Man
Professional
- Messages
- 3,223
- Reaction score
- 1,148
- Points
- 113
Against the backdrop of events in the US, the popularity of the secure messenger Signal has grown sharply - from 6,000 to 26,000 downloads per day. This program implements strong cryptography and end-to-end encryption, it is distributed with open source code and runs on well-known cryptographic protocols (unlike the proprietary MProto).
But now the developers of Signal are faced with a new threat. The US government is trying to compromise the messenger's security and again gain access to users' correspondence. In 2016, they managed to get a subpoena to seize the correspondence of one user, but due to end-to-end encryption, there was nothing to seize.
The only data Signal can provide to a government request or subpoena is the data it holds about a user. This includes:
And that’s it. No contacts, group information, or profile data.

The user profile that Signal provided under a subpoena. Screenshot from the court documents
“We designed Signal so that personal data is stored by customers, not us,” the developers write. “Signal uses end-to-end encryption, so we never have access to the content of the messages you send. They are visible only to you and the intended recipients. However, Signal also applies this design philosophy to the rest of your data.”
Unlike any other popular messenger, Signal does not have access to your contacts, social graph, group data, group status information, profile name, profile avatar, location data, search history, and so on. There are no trackers, ads, or analytics code in the program’s code. Absolutely all information is encrypted, except for the account creation date and the date of last use, as shown in the screenshot.
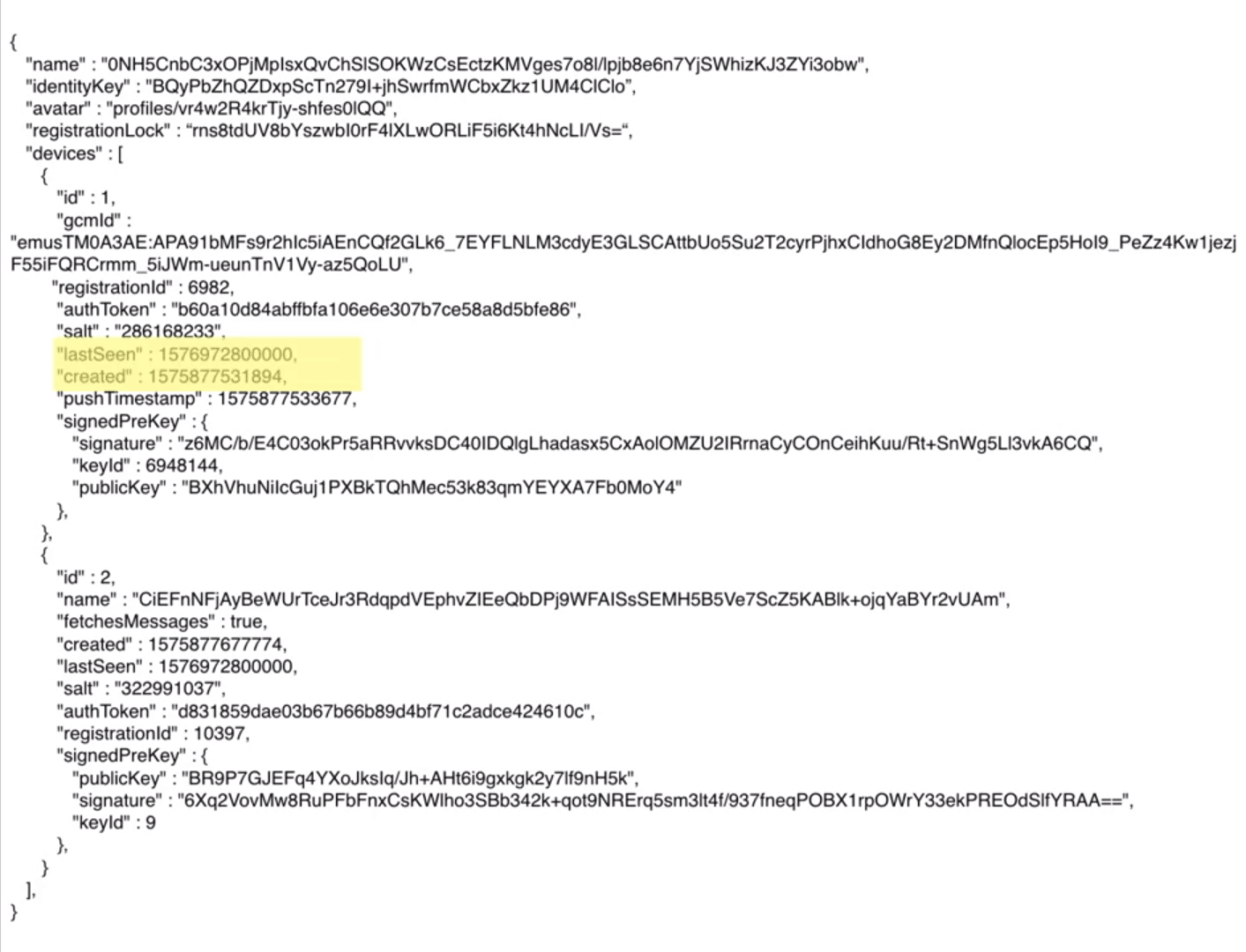
A screenshot from Moxie Marlinspike’s lecture at the Chaos Computer Club information security conference in December 2019, showing off his personal Signal account credentials.
“Because we built Signal to completely avoid storing any sensitive information, I can get on stage in front of thousands of people and publicly post all of my account details without revealing anything other than how long I’ve had Signal installed (since the last time I changed my phone) and the last date I used it (which is today, by the way),” says Moxie Marlinspike, a well-known hacker, crypto-anarchist, and the program’s main developer. The
main weakness of Signal and similar messengers is that they are tied to a specific phone number. For example, if an outsider joins a group, they will see the phone numbers of everyone in that group. This is a technique used by Hong Kong police to identify protesters on WhatsApp, Signal, and Telegram.
On the other hand, the attacker won’t get the rest of the account data, even with a subpoena.
“If you ask the CEO of any other major communications platform to publicly release their credentials from their platform, they won’t,” Moxie writes. “I don’t blame them — that’s a lot of data they’re not comfortable sharing with you — but it does raise the question of how comfortable they are sharing that same data with them [the authorities].”
Any American company is required to comply with American law and produce data in response to a subpoena, whether it’s WhatsApp or Signal. But in Signal’s case, it simply won’t have anything to show.
In some countries, after the WhatsApp leaks, even the military and politicians are being transferred to the mandatory use of crypto-messengers Signal and Wickr. For example, such rules have been established for the soldiers of the 82nd Airborne Division of the US Army and for the communication of members of the Conservative Party of Great Britain. So having Signal on your phone is not a sign of suspicious activity, but rather a sign of common sense.
The absence of personal data in the company's possession is the only strategy that allows you to ensure the security of this data, the creators of Signal are sure. Accordingly, trust in any company comes down not to trust in the safety of our personal data, but to trust in their engineering capabilities and know-how for developing software that will not allow the transfer of personal data from the user and guarantees that they are stored only by him and are not available to anyone else, including the company itself.
Signal is a 501 (c) (3) non-profit organization, so the software was and will remain free and open source. “Our mission is to improve privacy on the internet, so we publish our technology and share our knowledge to encourage other companies to use it in their own products and services,” writes Moxie Marlinspike. Today, some other messengers use the Signal protocol, although they have not implemented a strict no-personal-information policy and continue to store contacts, conversations, photos, and other data for each account on their servers. For example, WhatsApp also uses the secure Signal protocol, but it transmits the user’s social graph to its parent company Facebook. The same applies to commercial companies Telegram FZ LLC and Telegram Messenger Inc. In the case of Signal, only a truncated hash of each phone number in the contact list is transmitted to the server. Such a hash cannot be brute-forced directly, although we are not talking about complete secrecy.
Of course, there are more secure and reliable messengers with end-to-end encryption, without specifying a phone number and other identifiers. For example, the Matrix P2P direct encrypted messaging system with client software like Riot and other clients.
Riot client interface for the Matrix peer-to-peer crypto network But these programs are not very user-friendly yet. receipts
For example, to disable read in the Riot desktop client, you need to edit the /etc/riot/config.json configuration file .
Source
But now the developers of Signal are faced with a new threat. The US government is trying to compromise the messenger's security and again gain access to users' correspondence. In 2016, they managed to get a subpoena to seize the correspondence of one user, but due to end-to-end encryption, there was nothing to seize.
The only data Signal can provide to a government request or subpoena is the data it holds about a user. This includes:
- account creation date in Unix time;
- date of last use in Unix time.
And that’s it. No contacts, group information, or profile data.

The user profile that Signal provided under a subpoena. Screenshot from the court documents
“We designed Signal so that personal data is stored by customers, not us,” the developers write. “Signal uses end-to-end encryption, so we never have access to the content of the messages you send. They are visible only to you and the intended recipients. However, Signal also applies this design philosophy to the rest of your data.”
Unlike any other popular messenger, Signal does not have access to your contacts, social graph, group data, group status information, profile name, profile avatar, location data, search history, and so on. There are no trackers, ads, or analytics code in the program’s code. Absolutely all information is encrypted, except for the account creation date and the date of last use, as shown in the screenshot.

A screenshot from Moxie Marlinspike’s lecture at the Chaos Computer Club information security conference in December 2019, showing off his personal Signal account credentials.
“Because we built Signal to completely avoid storing any sensitive information, I can get on stage in front of thousands of people and publicly post all of my account details without revealing anything other than how long I’ve had Signal installed (since the last time I changed my phone) and the last date I used it (which is today, by the way),” says Moxie Marlinspike, a well-known hacker, crypto-anarchist, and the program’s main developer. The
main weakness of Signal and similar messengers is that they are tied to a specific phone number. For example, if an outsider joins a group, they will see the phone numbers of everyone in that group. This is a technique used by Hong Kong police to identify protesters on WhatsApp, Signal, and Telegram.
On the other hand, the attacker won’t get the rest of the account data, even with a subpoena.
“If you ask the CEO of any other major communications platform to publicly release their credentials from their platform, they won’t,” Moxie writes. “I don’t blame them — that’s a lot of data they’re not comfortable sharing with you — but it does raise the question of how comfortable they are sharing that same data with them [the authorities].”
Any American company is required to comply with American law and produce data in response to a subpoena, whether it’s WhatsApp or Signal. But in Signal’s case, it simply won’t have anything to show.
In some countries, after the WhatsApp leaks, even the military and politicians are being transferred to the mandatory use of crypto-messengers Signal and Wickr. For example, such rules have been established for the soldiers of the 82nd Airborne Division of the US Army and for the communication of members of the Conservative Party of Great Britain. So having Signal on your phone is not a sign of suspicious activity, but rather a sign of common sense.
The absence of personal data in the company's possession is the only strategy that allows you to ensure the security of this data, the creators of Signal are sure. Accordingly, trust in any company comes down not to trust in the safety of our personal data, but to trust in their engineering capabilities and know-how for developing software that will not allow the transfer of personal data from the user and guarantees that they are stored only by him and are not available to anyone else, including the company itself.
Signal is a 501 (c) (3) non-profit organization, so the software was and will remain free and open source. “Our mission is to improve privacy on the internet, so we publish our technology and share our knowledge to encourage other companies to use it in their own products and services,” writes Moxie Marlinspike. Today, some other messengers use the Signal protocol, although they have not implemented a strict no-personal-information policy and continue to store contacts, conversations, photos, and other data for each account on their servers. For example, WhatsApp also uses the secure Signal protocol, but it transmits the user’s social graph to its parent company Facebook. The same applies to commercial companies Telegram FZ LLC and Telegram Messenger Inc. In the case of Signal, only a truncated hash of each phone number in the contact list is transmitted to the server. Such a hash cannot be brute-forced directly, although we are not talking about complete secrecy.
Of course, there are more secure and reliable messengers with end-to-end encryption, without specifying a phone number and other identifiers. For example, the Matrix P2P direct encrypted messaging system with client software like Riot and other clients.

Riot client interface for the Matrix peer-to-peer crypto network But these programs are not very user-friendly yet. receipts
For example, to disable read in the Riot desktop client, you need to edit the /etc/riot/config.json configuration file .
Source
