Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,038
- Points
- 113

The Positive Hack Days 11 forum, held on May 18–19, 2022, was truly epic. In the competition for hacking ATMs, the competition was in earnest - 49 participants, this is very cool! The prize fund this year was 50,000 rubles, it was taken by a person with the nickname Igor, who was the first to break the virtual machines. By the way, he wasn’t even at the event!
In addition to the winner, this year eight people were awarded who showed good results while hacking virtual machines, namely: drd0c, vient, vrazov, durcm, zxcvcxzas7, asg_krd, hundred303, drink_more_water_dude. We would like to thank all participants, and for those who were not at PHDays, we provide links to virtual machines:
Figure 1. ATM interface
As for the tasks, they were the same for two different virtual machines:
1) bypassing the kiosk (was solved 34 times);
2) AppLocker bypass (solved 21 times);
3) elevation of privileges to administrator (resolved 12 times).
On drive C there were several files: task_kiosk.exe, task_applocker.exe, task_escalation.exe, which had to be launched for the task to count. The file task_kiosk.exe was available for launch immediately after bypassing the kiosk, task_applocker.exe was blocked using AppLocker, and administrator rights were required to run task_escalation.exe.
Architectural solutions this year allow us to track the number of participants and solved tasks through a telegram bot, which is why we can provide more detailed statistics (Figure 2).

Figure 2. Total number of participants
Analysis of tasks
It should be noted that this year there was much more scope for the participants to act, and each task on the virtual machine had a large number of solutions. Last year, participants took too long to walk around the kiosk, and some simply abandoned the task before completing it. This year's changes have brought results, and we have received very interesting solutions that were not included in the script.Below, an overview of the solutions is presented in general form, without reference to specific virtual machines. Participants will easily understand which solution fits which machine. This is done so that interested readers of the article have space to solve our problems.
Exit kiosk mode. First way
Many did not even suspect how simple it was. To exit kiosk mode in one of the virtual machines, you had to use the right mouse button. Surprisingly, the participants did not notice that the right mouse button worked and, like last year, looked for key combinations to exit kiosk mode. The kiosk application was a web browser written in Delphi, so the complete kiosk bypass script looked like this: right mouse button → Print → Find Printer (Figure 3).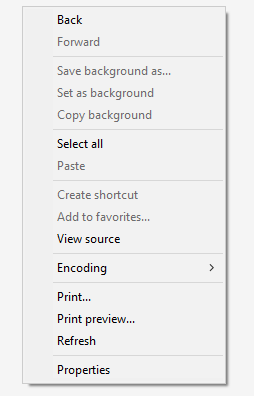
Figure 3. Menu after right-clicking
These actions allowed you to open the explorer.exe file and go to drive C to run task_kiosk.exe .
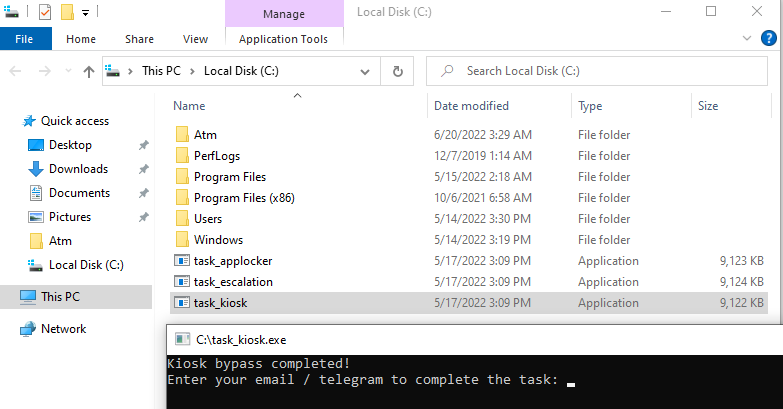
Figure 4. Completing the first task
Exit kiosk mode. Second way
In another virtual machine, things were a little more complicated, since the right mouse button was disabled along with the main keys. To exit the kiosk mode, a network vector was laid down that required scanning the ATM ports. After scanning ports using Nmap, participants may have noticed that a certain service is located on port 80. The easiest way to find out what's working there is to follow the link http://<atm_adress>:80 . A web server was specially written for the competition, running on port 80. For every user connection to it, it returned an error and opened a help page in a browser on a virtual machine.
Figure 5. Demonstration of the Nmap interface
In my case, the ATM IP was 192.168.56.102 and an Nmap scan showed that port 80 was open. After going to this address in the browser, an error appeared in which clicking on the “OK” button opened the Internet Explorer browser.
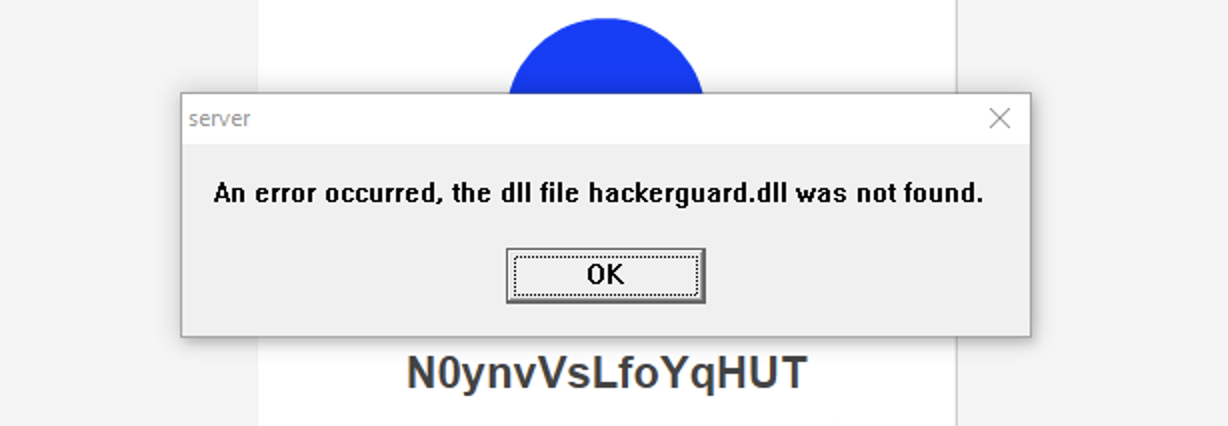
Figure 6. Embedded error
Figure 7. Demonstration of opening the browser after clicking “OK”
Exiting the browser is largely identical to the first scenario and can be done through Internet Explorer downloads.
Bypass AppLocker. First way
For unknown reasons, the script embedded in one of the virtual machines refused to work at the last moment, for which we apologizewlrmdr.exe -s 3600 -f 0 -t Click me! -m To run calculator -a 10 -u C:\task_applocker.exe
The above command, bypassing AppLocker, was supposed to show a notification, after clicking on which task_applocker.exe should have been launched, but for some reason this did not happen, and the warning from AppLocker did not appear.
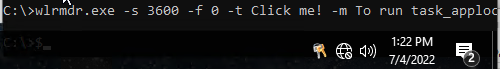
Figure 8. Demonstration of the wlrmdr.exe notification (keys in the Start line)
Bypass AppLocker. Second way
As for the second AppLocker bypass, everything worked fine. The rules checked the hash of the EXE file, so the bypass was as simple as possible (the solution was suggested by hx0day).We create an empty file 0.txt and execute the command copy /b task_applocker.exe+0.txt notepad.exe, and we get the file notepad.exe - essentially, a copy of task_applocker.exe with a different hash. We run it and get a ready-made solution.
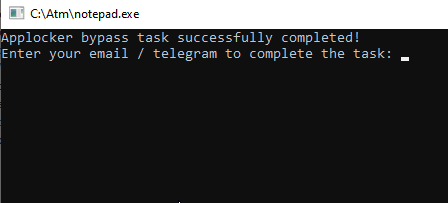
Figure 9. Executing task_applocker.exe

Figure 10. AppLocker rules
Elevation of privileges. First way
Elevating privileges in one of the virtual machines was quite simple. The script was to search for PowerShell history. Often, administrators using this software forget to delete the history of entered commands. PowerShell history, in turn, is accessible without administrator privileges, and hackers can use the information left there. In our case, in one of the virtual machines in the history, the administrator login and password were left in clear text. They could be found in the following path:C:\Users\ATM\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
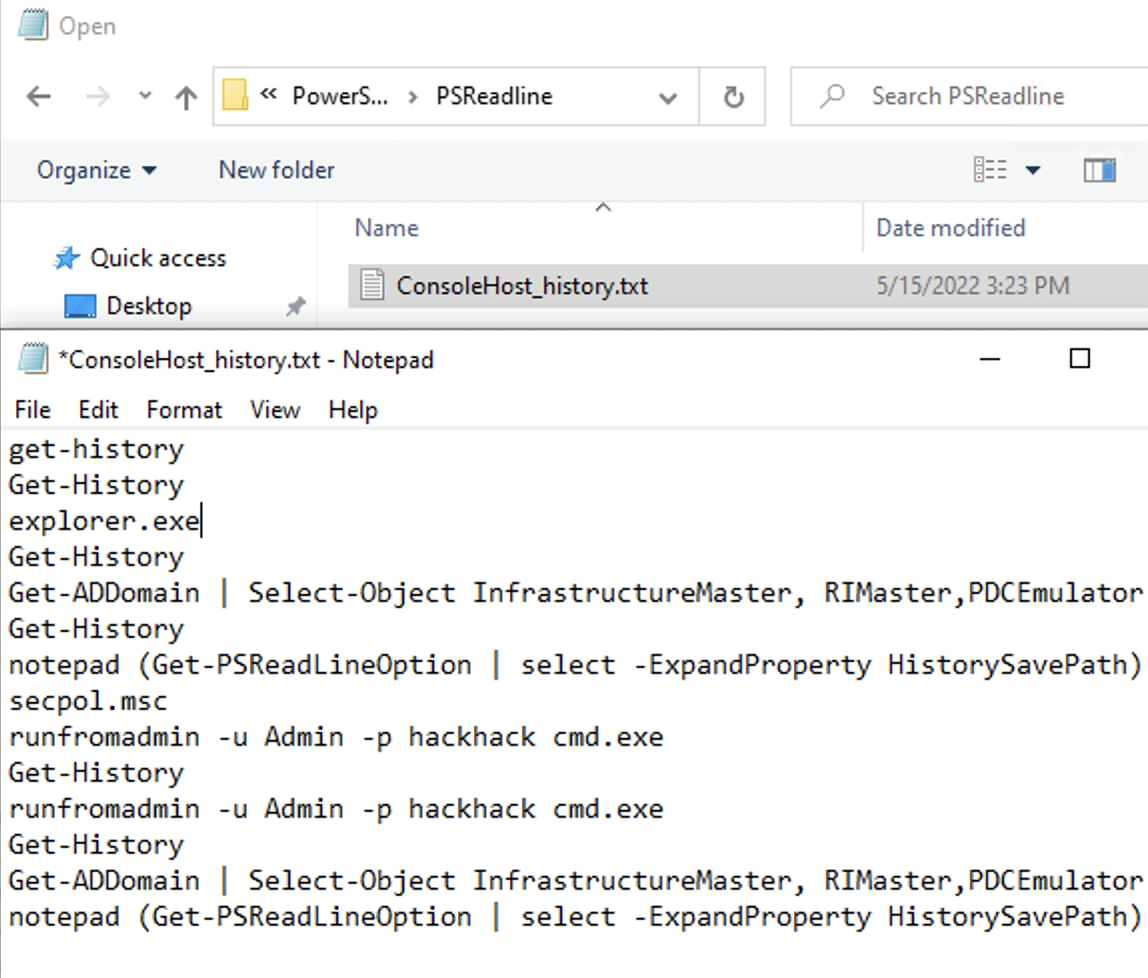
Figure 11. Administrator login and password in clear text
Elevation of privileges. Second way
Another way to escalate privileges was as non-standard as possible and was to use the runas command and find a shortcut on the administrator's desktop that opens a command line interpreter with maximum privileges. This command allows you to run EXE files with administrator rights. The fact is that some command arguments, such as /savecard , allow you to save the administrator login and password and launch applications in the future without entering this data.
Code:
runas /user:Admin /savecard cmd.exeHowever, there are nuances here too: when you execute the following command, the console opens, and you can see that it is running as an administrator, but after a more detailed check, you can understand that there are still no corresponding rights. However, along with this we have the opportunity to go to the administrator’s desktop, where we need to launch a shortcut.
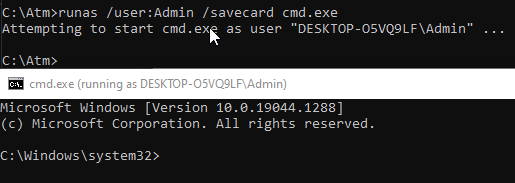
Figure 12. Executing the command and launching the console as administrator
We try to run task_escalation.exe and see the following error:
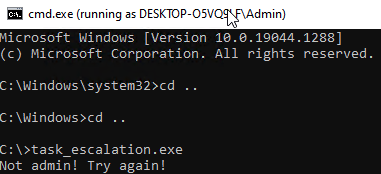
Figure 13. Lack of administrator rights
Next, launch the shortcut aministrator_cmd.lnk, located along the path C:\Users\Admin\Desktop.
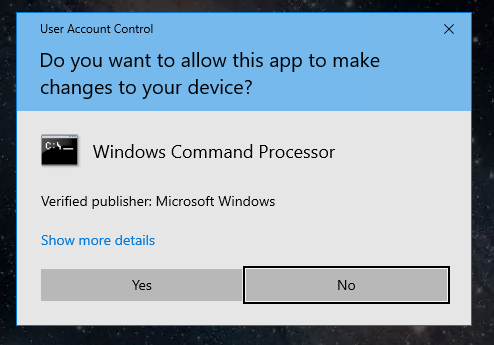
Figure 14. Launching the console
After this, you can run task_escalation.exe with full administrator rights to finally complete this task.

Figure 15. Running task_escalation.exe
Additional tasks
Now let's look at additional tasks. Let us recall that the ATM interface was a web page located at http://bank.paymentvillage.org. It is still available. The tasks are included in the additional category because they are indirectly related to the ATM and involve searching for classic web vulnerabilities. For convenience and to simplify hacking, PHP errors were included among the errors.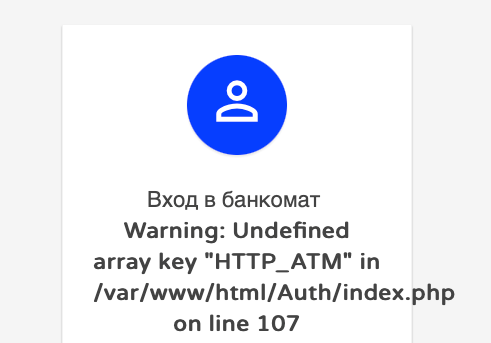
Figure 16. PHP error
Just a few people tried to break down the ATM cabinet, and we received reports on the laid down scenarios. The first vulnerability that was found by vient was Path Traversal. We happily gave him the T-shirt.
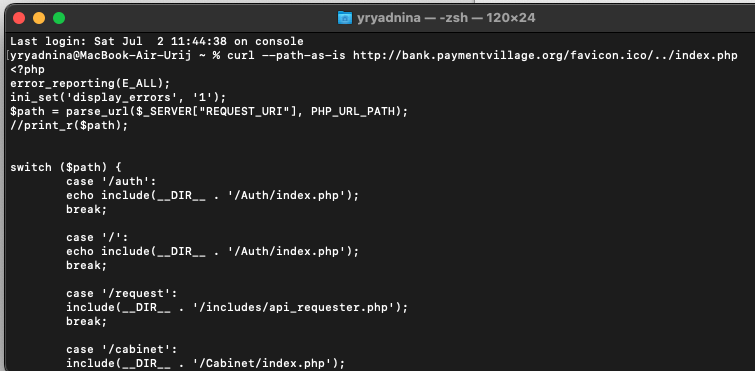
Figure 17. Source code of the index.php page
Code:
curl --path-as-is http://bank.paymentvillage.org/favicon.ico/../index.phpTo view the source code, you had to run the above command.
By the way, the error shown in Fig. 16 could have led the participants to another underlying vulnerability, but, unfortunately, no one found it. The fact is that the ATM code, written in Delphi, constantly read the file C:\Atm\atmkey.txt. This file contained atmkey, a unique identifier for the ATM, which we could use to track the execution of tasks. Next, atmkey was automatically inserted into each request in the form of an ATM header, and authorization at the ATM took place with it. This header is needed, among other things, so that money can be issued at a specific ATM (virtual machine). As a result, self-xss could be exploited by passing malicious JS code in the ATM header.
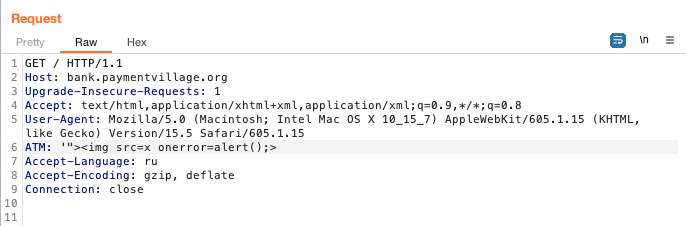
Figure 18. Demonstration of sending a request
Nobody discovered the following vulnerability either, although it could be found very easily by just changing the contents of the file C:\Atm\atmkey.txt. To do this, you didn’t even need to use tools that allow you to carry out MITM attacks. This is what it looks like:
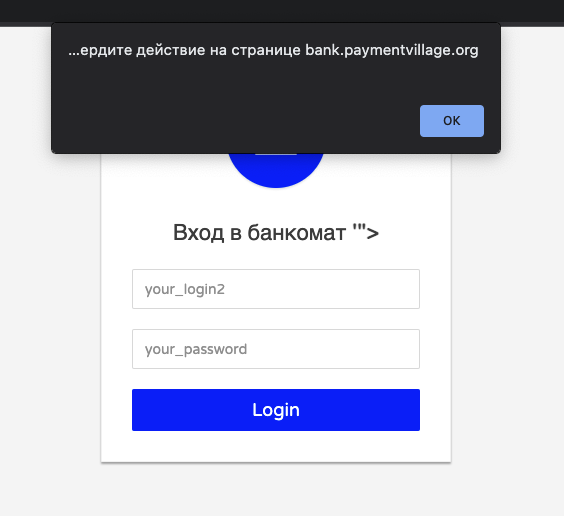
Figure 19. XSS Exploitation
This year, the included scenarios also included ARP Spoofing, the analysis of which we will not delve into, since an example of such an attack was described earlier. The point was that participants needed to forge the response http://bank.paymentvillage.org/payout?atmid= <your_atm_id> in order for the application C:\Atm\payout.exe to be launched on the second virtual machine, simulating the issuance of money . The ATM accesses this address every 5 seconds and waits for a true response to start dispensing money.
In addition, of course, there are vulnerabilities in the scenarios that you want to keep secret in order to maintain intrigue.
Conclusions
This year the set scenarios turned out to be very simple for the participants. Many had time to prepare well. Apparently, last year’s article played a roleWe realized that we need to look for a balance of complexity, and we made certain conclusions that we will implement next year. At the same time, many participants did not realize the real scale of the competition and performed only basic tasks.
Certificates were sent to the participants, and the first reviews have already been received. We hope everyone has received their prizes by the time this article is published. With the permission of one of the participants (thanks for the feedback, durcm !) we are publishing a photo with a certificate.

I would also like to say a huge thank you to our international participants, in particular Boschko. For several years now he has been sharing the walkthroughs of our virtual games with his readers:
Find more information about Payment Village on Telegram. See you soon!
Author: @yurasikhacker

