Hello, carders!
Let's continue yesterday's topic. A small review of the acclaimed browser (they bought decent ads, yes).
There are a variety of tasks (it's clear which ones, right?) that require you to quickly switch between a large number of accounts (including in social networks), and at the same time avoiding fingerprinting and other tracking mechanisms is critical. The Linken Sphere browser is just one of these solutions.
The standard way to ensure that you have a lot of "personalities" is to accumulate more VMs and make the necessary changes to them. Usually this has to be done manually, which is quite tedious. The Linken Sphere multithreaded browser makes all this work unnecessary and allows you to be in a variety of places at the same time, and also negates all attempts by anti-fraud systems to catch you and prevent you from freely switching between accounts.

How does this solution differ from other similar tools? Linken Sphere is based on Chromium. Work is done directly with the engine's source code, which allows you to completely get rid of Google's spyware code - developers of "boxed" products usually do not do this. Among other things, this gives you additional flexibility and access to any functions.
Main advantages
What features of the program should you pay attention to?
Preheater
As you know, in the case of farming, there is a need to receive cookies before you start working with your account in order to reduce the likelihood that a fake user will be identified as a robot. The browser allows you to automate the process of switching between sites in order to collect such data, and it does this in the background multithreaded mode. You can set up the necessary pages for visiting, the depth of viewing, and the time spent on the site yourself. In addition, it is possible to set up a timer so that this mechanism works exactly at the time interval when it is necessary.
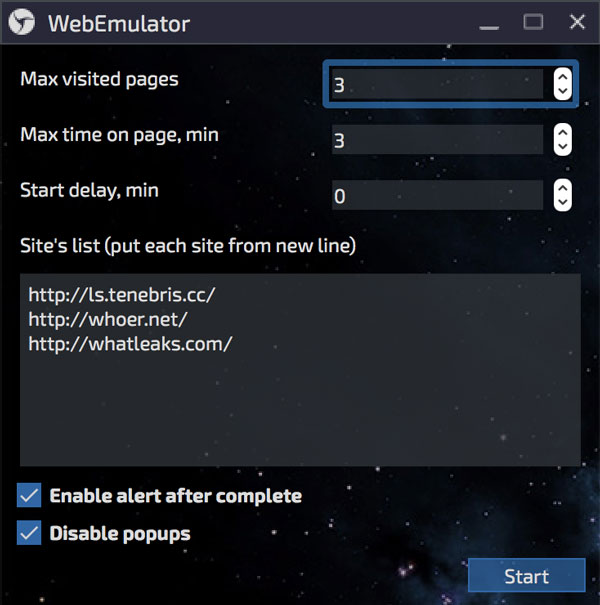
Settings
What can I configure? Yes, almost everything you might need, and even more. The browser's website contains extensive open documentation for the product, which describes all the features and settings. In short, for each individual session, you can configure or unify the following parameters that anti-fraud systems::
Working with sessions
You can call sessions by their proper names, assign colors to them for better navigation, copy, transfer, clean-in general, do everything you need to work with them comfortably not only on one computer, but on as many machines as you need. Linken Sphere is not linked to hardware in any way, and all types of installers are available for download. So you can safely have a browser on different machines with different operating systems, working in turn with the same username and password.
The main browser settings are configured either manually (for those with a strong skill and a lot of time), or when choosing built-in or purchased casts of real devices. The browser contains about 50,000 built-in free casts, but for certain tasks, the best option is to buy casts in the store.
As already mentioned, each session can have its own network connection configured. The browser supports several common operating modes:
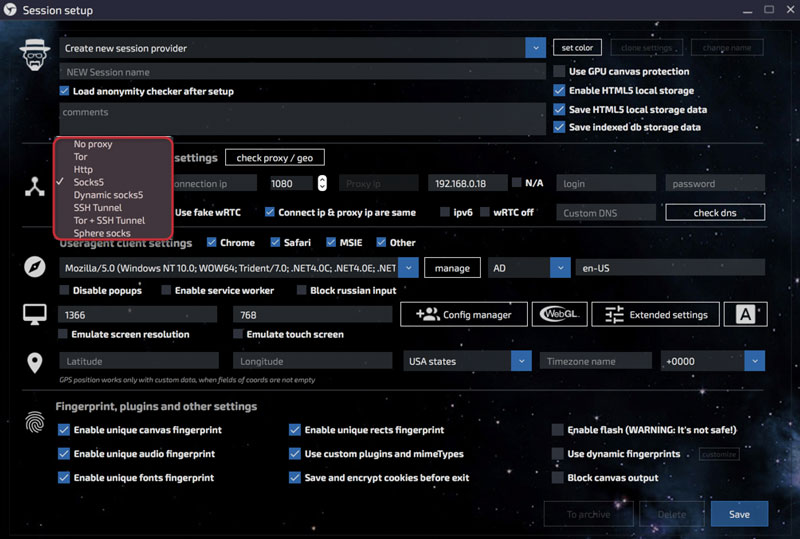
The browser also provides an artificial WebRTC drain, which allows you to keep it turned on during operation, but not to shine the real IP. Plus, it is possible to proxy the connection to the browser using the usual Proxifier + Bitvise/Plink.
Other interesting features include emulation of the touchscreen and gyroscope (it helps to simulate mobile devices), emulation of manual input when copying text, and an automatic "walker" that can visit the necessary sites in the background. By the way, it is noticeably improved from version to version and has gradually become a very useful tool.
By default, when running and logging in, the program uses the Tor network to tap the server, so as not to expose the user's real IP address. You can disable this feature if you want, and then the connection to the license verification server will be established using a native connection.
After starting the program, you will see a regular browser with the address bar. Linken Sphere is distinguished only by the presence of one important button - this is where further work will begin: Setup session provider. After clicking on it, we get to the settings menu "sessions".
A session is essentially a browser within a browser with its own settings for system parameters, headers, fingerprints, and cookies. In other words, you can store a huge number of accounts in one program, each of which will go online with different data. Thanks to multithreading support, you can work with many such accounts simultaneously, which is incredibly convenient.

Linken Sphere is an interesting all-in-one solution that can really make a lot of routine tasks much easier. Of course, the browser itself can not be a panacea for possible problems in the work, but in the right hands it will be very useful.
I'm not saying goodbye.
Let's continue yesterday's topic. A small review of the acclaimed browser (they bought decent ads, yes).
There are a variety of tasks (it's clear which ones, right?) that require you to quickly switch between a large number of accounts (including in social networks), and at the same time avoiding fingerprinting and other tracking mechanisms is critical. The Linken Sphere browser is just one of these solutions.
The standard way to ensure that you have a lot of "personalities" is to accumulate more VMs and make the necessary changes to them. Usually this has to be done manually, which is quite tedious. The Linken Sphere multithreaded browser makes all this work unnecessary and allows you to be in a variety of places at the same time, and also negates all attempts by anti-fraud systems to catch you and prevent you from freely switching between accounts.

How does this solution differ from other similar tools? Linken Sphere is based on Chromium. Work is done directly with the engine's source code, which allows you to completely get rid of Google's spyware code - developers of "boxed" products usually do not do this. Among other things, this gives you additional flexibility and access to any functions.

Main advantages
What features of the program should you pay attention to?
- The browser works in OTR mode, which makes it the most secure. Absolutely no traces of actions are saved on your computer, which will not allow even malicious programs that accidentally hit the machine to gain access to information.
- The browser is devoid of any hidden connections to Google services, which cannot be achieved without changing its source code.
- The browser encrypts all stored information using the AES-256 encryption standard. All data that is transmitted to the server for storage is only encrypted fragments of hashes that can only be read under your account.
- The browser out of the box is equipped with everything you need to work with network connections: HTTP, SOCKS, SSH, TOR, TOR + SSH, Dynamic Socks.
- The browser allows you to simultaneously work with different types of connections in multithreaded mode.
- The browser contains a built-in professional anti-detection tool, which is regularly updated and allows you to use all possible configurations of user agents, screen resolutions, language, time, geo-location and casts of real devices, changing them on the fly.
- The browser saves fingerprints and cookies for each session, allowing you to work from one place with hundreds of "personalities" without having to constantly switch between virtual machines.
- The browser contains a locally built-in licensed GeoIP2 MaxMind database, which allows you to configure the time and location of the session in just a few clicks.
- The browser has cloud-based session synchronization, which means that sessions can be easily shared between team members.
- The browser contains built-in intelligent tools that allow you to" warm up" sites in automatic mode ("Warm Up").
Preheater
As you know, in the case of farming, there is a need to receive cookies before you start working with your account in order to reduce the likelihood that a fake user will be identified as a robot. The browser allows you to automate the process of switching between sites in order to collect such data, and it does this in the background multithreaded mode. You can set up the necessary pages for visiting, the depth of viewing, and the time spent on the site yourself. In addition, it is possible to set up a timer so that this mechanism works exactly at the time interval when it is necessary.

Settings
What can I configure? Yes, almost everything you might need, and even more. The browser's website contains extensive open documentation for the product, which describes all the features and settings. In short, for each individual session, you can configure or unify the following parameters that anti-fraud systems::
- Canvas. This is an HTML5 element designed for displaying graphics, which is widely used to identify users based on the features of their video system.
- Fonts. Another channel used to determine the user is the fonts installed in the system.
- Plugins. Plug-ins installed in the browser also act as a component of the overall fingerprint, since this parameter is quite individual.
- Audiofingerprint. A relatively new technology that allows you to identify a computer by its audio system: a small audio file is played in the background, and an oscilloscope is taken.
- WebGL. This is a browser-based OpenGL implementation designed to work with three-dimensional graphics in the browser. Anti-fraud systems also successfully use it to assign fingerprints.
- Geolocation. Determining the user's location. This parameter can be used when performing sensitive operations: antifraud may want to make sure that the physical address matches the one determined by IP.
- ClientRects. An identification method based on obtaining hashes when zooming the image.
- Ubercookies. Another fingerprint is a hash from ClientRects and Audiofingerprint and allows you to identify the device with a high degree of probability.
- WebRTC (including device hashes). A technology that is used to directly connect a computer to media servers and allows you to get a real IP address without using network address anonymization tools (including proxies and VPNs). Microphones and cameras installed on your computer also have their own identifiers that need to be replaced.
- CSS (resolution). One of the ways to determine the actual window resolution is using CSS technology.
- Touch Emulation (allows you to emulate the touchscreen without showing the mouse). Even if you fake the User Agent field so that the browser is identified as a mobile device, the anti-fraud system can still identify it by other characteristics. In particular, it is very important to make sure that the mouse cursor is not displayed.
- JS Navigator (including time, language, and resolution). These are all basic browser parameters that are passed along with basic information about the program being used.
- HTTP Headers. Browser headers are one of the main parameters that make a site initially "familiar" with the browser. And of course, they are included in the set of prints.
- DNS (the ability to use your own DNS for each session). It is used to get the network address of a computer by its host name, and in some cases requires special addresses.
- Local IP. As a rule, a local address is a fairly unique value, albeit in a narrow range. It is important to be able to change this value when working with a large number of accounts.
Working with sessions
You can call sessions by their proper names, assign colors to them for better navigation, copy, transfer, clean-in general, do everything you need to work with them comfortably not only on one computer, but on as many machines as you need. Linken Sphere is not linked to hardware in any way, and all types of installers are available for download. So you can safely have a browser on different machines with different operating systems, working in turn with the same username and password.
The main browser settings are configured either manually (for those with a strong skill and a lot of time), or when choosing built-in or purchased casts of real devices. The browser contains about 50,000 built-in free casts, but for certain tasks, the best option is to buy casts in the store.

As already mentioned, each session can have its own network connection configured. The browser supports several common operating modes:
- No Proxy - using the main Internet channel;
- Tor - Using the Tor network to connect;
- SSH-implies the use of SSH tunnels;
- Tor + SSH-a combination of " Tor + tunnel»;
- HTTP-HTTPS proxy;
- Dynamic socks-dynamic proxy;
- Socks-the Socks5 proxy.

The browser also provides an artificial WebRTC drain, which allows you to keep it turned on during operation, but not to shine the real IP. Plus, it is possible to proxy the connection to the browser using the usual Proxifier + Bitvise/Plink.
Other interesting features include emulation of the touchscreen and gyroscope (it helps to simulate mobile devices), emulation of manual input when copying text, and an automatic "walker" that can visit the necessary sites in the background. By the way, it is noticeably improved from version to version and has gradually become a very useful tool.
By default, when running and logging in, the program uses the Tor network to tap the server, so as not to expose the user's real IP address. You can disable this feature if you want, and then the connection to the license verification server will be established using a native connection.
After starting the program, you will see a regular browser with the address bar. Linken Sphere is distinguished only by the presence of one important button - this is where further work will begin: Setup session provider. After clicking on it, we get to the settings menu "sessions".
A session is essentially a browser within a browser with its own settings for system parameters, headers, fingerprints, and cookies. In other words, you can store a huge number of accounts in one program, each of which will go online with different data. Thanks to multithreading support, you can work with many such accounts simultaneously, which is incredibly convenient.

Linken Sphere is an interesting all-in-one solution that can really make a lot of routine tasks much easier. Of course, the browser itself can not be a panacea for possible problems in the work, but in the right hands it will be very useful.
I'm not saying goodbye.
