CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 723
- Points
- 113

Shalom, running in the shadows! Hello, random carder. Today I will briefly tell you about the recently held annual contest for hackers. A normal topic. The guys and the dough made a mess, and quite so officially, and some even received job offers in cool companies with a lot of money.
Go:
At Positive Hack Days 8, the good old Leave ATM Alone ATM hacking contest was once again held. Participants had two ATMs at their disposal, and the hardware was provided by Bank, a banking security partner. Specifically for the competition, ATMs were set up and vulnerabilities were embedded in them. In 15 minutes, participants had to bypass security measures and withdraw money from their devices. The prize fund of the contest was $ 1000. About 40 participants came to bypass the protection. Leonid Krolle, the organizer of the contest and a specialist in the banking systems security research department at Positive Technologies, explained what it was like and analyzed the tasks in detail.

As mentioned above, the participants had two ATMs at their disposal. One of them has the applicationcontrol partner software installed, which prevents untrusted applications from running. It did not allow you to run any of the apps that are required for cash withdrawal (hello, Cutlet Maker, BubbleMaker and nemagiya!).
The second ATM was connected via the network to test processing, which allowed performing a cash withdrawal operation (which is available at the ATM). However, processing sent a signal to issue money from the cassette that did not contain any money. Therefore, the task of the participants was to substitute the processing response for issuing funds from the correct cassette.
The connection cables from the ATM and test processing were located outside, with the ability to connect to them using a network cord (LAN).
All the money withdrawn from the system was taken by the players themselves.

Application control
There are several ways to check whether an application matches the specified whitelist, from checking the path to the executable file or its hash to analyzing the digital signature and extension. Application control tools are most often used for additional protection of client computers (they prohibit the launch of software not from the white list) and ensure the security of isolated systems, such as ATMs, which do not imply constant operational intervention.
If the blacklist of extensions that should be blocked is more or less universal and easy to configure, then the whitelist of what is allowed to run is redundant by default — it often includes all applications from the operating system at the time of configuration.
Over the past few years, many methods have been described to bypass application control using Microsoft Windows tools (for example, "rundll32", "registr32"), which simply block the normal operation of the OS. Therefore, fine-tuning application control is a complex and painstaking work, the result of which was given to the contest participants to be torn to pieces. Note that in the real world, attackers don't have as much time to bypass application control.
The first day
The beginning of the first day of the contest was marked by a dense stream of forum participants who came to try their hand at bypassing application control and replacing the processing response — in total, more than 40 people came.

In total, it took 15 minutes to bypass protection on an ATM with application control: during this time, you had to run your own code. Unfortunately, on the first day, all attempts by participants to launch their exploit failed. However, one participant managed to detect a strange device installed on the ATM. It was a skimmer, a miniature portable reader that can be attached to an ATM. Such devices help fraudsters steal bank card data: banking details, PIN codes — all information recorded on a magnetic stripe.
After detecting the skimmer, it was necessary to extract card data from it: during the preparation of the contest, the organizers recorded a dump of a non-existent card with a certain number.

We will tell you a little about the preparation of the skimmer for the competition. The skimmer consists of a magnetic head for reading and a device for recording audio tracks (sometimes with Wi-Fi or Bluetooth).
This instance can be made on the basis of an Explay player-recorder or a similar USB voice recorder. Examples can be found here. In terms of size, such devices just fit into the cover on the anti-skimmer and there is still room for the battery, since it was necessary to prepare and revive the mini Frankenstein: the performance test was conducted on a similar device from another ATM model. To save space, the mounting area of the USB port is cut off, so the necessary adapter had to be made independently.

Experts tested the correct activation of the skimmer player according to the instructions from the player from the Internet (there were no symbols on the buttons, as they remained on the case) and recorded the map and number that participants needed to extract from the skimmer.

The information on the magnetic stripe of the card was recorded using F/2F frequency coding and represented alphanumeric characters in 7-bit encoding or numeric characters in 5-bit encoding. Parity and longitudinal redundancy control (or longitudinal redundant control — LRC) were used to determine read errors.
Data on any track must start with the start service symbol and end with the end service symbol. These characters are selected in such a way that they allow you to determine the beginning of a block of useful information, determine the reading direction of the card, and even the encoding format of the information (5 bits or 7 bits).
Control characters are intended for controlling hardware and cannot be used to transmit information (data content). Delimiters are used to separate data fields on the map.
In 7-bit encoding, characters [\]are reserved for additional national characters and should not be used in the framework of international information exchange. The symbol #is reserved for any additional graphic characters.
Here's an example of what it might look like:
;XXXXXXXXXXXXXXXX=YYYYYYYYYYYYYYYYY?Z
This is a standard ISO 2 track (37 characters). X...X — card number, Z— LRC. Data starts with the start symbol and ends with the end symbol. The card number is 16-digit.
In fact, it was possible to copy data from the player as an MP3 file, find where the track was recorded, enlarge it in the audio editor, and parse it bit by bit, but there are simpler ways, for example:
- SWipe-an application for reading the magnetic stripe of cards through the audio port;
- Magnetic Stripe Decoder — a program for decoding magnetic stripes by extracting " raw " data from a magnetic stripe using a sound card.
After about an hour, the map data recorded in the skimmer was provided. The well-deserved Audience Award has found its owner. Congratulations to Maxim Vikhlyantsev!
Other participants continued to compete for the main prizes uploaded to ATMs
Second day

On the second day of the contest, all the same participants could be observed at the ATM hacking sites. Perseverance and perseverance in trying to find a vector to bypass the protection did not remain in vain, and now Stanislav Povolotsky successfully bypassed the protection and, by executing an unsigned code, won a cash prize that was in the first ATM.

The essence of the network attack on the second ATM was as follows:the ATM had a laptop with installed software that emulates processing.
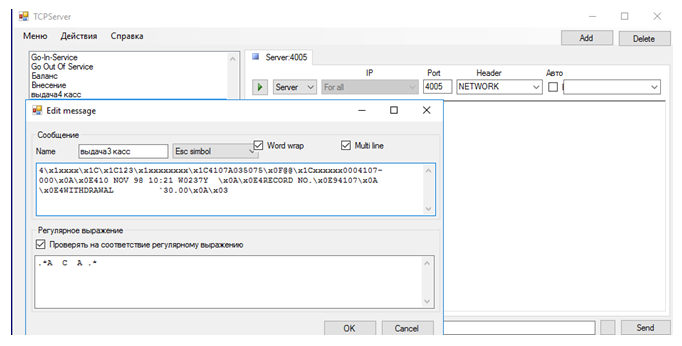
The emulator was configured to issue money with any inserted card, without a PIN code, but the tape that the emulator sent in response to the request was empty. To solve this problem, it was necessary to:
- intercept the processing emulator's response packet;
- disassemble the package and create your own-only with the correct set number of the cassette.;
- insert the card and respond to the ATM with the changed data when sending a request for processing;
- use the tcpdump, wireshark, scapy, or ettercap tools to perform a replay or spoofing attack with modified data in order to respond to the ATM.
WWW
- tcpdump is a UNIX utility that has a clone for Windows and allows you to intercept and analyze network traffic passing through the computer running this program.
- wireshark is a similar utility, only more "charged", with a GUI.
- scapy is an interactive shell and software library for manipulating network packets in the Python programming language.
- ettercap is a utility for analyzing network traffic passing through the computer interface, but with additional functionality. The program allows you to perform man-in-the-middle attacks to force another computer to transmit packets not to the router, but to the attacker.
If you don't believe me, here's a fact check - the full list of winners can be found on the official page of the contest.
In general, gentlemen, we are happy for the guys, continue to read the channel, make some features that I periodically tell you about here-and start making money on the sly.
xakep.ru

