Carding
Professional
- Messages
- 2,871
- Reaction score
- 2,372
- Points
- 113
Hackers do not give up and look for any ways to steal confidential data.
The Russian information security company F. A. C. C. T. has registered new attacks by the hacker group RedCurl, known for its activities in the field of commercial espionage and theft of corporate information.
The detected attacks were directed at one of the main banks in Russia, which was subjected to cyber attacks twice: the first time-using specialized phishing emails on behalf of a large Russian marketplace, and the second time — through a bank contractor.
A recent F. A. C. C. T. report details the RedCurl attacks that occurred in November 2022 and May 2023. In both cases, the primary implementation strategy for the corporate network was the use of phishing emails with malware. The letters were written on behalf of the marketplace and promised family members and employees a 25% corporate discount on all products.
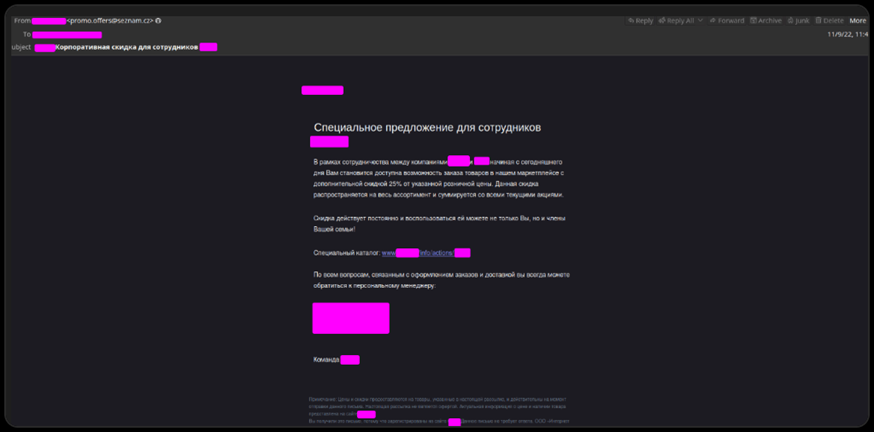
Example of a RedCurl phishing email
The target of the November hack was a well-known Russian bank from the list of systemically important credit institutions. Despite the cybercriminals ' attempt to send malicious messages, their emails were detected, blocked and did not reach the recipients due to the email protection system installed in the banking infrastructure.
After the first failed attempt, RedCurl hackers targeted the bank's contractor, using the tactic of attacking the supplier (Supply Chain). Having established control over the contractor's employee's computer, presumably through a phishing newsletter, the attackers gained access to a shared network drive with client documents, which allowed them to penetrate the infrastructure of the financial institution.
During the investigation of incidents in November 2022 and May 2023, F. A. C. C. T. specialists collected and analyzed samples of the RedCurl malware.
At the first stage of infection, the group used the loader "RedCurl.SimpleDownloader", specially designed for a new campaign using the marketplace brand. F. A. C. C. T. experts believe that this is a new full-fledged tool that will be modified and used in future RedCurl attacks.
In the next step, the updated loader "RedCurl.Downloader" was used to download "RedCurl.Extractor". This program is used to install the "RedCurl.FSABIN" agent, which, in turn, provides attackers with remote access to the infected computer.
The F. A. C. C. T. representative stressed that groups such as RedCurl pose a threat to Russian companies that do not have solutions for early prevention of complex attacks. Despite the fact that the email protection tool stopped the attack, cybercriminals found a weak link in the form of a supplier — this attack vector must also be taken into account.
In their report, F. A. C. C. T. specialists described the infection chains of the RedCurl group, compromise indicators (IoC), and protection recommendations in accordance with the MITRE ATT&CK matrix.
The Russian information security company F. A. C. C. T. has registered new attacks by the hacker group RedCurl, known for its activities in the field of commercial espionage and theft of corporate information.
The detected attacks were directed at one of the main banks in Russia, which was subjected to cyber attacks twice: the first time-using specialized phishing emails on behalf of a large Russian marketplace, and the second time — through a bank contractor.
A recent F. A. C. C. T. report details the RedCurl attacks that occurred in November 2022 and May 2023. In both cases, the primary implementation strategy for the corporate network was the use of phishing emails with malware. The letters were written on behalf of the marketplace and promised family members and employees a 25% corporate discount on all products.

Example of a RedCurl phishing email
The target of the November hack was a well-known Russian bank from the list of systemically important credit institutions. Despite the cybercriminals ' attempt to send malicious messages, their emails were detected, blocked and did not reach the recipients due to the email protection system installed in the banking infrastructure.
After the first failed attempt, RedCurl hackers targeted the bank's contractor, using the tactic of attacking the supplier (Supply Chain). Having established control over the contractor's employee's computer, presumably through a phishing newsletter, the attackers gained access to a shared network drive with client documents, which allowed them to penetrate the infrastructure of the financial institution.
During the investigation of incidents in November 2022 and May 2023, F. A. C. C. T. specialists collected and analyzed samples of the RedCurl malware.
At the first stage of infection, the group used the loader "RedCurl.SimpleDownloader", specially designed for a new campaign using the marketplace brand. F. A. C. C. T. experts believe that this is a new full-fledged tool that will be modified and used in future RedCurl attacks.
In the next step, the updated loader "RedCurl.Downloader" was used to download "RedCurl.Extractor". This program is used to install the "RedCurl.FSABIN" agent, which, in turn, provides attackers with remote access to the infected computer.
The F. A. C. C. T. representative stressed that groups such as RedCurl pose a threat to Russian companies that do not have solutions for early prevention of complex attacks. Despite the fact that the email protection tool stopped the attack, cybercriminals found a weak link in the form of a supplier — this attack vector must also be taken into account.
In their report, F. A. C. C. T. specialists described the infection chains of the RedCurl group, compromise indicators (IoC), and protection recommendations in accordance with the MITRE ATT&CK matrix.
