Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,323
- Points
- 113
Documents with an intricate name were at the forefront of the malicious campaign.
Recently, the Japanese Computer Response Coordination Center (JPCERT) confirmed that in March of this year, the North Korean hacker group Kimsuky carried out a series of cyber attacks on Japanese organizations. The agency shared the information with the public, which means that we can also review the details and methods of attacks identified by experts.
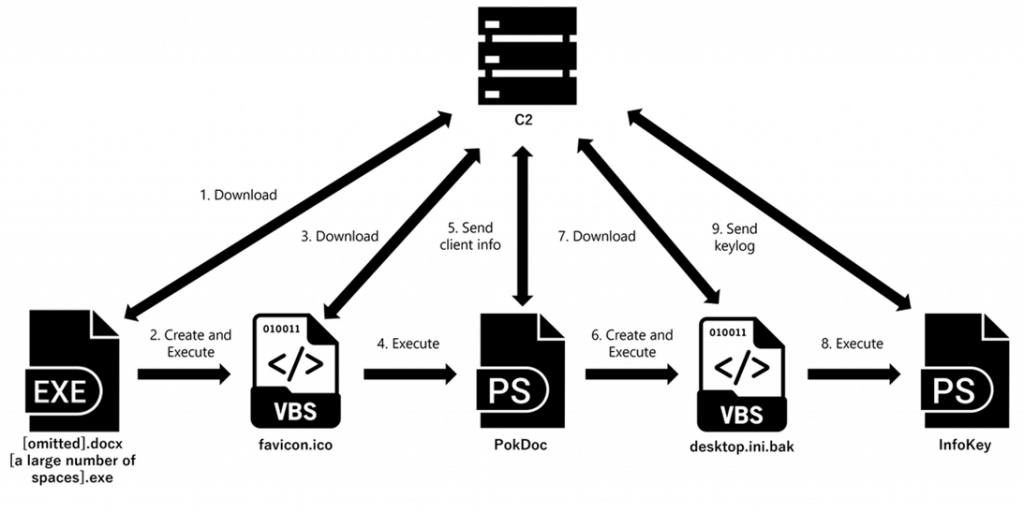
A malicious campaign starts with sending targeted emails with security and diplomatic themes. Attachments contain files with double extensions, such as ".docx.exe" and". docx.docx". Numerous spaces in the file names hide real extensions, forcing victims to run the executable file under the guise of an office document, which leads to infection of their devices.
After launching the decoy file, a VBS file is downloaded and executed from an external resource, which loads PowerShell and calls the PokDoc function, which sends the collected data to the URL specified by the attackers. The collected data includes information about the system, processes, networks, files, and user accounts.
After sending the data, another VBS file named "desktop.ini.bak"is created and executed. This file loads PowerShell in a similar way, calling the InfoKey function to act as a keylogger. Information about keystrokes and clipboard contents is saved and sent to the remote server.
Attack pattern
It is noted that Kimsuky uses similar attack methods, including VBS and PowerShell, against organizations in South Korea. This confirms that Kimsuky is also behind the attack on Japanese organizations.
Despite rare reports of Kimsuky attacks on Japanese organizations, the likelihood of active attacks in Japan remains high. Recent reports indicate the use of CHM files for keylogger execution, which requires increased attention to such threats in the future.
Source
Recently, the Japanese Computer Response Coordination Center (JPCERT) confirmed that in March of this year, the North Korean hacker group Kimsuky carried out a series of cyber attacks on Japanese organizations. The agency shared the information with the public, which means that we can also review the details and methods of attacks identified by experts.
A malicious campaign starts with sending targeted emails with security and diplomatic themes. Attachments contain files with double extensions, such as ".docx.exe" and". docx.docx". Numerous spaces in the file names hide real extensions, forcing victims to run the executable file under the guise of an office document, which leads to infection of their devices.
After launching the decoy file, a VBS file is downloaded and executed from an external resource, which loads PowerShell and calls the PokDoc function, which sends the collected data to the URL specified by the attackers. The collected data includes information about the system, processes, networks, files, and user accounts.
After sending the data, another VBS file named "desktop.ini.bak"is created and executed. This file loads PowerShell in a similar way, calling the InfoKey function to act as a keylogger. Information about keystrokes and clipboard contents is saved and sent to the remote server.

Attack pattern
It is noted that Kimsuky uses similar attack methods, including VBS and PowerShell, against organizations in South Korea. This confirms that Kimsuky is also behind the attack on Japanese organizations.
Despite rare reports of Kimsuky attacks on Japanese organizations, the likelihood of active attacks in Japan remains high. Recent reports indicate the use of CHM files for keylogger execution, which requires increased attention to such threats in the future.
Source

