Hello to everyone, dear friends!
It is possible that for many of you the title of the article is not clear. Don't worry, we'll figure it out now!
What it is?
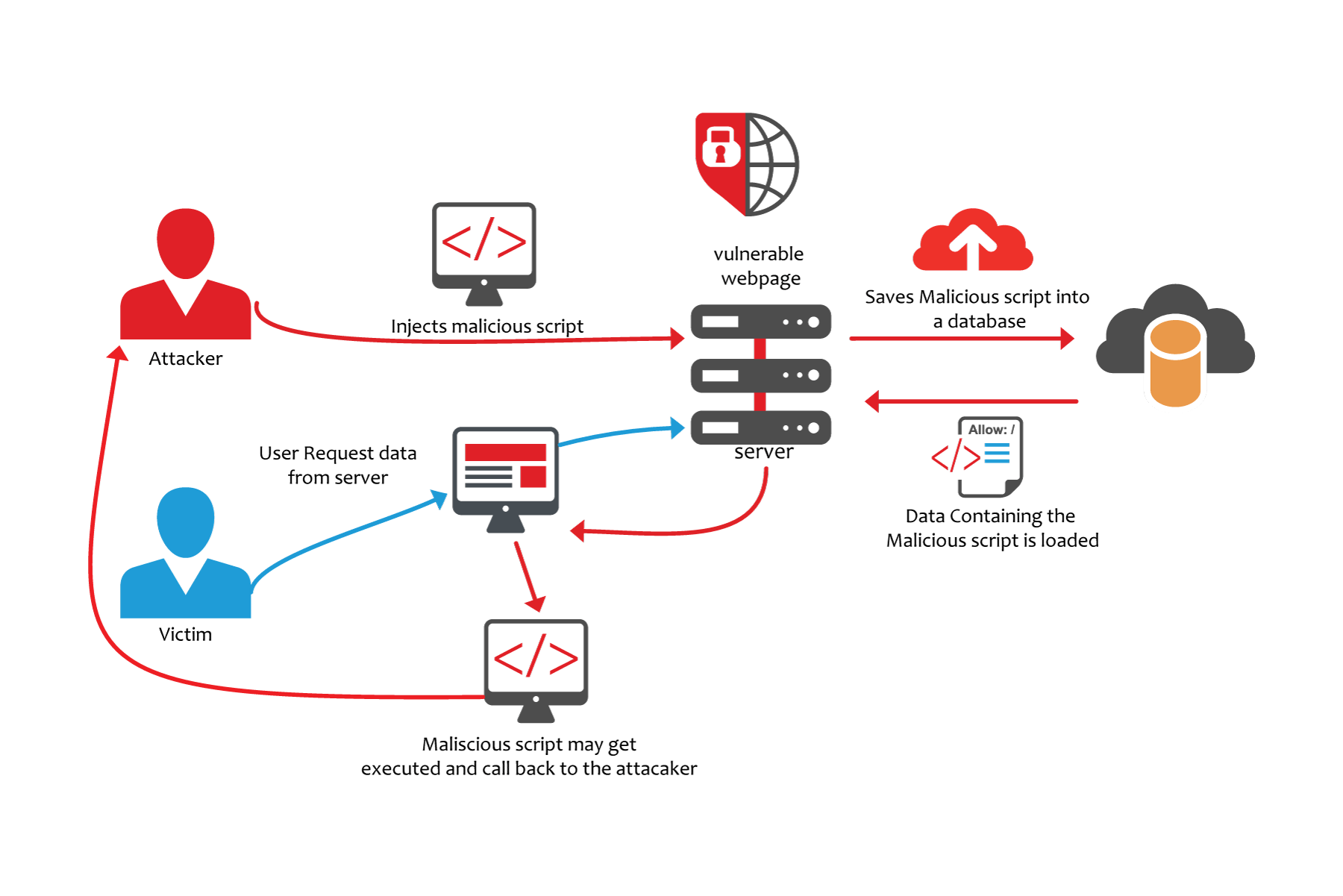
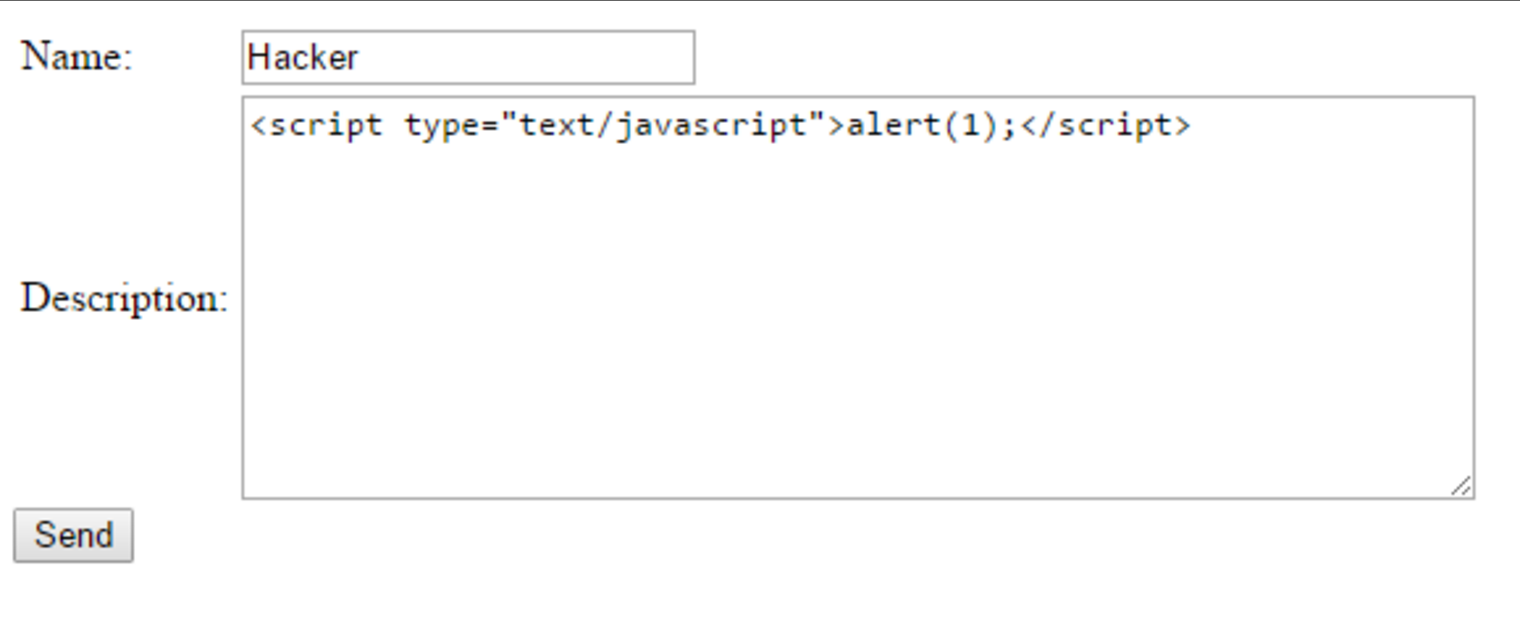
XSS attack or cross-site scripting is the injection of malicious code into the system server and exploitation of the vulnerability in order to obtain personal data.
In total, there are two types of attacks that I have met in practice:
The essence of scripting is that the embedded code uses the user's authorization on the website and receives all his personal data.
For a long time, programmers considered XSS to be harmless, not dangerous for servers. Protection was not given much attention. But in vain, now this is one of the most dangerous methods of hacking.
I will also mention stealing cookies, this method is often used by hackers, so it would be unfair to leave it unattended.
Cookies are a small piece of data that a web server sends to a user's PC. Each time a website page is opened, an HTML request is sent to the web server.
Many people believe that Cookies are special programs. But this is not the case. These are ordinary text files with a set of characters, symbols and tags.
I will tell you about the types of cookies that I use myself:
What vulnerabilities would I recommend using?
It is unlikely that a clear classification can be distinguished here, but we will divide them into two types:
- Reflected (Impermanent). I would say this is the most common type in use today. You can find them in the parameters of the request or HTML form.
- Stored (Persistent). Such vulnerabilities are used for the most destructive attacks. This requires injecting malicious code into the server. Each time entering the browser, the user will return to the original page.
Of course, if possible, it is better to use stored.
How to apply?
How can we use this information in practice? I will share with you my personal experience.
XSS vulnerabilities.
At the XSS attack is the kernel - it is such a loophole in the filter, which is a must to discover. There are several of them:
- Worms;
- Various web filters;
- Encryption;
- Tags;
- Brackets - open and closed. By type: “/?, #” >>>> << script {()});
- Filtering symbols and signs.
Cookie theft
How do you get someone else's information? Use interception! This is the most common use case for the vulnerability.
What do cookies contain?
Users should be wary of such things. After all, stealing data is not a very pleasant thing. There are special programs for minimal protection that anyone can download and install. But in reality, of course, few people think about online security.
Cookies are used to store data for the user, as well as:
How can they help?
Crackers use cross-site scripting and cookie theft to gain valuable insights.
What exactly does the exploitation of web vulnerabilities give us?
Cookies are very important, they are used for identification on the site. You can use your data if you know the cookie. It's easy to read them. You need to execute Javascript on the owner's pc. Javascript can go to any http server and load the image from there. In a request to upload an image, the text is transmitted. So cookies can be in this request and pass into the hands of an attacker. But for this you have to find a hosting with php.
By the way, if you are going to search for XSS vulnerabilities, do it in the Internet Explorer, this standard browser is best suited.
I hope this article helped you in choosing a way to hack a private page. All the information presented is not just theory. It has been tested in my practice more than once in the course of work.
Thank you for reading to the end, dear friend!
It is possible that for many of you the title of the article is not clear. Don't worry, we'll figure it out now!
What it is?
XSS attack or cross-site scripting is the injection of malicious code into the system server and exploitation of the vulnerability in order to obtain personal data.
In total, there are two types of attacks that I have met in practice:
- Passive - the participation of the user is required. It must be forced to follow the malicious link in order to initiate the code injection process. It is not easy to do such a thing, it requires knowledge in programming and psychological preparation.
- Active - you will need vulnerabilities from web resource filters. Using various combinations of symbols and tags, you need to create a request that the site will understand and execute.
The essence of scripting is that the embedded code uses the user's authorization on the website and receives all his personal data.
For a long time, programmers considered XSS to be harmless, not dangerous for servers. Protection was not given much attention. But in vain, now this is one of the most dangerous methods of hacking.
I will also mention stealing cookies, this method is often used by hackers, so it would be unfair to leave it unattended.
Cookies are a small piece of data that a web server sends to a user's PC. Each time a website page is opened, an HTML request is sent to the web server.
Many people believe that Cookies are special programs. But this is not the case. These are ordinary text files with a set of characters, symbols and tags.
I will tell you about the types of cookies that I use myself:
- First, I apply it during the current session. They are deleted at the end of the specified time period.
- Second, these files remain forever, they are not deleted. Stored on your hard drive. Under the guise of an ordinary user, hackers use them to decrypt.
What vulnerabilities would I recommend using?
It is unlikely that a clear classification can be distinguished here, but we will divide them into two types:
- Reflected (Impermanent). I would say this is the most common type in use today. You can find them in the parameters of the request or HTML form.
- Stored (Persistent). Such vulnerabilities are used for the most destructive attacks. This requires injecting malicious code into the server. Each time entering the browser, the user will return to the original page.
Of course, if possible, it is better to use stored.
How to apply?
How can we use this information in practice? I will share with you my personal experience.
XSS vulnerabilities.
At the XSS attack is the kernel - it is such a loophole in the filter, which is a must to discover. There are several of them:
- Worms;
- Various web filters;
- Encryption;
- Tags;
- Brackets - open and closed. By type: “/?, #” >>>> << script {()});
- Filtering symbols and signs.
Cookie theft
How do you get someone else's information? Use interception! This is the most common use case for the vulnerability.
What do cookies contain?
- Login: Password;
- Valuable contact information;
- Virus for active session seizure.
Users should be wary of such things. After all, stealing data is not a very pleasant thing. There are special programs for minimal protection that anyone can download and install. But in reality, of course, few people think about online security.
Cookies are used to store data for the user, as well as:
- Site authentication;
- Saving settings and personal data;
- Creation of user statistics and accounting;
- Monitoring the states of access sessions.
How can they help?
Crackers use cross-site scripting and cookie theft to gain valuable insights.
What exactly does the exploitation of web vulnerabilities give us?
- Access to any account on a social network, messenger or dating site;
- Account login data - login and password;
- The ability to make changes to the appearance of the page;
- Access to the clipboard.
Cookies are very important, they are used for identification on the site. You can use your data if you know the cookie. It's easy to read them. You need to execute Javascript on the owner's pc. Javascript can go to any http server and load the image from there. In a request to upload an image, the text is transmitted. So cookies can be in this request and pass into the hands of an attacker. But for this you have to find a hosting with php.
By the way, if you are going to search for XSS vulnerabilities, do it in the Internet Explorer, this standard browser is best suited.
I hope this article helped you in choosing a way to hack a private page. All the information presented is not just theory. It has been tested in my practice more than once in the course of work.
Thank you for reading to the end, dear friend!