Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,320
- Points
- 113
Cybercriminals have abandoned leak sites in favor of repeated direct threats.
Cybersecurity researchers have identified a new version of malware called HardBit, which includes new masking techniques to make analysis more difficult. According to experts from Cybereason, " unlike previous versions, HardBit 4.0 is protected by a password that must be entered directly during program execution, which significantly complicates malware analysis."
The HardBit group of the same name, which is behind the spread of this malware, was first discovered by Fortinet researchers in October 2022. She is financially motivated and usually uses double extortion techniques.
The main difference between this group and other cybercrime associations is that there is no site for data leakage. Instead, hackers threaten their victims with new attacks in order to get a ransom. The main communication channel used by hackers is the secure Tox messenger.
The exact method of initial penetration into the systems of HardBit victims is still unclear, but it is assumed that this may be a brute-force attack on RDP and SMB services. After gaining access, attackers steal credentials using tools such as Mimikatz and NLBrute, and also conduct network research using Advanced Port Scanner, which allows them to navigate through it via RDP.
As Varonis noted in its report last year, "once compromised, the HardBit malware performs a series of actions that reduce the host's security level before encrypting the victim's data." The encryption itself is performed using a Neshta file, which was previously used to distribute other types of malware.
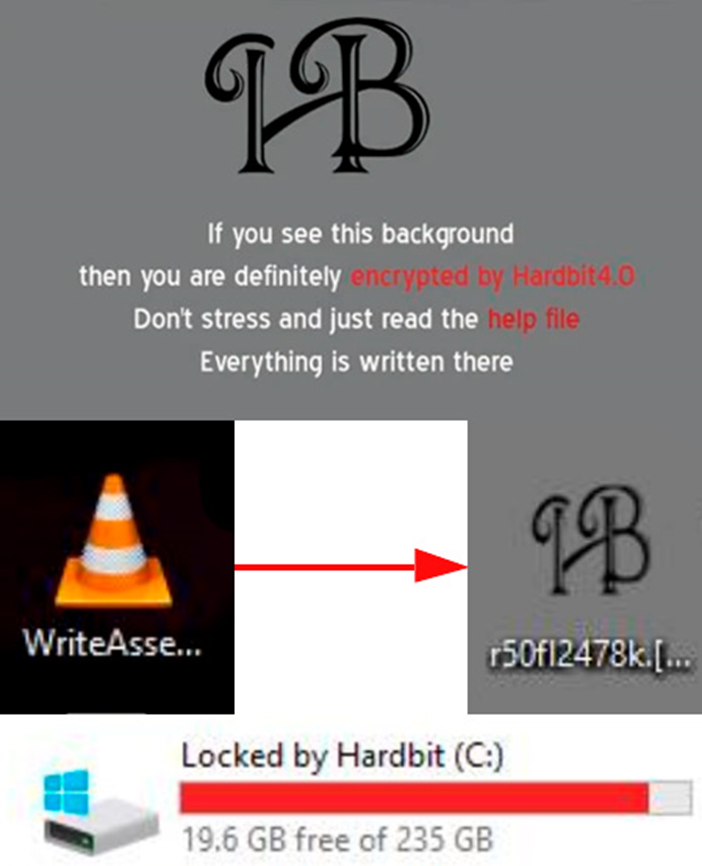
HardBit is also able to disable the Microsoft Defender antivirus built into Windows and terminate various system processes and services to avoid detection. After that, the program encrypts files, updates their icons, changes the desktop wallpaper and the system volume label to "Locked by HardBit".
Malware comes in two versions: with and without a graphical interface. For successful execution, the attacker must specify a special authorization ID. The graphical version, unlike the command-line version, supports viper mode, which allows the malware to permanently delete files and format disks.
Cybereason notes that "after entering the authorization ID, HardBit requests an encryption key to encrypt files on the target machines." Viper mode is activated separately at the request of operators who need to deploy a special configuration file.
Thus, the continuous complication of malware underscores the importance of a proactive approach to cybersecurity. Organizations should not only strengthen technical defenses, but also develop a culture of digital vigilance among employees in order to effectively counter constantly evolving threats.
Source
Cybersecurity researchers have identified a new version of malware called HardBit, which includes new masking techniques to make analysis more difficult. According to experts from Cybereason, " unlike previous versions, HardBit 4.0 is protected by a password that must be entered directly during program execution, which significantly complicates malware analysis."
The HardBit group of the same name, which is behind the spread of this malware, was first discovered by Fortinet researchers in October 2022. She is financially motivated and usually uses double extortion techniques.
The main difference between this group and other cybercrime associations is that there is no site for data leakage. Instead, hackers threaten their victims with new attacks in order to get a ransom. The main communication channel used by hackers is the secure Tox messenger.
The exact method of initial penetration into the systems of HardBit victims is still unclear, but it is assumed that this may be a brute-force attack on RDP and SMB services. After gaining access, attackers steal credentials using tools such as Mimikatz and NLBrute, and also conduct network research using Advanced Port Scanner, which allows them to navigate through it via RDP.
As Varonis noted in its report last year, "once compromised, the HardBit malware performs a series of actions that reduce the host's security level before encrypting the victim's data." The encryption itself is performed using a Neshta file, which was previously used to distribute other types of malware.
HardBit is also able to disable the Microsoft Defender antivirus built into Windows and terminate various system processes and services to avoid detection. After that, the program encrypts files, updates their icons, changes the desktop wallpaper and the system volume label to "Locked by HardBit".

Malware comes in two versions: with and without a graphical interface. For successful execution, the attacker must specify a special authorization ID. The graphical version, unlike the command-line version, supports viper mode, which allows the malware to permanently delete files and format disks.
Cybereason notes that "after entering the authorization ID, HardBit requests an encryption key to encrypt files on the target machines." Viper mode is activated separately at the request of operators who need to deploy a special configuration file.
Thus, the continuous complication of malware underscores the importance of a proactive approach to cybersecurity. Organizations should not only strengthen technical defenses, but also develop a culture of digital vigilance among employees in order to effectively counter constantly evolving threats.
Source

