CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 728
- Points
- 113
In the right hands Booking.com it became a tool for hacking into the systems of hotels and travelers computers.
Perception Point security researchers have discovered a multi-stage information theft campaign in which hackers break into the systems of hotels, booking sites, and travel agencies, and then use the access to obtain travelers ' financial data.
According to the Perception Point report, the chain of infections starts with a simple request for a reservation or mention of an existing reservation. After establishing a connection with the hotel, criminals provide a reason, such as a health condition or a special traveler's wish, to send important documents to the URL. When a hotel manager clicks the URL, malware is downloaded to the company's system, which surreptitiously collects confidential information such as credentials and financial information.
However, Akamai experts said that the attack goes beyond the described step and is aimed at customers of the compromised organization. According to Akamai, after activating the malware in the hotel's system, an attacker can gain access to correspondence with real customers. With a direct and trusted channel of communication with the final victim, a cybercriminal can send their phishing message on behalf of a compromised hotel or travel agency.
At the same time, the message is "written professionally and based on real interactions of the hotel with guests", which eliminates any suspicion. In addition, communication takes place through the official channel of the booking site, so the target has no reason to doubt the authenticity of the message.
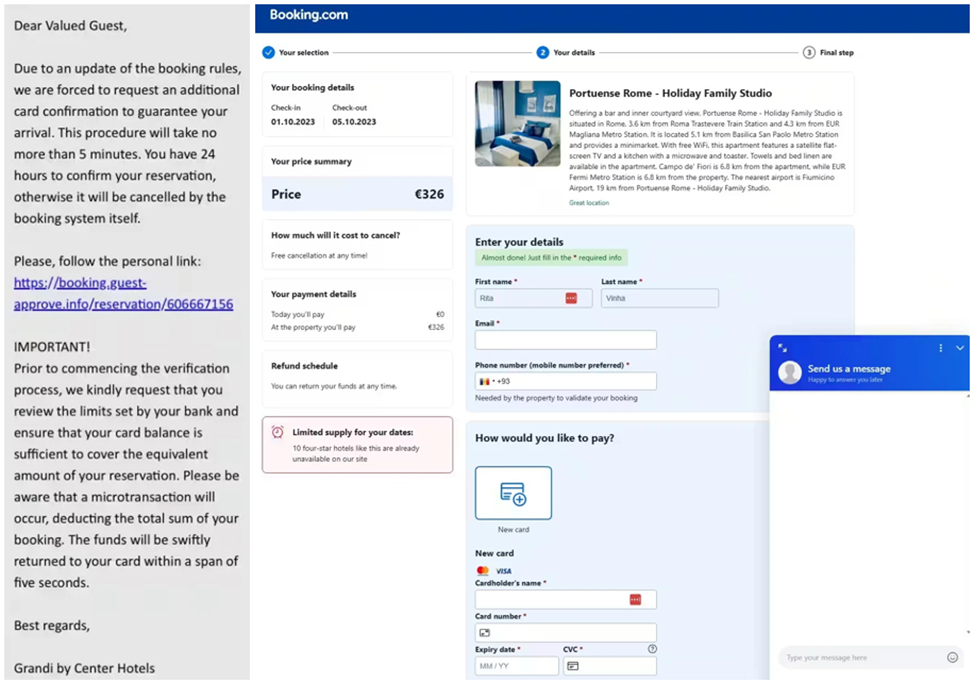
Phishing message (left) and fake payment pageBooking.com(on the right)
The victim receives a link to the page for checking the card. The link activates an executable file encoded (base64) in complex JavaScript code on the victim's computer. The attacker also included a variety of security checks and anti-analysis techniques to make sure that only the potential victim progresses to the next stage of fraud, in which the victim is shown a fake payment page. Booking.com. On this page, the victim enters their payment details, and they fall into the hands of cybercriminals.
Despite the sophisticated approach that makes cheating very difficult to detect, Akamai experts say that the usual signs can still reveal fraud. Users should avoid clicking on unwanted links, even if they look legitimate, be skeptical of messages that require immediate action, and check URLs for signs of phishing. To avoid falling victim to more sophisticated phishing campaigns, we recommend that you contact the company directly at the official email address or phone number and ask for clarification about the message.
Perception Point security researchers have discovered a multi-stage information theft campaign in which hackers break into the systems of hotels, booking sites, and travel agencies, and then use the access to obtain travelers ' financial data.
According to the Perception Point report, the chain of infections starts with a simple request for a reservation or mention of an existing reservation. After establishing a connection with the hotel, criminals provide a reason, such as a health condition or a special traveler's wish, to send important documents to the URL. When a hotel manager clicks the URL, malware is downloaded to the company's system, which surreptitiously collects confidential information such as credentials and financial information.
However, Akamai experts said that the attack goes beyond the described step and is aimed at customers of the compromised organization. According to Akamai, after activating the malware in the hotel's system, an attacker can gain access to correspondence with real customers. With a direct and trusted channel of communication with the final victim, a cybercriminal can send their phishing message on behalf of a compromised hotel or travel agency.
At the same time, the message is "written professionally and based on real interactions of the hotel with guests", which eliminates any suspicion. In addition, communication takes place through the official channel of the booking site, so the target has no reason to doubt the authenticity of the message.

Phishing message (left) and fake payment pageBooking.com(on the right)
The victim receives a link to the page for checking the card. The link activates an executable file encoded (base64) in complex JavaScript code on the victim's computer. The attacker also included a variety of security checks and anti-analysis techniques to make sure that only the potential victim progresses to the next stage of fraud, in which the victim is shown a fake payment page. Booking.com. On this page, the victim enters their payment details, and they fall into the hands of cybercriminals.
Despite the sophisticated approach that makes cheating very difficult to detect, Akamai experts say that the usual signs can still reveal fraud. Users should avoid clicking on unwanted links, even if they look legitimate, be skeptical of messages that require immediate action, and check URLs for signs of phishing. To avoid falling victim to more sophisticated phishing campaigns, we recommend that you contact the company directly at the official email address or phone number and ask for clarification about the message.
