Man
Professional
- Messages
- 3,221
- Reaction score
- 1,187
- Points
- 113
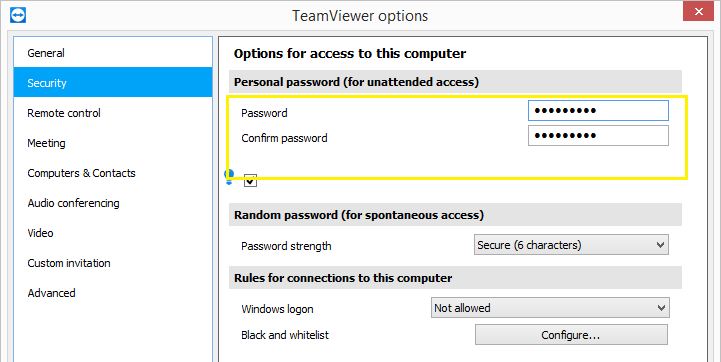
TeamViewer is a popular program for remote desktop access. So it is quite interesting to see how it stores passwords. In short, passwords are stored in the Windows registry in encrypted form. The encryption algorithm is AES-128-CBC and the secret key is 0602000000a400005253413100040000.
This method of storing passwords and the associated privilege escalation were officially registered on February 7, 2020 as a vulnerability CVE-2019-18988 (applicable to all TeamViewer versions up to and including 14.7.1965).
The rookie security researcher who made this vulnerability public stumbled upon it by accident. He says OptionsPasswordAES he was working for a client and noticed TeamViewer registry keys called and during a backup SecurityPasswordAES.
He later became curious about these keys and how TeamViewer stores passwords. He imported them to a fresh system on a virtual machine and ran the BulletPassView scanner, which collects passwords from the system. The scanner returned the TeamViewer password in plain text.
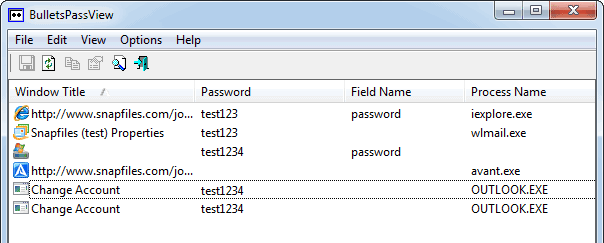
BulletPassView Scanner
Then, using the Cheat Engine program (for hacking games under Windows), the specialist searched for this password in RAM - and found it again in plain text. Later it turned out that this vulnerability was already recorded two years ago as CVE-2018-14333.
Then it was time to check where the TeamViewer client's memory gets the key from: from the server or from the local host. It turned out that there is no network traffic, but the password is still in memory. Reverse engineering the TeamViewer binary using IDA Pro, API Monitor, procdump and Frida took several weeks, but did not give anything, although the guy mastered several new tools along the way, so the process cannot be called useless.
During the search for information, it turned out that many people had already wondered how to find AES keys for Unity games in resources. It turned out that this is a very simple process, for which it is enough to use a debugger. Six hours later, he found a fragment of TeamViewer code responsible for AES encryption:
Code:
=================================================
"ServerPasswordAES"=hex:88,44,d7,0a,b2,96,2a,3d,63,16,3c,ff,e4,15,04,fb
=================================================
Takes 8844d70ab2962a3d63163cffe41504fb into xmm0
Takes 5B659253E5E873D26723B7D5EAC06E3B into xmm1
pxor xmm0, xmm1
movdqa xmmword ptr ds:[eax],xmm0
[eax] = D3214559577E59EF04358B2A0ED56AC0
movdqa xmm1,xmmword ptr ds:[esi] | [esi] = 25C8C8BD4298BB32A57EECBDBD045BBB
movdqa xmm0,xmmword ptr ds:[eax] | [eax] = D3214559577E59EF04358B2A0ED56AC0
aesdec xmm0,xmm1 | One round of an AES decryption, using Equivalent Inverse Cipher, 128-bit data (state) from xmm1 with 128-bit round key from xmm2/m128; store the result in xmm1.
movdqa xmmword ptr ds:[eax],xmm0 | [eax] = 6F AA 98 76 DE 11 7D 8D 7E B6 EE 61 2D 3D 15 52
movdqa xmm1,xmmword ptr ds:[esi+10] | [esi+10]=[008FDE10]=79 DC 78 A6 67 50 73 8F E7 E6 57 8F 18 7A B7 06
add esi,20 |
dec ecx | ecx = 3
aesdec xmm0,xmm1 | do the actual decryption
movdqa xmmword ptr ds:[eax],xmm0 | [eax]=[008FDC90]=E3 58 26 46 A7 37 12 40 85 1C C0 43 7D 1F 1E 30
Three more rounds of aesdec then
aesdeclast xmm0, xmm1 .| Last round of AES decryption, using Equivalent Inverse Cipher, 128-bit data (state) from xmm2 with a 128-bit round key from xmm3/m128; store the result in xmm1.
008FDC90 01 00 01 00 67 24 4F 43 6E 67 62 F2 5E A8 D7 04 ....g$OCngbò^¨×.This code takes several bytes from the registry ServerPasswordAESand decrypts them using a key obtained by XORing the specified values esiand eax. The resulting key is 0602000000a400005253413100040000, and the IV value is 0100010067244F436E6762F25EA8D704.
In TeamViewer version 14, the new script engine allows you to increase privileges to NT AUTHORITY\SYSTEM, by reading the TeamViewer password in the registry with user rights.
Well, you can also decrypt some other people's passwords by googling [SecurityPasswordAES], [OptionsPasswordAES], [SecurityPasswordExported] or [PermanentPassword] with the search parameter [filetype:reg].
TeamViewer closed this vulnerability in the latest versions. How the program now encrypts passwords is still unclear.
Source

