocity item tells us about the number of complaints received for a given IP address, but we also have the recent abuse item :

The recent abuse item allows us to identify approved complaints that occurred within the last 24-48 hours. This means that the abuse velocity point may receive a complaint about illegal activity from this IP address, after which this complaint is considered and if it is approved, then it goes to the recent abuse point , that is, that there are indeed confirmed cases from this IP address cases of fraud and violation of the law. In other cases, the abuse velocity parameter may differ from the recent abuse item.
It happens that abuse velocity will be, for example, high, and recent abuse will be False . This is a sign that illegal activity began from this IP address only in the last 24 hours and the complaints simply have not yet been reviewed and confirmed, so we pay attention to this too.
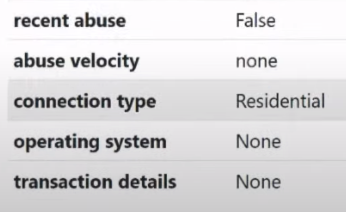
Well, the last point, which is familiar in principle to everyone who works with a proxy, is the connection type :

In this case we have type Residential. This means that this IP address is home. Homemade, clean, good IP address. There are other options that we may have here. We may have the hosting option , we may have the military, government, cedudar option , we may also have government IP addresses, military, IP addresses of educational institutions, cell IP addresses, IP addresses of various different companies. But mainly we will encounter two types. These are the Residential type (home) and the Hosting type (IP address of the hosting provider).
That's all, we checked the IP address, it turned out to be good and you can buy and use it. I hope now you understand how it works.
Different people change IP addresses for completely different purposes. Someone trying to be “anonymous” thinks that VPN is a means of anonymity, not a means of security. He thinks that if he changes his IP address, he will become anonymous.Today we'll talk to you about how to choose and change the IP address correctly. The issue of changing IP addresses is probably the oldest of all the issues that I have encountered and that other people face. You have asked me a question on this topic very often since the creation of our blog.
For example, someone uses a change of IP in order to create a multi-account.
And someone, of course, uses it for shady purposes.
It doesn't matter what you do, you all have the same problems.
Everyone seems to know how to change this IP, but only a few know how to change it correctly; many have huge problems with this. There is a belief that you should only use private VPNs and proxies, which no one knows about. Go to any hacker chat and ask where to buy a proxy, and the answer will be: “We won't tell you, this is a super private service. ” And in fact, when a newbie arrives, he doesn't really understand what to do, but the fact is that even the person who seems to say that he understands what IP address to choose, he himself actually doesn't really understand it . And alas, this is not the problem of this person, this is the problem of the fact that in our time there are no clear criteria for checking the IP address. Therefore, the only option that we can use with you to assess the quality of an IP address is special checkers whose main purpose is to check it. Such checkers specialize in checking IP addresses and anti-fraud systems (anti-fraud systems). But there is a small problem.
These anti-fraud systems in most cases will not want to communicate with just anyone. Well that's a fact. And therefore, basically they either put a very high price tag on their services, or they work only with confirmed legal entities, that is, they will not even want to work with individuals.
But there are still some good services, I'll show you one of them, it's paid, a subscription costs $45. I won't give a link so that you don't consider it an advertisement; anyone who needs it will find it themselves. This service has two linked anti-fraud systems, the IP DATA system and the IP QULITY SCORE system.
You may ask why there are no such free services? There are huge difficulties with the free mode. These difficulties come from Southeast Asia. They consist in the fact that any free service is simply stupidly destroyed by guests from India, Vietnam, Indonesia and so on, everyone who is engaged in shadow activities begins to rush there in droves and such services constantly lie unable to withstand the load. Paid subscriptions weed out 98% of freeloaders.
So, let's move on to practice. What can we see from our IP address?
I'll switch to the service I talked about at the beginning. It will help us determine which proxy and VPN we use.
Let's go to the service. I already have a subscription there:

On it we can check our own or someone else's IP address. But our main task now is to learn how to determine whether we are using a high-quality proxy or VPN service or not.
Almost not a day goes by without you asking me in PM which proxy or VPN service to use. Someone is shouting that it is better to use a proxy from 911, whoever knows the topic. “Everything works fine for me, I load goods from them without any problems.” Another will look at him and say: “You're not a very smart person, I use another service, super duper straight from the USA and everything is fine with carding, hacking and fraud. “Therefore, I would like to immediately explain this matter. For each goal and user, it is necessary that the complexity of the tasks that he wants to cope with is clearly established. We understand perfectly well that if we work with some Russian affiliate and fraud it, then it will allow you to work with some proxies, no questions asked. And if you want to enter some product on Amazon, then Amazon will tell you: “Get out of here with your proxies, I'm not going to work with you, why are you hiding your identity”? The same applies to qiwi wallets, they are banned for the same reason. Therefore, it is necessary for everyone to have a clear understanding in their head that there are different goals and these different goals can be achieved with different resources. In some cases, a regular public proxy downloaded from some free distribution site, which has already been used by schoolchildren more than once, will suit you, but it may work for you. We will consider the most complex options. The options are ideal, because it makes no sense for us to rely on crap, right? Right. So, someone says proxy 911 is better, someone else shouts that another service is better, a third generally rubs in about the next service, a fourth shouts mobile proxies are better. What to do in this situation? How to understand? You are a newbie, you come to a hacker chat and think: “So who should I listen to? How many people - so many opinions. How can I find out the truth?” Let's get to the bottom of it. I found one of the proxy selling services:

I'll take the first one I come across that's on sale, copy the IP address into the checker and start checking it to see if I should buy it:

I paste the address into the checker and now I can read information about it:

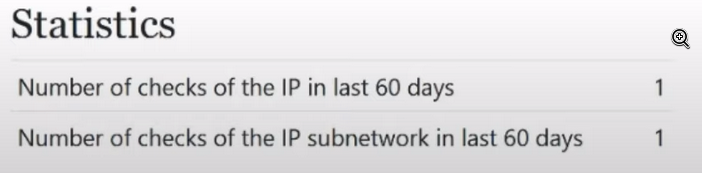
We see his statistics:

What do these statistics mean? The first line shows us how often this ip has been checked over the last 60 days, and the second line shows how often its subnet has been checked over the last 60 days. Why is this important to us and why do we need to pay attention to the IP address itself and its subnet? Will explain. Firstly, the number is 60 days. Where did this come from? The number of 60 days was taken from publicly available sources and from other anti-fraud systems; this value was chosen as the standard for storing information. Not only storing information about the IP address, but also storing information about browser fingerprints, incidents, and so on.
In the world, for those who do not know, the ipv4 protocol is currently used, which is limited to 4 billion-plus IP addresses; technically there cannot be more of them, in any way. Only when the whole world switches to the ipv6 protocol, then there will be around 4 quadrillion IP addresses, but this will not happen very soon, apparently. Therefore, we understand that we have only 4 billion IP addresses, and there are more than 10 billion users of the same Internet network, by user I mean devices. What to do in this situation? There are NAT networks for this, everyone knows about them. But, most importantly, the IP addresses in the world are in such a big concrete mixer. Imagine how on TV on a Sunday morning they spin a tray, there are such reels and there are a bunch of different balls, and then they pull out a ball and maybe you'll win something someday. The situation is approximately the same with IP addresses. All IP addresses in the world belong to the American company RIPE. It has offshoots, subsidiaries that operate and are set up to operate under certain laws in some parts of the world, but basically everything is owned by one company. And when RIPE wants to issue IP addresses to a legal entity:

In this case, Charter Communications will first give him an autonomous network:

This is a pool of these IP addresses. And here it is not necessary that the IP addresses will be in order. This could be 173.168

And the next subnet could be 222, 223 and so on. The bottom line is that these subnets are constantly mixed, and the IP address that today belongs to, for example, Voronezh, tomorrow will belong to Pyongyang, for example. Therefore, our check for the last 60 days in this case allows us to find out whether this IP address was interested in over the last 60 days. Accordingly, if we are here:

We see the value 2, which means we can understand that someone has already checked this IP. If we see any value, 10 or more, it means most likely that this IP has become publicly available and fellow schoolchildren are already in full swing using it to earn money for beer. Therefore, the first thing we pay attention to is statistics, if we see a number greater than one, maximum two, if more, then I do not recommend using this IP address, it means someone was already interested in it before you and most likely he saw that this IP address no one was interested in it before and took advantage of it, so be careful.
The next point is the subnet:

Why do we need this? Now pay attention to this IP address:

Imagine that instead of the value 97 we could have the value 96, 95, maybe even 254. What does this mean? This means our subnet. You need to pay attention to the subnet very carefully, now I'll explain why. There are quite a few proxy services on the Internet that, in order to provide services and sell IP addresses for rent, enter into an agreement with Internet providers and the providers simply provide them with an entire subnet. Accordingly, imagine that you want to register an Amazon account for driving in and you will have an IP address with a subnet of 97, and after 30 minutes someone bought a new proxy, and there will already be 98, and after another 30 minutes someone bought it there too will be 101 for example. Thanks to this, the antifraud system analyzes IP addresses not only by the addresses themselves, but also by subnetworks. Thanks to this subnet check, you can understand when the proxy got into some kind of trouble, became infected with a network worm, or actually ended up being sold as a
pro. Therefore, suspicious activity from a subnet is also very important.
So we definitely pay attention to it the next time you see that the IP value is here:

exceeds 2, then I categorically do not recommend using this proxy or VPN.
Let's now move on to anti-fraud systems. We present 2 systems in this case:
This is the system ip data:


And the ipqualityscore system:



IP DATA is a simple system compared to the IPQUALITYSCORE system, but it still has a place, it is really important to us because quite a large number of resources are connected to it, and ideally, of course, this is what large players in the Internet market do. They connect a huge number of anti-fraud systems to collect data from different sources. Imagine sitting like a spider and collecting data from various sources into your webs. There's a fly ran by, and there's a flea jumped. You are already aware of everything that is happening around, and if we have only one web, it will not be very good. Therefore, it is the large number of connected anti-fraud systems that play a truly important role.
I'll move on to decrypt the data. They may seem completely boring and unimportant to some, but I assure you that by the time you read my post you will understand the value of this data.
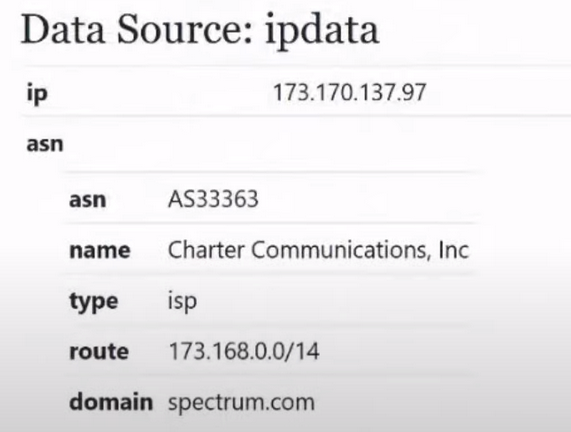
The first thing that greets us. We are greeted by ip:

We are familiar with him. Next we have ASN:

Autonomous network. Previously called BGP (Border Gateway Protocol). This autonomous network has its own number:

In this case, our number is 33363. This means that when the legal entity of the company (in this case we have the company Charter Communication):

contacted the RIPE company in order to obtain IP addresses and provide Internet services in order to organize a network for a large enterprise, such as a concern. And they were given an autonomous network with the following number: 33363.
Next we have the ISP type:

This stands for Internet Service Provider.
Next we have our subnet:

And the domain of the rental company:

In principle, in this case, it makes no sense to pay attention to anything other than type . There is no particularly important information for us here.
Let's go below:

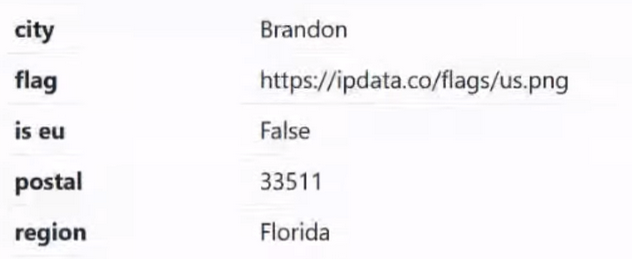
Everything is clear here. The city and flag are indicated if anyone is interested in looking. Next point:

Is eu checks whether the IP address is in the European Union. If we go to the same Google from a US or European IP address, then different amounts of data will be collected from us. This is all due to the difference in personal data policies in the European Union and the United States. Therefore, in principle, theoretically this can help us, but in practice we understand perfectly well that if we buy a proxy or VPN from Switzerland, it is unlikely to end up in the USA.
Next we have the postal code:

The postal code will definitely be useful to us if we are engaged in carding.
Next we have the region:

In this case it is the state.
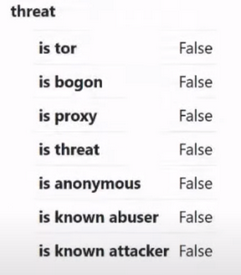
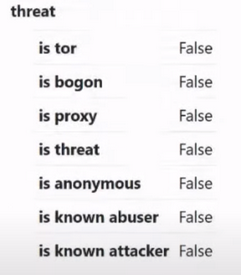
If above we looked at more regional data, then the next paragraph already carries directly interesting information. These are threats :

- is tor (tor detection)
- is bogon (visual ip detection)
- is proxy (detects whether the IP is a proxy)
- is threat (ip threat detection)
- is anonymous (anonymous ip detection)
- is known abuse (detects the IP causing problems, the IP address from which previously illegal activities were carried out)
- is known attacker (detects the IP from which network attacks have previously been carried out)
In this case, our IP is clean in this regard, everything is fine:

If we see False, it means it is not visible to antifraud systems like TOR, proxy or any other threat. This is good. We can work with this IP. Let's go further:

Here we see information about the currency, we don't really need this information, we already know what currency is used in the USA. But why is this information here? Not always in countries that have territorial affiliation, if we take colonies for example, the currency coincides with the parent country. Let me give you an example: Tahiti, French Polynesia, is under the jurisdiction of France, but the currency there is not the euro. I'll take Mauritius, Mauritius is also under France and there are no euros there either. And there are such moments, they are specific. It is clear that if we choose the USA, then we will have the USD dollar everywhere, but it is still necessary to mention this nuance.
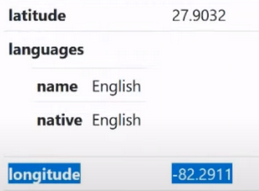
Next we have the items latitude and longitude (width and longitude):

In fact, for the average user the points are useless, but the points are incredibly useful for those who are trying to deceive anti-fraud systems, which are based on triangulation of surrounding Wi-Fi networks. This is quite important. Also, the latitude and longitude parameters can be used to replace geolocation manually, for example, as a default location in Windows.
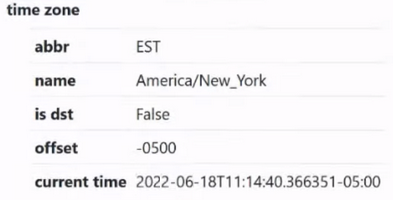
Further. Time zone (time zone or other regional parameter):

Very important. Extremely important. The parameters are simple, but these simple parameters are used by a very large number of beginners. When a person cards for example in the USA, but he lives in another country, he checks the IP and his IP is -0500:

He still sets himself the same time zone, that is, -5 hours from the prime meridian, but still his time does not match. Why is this happening? Because in the USA, for example, there is a transition to summer and winter time, and therefore checkers can show you information without this transition. And this will really be a problem, that is, it is not clear who to believe. You can go to some checker site where this point is not taken into account and, accordingly, your time will differ by 1 hour, that is, for example, it will not be 11:14:
and 12:14. And thanks to this, you may have problems with the fact that this behavior will already be anomalous for anti-fraud systems. Therefore, for all its apparent simplicity, be sure to pay attention to the regional parameters, time, time zone, and whether the state in which you are going to enter, in that city, has a transition to winter and summer time. This is extremely important. On the computer we also set the time indicated in the IP.
Let's go below:

I think these parameters are clear to everyone.
- Region code
- Calling code (phone code)
- County name
- Emoji unicode (unicode)
We finished with the very first IP DATA block and figured out what we should pay attention to when analyzing information. It is worth paying attention to the type of IP address, the threats that this checker has identified (thread), and you should also pay attention to the time zone. It is necessary. This is a must that you must do when working with absolutely any anti-fraud system.
Now let's move on to the IPQUALITYSCORE block. This block gives us much more interesting information and we will now get acquainted with it. Some information is duplicated:



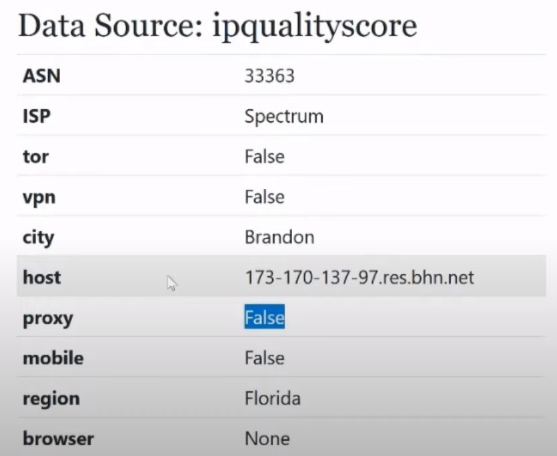
We see the ASN already familiar to us:

We see the already familiar ISP item:

Next we see the definition of TOR , VPN , city, host:

And a very important parameter that works much better in ipqualityscore than in ipdata , and better than in other anti-fraud systems, is the proxy parameter:

The proxy parameter, you will encounter it many times. If you see True here, it means you are 100% using a bad IP address, which is visible as a proxy for ipqualityscore .
Let's go lower. Mobile Item:

Some users who use LTE IP addresses may sometimes see that they have a mobile IP address. This is purely statistical information that is practically not used in anti-fraud systems. Maybe some anti-fraud system will want to use this, but in essence we can always identify a mobile device and in this case it makes no sense for us to check its IP address, because this mobile device can be connected to a router, to a hot spot. That it is True, that it is False, usually we will not extract any interesting information from this.
Next we have regional parameters:

Next we see another block regarding active TOR and active VPN :

That is, are they currently active with us?
Next, we check the status of the bot:

Bot status means whether there is any automatic activity from this IP address. For example, automatic requests to a search engine, automatic registrations, and so on and so forth. If the ip has received bot status, then even making a request on Google will be problematic; it will constantly train you with the help of chimneys, pedestrian crossings and traffic lights in the form of a captcha.
The next item is crawler:

It checks whether this IP is used to collect information. In this case, it is False.
And we move on to one of the most important parameters fraud score :

Fraud score literally translates as a fraud rating, how suspicious our IP address is. Oddly enough, quite a large number of checkers focus specifically on the Fraud Score parameter . From 0 to 100.
0 is the ideal IP, and 100 is the worst. In principle, this is easy to say, but the fact is that fraud score is not a completely independent parameter, because it also has 2 very good friends. These 2 friends are present in the ipquality score only in expensive tariff plans, for some reason they were not included in the cheap ones. And here they are: Recent abuse and abuse velocity:

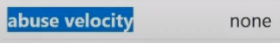
What does this mean? I'll start from the bottom, the abuse velocity item :

Abuse velocity allows us to determine whether complaints have been received at our IP address. Number of complaints. We can have the value none here, meaning there were no complaints at all. But there can be a value of low , middle and high . This means that some scoundrel has taken our IP and is doing bad things with it in different services. If you do something bad in one service, you will receive one complaint; if you do something bad in several services, you will receive more complaints. And if there are not 1 such scoundrels, but 2, 3 or more, this especially applies to the fantastic method of monetizing IP addresses that Asians came up with. Imagine that the monetization of the IP address that they buy for 30-40 cents occurs on the maximum possible scale, that is, everything that can be registered on it is registered, starting from games, ending with dating, porn sites, everything possible, they squeeze it out to the maximum.
So, the abuse velocity item tells us about the number of complaints received for a given IP address, but we also have the recent abuse item :

The recent abuse item allows us to identify approved complaints that occurred within the last 24-48 hours. This means that the abuse velocity point may receive a complaint about illegal activity from this IP address, after which this complaint is considered and if it is approved, then it goes to the recent abuse point , that is, that there are indeed confirmed cases from this IP address cases of fraud and violation of the law. In other cases, the abuse velocity parameter may differ from the recent abuse item.
- Recent abuse is confirmed incidents over the last 24-48 hours
- Abuse velocity is simply the number of complaints.
It happens that abuse velocity will be, for example, high, and recent abuse will be False . This is a sign that illegal activity began from this IP address only in the last 24 hours and the complaints simply have not yet been reviewed and confirmed, so we pay attention to this too.
Well, the last point, which is familiar in principle to everyone who works with a proxy, is the connection type :

In this case we have type Residential. This means that this IP address is home. Homemade, clean, good IP address. There are other options that we may have here. We may have the hosting option , we may have the military, government, cedudar option , we may also have government IP addresses, military, IP addresses of educational institutions, cell IP addresses, IP addresses of various different companies. But mainly we will encounter two types. These are the Residential type (home) and the Hosting type (IP address of the hosting provider).
That's all, we checked the IP address, it turned out to be good and you can buy and use it. I hope now you understand how it works.
