Man
Professional
- Messages
- 3,222
- Reaction score
- 1,199
- Points
- 113
AI is becoming a tool for hackers to steal tourist data.
Cyber fraudsters have found a new way to make money on tourists using the popular Booking.com booking service. Recently, in California, hackers hacked into the account of one of the hotels, which allowed them to launch a phishing attack. The victim was a customer who had just booked a room and received a message through the Booking.com app asking them to confirm their details, ostensibly to complete the reservation. The message looked convincing, as it contained the name of the hotel and information about its reservation.
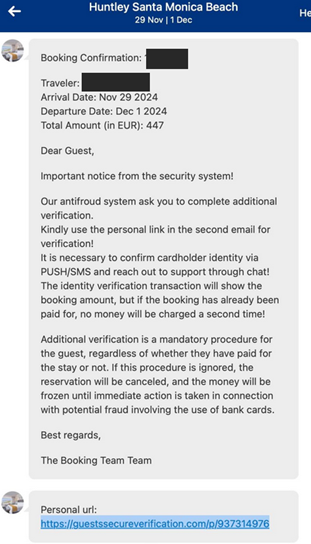
Phishing Message (KrebsOnSecurity)
The company Booking.com confirmed the incident, specifying that the attackers gained access to the data due to the hacking of the system of one of the partners. There were no Booking.com leaks in the system itself. After the incident, Booking.com strengthened security measures and introduced mandatory two-factor authentication (2FA) for all partners. Now, to access payment details, you need to enter a one-time code from the mobile authentication application. However, criminals find ways to bypass the protection by infecting partner computers with malware to gain access to accounts and send phishing messages to customers.
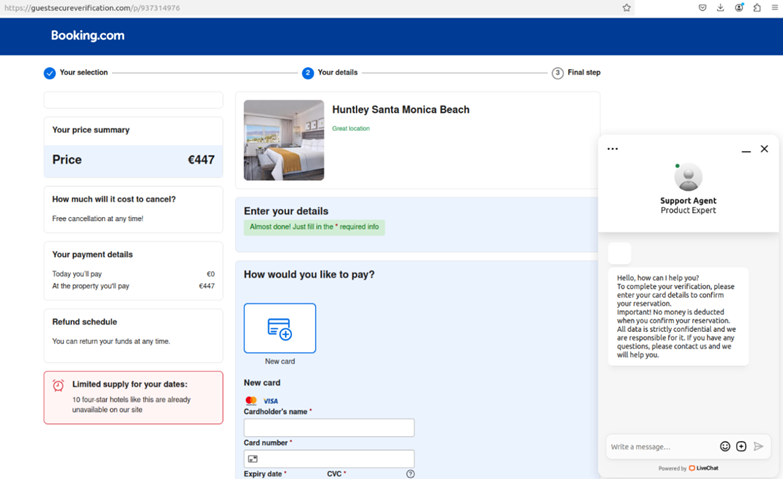
Phishing site that opens when you click on a link in a text message (KrebsOnSecurity)
Analysis of social networks showed that such schemes are common not only among hotels, but also on other popular platforms. In 2023, SecureWorks recorded an increase in malware attacks aimed at stealing data from Booking.com partners. According to SecureWorks, the attacks began in March 2023 when one of the hotels did not enable multi-factor authentication, making it easier for cybercriminals to access the account.
In June 2024, the Booking.com service reported a 900% increase in phishing attacks, which is attributed to the use of artificial intelligence to create more effective deception schemes. In response, the company implemented its own AI solutions that blocked 85 million fraudulent bookings and prevented more than 1.5 million phishing attempts in 2023.
Additional investigation revealed that the domain of the fake site sent to the client was guestssecureverification[.]com — registered to an email address that was used to create more than 700 phishing domains targeting hotel services and other popular platforms such as Shopify and Steam.
The demand for compromised Booking.com accounts remains high among cybercriminals. Hacker forums actively offer stolen data, as well as monetization services for compromised accounts. Some attackers even create "their own travel agencies", providing fraudsters with discounts on hotel bookings.
SecureWorks has identified phishers using malware to steal credentials, but today criminals only need to purchase stolen credentials on the black market, especially if the services do not require 2FA. This is confirmed by the case of the Snowflake cloud platform, where vulnerable accounts were used to steal the data of more than 160 companies.
Source
Cyber fraudsters have found a new way to make money on tourists using the popular Booking.com booking service. Recently, in California, hackers hacked into the account of one of the hotels, which allowed them to launch a phishing attack. The victim was a customer who had just booked a room and received a message through the Booking.com app asking them to confirm their details, ostensibly to complete the reservation. The message looked convincing, as it contained the name of the hotel and information about its reservation.

Phishing Message (KrebsOnSecurity)
The company Booking.com confirmed the incident, specifying that the attackers gained access to the data due to the hacking of the system of one of the partners. There were no Booking.com leaks in the system itself. After the incident, Booking.com strengthened security measures and introduced mandatory two-factor authentication (2FA) for all partners. Now, to access payment details, you need to enter a one-time code from the mobile authentication application. However, criminals find ways to bypass the protection by infecting partner computers with malware to gain access to accounts and send phishing messages to customers.

Phishing site that opens when you click on a link in a text message (KrebsOnSecurity)
Analysis of social networks showed that such schemes are common not only among hotels, but also on other popular platforms. In 2023, SecureWorks recorded an increase in malware attacks aimed at stealing data from Booking.com partners. According to SecureWorks, the attacks began in March 2023 when one of the hotels did not enable multi-factor authentication, making it easier for cybercriminals to access the account.
In June 2024, the Booking.com service reported a 900% increase in phishing attacks, which is attributed to the use of artificial intelligence to create more effective deception schemes. In response, the company implemented its own AI solutions that blocked 85 million fraudulent bookings and prevented more than 1.5 million phishing attempts in 2023.
Additional investigation revealed that the domain of the fake site sent to the client was guestssecureverification[.]com — registered to an email address that was used to create more than 700 phishing domains targeting hotel services and other popular platforms such as Shopify and Steam.
The demand for compromised Booking.com accounts remains high among cybercriminals. Hacker forums actively offer stolen data, as well as monetization services for compromised accounts. Some attackers even create "their own travel agencies", providing fraudsters with discounts on hotel bookings.
SecureWorks has identified phishers using malware to steal credentials, but today criminals only need to purchase stolen credentials on the black market, especially if the services do not require 2FA. This is confirmed by the case of the Snowflake cloud platform, where vulnerable accounts were used to steal the data of more than 160 companies.
Source

