Over the past few years, attitudes towards privacy have become much more serious.
Storing personal data on servers has become the norm; the world is flooded with mobile gadgets with GPS receivers and GSM-modules that can tell almost everything about their owners; Snowden has shown how vulnerable we are to being monitored; Governments are increasingly invade the privacy of citizens and control our every word. A reasonable question: is it possible to remain anonymous in such conditions?

Anonymity in android
The situation with smartphones is much more complicated.
These devices seem to be created in order to spy on us, and they do it all the time, regardless of whether we are actively using them or just calling. Modern smartphone drains
data on several fronts at the same time:
When these requirements are met, we take the smartphone in hand, get root (we wrote many times how to do this), register in Google play, install the ROM Installer application and flash CyanogenMod with it. We will definitely refuse to install Google Apps. They will have to be sacrificed to the god of privacy.
Another advantage of CyanogenMod over stock firmware is SELinux, which is activated by default. SELinux is a system for enforcing access to kernel functionality that runs below Android and does not apply to standard user applications. This is a kind of Privacy Guard analogue for various low-level services.
SELinux severely restricts the capabilities of such services, preventing them from performing actions for which they are not intended. In other words, if a virus causes a buffer overflow in adbd, rild, or any other native service in order to elevate itself on the system, SELinux will stop that attempt. The second important advantage of SELinux is blocking backdoors, which can be embedded in proprietary libraries and services that have no open counterparts (almost any CyanogenMod assembly includes proprietary components from a smartphone or mobile chip manufacturer).
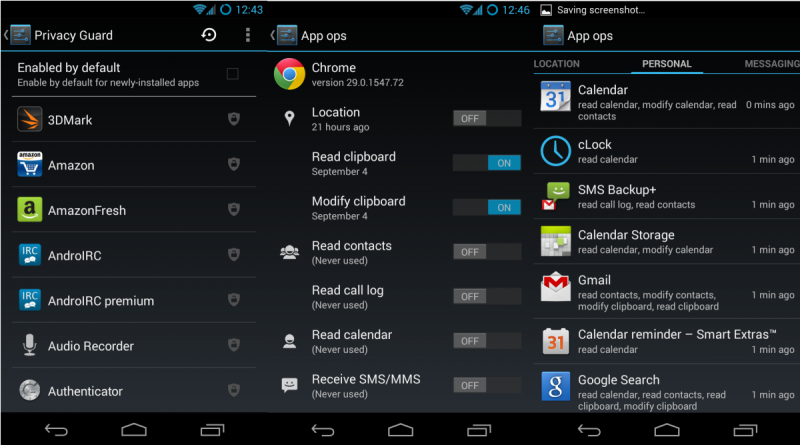
After the first download, CyanogenMod will offer to register or connect a CM account, as well as enable the sending of anonymous statistics. Of course, you should refuse to perform these procedures. Next, we proceed to the initial configuration of the firmware. We go to the settings and mark the following items:
privacy-guard02
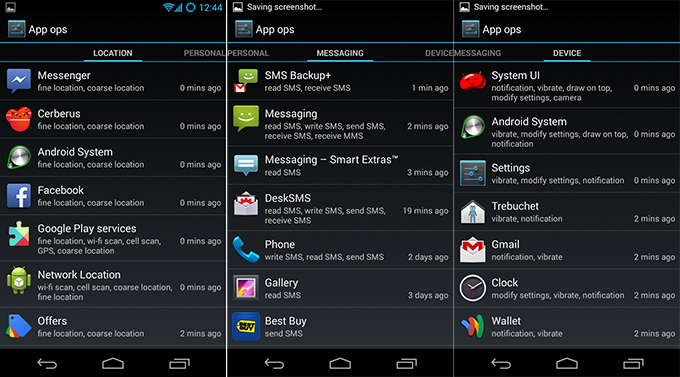
To activate Privacy Guard for stock applications, press the settings button at the top (three dots), check the "System Applications" option and select all applications except Trebuchet (this is the desktop). By default, Privacy Guard is configured to ask the user every time the application tries to access personal data (you can see this in the "Privacy Guard in action" screenshot). Allow this action only if it really needs such data (for example, the phone is trying to read the address book).
privacy-guard
The last step is to enable encryption of the smartphone's memory. This action does not apply to data leaks on the Internet, but it will help in case of smartphone theft. To do this, launch the terminal and type two commands:
First command: $ su
Second command: vdc cryptfs enablecrypto inplace PASSWORD
The smartphone will reboot and encrypt the application data. After that, each time you turn on the smartphone, you will have to enter the password to decrypt them. By the way, the same operation can be done through the settings, but in this case the decryption password will coincide with the unreliable four-digit PIN-code of the lock screen.

orbot-setting
Tor (in Android it is called Orbot), in turn, will allow us to remain anonymous when using the Web. The firewall will block incoming connections and redirect traffic of all installed applications to Orbot.
$ ./install-fi rewall.sh
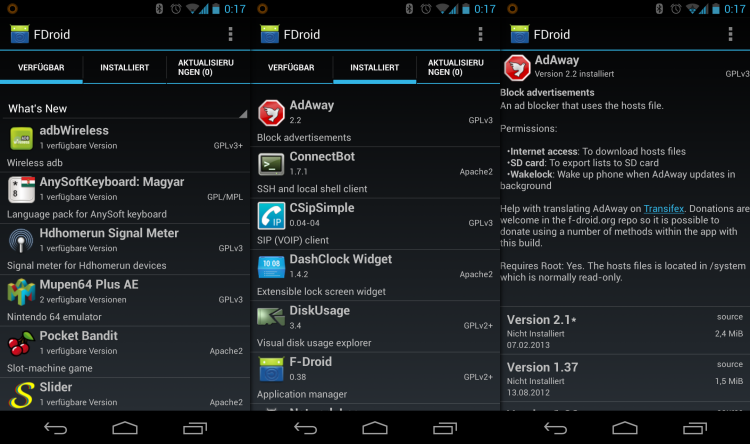
fdroid-setting
The script works only in Linux and requires that the Android SDK be installed, and the debug mode is activated on the smartphone ("Settings - About the phone - Seven tapes on the item" Build number ",
further "Settings - For Developers - USB Debugging"). The script does the following:
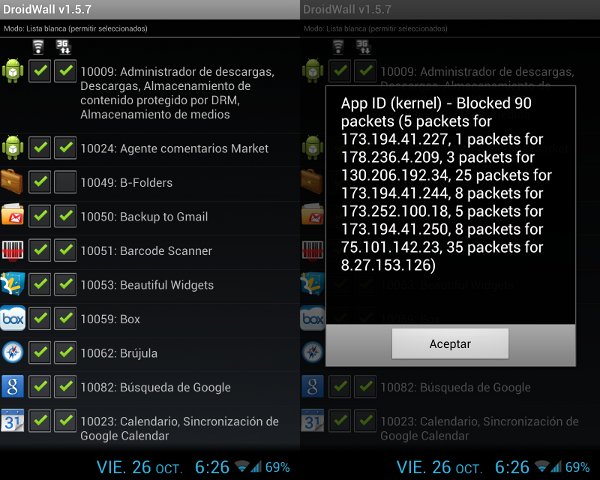
When the scripts are installed, launch DroidWall, go to "Menu - More - Install Script" and enter the line ". /Data/local/firewall-torify-all.sh", click the "OK" button. We return to the main screen and mark the applications that need to access the Web with checkmarks (Orbot can be left unchecked, it will get access anyway thanks to the script). Reopen the menu and select the "Firewall Disabled" item to activate the firewall. Then launch Orbot and follow the instructions, but in no case enable root support; For the rules written in the script to work correctly, Orbot must work in user space in proxy mode. Finally, click on the button in the center of the screen to turn on Tor. The Tor icon will appear in the status bar, which means that now all data will go through it.
droidwall
The smartphone does not have a single Google app or backdoor hidden in the firmware that could send sensitive data to remote servers. If such an application is installed on the system, it will be subject to the Privacy Guard system, which will exclude any leaks, even if they would have occurred in a standard situation. If malware somehow starts up in the system, it will be limited on three fronts at once: SELinux will cut off the possibility of hidden root gain, Privacy Guard will not allow confidential data to be merged, DroidWall will not allow access to the Network until you yourself want it ...
Only one question remains open:
how to deal with backdoors in proprietary components and GSM networks. Unfortunately, it is not yet possible to fully defend against this threat: even despite the presence of SELinux, the backdoor embedded in the firmware may well gain access to data bypassing Android, receiving commands from the attacker / FSB via GSM commands. However, traffic passing over cellular networks will still be protected.
Useful links:
Build Chromium for Android:
https://ci.chromium.org/buildbot/chromium/Android/
Guardian Project - Android anonymization applications: guardianproject.info
Blackphone - the first smartphone for anonymous users: www.blackphone.ch
The definitive guide to smartphone anonymization from the Tor developers: https://blog.torproject.org/mission-impossible-hardening-android-security-and-privacy
Storing personal data on servers has become the norm; the world is flooded with mobile gadgets with GPS receivers and GSM-modules that can tell almost everything about their owners; Snowden has shown how vulnerable we are to being monitored; Governments are increasingly invade the privacy of citizens and control our every word. A reasonable question: is it possible to remain anonymous in such conditions?

Anonymity in android
BRIEF COURSE OF CONSPIROLOGY
When it comes to an ordinary home computer, the issue of anonymity is easy to solve. A fresh version of the open source operating system, an open source browser with JavaScript disabled, Tor, changing MAC addresses, DuckDuckGo instead of Google and Yandex, replacing Dropbox with a personal Rsync server, rejecting any services that require identity verification - that is, in fact, everything that is required to hide yourself from the eyes of the Internet.The situation with smartphones is much more complicated.
These devices seem to be created in order to spy on us, and they do it all the time, regardless of whether we are actively using them or just calling. Modern smartphone drains
data on several fronts at the same time:
- Synchronization of data with the servers of the smartphone manufacturer and / or operating system. The same Android, by default, pours our contacts, location information, credit card information, scheduled calendar events, photos, documents created in Google Docs to Google servers. The stock firmware of many smartphones remains in contact with the manufacturer's servers, and in many cases forces the user to create an account on their servers.
- Open Wi-Fi networks in McDucks and other Subways do not offer any means of protecting traffic, so it can be easily intercepted by a third party (or even by the admin).
- Many third-party applications do not encrypt traffic and send information about the device and its owner to remote servers without even asking the latter.
- GSM networks do not provide a means of authenticating subscribers, allowing anyone to intercept traffic with a base station purchased for $ 1000. And if serious organizations are interested in you, then the triangulation method will allow you to find out your
- location with an accuracy of one hundred meters.
- Inside any smartphone, there is a built-in miniature closed-source RTOS, the capabilities of which only the manufacturer of the mobile chip and special services know about. It is not difficult to assume that such an OS can give out your location and send personal information to whomever needs it.
ANDROID AND CYANOGENMOD SMARTPHONE
Obviously, dealing with leaks in smartphones based on proprietary operating systems is stupid. No source - no evidence of no backdoors. To get at least some anonymized smartphone, we need a Googlephone. And not just a Googlephone, but one for which there is an official version of the latest CyanogenMod firmware and open source kernels (stock firmware or the kernel of an Android smartphone may also contain backdoors).When these requirements are met, we take the smartphone in hand, get root (we wrote many times how to do this), register in Google play, install the ROM Installer application and flash CyanogenMod with it. We will definitely refuse to install Google Apps. They will have to be sacrificed to the god of privacy.
Another advantage of CyanogenMod over stock firmware is SELinux, which is activated by default. SELinux is a system for enforcing access to kernel functionality that runs below Android and does not apply to standard user applications. This is a kind of Privacy Guard analogue for various low-level services.
SELinux severely restricts the capabilities of such services, preventing them from performing actions for which they are not intended. In other words, if a virus causes a buffer overflow in adbd, rild, or any other native service in order to elevate itself on the system, SELinux will stop that attempt. The second important advantage of SELinux is blocking backdoors, which can be embedded in proprietary libraries and services that have no open counterparts (almost any CyanogenMod assembly includes proprietary components from a smartphone or mobile chip manufacturer).
After the first download, CyanogenMod will offer to register or connect a CM account, as well as enable the sending of anonymous statistics. Of course, you should refuse to perform these procedures. Next, we proceed to the initial configuration of the firmware. We go to the settings and mark the following items:
Nothing fancy, standard options. Next, we need to protect ourselves from data leaks from pre-installed applications and software that will be installed later. CyanogenMod has a Privacy Guard mechanism for this, which obfuscates the user's personal data, slipping random data instead: a randomly generated username instead of a real one, random coordinates, and so on. To activate it, go to "Settings - Privacy - Protected mode" and enable the "Protected mode by default" option. Now it will be activated for all installed applications.1. Wireless networks - More - NFC - Disable.
2. Security - Screen lock - PIN.
3. Security - Unknown sources.

privacy-guard02
To activate Privacy Guard for stock applications, press the settings button at the top (three dots), check the "System Applications" option and select all applications except Trebuchet (this is the desktop). By default, Privacy Guard is configured to ask the user every time the application tries to access personal data (you can see this in the "Privacy Guard in action" screenshot). Allow this action only if it really needs such data (for example, the phone is trying to read the address book).

privacy-guard
The last step is to enable encryption of the smartphone's memory. This action does not apply to data leaks on the Internet, but it will help in case of smartphone theft. To do this, launch the terminal and type two commands:
First command: $ su
Second command: vdc cryptfs enablecrypto inplace PASSWORD
The smartphone will reboot and encrypt the application data. After that, each time you turn on the smartphone, you will have to enter the password to decrypt them. By the way, the same operation can be done through the settings, but in this case the decryption password will coincide with the unreliable four-digit PIN-code of the lock screen.
F-DROID, TOR AND FIREWALL
The next step is to install F-Droid, Tor and configure the firewall. We need the first one due to the lack of Google play, as well as any replacement that we could trust. In contrast, F-Droid contains only open source software, which effectively guarantees the safety of the software. There are slightly more than 1100 applications in the F-Droid repository, but among them there is almost everything you need, including browsers, twitter clients, desktops, weather widgets and even Telegram.
orbot-setting
Tor (in Android it is called Orbot), in turn, will allow us to remain anonymous when using the Web. The firewall will block incoming connections and redirect traffic of all installed applications to Orbot.
Why not use ORBOT ROOT mode
First, install F-Droid. To do this, just open the f-droid.org website from your smartphone and download the latest version of the client. We launch it, find the Orbot application and install it. Next, go to the DroidWall page (goo.gl/dCXXev) from your smartphone, download the APK package and install it. Now we need to create a set of iptables rules for DroidWall (by default, it can only enable / disable access of applications to the Network). We could have done it manually, but the guys from the Tor project have already done everything for us. All you need to do is download the ZIP archive (goo.gl/2JK9MQ), unpack it, connect the smartphone using a USB cable and run the installation script:Orbot supports root mode, which allows it to transparently proxy any Android application through itself. It may seem that this option would be preferable to a bunch of DroidWall and scripts, but this is not the case. Firstly, working in root mode, Orbot will conflict with DroidWall, and the latter is necessary for us to be able to restrict applications on the Internet. Secondly, Orbot has the ability to reset transparent proxying settings when switching between networks (Wi-Fi - Wi-Fi or Wi-Fi - 3G), which can lead to a data leak. The Linux firewall (which is used in the script) does not have this problem. Last but not least, you don't have to worry about Orbot crashing or being compromised.
$ ./install-fi rewall.sh

fdroid-setting
The script works only in Linux and requires that the Android SDK be installed, and the debug mode is activated on the smartphone ("Settings - About the phone - Seven tapes on the item" Build number ",
further "Settings - For Developers - USB Debugging"). The script does the following:
1. Adds an init script that blocks all incoming and outgoing connections during system boot (to avoid leaks).
2. Installs a script for DroidWall to redirect all connections to Tor (using multiple workarounds for known Tor bugs).
3. Blocks all connections from the outside.
4. Installs three scripts that open access to the Network bypassing Tor for the standard browser, ADB and LinPhone. The first may be needed if there is a need to enter the captive portal in open Wi-Fi networks, the second is needed for remote debugging, the third is needed by the LinPhone application, which implements a SIP client with an encrypted communication channel.
When the scripts are installed, launch DroidWall, go to "Menu - More - Install Script" and enter the line ". /Data/local/firewall-torify-all.sh", click the "OK" button. We return to the main screen and mark the applications that need to access the Web with checkmarks (Orbot can be left unchecked, it will get access anyway thanks to the script). Reopen the menu and select the "Firewall Disabled" item to activate the firewall. Then launch Orbot and follow the instructions, but in no case enable root support; For the rules written in the script to work correctly, Orbot must work in user space in proxy mode. Finally, click on the button in the center of the screen to turn on Tor. The Tor icon will appear in the status bar, which means that now all data will go through it.

droidwall
WHAT WE DIDN'T LEARN
The configuration described above eliminates almost all "traditional" data leaks. After turning on, the smartphone will be cut off from the Network exactly until the autorun of DroidWall and Orbot occurs. DroidWall, in turn, will cut off any applications that we have not checked from the Web, and wrap the rest in Tor.The smartphone does not have a single Google app or backdoor hidden in the firmware that could send sensitive data to remote servers. If such an application is installed on the system, it will be subject to the Privacy Guard system, which will exclude any leaks, even if they would have occurred in a standard situation. If malware somehow starts up in the system, it will be limited on three fronts at once: SELinux will cut off the possibility of hidden root gain, Privacy Guard will not allow confidential data to be merged, DroidWall will not allow access to the Network until you yourself want it ...
Only one question remains open:
how to deal with backdoors in proprietary components and GSM networks. Unfortunately, it is not yet possible to fully defend against this threat: even despite the presence of SELinux, the backdoor embedded in the firmware may well gain access to data bypassing Android, receiving commands from the attacker / FSB via GSM commands. However, traffic passing over cellular networks will still be protected.
INSTEAD OF CONCLUSION
There was a movie called Johnny the Mnemonic, about people with implants who could carry important data. They were hunted not only by the special services, but simply by everyone, everyone wanted that piece of information that was stored in the mnemonic implant. They were killed, torn to pieces and cut with fishing line only in order to obtain classified information. Fairy tale. Absurd. But somehow so familiar. In general, take care of yourself and your personal data. This is getting more and more difficult today.Useful links:
Build Chromium for Android:
https://ci.chromium.org/buildbot/chromium/Android/
Guardian Project - Android anonymization applications: guardianproject.info
Blackphone - the first smartphone for anonymous users: www.blackphone.ch
The definitive guide to smartphone anonymization from the Tor developers: https://blog.torproject.org/mission-impossible-hardening-android-security-and-privacy
