From a legal point of view, cryptocurrency can be defined as property in electronic form, created using cryptographic means, and recorded in the distributed register of digital transactions in accordance with the established rules for its maintenance.
From a technical point of view, cryptocurrency is a distributed, open-source peer-to-peer virtual currency based on mathematical principles, which does not have a centralized administrator, as well as appropriate control and supervision by government agencies or other third parties.
Cryptocurrencies have significant differences from the usual financial transactions. They do not require a centralized regulator or issuer. At the same time, all cryptocurrency transactions are public and recorded in a special register - the blockchain. At the same time, there is no data on the actual owner of a particular cryptocurrency wallet in the blockchain. It is anonymous, and actually has the ability to create an unlimited number of unique addresses to the wallet.
The existing methodology for deanonymizing cryptocurrency transactions involves tracking the entire chain of their execution from the moment of the payment under study to the intended exchange of cryptocurrency for "fiat money" through cryptocurrency exchanges, in an exchanger or ATM.
To collect data about crypto wallets and track their transactions, you can use regular blockchain browsers:
As well as universal browsers:
The latter make it possible to conduct a more thorough analysis and study several cryptocurrencies in one service. Browsers store the following information about completed transactions:

Some of these shortcomings can be offset by using free software. So the visual representation of cryptocurrency transactions can be organized using the services:
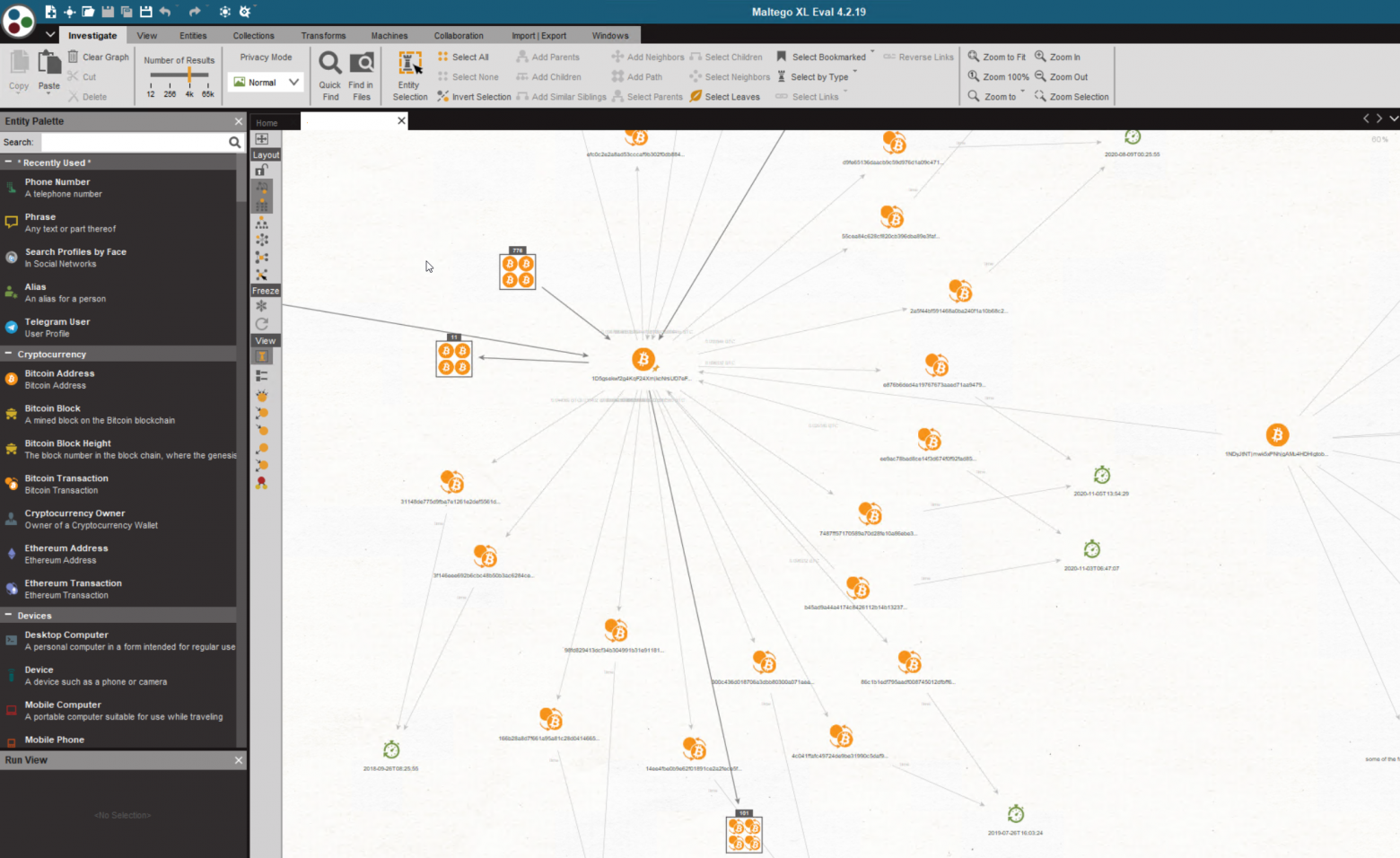
Now that we know how to organize transactions in a virtual environment, we need to move on to studying the question of assigning each specific crypto wallet to known entities.
The first thing that comes to mind here is the use of regular Google search capabilities. Proof of ownership of a crypto wallet can be provided by specifying the address of a cryptocurrency wallet as a payment system on a website, social network, messenger, blog, or forum. Such data can be detected by Google's search engines.
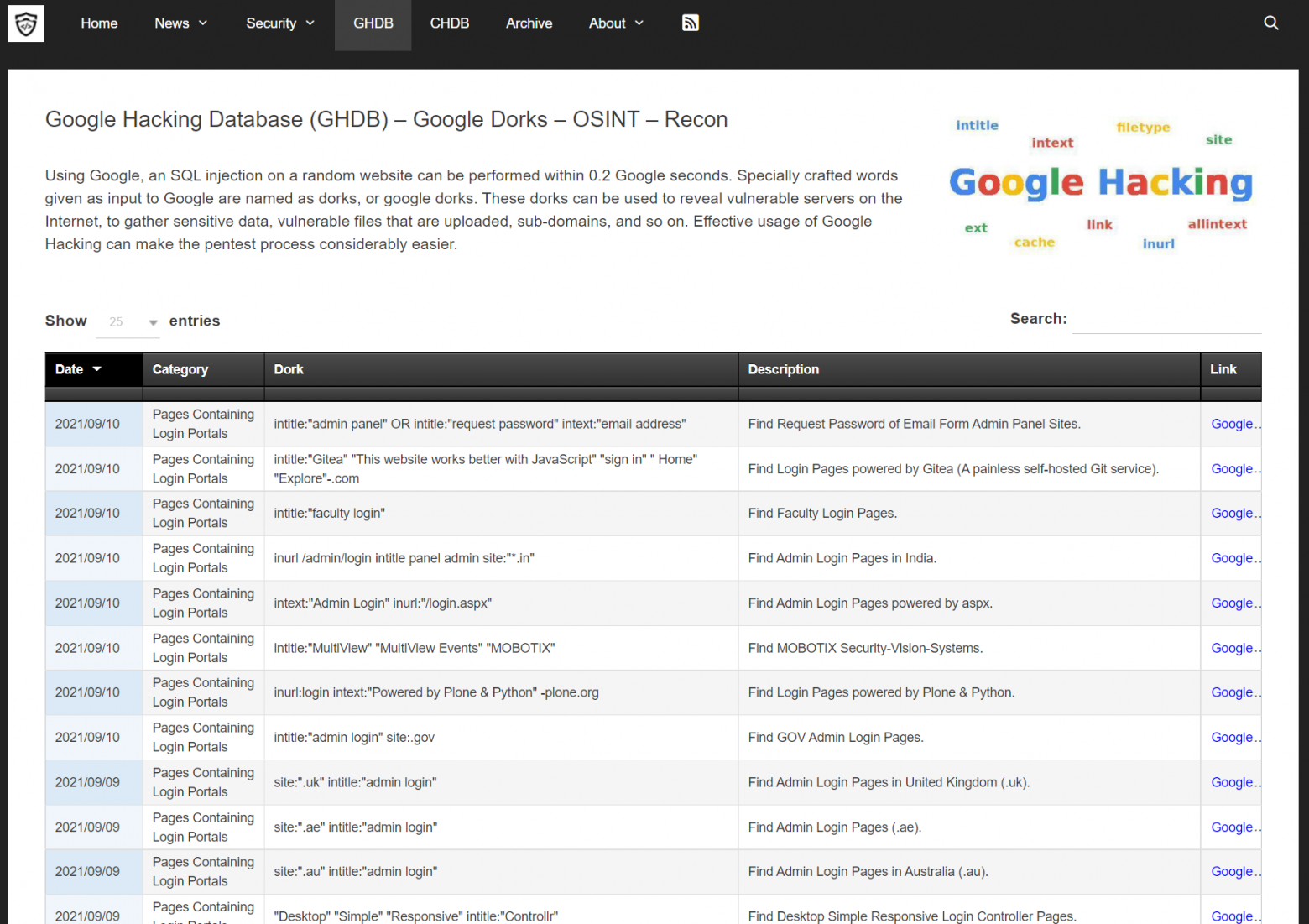
Of particular interest is the use of Google Dorks.
For example, the search query [url_cryptocashel -block] allows you to clean up the output, excluding most of the blockchain browsers from it.
Request for [site:bitcointalk.org address_cryptoshelka] allows you to search for information about the cryptoshelka on the selected site.
Request for [site:https://docs.google.com/spreadsheets Bounty intext: "@gmail.com"] makes it possible to find lists of identified crypto wallets involved in Bug Bounty programs.
The use of search engines allows us to find a link between the address of a cryptocurrency wallet and other identifiers that may be useful for identifying its user.
These identifiers include:
You can identify a user's photo by clicking on the following links:

Identification of contacts of site owners and domain names is possible when using sites such as:
WHOIS data, including archived data, is available on the following resources:
Ad ID analysis - using the following services:
The mobile phone number and email address of the cryptoasset owner can be identified using the TelPoisk, Infosphere, NEO, Prima Inform, IDX, Spectrum Data and a number of other services.
Further information about crypto wallets should be searched on otzoviki.
They are interesting because they aggregate data about the use of wallets in illegal activities. These services include:
In part, we can also refer to the service as "otzoviki" bitrankverified.com, which allows you to conduct a scoring assessment of the cryptographic wallet.
And you can check whether a crypto wallet belongs to an exchange, exchanger, or other entity using resources such as:
habrastorage.org
From a technical point of view, cryptocurrency is a distributed, open-source peer-to-peer virtual currency based on mathematical principles, which does not have a centralized administrator, as well as appropriate control and supervision by government agencies or other third parties.
Cryptocurrencies have significant differences from the usual financial transactions. They do not require a centralized regulator or issuer. At the same time, all cryptocurrency transactions are public and recorded in a special register - the blockchain. At the same time, there is no data on the actual owner of a particular cryptocurrency wallet in the blockchain. It is anonymous, and actually has the ability to create an unlimited number of unique addresses to the wallet.
The existing methodology for deanonymizing cryptocurrency transactions involves tracking the entire chain of their execution from the moment of the payment under study to the intended exchange of cryptocurrency for "fiat money" through cryptocurrency exchanges, in an exchanger or ATM.
To collect data about crypto wallets and track their transactions, you can use regular blockchain browsers:
- btc.com
- etherscan.io
- xrpcharts.ripple.com/#/graph
- explorer.bitcoin.com/bch
- litecoinblockexplorer.net
- steexp.com
As well as universal browsers:
- blockchair.com
- tokenview.com
- blockchain.com
- bitaps.com
- live.blockcypher.com
The latter make it possible to conduct a more thorough analysis and study several cryptocurrencies in one service. Browsers store the following information about completed transactions:
- date and time of the transaction
- addresses of the sender's and recipient's cryptocurrency wallets
- amount of cryptocurrency transferred
- transaction fee and hash (which serves as proof of the transaction and is used to verify it)

Some of these shortcomings can be offset by using free software. So the visual representation of cryptocurrency transactions can be organized using the services:
- sicp.ueba.su
- graphsense.info
- blockpath.com
- c-hound.ai
- oxt.me
- repository github.com/s0md3v/Orbit

Now that we know how to organize transactions in a virtual environment, we need to move on to studying the question of assigning each specific crypto wallet to known entities.
The first thing that comes to mind here is the use of regular Google search capabilities. Proof of ownership of a crypto wallet can be provided by specifying the address of a cryptocurrency wallet as a payment system on a website, social network, messenger, blog, or forum. Such data can be detected by Google's search engines.
Of particular interest is the use of Google Dorks.
For example, the search query [url_cryptocashel -block] allows you to clean up the output, excluding most of the blockchain browsers from it.
Request for [site:bitcointalk.org address_cryptoshelka] allows you to search for information about the cryptoshelka on the selected site.
Request for [site:https://docs.google.com/spreadsheets Bounty intext: "@gmail.com"] makes it possible to find lists of identified crypto wallets involved in Bug Bounty programs.

The use of search engines allows us to find a link between the address of a cryptocurrency wallet and other identifiers that may be useful for identifying its user.
These identifiers include:
- first name or nickname
- email address
- phone number
- user id in a social network or messenger
- photo
- site address
- other digital assets, etc
You can identify a user's photo by clicking on the following links:
- findclone.ru
- search4faces.com

Identification of contacts of site owners and domain names is possible when using sites such as:
- domainbigdata.com
- phonebook.cz
- mailshunt.com
- hunter.io
WHOIS data, including archived data, is available on the following resources:
- whois.domaintools.com
- drs.whoisxmlapi.com/whois-history

Ad ID analysis - using the following services:
- spiderfoot.net
- themarkup.org/blacklight
- urlscan.io
- spyonweb.com
- dnslytics.com/reverse-analytics

The mobile phone number and email address of the cryptoasset owner can be identified using the TelPoisk, Infosphere, NEO, Prima Inform, IDX, Spectrum Data and a number of other services.
Further information about crypto wallets should be searched on otzoviki.
They are interesting because they aggregate data about the use of wallets in illegal activities. These services include:
- bitcoinabuse.com
- bitcoinwhoswho.com
- checkbitcoinaddress.com
- cryptscam.com
- scam-alert.io

In part, we can also refer to the service as "otzoviki" bitrankverified.com, which allows you to conduct a scoring assessment of the cryptographic wallet.
And you can check whether a crypto wallet belongs to an exchange, exchanger, or other entity using resources such as:
- walletexplorer.com
- bitinfocharts.com
- oxt.me
habrastorage.org
