Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Is Predator really what it claims to be?
Insikt has identified a new infrastructure allegedly used by commercial Predator spyware operators in at least 11 countries.
Analyzing the domains that could be used to distribute the program, experts found potential Predator customers in Angola, Armenia, Botswana, Egypt, Indonesia, Kazakhstan, Mongolia, Oman, the Philippines, Saudi Arabia, as well as in Trinidad and Tobago.
Predator is a sophisticated spyware developed by the Israeli Intellexa consortium, which has been used since 2019 to infect Android and iPhone-based devices. Predator lets you access your device's microphone, camera, and all stored or transmitted data, including contacts, messages, photos, and videos. The program leaves a minimum of traces on the target device, which makes it difficult to investigate.
During the analysis, the Insikt group discovered a new multi-level Predator delivery network, including:
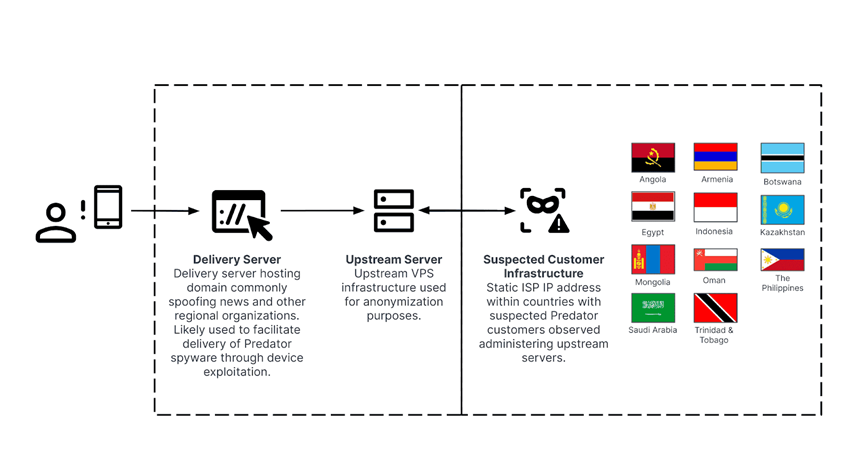
Multi-level architecture of the Predator delivery network
Not just for law enforcement agencies
Spyware technologies such as Predator and Pegasus are touted as tools designed to fight terrorism and be used by law enforcement agencies. However, they are constantly used for targeted attacks on civil society, including journalists, politicians and activists. For example, in 2021, the phone of an Egyptian opposition politician was infected with Predator in a campaign backed by the Egyptian government, according to Citizen Lab experts.
Predator clients typically target high-level individuals who may have significant intelligence value due to the high deployment costs and per-infection charges. The use of commercial spyware other than in the context of crime investigation and counterterrorism poses risks to the privacy, legal protection, or physical security of the final targets, their employers, and the entities involved in such activities.
Last year, the Cisco Talos and Citizen Lab research groups published a technical analysis of Predator and its Alien bootloader, as well as revealed details of how the spyware works. And even after a deep analysis of experts, the perfect spyware remained unknown.
Insikt has identified a new infrastructure allegedly used by commercial Predator spyware operators in at least 11 countries.
Analyzing the domains that could be used to distribute the program, experts found potential Predator customers in Angola, Armenia, Botswana, Egypt, Indonesia, Kazakhstan, Mongolia, Oman, the Philippines, Saudi Arabia, as well as in Trinidad and Tobago.
Predator is a sophisticated spyware developed by the Israeli Intellexa consortium, which has been used since 2019 to infect Android and iPhone-based devices. Predator lets you access your device's microphone, camera, and all stored or transmitted data, including contacts, messages, photos, and videos. The program leaves a minimum of traces on the target device, which makes it difficult to investigate.
During the analysis, the Insikt group discovered a new multi-level Predator delivery network, including:
- Server) servers (–the server that is used for initial infection of target devices. It usually hosts malicious content or vulnerability exploitation tools. These servers often host domains that spoof specific organizations ' websites, which may be of interest to the target. Some of the domains are disguised as legitimate news portals, weather forecast sites, or specific companies in order to trick the user into downloading spyware.;
- VPS servers (located above the delivery servers) are servers located between the delivery servers and the final spyware operators (in this case, Predator clients). They can be used to anonymize traffic, provide an additional layer of protection for operators, and complicate the process of tracking the source of an attack. VPS servers can manage data transferred between an infected device and operators, while hiding the real location and identity of operators;
- infrastructure supposedly associated with Predator clients. The upstream servers interacted with static addresses of Internet service providers within the country, which were probably associated with Predator clients.

Multi-level architecture of the Predator delivery network
Not just for law enforcement agencies
Spyware technologies such as Predator and Pegasus are touted as tools designed to fight terrorism and be used by law enforcement agencies. However, they are constantly used for targeted attacks on civil society, including journalists, politicians and activists. For example, in 2021, the phone of an Egyptian opposition politician was infected with Predator in a campaign backed by the Egyptian government, according to Citizen Lab experts.
Predator clients typically target high-level individuals who may have significant intelligence value due to the high deployment costs and per-infection charges. The use of commercial spyware other than in the context of crime investigation and counterterrorism poses risks to the privacy, legal protection, or physical security of the final targets, their employers, and the entities involved in such activities.
Last year, the Cisco Talos and Citizen Lab research groups published a technical analysis of Predator and its Alien bootloader, as well as revealed details of how the spyware works. And even after a deep analysis of experts, the perfect spyware remained unknown.

