Father
Professional
- Messages
- 2,602
- Reaction score
- 831
- Points
- 113
A new malicious campaign leaves no chance for South Korean civil servants.
North Korean hacker group Kimsuky uses advanced cyber espionage techniques, including the use of social networks and system management tools. This is reported by a recent report of the South Korean company Genians.
Kimsuky actively uses fake Facebook profiles created to imitate South Korean government officials to establish contacts with people involved in human rights and security in North Korea.
Attackers recruit their victims through simple friend requests and private messages, creating the appearance of trusting communication. Then malicious links and documents are distributed through these accounts, when the victim is no longer waiting for a trick from the interlocutor.
One of the main tools of Kimsuky attacks was the Microsoft Management Console (MMC) tool. Files with the extension ". msc" are disguised as harmless documents, but they are designed to perform unauthorized actions when they are opened. Under the guise of regular Word documents, these files run embedded malicious code that can give attackers control over the system or the ability to steal confidential information.
After successful malware installation, Kimsuky hackers set up a C2 channel for remote management of infected systems. The C2 servers used by the group are often well camouflaged to avoid detection, and also coordinate the collection of data from infected machines, including keystrokes, system information, and other sensitive data.
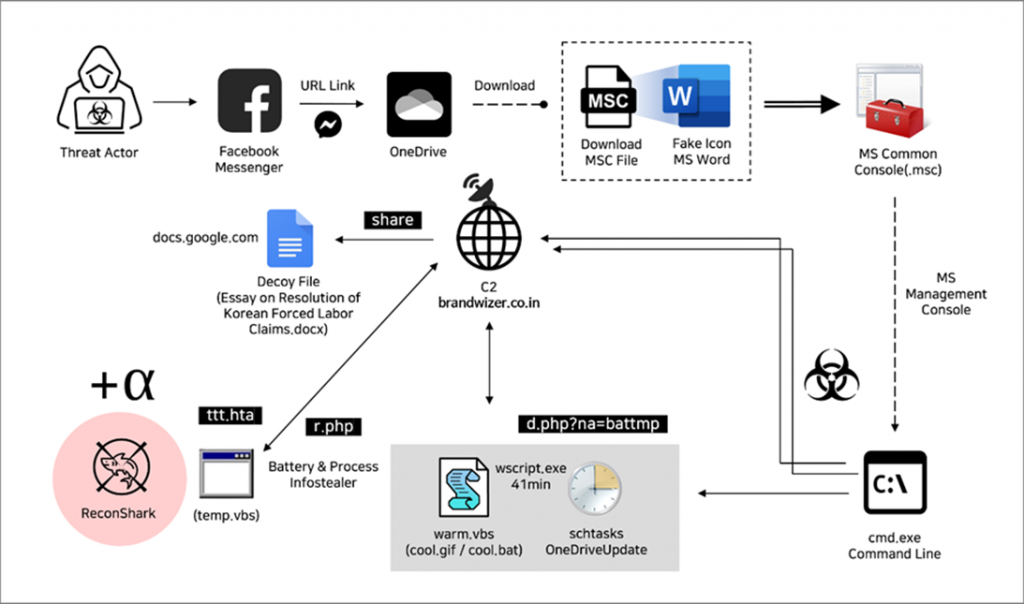
General attack pattern in the latest Kimsuky campaign
The technique used by Kimsuky indicates a shift towards more stealthy attacks, aimed primarily at using social engineering methods that can bypass traditional security measures.
Cybersecurity experts recommend paying more attention to social media interactions, especially with unknown contacts. In addition, organizations should implement threat detection systems that can detect and neutralize complex malware such as the ".msc" files used by Kimsuky.
North Korean hacker group Kimsuky uses advanced cyber espionage techniques, including the use of social networks and system management tools. This is reported by a recent report of the South Korean company Genians.
Kimsuky actively uses fake Facebook profiles created to imitate South Korean government officials to establish contacts with people involved in human rights and security in North Korea.
Attackers recruit their victims through simple friend requests and private messages, creating the appearance of trusting communication. Then malicious links and documents are distributed through these accounts, when the victim is no longer waiting for a trick from the interlocutor.
One of the main tools of Kimsuky attacks was the Microsoft Management Console (MMC) tool. Files with the extension ". msc" are disguised as harmless documents, but they are designed to perform unauthorized actions when they are opened. Under the guise of regular Word documents, these files run embedded malicious code that can give attackers control over the system or the ability to steal confidential information.
After successful malware installation, Kimsuky hackers set up a C2 channel for remote management of infected systems. The C2 servers used by the group are often well camouflaged to avoid detection, and also coordinate the collection of data from infected machines, including keystrokes, system information, and other sensitive data.

General attack pattern in the latest Kimsuky campaign
The technique used by Kimsuky indicates a shift towards more stealthy attacks, aimed primarily at using social engineering methods that can bypass traditional security measures.
Cybersecurity experts recommend paying more attention to social media interactions, especially with unknown contacts. In addition, organizations should implement threat detection systems that can detect and neutralize complex malware such as the ".msc" files used by Kimsuky.
