Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,087
- Points
- 113
The use of OCR made it possible to automate the process of collecting confidential data.
Researchers from McAfee have discovered more than 280 malicious Android apps that use optical character recognition (OCR) technology to steal cryptocurrency data. Collectively known as SpyAgent, these apps are cleverly disguised as official services from banks, government services, and popular platforms such as streaming services and utility bill management apps.
Attackers, distributing applications through phishing SMS messages and malicious sites, actively collect data from infected devices, including contacts, text messages and images stored in the phone's memory. It is noteworthy that all the identified applications have never been distributed through Google Play.
The main feature of this campaign was the use of OCR to extract cryptocurrency wallets, the data of which is often stored in the form of simple screenshots. Many wallets are protected with mnemonic phrases, a random set of words that are easier to remember than complex private keys. Attackers convert these phrases into text using OCR.
Researcher SangRyol Ryu, who works at McAfee and actually discovered the SpyAgent campaign, was able to gain access to the servers where the stolen data was sent. This was achieved thanks to errors in the malware's security settings. Among the stolen information were images of wallets and related mnemonic phrases, indicating a targeted attack on users' cryptocurrency assets.
To process the stolen data, the attackers use Python and Javascript technologies. Images with victims' devices go through a character recognition process, after which the text is structured and managed through an administrative panel. This demonstrates the high level of professionalism of the hackers.
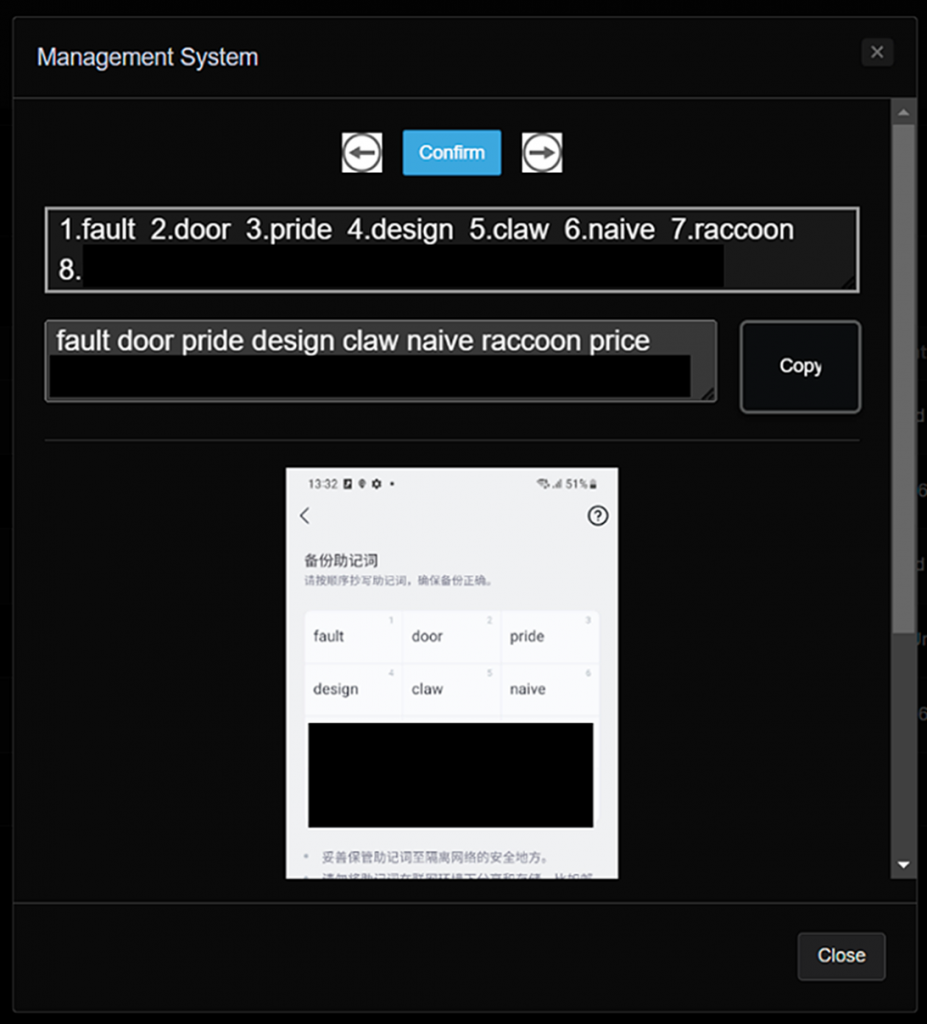
The apps were updated regularly to better mask their malicious activity. In the latest version, they started using WebSockets to communicate with the command and control servers, which made it difficult for antivirus programs to detect them. Attackers also use methods to obfuscate the code, which makes it more difficult to analyze it.
While the majority of SpyAgent-infected apps are currently concentrated in South Korea, there are signs that the campaign has expanded to the UK. This indicates that attackers are seeking to expand the geography of attacks by adapting applications for different regions and users.
It is noteworthy that this malicious campaign was identified shortly after the discovery of a similar Trojan - CraxsRAT, which attacked users of banking services in Malaysia. CraxsRAT has also been previously identified in Singapore, where it has been used for remote device management, data theft, and unauthorized withdrawals.
Source
Researchers from McAfee have discovered more than 280 malicious Android apps that use optical character recognition (OCR) technology to steal cryptocurrency data. Collectively known as SpyAgent, these apps are cleverly disguised as official services from banks, government services, and popular platforms such as streaming services and utility bill management apps.
Attackers, distributing applications through phishing SMS messages and malicious sites, actively collect data from infected devices, including contacts, text messages and images stored in the phone's memory. It is noteworthy that all the identified applications have never been distributed through Google Play.
The main feature of this campaign was the use of OCR to extract cryptocurrency wallets, the data of which is often stored in the form of simple screenshots. Many wallets are protected with mnemonic phrases, a random set of words that are easier to remember than complex private keys. Attackers convert these phrases into text using OCR.
Researcher SangRyol Ryu, who works at McAfee and actually discovered the SpyAgent campaign, was able to gain access to the servers where the stolen data was sent. This was achieved thanks to errors in the malware's security settings. Among the stolen information were images of wallets and related mnemonic phrases, indicating a targeted attack on users' cryptocurrency assets.
To process the stolen data, the attackers use Python and Javascript technologies. Images with victims' devices go through a character recognition process, after which the text is structured and managed through an administrative panel. This demonstrates the high level of professionalism of the hackers.

The apps were updated regularly to better mask their malicious activity. In the latest version, they started using WebSockets to communicate with the command and control servers, which made it difficult for antivirus programs to detect them. Attackers also use methods to obfuscate the code, which makes it more difficult to analyze it.
While the majority of SpyAgent-infected apps are currently concentrated in South Korea, there are signs that the campaign has expanded to the UK. This indicates that attackers are seeking to expand the geography of attacks by adapting applications for different regions and users.
It is noteworthy that this malicious campaign was identified shortly after the discovery of a similar Trojan - CraxsRAT, which attacked users of banking services in Malaysia. CraxsRAT has also been previously identified in Singapore, where it has been used for remote device management, data theft, and unauthorized withdrawals.
Source

