Tomcat
Professional
- Messages
- 2,688
- Reaction score
- 1,015
- Points
- 113
So, fasten your seat belts and get ready for a rollercoaster ride through OTP, Burp Suite, and the intriguing world of cybersecurity. Let's make learning online safety as easy as chatting with friends - after all, we're in this digital adventure together!
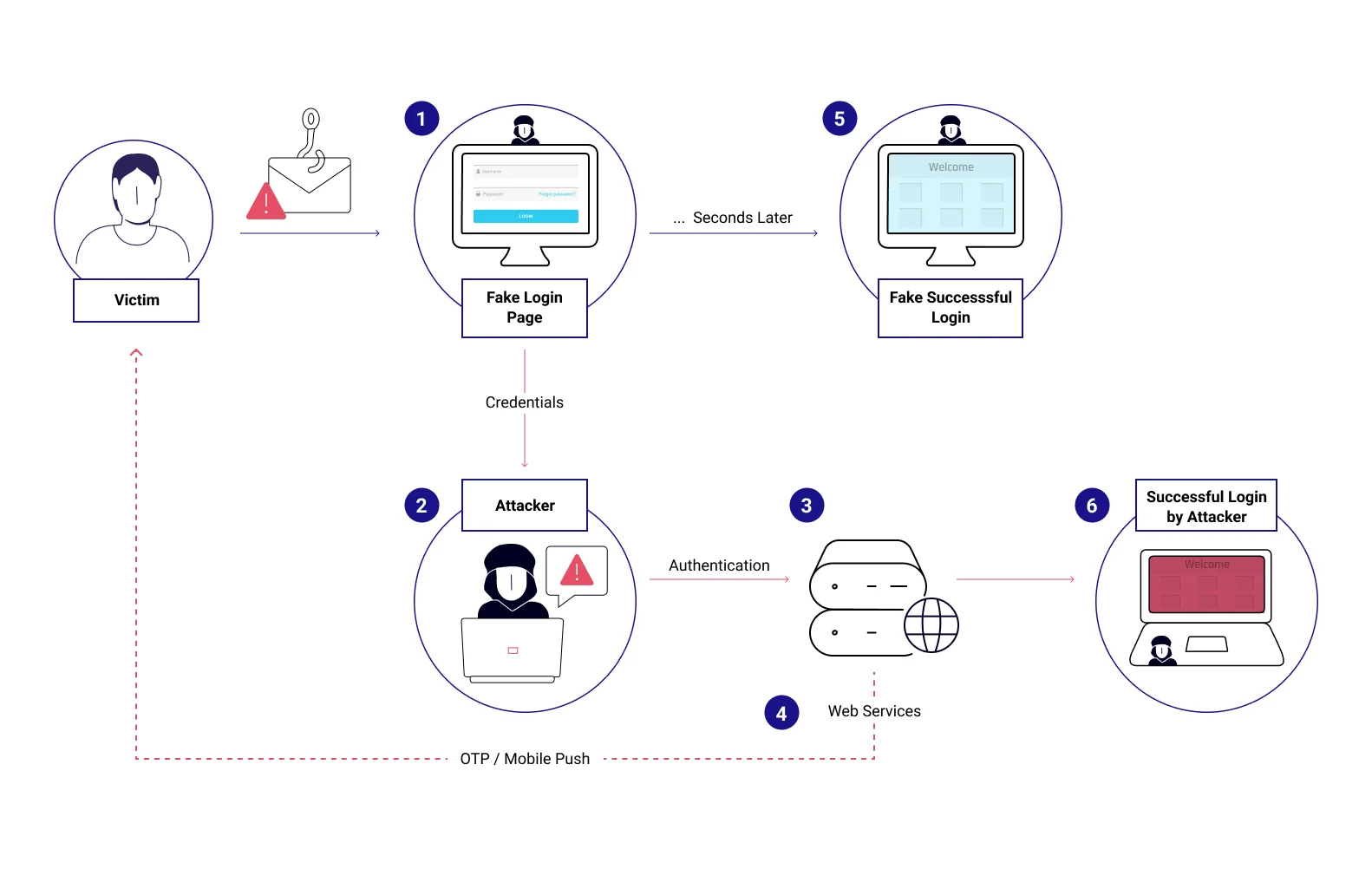
Our comprehensive guide will teach you the ins and outs of one-time password (OTP) authentication. Understand how OTPs work, what their role is in improving online security, and what the different OTP delivery methods are. Delve into the mechanics of popular OTP algorithms such as TOTP and HOTP and gain valuable insights into their applications. Arm yourself with knowledge to prevent OTP bypass attacks, protect sensitive information, and strengthen your digital defense. Explore the world of OTP authentication and equip yourself with essential cybersecurity knowledge
Imagine that you are baking cookies and you want each cookie to be different from the other. OTPs work in much the same way. When you need an OTP, a special algorithm in the application or system prepares a unique code just for you. This code is based on the current time, your device data, and some secret ingredients known only to the app. Result? Fresh, one of a kind OTP, ready to use.
But here's the interesting part: OTP has a very short shelf life. They're like cookies straight out of the oven - best when they're hot! Therefore, they are only valid for a short time, usually only a minute or two. They then expire, rendering them useless to anyone trying to break into your accounts later.
When you enter the OTP at login, the system checks it against the one that was created for you. If they match, you are logged in! It's like presenting a movie ticket - if it's real and matches the system data, then you can enjoy the show.
So OTPs are like temporary access codes that are generated whenever they are needed. They add an extra layer of security to your accounts, ensuring that only you, and not the internet's cookie monsters, can log in. Nice, right? This is the OTP for you!
1. SMS (text messages): Imagine: you log into your account, and suddenly - ding! - a text message arrives with your OTP. SMS is the good old method of OTP delivery. The service provider sends the code directly to your phone via text message. It's fast, easy and doesn't require an Internet connection. Just a good old phone signal and you can log in with peace of mind.
2. Email: Ah, a secure inbox—not just for messages from Aunt Martha. Sometimes your OTP ends up there! When you request an OTP, the system sends it to your email. It looks like a digital letter with a secret code inside. You open the email, find the OTP and use it to unlock your account. Easy and simple, right?
3. Authenticator apps: Now this is where things get a little more complicated. Authenticator apps are like your personal OTP vaults. Apps like Google Authenticator or Authy generate OTP for you even without an internet connection. How? When you create an account, you scan a QR code. The app uses this code to create unique OTPs that sync perfectly with the website or service you are visiting. No need to wait for text messages or emails - your OTPs are right in the app and ready to send at a moment's notice.
Each method has its own advantages, but they all serve the same purpose - to obtain a secret code to keep your accounts safe and sound. Whether it's a quick SMS, a digital note in your email, or a high-tech authenticator app, OTPs are always just a tap away, keeping your online adventures safe!
Setting up Burp Suite to intercept OTP requests
Today we'll roll up our sleeves and look at the practical side of setting up Burp Suite to intercept OTP requests - all in the name of ethical hacking and a better understanding of security.
Step 1: Setting up Burp Suite: First of all, download and install Burp Suite on your system. After installation, launch the application. Burp Suite has both free and paid versions, so choose the one that suits your needs.
Step 2: Set up your browser: Burp Suite works as a proxy between your browser and the Internet. To enable this feature, configure your browser to use Burp Suite as a proxy. Set the proxy address to "127.0.0.1" and the port specified in the Burp Suite configuration (usually 8080). This step allows Burp Suite to intercept requests and responses.
Step 3: Install Burp Suite CA Certificate: Burp Suite uses its own Certificate Authority (CA) certificate to intercept HTTPS traffic. To do this, you need to install the Burp CA certificate in your browser. This certificate can be found in Burp Suite under "Proxy" > "Options" > "Import/export CA certificate". Follow the instructions provided to install the certificate into your browser's certificate store.
Step 4: Configuring proxy listeners in Burp Suite: In Burp Suite, go to the "Proxy" tab and then click on the "Options" tab. Here you can configure proxy listeners. Make sure the proxy listener is set to the same port you configured in the browser (usually 8080). You can also bind Burp Suite to specific network interfaces if you want to intercept traffic from specific devices.
Step 5: Intercept OTP Requests: After installing Burp Suite and setting up your browser, you can intercept OTP requests. Go to the website or app where you want to check OTP security. Burp Suite will intercept the requests and display them in the Proxy > Interception tab. You can intercept specific requests, modify them, and then forward them to see how the system responds.
Important note: Before testing any application or site, even for educational or ethical purposes, be sure to obtain permission from the site owner or system administrator. Unauthorized testing may be illegal and unethical.
By completing these steps, you will be able to learn OTP interception in a controlled, ethical environment. Remember that ethical hacking is about exploring and protecting systems, not exploiting them.
Analysis and modification of OTP requests in real time
Let's sharpen our ethical hacking skills and learn the nuances of intercepting and manipulating data packets for a deeper understanding of Internet security.
Step 1: Intercept OTP Requests: Open Burp Suite and configure it as we discussed earlier. Once configured, go to the website or app where you want to check the OTP security. Burp Suite will intercept requests as they pass between your browser and the server. Go to the Proxy tab > Interception and enable interception. You will see incoming OTP requests waiting for your review.
Step 2: Understand the request structure: Carefully examine the intercepted OTP request. Define the parameters containing the OTP - usually a string of characters or numbers. Understand the structure of the request, such as where the OTP is located, and become familiar with the format in which it is sent to the server.
Step 3: Modifying the OTP Request: Now comes the fun part - modifying the OTP request. Click on the intercepted request and select "Edit". Here you can change the OTP value and see how the server reacts. Experiment with different values, lengths, or characters to understand how the system handles OTP input variations.
Step 4: Observe the server's response: After modifying the OTP, send a request to the server and observe the response. Does the server accept modified OTP? Does he reject it? Understanding how the server responds to various OTP inputs provides valuable insight into the system's security mechanisms.
Step 5: Study the responses: Carefully analyze the server responses. Does it give special error messages when OTP is entered incorrectly? Does it block the account after several failed attempts? By reviewing these answers, you will gain valuable information about security measures and potential system vulnerabilities.
Step 6: Document your findings: Write down your observations and conclusions. Record the system's response to various OTP modifications. This documentation is essential for reporting ethical hacking and understanding the strengths and weaknesses of the system.
Important Reminder: Always comply with ethical and legal standards when conducting testing. Before testing any application, make sure you have express permission from the site owner or administrator. Unauthorized testing is not only unethical, but also illegal.
By following these steps, you can hone your skills in analyzing and modifying OTP requests in real time. Remember, ethical hacking is all about learning, understanding, and strengthening digital security.
Step 1: Define the target: First of all, identify the site or application with a vulnerable OTP implementation that you want to test. Make sure you have explicit permission from the site owner or administrator to conduct testing.
Step 2: Intercept OTP Requests: Launch Burp Suite and set it up as your trusted companion. Intercept OTP requests as they pass between your browser and the server. Burp Suite will intercept these requests, allowing you to analyze them for vulnerabilities.
Step 3: Analyze the OTP generation and verification process: Carefully study the OTP generation and verification process. Understand how OTRs are generated, what algorithms are used, and how the server validates them. Look for patterns, inconsistencies, or weak algorithms that may be exploited.
Step 4: Creating Custom OTP Requests: Now comes the fun part - creating custom OTP requests. Use Burp Suite tools to modify queries, testing the system's response to different OTP inputs. Try options such as incorrect OTP length, special characters or repeated patterns. The goal is to determine how the system responds to these requests and whether it exhibits unexpected behavior.
Step 5: Experiment with Time and Frequency: Explore vulnerabilities related to time and frequency. Check if the system blocks the user after several incorrect OTP attempts. Experiment with the time frame for which OTPs are valid. Sometimes vulnerabilities arise from the way the system handles timing and frequency parameters, so pay close attention to these aspects.
Step 6: Analyze Server Responses: Carefully examine the server responses. Does the server issue special error messages when OTP attempts fail? Does it lock user accounts temporarily or permanently? Understanding these answers will help identify potential weaknesses and areas for improvement.
Step 7: Document and Report: Document your findings in detail. Include what vulnerabilities were discovered, how they could be exploited, and possible solutions to fix them. Prepare a full report for the site owner or administrator describing vulnerabilities and suggestions for strengthening security.
Important note: Always conduct these tests ethically and responsibly. Unauthorized testing is against the law and can have serious consequences. Get clear permission and make sure your actions are legal and ethical.
By following these steps, you can effectively test vulnerable OTP systems, helping organizations improve their security posture. Remember that ethical hacking is a powerful tool for strengthening digital security and ensuring a safe online environment for everyone.
Using the powerful capabilities of Burp Suite, we gain insight into potential vulnerabilities. Armed with this knowledge, we can work to harden systems to ensure they are resilient to OTP bypass attempts.
So, get ready to unlock the secrets of OTP bypass using Burp Suite. This is not just a tool, it is our digital Sherlock Holmes, leading us through the intricacies of cybersecurity.
Result: Trusting the urgency of the letter and its obvious source, Sarah enters the OTP without hesitation. It is unknown that this email was an elaborate phishing attempt. The attackers, posing as employees of the IT department, gain access to Sarah's account, which allows them to gain unauthorized access to the company's internal systems.
Consequences:
Consequences:
Preventive action:
Result: The vulnerability allows an attacker to reuse old OTPs for unauthorized transactions. By manipulating the system, the hacker successfully reuses an outdated OTP to authenticate a large financial transaction.
Consequences:
Preventive action:
Result: After gaining control of the victim's phone number, the hacker intercepts OTPs (one-time passwords) sent through text messages. Using these one-time passwords, the attacker gains unauthorized access to the victim's online accounts, compromising personal and financial information.
Consequences:
Preventive action:
Result: Unsuspecting users, anxious at the thought of losing access to their messaging platform, enter the provided OTP without questioning its authenticity. The moment they send the OTP, the attackers take control of their WhatsApp accounts.
Consequences:
Preventive action:
These case studies and real-life examples demonstrate the importance of strong OTP security measures and the need for vigilance among users. Cyber threats are real and constantly evolving, so it is critical for both individuals and organizations to stay informed and implement online security best practices.
By learning from these examples, we can better protect ourselves and our digital assets, ultimately helping to create a safer online environment. Stay informed, stay alert, and together we can combat OTP security challenges.
Concept of OTP authentication

Our comprehensive guide will teach you the ins and outs of one-time password (OTP) authentication. Understand how OTPs work, what their role is in improving online security, and what the different OTP delivery methods are. Delve into the mechanics of popular OTP algorithms such as TOTP and HOTP and gain valuable insights into their applications. Arm yourself with knowledge to prevent OTP bypass attacks, protect sensitive information, and strengthen your digital defense. Explore the world of OTP authentication and equip yourself with essential cybersecurity knowledge
How are OTPs generated and verified?
So, let's understand what OTPs are - how they are created and verified to ensure the security of your accounts.Imagine that you are baking cookies and you want each cookie to be different from the other. OTPs work in much the same way. When you need an OTP, a special algorithm in the application or system prepares a unique code just for you. This code is based on the current time, your device data, and some secret ingredients known only to the app. Result? Fresh, one of a kind OTP, ready to use.
But here's the interesting part: OTP has a very short shelf life. They're like cookies straight out of the oven - best when they're hot! Therefore, they are only valid for a short time, usually only a minute or two. They then expire, rendering them useless to anyone trying to break into your accounts later.
When you enter the OTP at login, the system checks it against the one that was created for you. If they match, you are logged in! It's like presenting a movie ticket - if it's real and matches the system data, then you can enjoy the show.
So OTPs are like temporary access codes that are generated whenever they are needed. They add an extra layer of security to your accounts, ensuring that only you, and not the internet's cookie monsters, can log in. Nice, right? This is the OTP for you!
Various OTP delivery methods: SMS, email, authenticator apps
Have you ever wondered how secret codes, called OTPs, get into your devices? There are several shipping methods available, and they are easier than you think.1. SMS (text messages): Imagine: you log into your account, and suddenly - ding! - a text message arrives with your OTP. SMS is the good old method of OTP delivery. The service provider sends the code directly to your phone via text message. It's fast, easy and doesn't require an Internet connection. Just a good old phone signal and you can log in with peace of mind.
2. Email: Ah, a secure inbox—not just for messages from Aunt Martha. Sometimes your OTP ends up there! When you request an OTP, the system sends it to your email. It looks like a digital letter with a secret code inside. You open the email, find the OTP and use it to unlock your account. Easy and simple, right?
3. Authenticator apps: Now this is where things get a little more complicated. Authenticator apps are like your personal OTP vaults. Apps like Google Authenticator or Authy generate OTP for you even without an internet connection. How? When you create an account, you scan a QR code. The app uses this code to create unique OTPs that sync perfectly with the website or service you are visiting. No need to wait for text messages or emails - your OTPs are right in the app and ready to send at a moment's notice.
Each method has its own advantages, but they all serve the same purpose - to obtain a secret code to keep your accounts safe and sound. Whether it's a quick SMS, a digital note in your email, or a high-tech authenticator app, OTPs are always just a tap away, keeping your online adventures safe!
Using Burp Suite to Bypass OTP
Ready to dive into the world of OTP bypass with the most advanced tool in our arsenal - Burp Suite? Fasten your seatbelts because we're going on an exciting digital journey!Setting up Burp Suite to intercept OTP requests
Today we'll roll up our sleeves and look at the practical side of setting up Burp Suite to intercept OTP requests - all in the name of ethical hacking and a better understanding of security.
Step 1: Setting up Burp Suite: First of all, download and install Burp Suite on your system. After installation, launch the application. Burp Suite has both free and paid versions, so choose the one that suits your needs.
Step 2: Set up your browser: Burp Suite works as a proxy between your browser and the Internet. To enable this feature, configure your browser to use Burp Suite as a proxy. Set the proxy address to "127.0.0.1" and the port specified in the Burp Suite configuration (usually 8080). This step allows Burp Suite to intercept requests and responses.
Step 3: Install Burp Suite CA Certificate: Burp Suite uses its own Certificate Authority (CA) certificate to intercept HTTPS traffic. To do this, you need to install the Burp CA certificate in your browser. This certificate can be found in Burp Suite under "Proxy" > "Options" > "Import/export CA certificate". Follow the instructions provided to install the certificate into your browser's certificate store.
Step 4: Configuring proxy listeners in Burp Suite: In Burp Suite, go to the "Proxy" tab and then click on the "Options" tab. Here you can configure proxy listeners. Make sure the proxy listener is set to the same port you configured in the browser (usually 8080). You can also bind Burp Suite to specific network interfaces if you want to intercept traffic from specific devices.
Step 5: Intercept OTP Requests: After installing Burp Suite and setting up your browser, you can intercept OTP requests. Go to the website or app where you want to check OTP security. Burp Suite will intercept the requests and display them in the Proxy > Interception tab. You can intercept specific requests, modify them, and then forward them to see how the system responds.
Important note: Before testing any application or site, even for educational or ethical purposes, be sure to obtain permission from the site owner or system administrator. Unauthorized testing may be illegal and unethical.
By completing these steps, you will be able to learn OTP interception in a controlled, ethical environment. Remember that ethical hacking is about exploring and protecting systems, not exploiting them.
Analysis and modification of OTP requests in real time
Let's sharpen our ethical hacking skills and learn the nuances of intercepting and manipulating data packets for a deeper understanding of Internet security.
Step 1: Intercept OTP Requests: Open Burp Suite and configure it as we discussed earlier. Once configured, go to the website or app where you want to check the OTP security. Burp Suite will intercept requests as they pass between your browser and the server. Go to the Proxy tab > Interception and enable interception. You will see incoming OTP requests waiting for your review.
Step 2: Understand the request structure: Carefully examine the intercepted OTP request. Define the parameters containing the OTP - usually a string of characters or numbers. Understand the structure of the request, such as where the OTP is located, and become familiar with the format in which it is sent to the server.
Step 3: Modifying the OTP Request: Now comes the fun part - modifying the OTP request. Click on the intercepted request and select "Edit". Here you can change the OTP value and see how the server reacts. Experiment with different values, lengths, or characters to understand how the system handles OTP input variations.
Step 4: Observe the server's response: After modifying the OTP, send a request to the server and observe the response. Does the server accept modified OTP? Does he reject it? Understanding how the server responds to various OTP inputs provides valuable insight into the system's security mechanisms.
Step 5: Study the responses: Carefully analyze the server responses. Does it give special error messages when OTP is entered incorrectly? Does it block the account after several failed attempts? By reviewing these answers, you will gain valuable information about security measures and potential system vulnerabilities.
Step 6: Document your findings: Write down your observations and conclusions. Record the system's response to various OTP modifications. This documentation is essential for reporting ethical hacking and understanding the strengths and weaknesses of the system.
Important Reminder: Always comply with ethical and legal standards when conducting testing. Before testing any application, make sure you have express permission from the site owner or administrator. Unauthorized testing is not only unethical, but also illegal.
By following these steps, you can hone your skills in analyzing and modifying OTP requests in real time. Remember, ethical hacking is all about learning, understanding, and strengthening digital security.
Testing Vulnerable OTP Implementations with Burp Suite
Greetings, cybersecurity enthusiasts! Today we dive into the exciting world of ethical hacking and learn how to test vulnerable OTP (One-Time Password) implementations using Burp Suite. This will allow us to identify weaknesses and effectively strengthen Internet security measures.Step 1: Define the target: First of all, identify the site or application with a vulnerable OTP implementation that you want to test. Make sure you have explicit permission from the site owner or administrator to conduct testing.
Step 2: Intercept OTP Requests: Launch Burp Suite and set it up as your trusted companion. Intercept OTP requests as they pass between your browser and the server. Burp Suite will intercept these requests, allowing you to analyze them for vulnerabilities.
Step 3: Analyze the OTP generation and verification process: Carefully study the OTP generation and verification process. Understand how OTRs are generated, what algorithms are used, and how the server validates them. Look for patterns, inconsistencies, or weak algorithms that may be exploited.
Step 4: Creating Custom OTP Requests: Now comes the fun part - creating custom OTP requests. Use Burp Suite tools to modify queries, testing the system's response to different OTP inputs. Try options such as incorrect OTP length, special characters or repeated patterns. The goal is to determine how the system responds to these requests and whether it exhibits unexpected behavior.
Step 5: Experiment with Time and Frequency: Explore vulnerabilities related to time and frequency. Check if the system blocks the user after several incorrect OTP attempts. Experiment with the time frame for which OTPs are valid. Sometimes vulnerabilities arise from the way the system handles timing and frequency parameters, so pay close attention to these aspects.
Step 6: Analyze Server Responses: Carefully examine the server responses. Does the server issue special error messages when OTP attempts fail? Does it lock user accounts temporarily or permanently? Understanding these answers will help identify potential weaknesses and areas for improvement.
Step 7: Document and Report: Document your findings in detail. Include what vulnerabilities were discovered, how they could be exploited, and possible solutions to fix them. Prepare a full report for the site owner or administrator describing vulnerabilities and suggestions for strengthening security.
Important note: Always conduct these tests ethically and responsibly. Unauthorized testing is against the law and can have serious consequences. Get clear permission and make sure your actions are legal and ethical.
By following these steps, you can effectively test vulnerable OTP systems, helping organizations improve their security posture. Remember that ethical hacking is a powerful tool for strengthening digital security and ensuring a safe online environment for everyone.
Using the powerful capabilities of Burp Suite, we gain insight into potential vulnerabilities. Armed with this knowledge, we can work to harden systems to ensure they are resilient to OTP bypass attempts.
So, get ready to unlock the secrets of OTP bypass using Burp Suite. This is not just a tool, it is our digital Sherlock Holmes, leading us through the intricacies of cybersecurity.
Case studies and real-life examples
Welcome to the real battlefield for bypassing VET! In this section, we will look at real cases and examples that demonstrate the problems and consequences of an OTP security breach. These stories serve as a stark reminder of why strong security is paramount in today's digital landscape.Example 1: Triumph of the Social Engineer
Scenario: At a large multinational corporation, employees regularly receive emails from the IT department informing them of security protocols and software improvements. One day, an employee named Sarah received an email that seemed urgent to her. The letter claims that the letter came from the IT department and requests that her account be reviewed immediately due to a security breach. Sarah is asked to enter an OTP (One-Time Password) sent to her phone to verify her identity and prevent unauthorized access.Result: Trusting the urgency of the letter and its obvious source, Sarah enters the OTP without hesitation. It is unknown that this email was an elaborate phishing attempt. The attackers, posing as employees of the IT department, gain access to Sarah's account, which allows them to gain unauthorized access to the company's internal systems.
Consequences:
Consequences:
- Data breach. The attacker gains access to sensitive corporate data, including customer information, financial records and proprietary research, potentially leading to significant financial and reputational damage.
- Compromised communications. An attacker can monitor internal communications, allowing him to eavesdrop on confidential discussions, trade secrets, and upcoming business strategies.
- Financial implications. Depending on the nature of the company, a breach could result in financial loss due to theft of intellectual property or disruption of business operations.
Preventive action:
- Employee training: Provide regular cybersecurity training to employees, educating them on phishing attempts, how to identify suspicious emails, and the importance of validating requests for sensitive information.
- Multi-factor authentication (MFA). Implement MFA across all systems, ensuring that even if an attacker obtains the OTP, they will still require an additional authentication factor to access the account.
- Email authentication protocols. Use email authentication methods such as DMARC, SPF, and DKIM to verify the authenticity of incoming emails, reducing the likelihood of successful phishing attacks.
- Incident Response Plan: Develop a robust incident response plan that describes the steps to take in the event of a security breach. Update and test your plan regularly to ensure a quick and effective response.
Example 2: The weak link of the financial application
Scenario: A widely used financial application uses OTP (one-time password) verification to ensure transaction security. An eagle-eyed hacker discovers a vulnerability in the application code that allows him to exploit the OTP verification process.Result: The vulnerability allows an attacker to reuse old OTPs for unauthorized transactions. By manipulating the system, the hacker successfully reuses an outdated OTP to authenticate a large financial transaction.
Consequences:
- Financial Loss: The victim suffers financial loss due to a fraudulent transaction, which impacts their savings and can potentially cause severe financial hardship.
- Erosion of trust: Users lose confidence in the security of a financial application, which damages the company's reputation and potentially leads to the loss of customers.
- Regulatory Control: Financial institutions are subject to strict regulations. A security breach can result in investigations, fines and legal consequences, tarnishing an organization's reputation in the industry.
Preventive action:
- Regular security audits: Conduct regular security audits and code reviews to identify and fix vulnerabilities in the application, ensuring strong protection against hacking.
- Implement strong encryption. Use strong encryption protocols to protect one-time passwords during transmission, reducing the risk of interception and reuse.
- Token Expiration: Implement OTP token expiration mechanisms to ensure that one-time passwords have a limited period of use, making old tokens ineffective for verification.
- Dynamic Security: Explore advanced security measures such as dynamic one-time passwords generated based on transaction details that enhance security and make reused one-time passwords unnecessary.
- User education: Educate users on secure transaction methods, emphasizing the importance of maintaining the confidentiality of one-time passwords and promptly reporting any suspicious activity.
Example 3: SIM card replacement went wrong
Scenario: A sophisticated hacker targets a high-ranking individual and arranges for a SIM card swap using social engineering tactics. The hacker successfully convinces the victim's mobile operator to transfer the victim's phone number to a new SIM card under the hacker's control.Result: After gaining control of the victim's phone number, the hacker intercepts OTPs (one-time passwords) sent through text messages. Using these one-time passwords, the attacker gains unauthorized access to the victim's online accounts, compromising personal and financial information.
Consequences:
- Account hijacking: The attacker gains control of the victim's accounts, potentially gaining access to email, social media profiles, and financial accounts, resulting in identity theft and privacy violations.
- Financial losses. The victim may suffer financial losses if the hacker gains access to bank or investment accounts, makes unauthorized transactions, or steals funds.
- Disclosure of Confidential Information: Private conversations, contact details and confidential information stored on the victim's phone are exposed, putting personal and professional relationships at risk.
Preventive action:
- Security of mobile service providers. Mobile service providers must improve their customer verification processes, ensuring that SIM card replacement requires multiple layers of authentication and thorough verification of the customer's identity.
- More secure authentication methods. Encourage users to use authentication methods other than SMS-based OTP, such as authentication apps or hardware tokens, which are less vulnerable to SIM swapping attacks.
- Customer Awareness: Inform customers about the risks of SIM swapping and advise them to set up additional security measures with their mobile operator, such as PINs or passphrases to verify account changes.
- Regular monitoring. Users and organizations should regularly monitor their accounts for unusual activity, allowing them to promptly detect and report any unauthorized access.
Real example: WhatsApp OTP phishing
Scenario: Cybercriminals launch a massive phishing campaign targeting WhatsApp users. Victims are receiving deceptive messages claiming to be from WhatsApp support. The message informs users that their WhatsApp account will expire soon and asks them to verify their account by entering the OTP (one-time password) received via SMS.Result: Unsuspecting users, anxious at the thought of losing access to their messaging platform, enter the provided OTP without questioning its authenticity. The moment they send the OTP, the attackers take control of their WhatsApp accounts.
Consequences:
- Identity theft. Attackers may impersonate the victim by sending messages on their behalf, which can harm personal and professional relationships.
- Invasion of privacy: attackers gain access to private conversations, photos and multimedia files stored in the victim's WhatsApp account.
- Distribution of malware. Attackers can use compromised accounts to distribute malware or phishing links to a victim's contacts, potentially affecting a wider audience.
- Financial implications. In some cases, attackers use compromised accounts to conduct scams or request financial assistance from the victim's contacts, resulting in financial losses.
Preventive action:
- Awareness of official communications: Inform users about official communication channels used by platforms such as WhatsApp. Remind them that official communications usually come from the app and never ask for sensitive information such as one-time passwords via SMS or email.
- Two-factor authentication: Prompt users to enable two-factor authentication on WhatsApp. This adds an extra layer of security by requiring a PIN in addition to OTP for account verification.
- Phishing awareness: Train users to identify phishing attempts. Teach them to carefully check messages for unusual language, grammatical errors, and suspicious URLs. Be careful not to click on links from unknown sources.
- Reporting suspicious activity. Provide clear instructions on how to report suspicious messages or accounts on the messaging platform, giving users the opportunity to take immediate action against potential threats.
These case studies and real-life examples demonstrate the importance of strong OTP security measures and the need for vigilance among users. Cyber threats are real and constantly evolving, so it is critical for both individuals and organizations to stay informed and implement online security best practices.
By learning from these examples, we can better protect ourselves and our digital assets, ultimately helping to create a safer online environment. Stay informed, stay alert, and together we can combat OTP security challenges.
