Carding Forum
Professional
The eliminated vulnerability became a channel for penetration into systems.
Cybercriminals report that hackers have found a way to bypass Microsoft's SmartScreen protection to spread malware to users ' devices. A vulnerability in SmartScreen allows you to enter the system through Windows Defender and infect devices.
In January 2024, the DarkGate group exploited the vulnerability CVE-2024-21412 (CVSS score: 8.1) to deliver malicious installers that mimic popular applications such as iTunes, Notion, and NVIDIA. Microsoft fixed the vulnerability in February, but another group, Water Hydra, continued to use the flaw to distribute malware, including the DarkMe Trojan.
The initial infection begins with an email from a supposedly reliable source. The message is designed to encourage the recipient to click on a link that tricks the user into viewing a URL hosted on a remote WebDAV resource. When you click on the URL, an LNK file hosted on the same WebDAV resource is launched, initiating the infection process.
Launching URL links allows you to skip the SmartScreen verification stage and initiate a multi-stage attack using PowerShell and JavaScript scripts. Eventually, the Lumma and Meduza Stealer malware is installed on the devices.
PowerShell scripts decrypt and execute additional payloads, install malware, and display a fake document on the victim's device. Methods of attack include DLL Sideloading and exploitation of the IDAT Loader for delivering Lumma and Meduza Stealer. The malware is then embedded in explorer.exe.
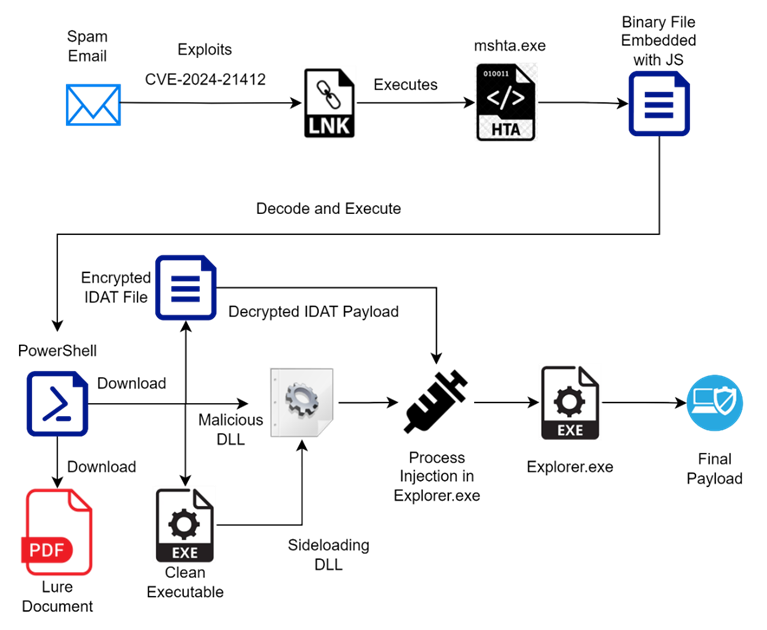
Infection chain
The attack targets individuals and organizations around the world. The campaign uses tricks such as fake tax documents in Spanish, emails from the US Department of Transportation, and Medicare forms.
The growing use of the CVE-2024-21412 vulnerability, combined with such sophisticated approaches, underscores the need for proactive security measures and constant changes to counter new threats. And the availability of the Ransomware-as-a-Service (RaaS) model can only make the situation worse, which makes it even more urgent to take measures to protect against such threats.
Source
Cybercriminals report that hackers have found a way to bypass Microsoft's SmartScreen protection to spread malware to users ' devices. A vulnerability in SmartScreen allows you to enter the system through Windows Defender and infect devices.
In January 2024, the DarkGate group exploited the vulnerability CVE-2024-21412 (CVSS score: 8.1) to deliver malicious installers that mimic popular applications such as iTunes, Notion, and NVIDIA. Microsoft fixed the vulnerability in February, but another group, Water Hydra, continued to use the flaw to distribute malware, including the DarkMe Trojan.
The initial infection begins with an email from a supposedly reliable source. The message is designed to encourage the recipient to click on a link that tricks the user into viewing a URL hosted on a remote WebDAV resource. When you click on the URL, an LNK file hosted on the same WebDAV resource is launched, initiating the infection process.
Launching URL links allows you to skip the SmartScreen verification stage and initiate a multi-stage attack using PowerShell and JavaScript scripts. Eventually, the Lumma and Meduza Stealer malware is installed on the devices.
PowerShell scripts decrypt and execute additional payloads, install malware, and display a fake document on the victim's device. Methods of attack include DLL Sideloading and exploitation of the IDAT Loader for delivering Lumma and Meduza Stealer. The malware is then embedded in explorer.exe.

Infection chain
The attack targets individuals and organizations around the world. The campaign uses tricks such as fake tax documents in Spanish, emails from the US Department of Transportation, and Medicare forms.
The growing use of the CVE-2024-21412 vulnerability, combined with such sophisticated approaches, underscores the need for proactive security measures and constant changes to counter new threats. And the availability of the Ransomware-as-a-Service (RaaS) model can only make the situation worse, which makes it even more urgent to take measures to protect against such threats.
Source







