BadB
Professional
- Messages
- 1,910
- Reaction score
- 1,951
- Points
- 113
How the honeypot works
Hanipot is a utility designed to attract the attacker's attention, allowing the defender to learn more about the attacker's identity and hacking tactics. Honeypots can take many forms: they are often disguised as important files, email messages, links, account data, or devices that are most likely to attract the attacker's interest. The ideal honeypot looks as plausible as possible, in an attempt to compromise the attacker through its own disclosure to the defending party.
There are many creative and useful ways that defenders have come up with to detect and unmask intruders using hanipots. For example, the classic "Kippo" bait is famous for its way to disguise itself as a vulnerable SSH service accessible from the Internet with a weak account. Kippo lures out the attacker with its easy accessibility, while secretly recording all the activity that occurs inside.
Such honeypots reveal attackers who have penetrated an unsecured network, and allow researchers to analyze the payload used by automated bots to attack vulnerable targets. They also contributed to the development of the genre of YouTube videos with script-wretches desperately trying to hack Kippo-hanipots.
Some honeypots can even mislead hackers that they have already connected back to their own system, while continuing to record all their actions in the terminal window, bringing the degree of cunning to a new level. This allows you to learn more about the attacker's identity and other systems that they have access to.
Modern honeypots can be anywhere
Hanipots have evolved to be quite difficult to detect, as attackers have already become accustomed to avoiding targets that look too good to be true.
Using the free canarytoken tracker, the defender can embed a tracking link based on the DNS Protocol or web links that are launched as soon as the PDF file is opened. CanaryToken collects the IP addresses of anyone who tries to open a tracked file, which may contain sensitive information.
To catch attackers using phishing tactics, the defending party can use honeypot links embedded in the website code. This will allow you to detect cases of website cloning, warning the defenders in advance of a possible attack.
Other honeypots track stolen credentialsby taking the form of a fake username and password (so-called "Honeycredentials") stored in a file with an "important" name in a relatively easily accessible place for the attacker inside the network. If an attacker attempts to use these credentials, the defending party immediately receives a notification about an attempt to use the stolen information to gain access to the account.
Another use of honeypots is to use tracking links to know when an attacker publishes your links on Skype, WhatsApp, or another messenger. This is possible due to the fact that most chat apps automatically click on links to generate URL previews. Despite the fact that the logged IP address belongs to the messenger app and not to the attacker, this tactic allows you to find out whether the tracked honeypot links are transmitted to someone else or not, even if the attacker is smart enough to never click on them.
Hanipot can be used by anyone
In the "wild West" of shopping sites, online Dating sites, and rental properties, it's easy to imagine that there's no way to check who you're actually talking to. Scammers and bots taking advantage of this situation may sound extremely convincing, but their real background can often be found out if they can be tricked into revealing information about their location, keyboard layout, or language settings that do not match their stories. Thanks to this, hanipots have gained popularity among ordinary people who use tracking links to change the course of the game, during which attackers take advantage of anonymity on the Internet.
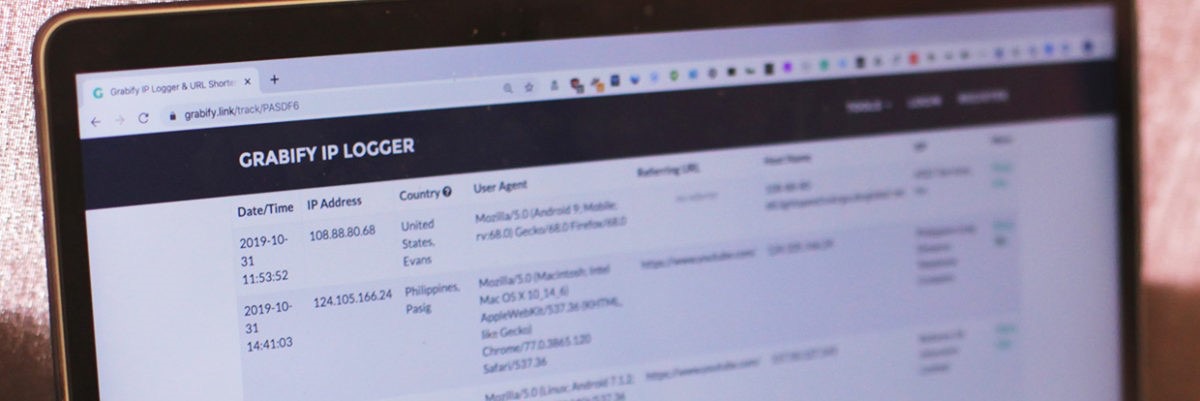
Tracking web links are easily embedded in web pages, run scripts, or email messages and are free for everyone. If an attacker opens a link directly or through opening a file that calls the URL, the defender can learn information about the attacker's hardware, software, and network data. Even if an attacker tries to hide their real IP address using a VPN, information about their real identity can still leak. Grabify it can detect differences such as mismatched time zones or keyboard layouts that don't match the location of an IP address, or even detect an attacker using a VPN or Tor to hide their information.

Tracking honeypot links can level the odds for people who are usually at a disadvantage when dealing with various suspicious individuals online, by identifying details that are otherwise very difficult to verify. When using tracking links that lead to sites that are logical to share when communicating with a potential landlord, the tenant can stay away from "too good to be true" offers by identifying attackers who are deceiving about their location. For example, this might allow you to identify someone from India posing as a landlord in Los Angeles.

Honeybots generate real-time alerts
Honeypots are inexpensive and easy to deploy. They are one of the best ways to detect when something is going wrong. For example, a DNS-tracked CanaryToken mailbox with a list of important contacts can immediately report a leak of credentials from this list, informing you about a situation that would otherwise take months to detect.
Information security researcher Kevin Beaumont deployed an RDP honeypot network called "BluePot" to detect BlueKeep exploits in the wild, to provide timely warnings about worm exploits and prevent large-scale attacks like NotPetya and WannaCry.
Modern honeypots expand the boundaries of understanding how easy they can be deployed and how convincing they seem to the attacker. While impressive next-generation honeypots can virtualize entire networks in an attempt to catch more advanced attackers who can spot the usual bait, most companies will benefit even from using simple and free honeypot tactics, being the first to learn about the attacker's penetration.
Hanipot is a utility designed to attract the attacker's attention, allowing the defender to learn more about the attacker's identity and hacking tactics. Honeypots can take many forms: they are often disguised as important files, email messages, links, account data, or devices that are most likely to attract the attacker's interest. The ideal honeypot looks as plausible as possible, in an attempt to compromise the attacker through its own disclosure to the defending party.
There are many creative and useful ways that defenders have come up with to detect and unmask intruders using hanipots. For example, the classic "Kippo" bait is famous for its way to disguise itself as a vulnerable SSH service accessible from the Internet with a weak account. Kippo lures out the attacker with its easy accessibility, while secretly recording all the activity that occurs inside.
Such honeypots reveal attackers who have penetrated an unsecured network, and allow researchers to analyze the payload used by automated bots to attack vulnerable targets. They also contributed to the development of the genre of YouTube videos with script-wretches desperately trying to hack Kippo-hanipots.
Some honeypots can even mislead hackers that they have already connected back to their own system, while continuing to record all their actions in the terminal window, bringing the degree of cunning to a new level. This allows you to learn more about the attacker's identity and other systems that they have access to.

Modern honeypots can be anywhere
Hanipots have evolved to be quite difficult to detect, as attackers have already become accustomed to avoiding targets that look too good to be true.
Using the free canarytoken tracker, the defender can embed a tracking link based on the DNS Protocol or web links that are launched as soon as the PDF file is opened. CanaryToken collects the IP addresses of anyone who tries to open a tracked file, which may contain sensitive information.
To catch attackers using phishing tactics, the defending party can use honeypot links embedded in the website code. This will allow you to detect cases of website cloning, warning the defenders in advance of a possible attack.
Other honeypots track stolen credentialsby taking the form of a fake username and password (so-called "Honeycredentials") stored in a file with an "important" name in a relatively easily accessible place for the attacker inside the network. If an attacker attempts to use these credentials, the defending party immediately receives a notification about an attempt to use the stolen information to gain access to the account.
Another use of honeypots is to use tracking links to know when an attacker publishes your links on Skype, WhatsApp, or another messenger. This is possible due to the fact that most chat apps automatically click on links to generate URL previews. Despite the fact that the logged IP address belongs to the messenger app and not to the attacker, this tactic allows you to find out whether the tracked honeypot links are transmitted to someone else or not, even if the attacker is smart enough to never click on them.
Hanipot can be used by anyone
In the "wild West" of shopping sites, online Dating sites, and rental properties, it's easy to imagine that there's no way to check who you're actually talking to. Scammers and bots taking advantage of this situation may sound extremely convincing, but their real background can often be found out if they can be tricked into revealing information about their location, keyboard layout, or language settings that do not match their stories. Thanks to this, hanipots have gained popularity among ordinary people who use tracking links to change the course of the game, during which attackers take advantage of anonymity on the Internet.
Tracking web links are easily embedded in web pages, run scripts, or email messages and are free for everyone. If an attacker opens a link directly or through opening a file that calls the URL, the defender can learn information about the attacker's hardware, software, and network data. Even if an attacker tries to hide their real IP address using a VPN, information about their real identity can still leak. Grabify it can detect differences such as mismatched time zones or keyboard layouts that don't match the location of an IP address, or even detect an attacker using a VPN or Tor to hide their information.

Tracking honeypot links can level the odds for people who are usually at a disadvantage when dealing with various suspicious individuals online, by identifying details that are otherwise very difficult to verify. When using tracking links that lead to sites that are logical to share when communicating with a potential landlord, the tenant can stay away from "too good to be true" offers by identifying attackers who are deceiving about their location. For example, this might allow you to identify someone from India posing as a landlord in Los Angeles.

Honeybots generate real-time alerts
Honeypots are inexpensive and easy to deploy. They are one of the best ways to detect when something is going wrong. For example, a DNS-tracked CanaryToken mailbox with a list of important contacts can immediately report a leak of credentials from this list, informing you about a situation that would otherwise take months to detect.
Information security researcher Kevin Beaumont deployed an RDP honeypot network called "BluePot" to detect BlueKeep exploits in the wild, to provide timely warnings about worm exploits and prevent large-scale attacks like NotPetya and WannaCry.
Modern honeypots expand the boundaries of understanding how easy they can be deployed and how convincing they seem to the attacker. While impressive next-generation honeypots can virtualize entire networks in an attempt to catch more advanced attackers who can spot the usual bait, most companies will benefit even from using simple and free honeypot tactics, being the first to learn about the attacker's penetration.
