Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,095
- Points
- 113
Bi.Zone analysts noted that since the beginning of 2024, commercial malware, whose developers prohibit its use against organizations in the CIS countries, has been increasingly used to attack Russian companies. However, attackers disable regional restrictions and "pirated" versions of malware are distributed on hack forums and in Telegram.
According to experts, in 73% of cases, commercial malware is used by financially motivated attackers who seek to collect ransom from their victims or resell stolen data on the darknet. Much less often (in 14% of cases), such malware is used for espionage purposes, and hacktivists account for only 3% of such attacks.
At the same time, about 5% of activity clusters attacking companies from Russia and the CIS countries violate the instructions of commercial malware developers, who prohibit the use of their software to attack organizations in this region. Such bans are often related to the fact that the malware developers themselves are located in the CIS and expect that it will be more difficult to identify them and bring them to justice if their software is not used against local companies.
The trend of violating bans and “refining” malware emerged in 2023 and intensified at the beginning of this year. Researchers note that this is well illustrated by the activity of the recently discovered Stone Wolf group.
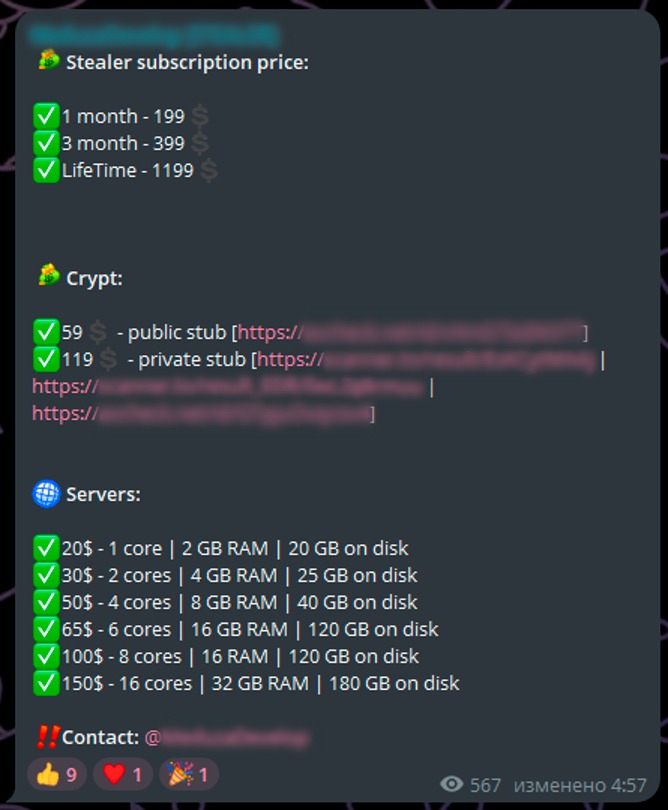
The Meduza stealer went on sale in June 2023 at a price of $199 per month of use, $399 for three months, or $1,199 for a perpetual license. Since March 2024, additional options have been available to buyers: for example, for a price starting at $20, you can rent a dedicated server with a choice of parameters for the number of cores, RAM, and disk space.
Researchers write that, as a rule, when it becomes known that a particular malware is being used against companies in the CIS countries, its sales are blocked on hack forums, and the developers transfer their activities to Telegram.
For example, in August 2023, experts published a report on the White Snake stealer. At that time, the attackers distributed the malware under the guise of Roskomnadzor requirements, attacking Russian companies, despite the ban on the developers. Soon after the publication of the study, the topic of selling White Snake on a popular shadow forum was closed, and the only platform for distributing the stealer was the developer's Telegram channel. Currently, the malware can be purchased at a price ranging from $200 (a month of use) to $1,950 (a perpetual license).
A similar situation developed with the Rhadamantys stealer, the prices for which ranged from $59 for a week of use to $999 for a perpetual license. Sales of the stealer were blocked on hack forums in April 2024, after it was discovered that the Sticky Werewolf group was using the stealer to attack Russian and Belarusian organizations.
Source
According to experts, in 73% of cases, commercial malware is used by financially motivated attackers who seek to collect ransom from their victims or resell stolen data on the darknet. Much less often (in 14% of cases), such malware is used for espionage purposes, and hacktivists account for only 3% of such attacks.
At the same time, about 5% of activity clusters attacking companies from Russia and the CIS countries violate the instructions of commercial malware developers, who prohibit the use of their software to attack organizations in this region. Such bans are often related to the fact that the malware developers themselves are located in the CIS and expect that it will be more difficult to identify them and bring them to justice if their software is not used against local companies.
The trend of violating bans and “refining” malware emerged in 2023 and intensified at the beginning of this year. Researchers note that this is well illustrated by the activity of the recently discovered Stone Wolf group.
"The Stone Wolf group carried out at least 9 attacks on Russian companies using the Meduza stealer. According to the developers, it has a built-in module that restricts attacks on the territory of the CIS. However, Stone Wolf modified the software, disabling the ban function. The criminals sent the stealer modified in this way as attachments to phishing emails on behalf of a real company that works in the field of industrial automation," comments Oleg Skulkin, head of BI.ZONE Threat Intelligence.
The Meduza stealer went on sale in June 2023 at a price of $199 per month of use, $399 for three months, or $1,199 for a perpetual license. Since March 2024, additional options have been available to buyers: for example, for a price starting at $20, you can rent a dedicated server with a choice of parameters for the number of cores, RAM, and disk space.

Researchers write that, as a rule, when it becomes known that a particular malware is being used against companies in the CIS countries, its sales are blocked on hack forums, and the developers transfer their activities to Telegram.
For example, in August 2023, experts published a report on the White Snake stealer. At that time, the attackers distributed the malware under the guise of Roskomnadzor requirements, attacking Russian companies, despite the ban on the developers. Soon after the publication of the study, the topic of selling White Snake on a popular shadow forum was closed, and the only platform for distributing the stealer was the developer's Telegram channel. Currently, the malware can be purchased at a price ranging from $200 (a month of use) to $1,950 (a perpetual license).
A similar situation developed with the Rhadamantys stealer, the prices for which ranged from $59 for a week of use to $999 for a perpetual license. Sales of the stealer were blocked on hack forums in April 2024, after it was discovered that the Sticky Werewolf group was using the stealer to attack Russian and Belarusian organizations.
Source

