Man
Professional
- Messages
- 3,221
- Reaction score
- 1,175
- Points
- 113
Hackers have learned to hide viruses where no one is looking for them.
Group-IB specialists have identified a new way to distribute a Trojan for macOS called RustyAttr. Hackers use advanced file attributes to hide malicious code in metadata and use fake PDF documents to bypass defenses.
The essence of the technique is that attackers hide malicious code in extended attributes of macOS files. This metadata is usually hidden from the user's eyes and is not visible in the Finder or terminal. They can only be seen and changed with the special "xattr" command. In the case of RustyAtr, the hidden attribute is called "test" and contains a shell script.
Malicious applications using this technique are based on the Tauri framework, which combines a web frontend (HTML, JavaScript) with a Rust backend. When launched, these applications load a web page where a JavaScript script «preload.js" retrieves code from a hidden attribute and runs it.
To avoid arousing suspicion, hackers use fake PDFs or show error messages. These PDF documents are downloaded from the pCloud service and often have names related to cryptocurrency investments, which coincides with the goals of the Lazarus group. Group-IB experts believe that hackers from Lazarus may be behind this attack, but there is no exact confirmation of this yet. Researchers believe that the attackers are now testing a new way to distribute malware.
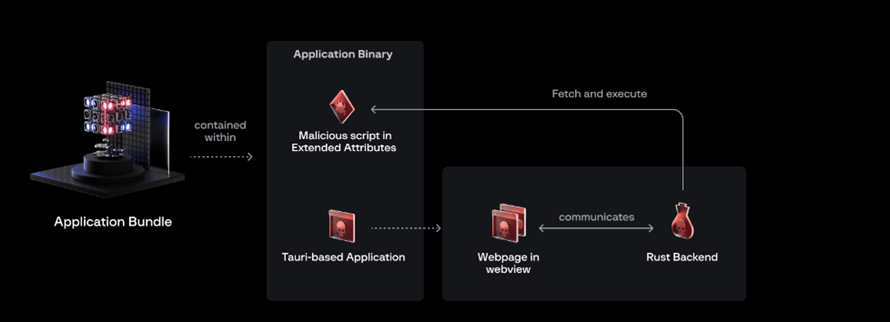
Infection chain
The method used turned out to be effective in bypassing antivirus solutions — none of the analyzers of the Virus Total platform recognized malicious files. The programs were signed with a compromised certificate, which Apple has already revoked, but they did not go through the notarization procedure.
At the moment, researchers have not been able to extract and study the next link in the malicious chain, but they have found a connection to a familiar domain that is used in the Lazarus infrastructure to download malware.
Previously, a similar tactic was used by another North Korean group, BlueNoroff. The group used cryptocurrency-themed phishing to trick users into installing malicious applications. These programs were also signed, but used a different technique to bypass protection. While it is not known whether these attacks are related, experts suggest that hackers may be sharing successful hacking techniques to bypass macOS security systems.
For now, built-in macOS tools such as Gatekeeper block these applications from running unless users have disabled protection. However, if users disable Gatekeeper, it will allow attackers to bypass security. Lazarus can refine its techniques and prepare new versions of attacks with signed and notarized applications to bypass macOS protection.
Source
Group-IB specialists have identified a new way to distribute a Trojan for macOS called RustyAttr. Hackers use advanced file attributes to hide malicious code in metadata and use fake PDF documents to bypass defenses.
The essence of the technique is that attackers hide malicious code in extended attributes of macOS files. This metadata is usually hidden from the user's eyes and is not visible in the Finder or terminal. They can only be seen and changed with the special "xattr" command. In the case of RustyAtr, the hidden attribute is called "test" and contains a shell script.
Malicious applications using this technique are based on the Tauri framework, which combines a web frontend (HTML, JavaScript) with a Rust backend. When launched, these applications load a web page where a JavaScript script «preload.js" retrieves code from a hidden attribute and runs it.
To avoid arousing suspicion, hackers use fake PDFs or show error messages. These PDF documents are downloaded from the pCloud service and often have names related to cryptocurrency investments, which coincides with the goals of the Lazarus group. Group-IB experts believe that hackers from Lazarus may be behind this attack, but there is no exact confirmation of this yet. Researchers believe that the attackers are now testing a new way to distribute malware.

Infection chain
The method used turned out to be effective in bypassing antivirus solutions — none of the analyzers of the Virus Total platform recognized malicious files. The programs were signed with a compromised certificate, which Apple has already revoked, but they did not go through the notarization procedure.
At the moment, researchers have not been able to extract and study the next link in the malicious chain, but they have found a connection to a familiar domain that is used in the Lazarus infrastructure to download malware.
Previously, a similar tactic was used by another North Korean group, BlueNoroff. The group used cryptocurrency-themed phishing to trick users into installing malicious applications. These programs were also signed, but used a different technique to bypass protection. While it is not known whether these attacks are related, experts suggest that hackers may be sharing successful hacking techniques to bypass macOS security systems.
For now, built-in macOS tools such as Gatekeeper block these applications from running unless users have disabled protection. However, if users disable Gatekeeper, it will allow attackers to bypass security. Lazarus can refine its techniques and prepare new versions of attacks with signed and notarized applications to bypass macOS protection.
Source

