Father
Professional
- Messages
- 2,602
- Reaction score
- 786
- Points
- 113
Administrators need to take urgent measures to protect the network.
F5 has announced the elimination of two critical vulnerabilities in the BIG-IP Next Central Manager management system that could be used to gain administrative access and create hidden unauthorized accounts on managed devices.
BIG-IP Next Central Manager is a tool that allows administrators to manage BIG-IP Next instances in on-premises and cloud environments through a single user interface.
The SQL injection (CVE – 2024-26026, CVSS score: 7.5) and OData injection (CVE-2024-21793, CVSS score: 7.5) vulnerabilities found in the BIG-IP Next Central Manager API allow a remote, unauthorized attacker to execute malicious SQL queries on non-updated devices.
The information security company Eclypsium, which reported these vulnerabilities and published a PoC exploit, said that hidden accounts created after hacking are not displayed in Next Central Manager and can be used for malicious activities in the victim's environment.
Eclypsium also added that the Central Manager management console can be used remotely by any attacker to gain full administrative control over the system.
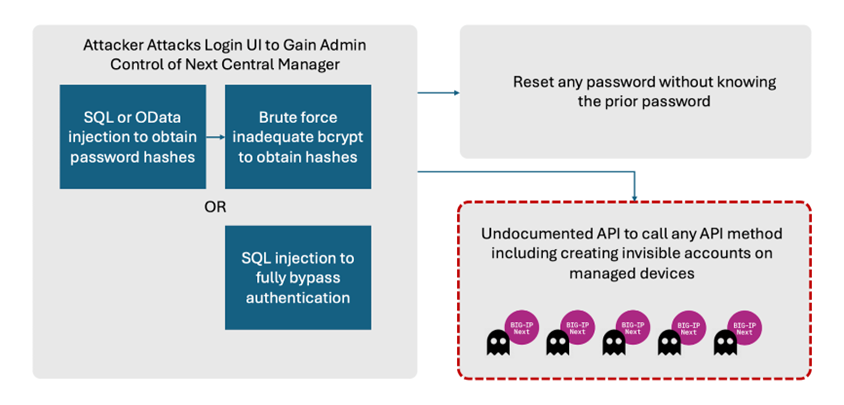
Potential attack vectors
As a temporary security measure, F5 recommends that access to Next Central Manager should only be granted to trusted users over secure networks until administrators install security updates.
According to Eclypsium, at the moment there is no evidence that the vulnerabilities were used in attacks. Despite the lack of accurate data on the number of users of BIG-IP Next Central Manager, Shodan tracks more than 10,000 F5 BIG-IP devices with open management ports on the Internet.
F5 has announced the elimination of two critical vulnerabilities in the BIG-IP Next Central Manager management system that could be used to gain administrative access and create hidden unauthorized accounts on managed devices.
BIG-IP Next Central Manager is a tool that allows administrators to manage BIG-IP Next instances in on-premises and cloud environments through a single user interface.
The SQL injection (CVE – 2024-26026, CVSS score: 7.5) and OData injection (CVE-2024-21793, CVSS score: 7.5) vulnerabilities found in the BIG-IP Next Central Manager API allow a remote, unauthorized attacker to execute malicious SQL queries on non-updated devices.
The information security company Eclypsium, which reported these vulnerabilities and published a PoC exploit, said that hidden accounts created after hacking are not displayed in Next Central Manager and can be used for malicious activities in the victim's environment.
Eclypsium also added that the Central Manager management console can be used remotely by any attacker to gain full administrative control over the system.

Potential attack vectors
As a temporary security measure, F5 recommends that access to Next Central Manager should only be granted to trusted users over secure networks until administrators install security updates.
According to Eclypsium, at the moment there is no evidence that the vulnerabilities were used in attacks. Despite the lack of accurate data on the number of users of BIG-IP Next Central Manager, Shodan tracks more than 10,000 F5 BIG-IP devices with open management ports on the Internet.
