Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,095
- Points
- 113
The security tool has become the main enemy.
The hackers use malware masquerading as the Palo Alto GlobalProtect tool, which can steal data and execute remote PowerShell commands to further infiltrate internal networks. The victims of the attacks were organizations in the Middle East.
The use of Palo Alto GlobalProtect as a bait indicates that the attackers are targeting corporate entities using enterprise-level software, rather than random users.
Trend Micro specialists who discovered the campaign suggest that the attack begins with a phishing email, although the exact method of delivery of the malware is not yet known. The victim runs a file named "setup.exe", which then deploys another file "GlobalProtect.exe" along with the configuration files. At this point, a window appears on the screen that mimics the GlobalProtect installation process, but in the background, the malware is quietly loaded onto the system.
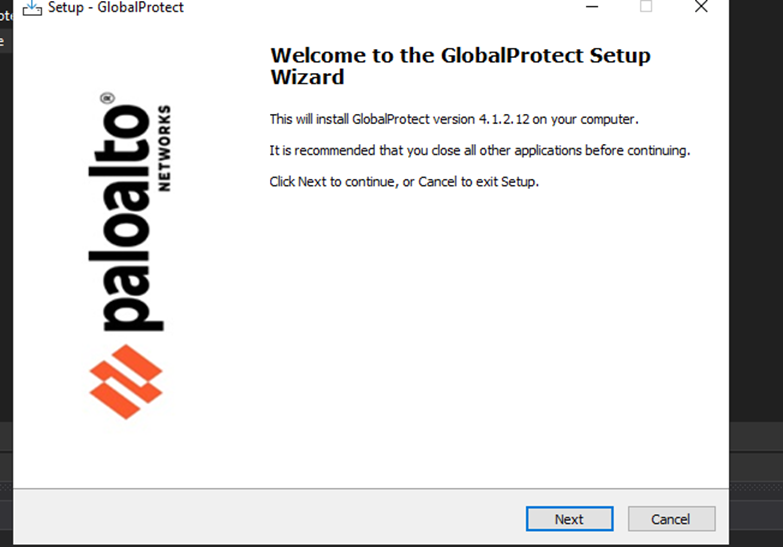
GlobalProtect fake installation window
Once executed, the malware checks to see if it is running in the sandbox before it starts executing the main code. The virus then transmits information about the compromised device to a C2 server. As an additional layer of detection protection, the malware uses AES encryption for the data strings and packets it sends.
Notably, the URL of the C2 server is newly registered and contains the string "sharjahconnect", which makes it similar to a legitimate VPN portal for offices in Sharjah, UAE. This choice of URL helps cybercriminals disguise their actions as legitimate operations and reduces the likelihood that the victim will become suspicious.
To communicate with operators after infection, the malware periodically sends signals using the legitimate open-source tool Interactsh. Although Interactsh is often used by pentesters, its "oast.fun" domain has also been seen in APT group campaigns. It should be noted that no attributions were established in this operation.
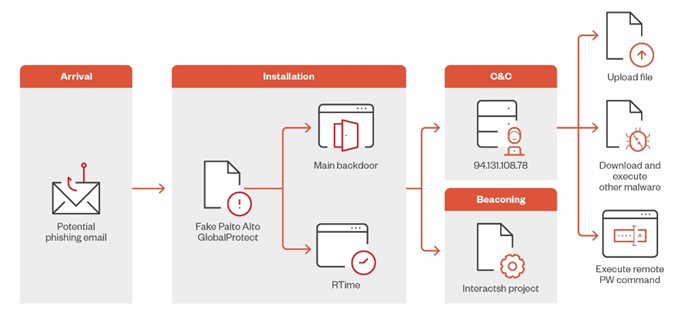
Infection chain
The C2 server can send various commands to the infected device, including:
Trend Micro researchers note that while the attackers remain unknown, the operation appears to be highly targeted. Using custom URLs for specific purposes and "fresh" C2 server domains helps hackers bypass block lists.
Source
The hackers use malware masquerading as the Palo Alto GlobalProtect tool, which can steal data and execute remote PowerShell commands to further infiltrate internal networks. The victims of the attacks were organizations in the Middle East.
The use of Palo Alto GlobalProtect as a bait indicates that the attackers are targeting corporate entities using enterprise-level software, rather than random users.
Trend Micro specialists who discovered the campaign suggest that the attack begins with a phishing email, although the exact method of delivery of the malware is not yet known. The victim runs a file named "setup.exe", which then deploys another file "GlobalProtect.exe" along with the configuration files. At this point, a window appears on the screen that mimics the GlobalProtect installation process, but in the background, the malware is quietly loaded onto the system.

GlobalProtect fake installation window
Once executed, the malware checks to see if it is running in the sandbox before it starts executing the main code. The virus then transmits information about the compromised device to a C2 server. As an additional layer of detection protection, the malware uses AES encryption for the data strings and packets it sends.
Notably, the URL of the C2 server is newly registered and contains the string "sharjahconnect", which makes it similar to a legitimate VPN portal for offices in Sharjah, UAE. This choice of URL helps cybercriminals disguise their actions as legitimate operations and reduces the likelihood that the victim will become suspicious.
To communicate with operators after infection, the malware periodically sends signals using the legitimate open-source tool Interactsh. Although Interactsh is often used by pentesters, its "oast.fun" domain has also been seen in APT group campaigns. It should be noted that no attributions were established in this operation.

Infection chain
The C2 server can send various commands to the infected device, including:
- Suspension of malware for a specified time;
- Execute a PowerShell script and send the result to a C2 server.
- Downloading a file from a specified URL
- Uploading a file to a remote server;
Trend Micro researchers note that while the attackers remain unknown, the operation appears to be highly targeted. Using custom URLs for specific purposes and "fresh" C2 server domains helps hackers bypass block lists.
Source

