Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,036
- Points
- 113
Hi all. Carder is with you.
2019 Let's go back 4 years. I was offered to participate in a top award ceremony that is held every year in Germany. This is an award for the best specialists in IT. One of the degrees of this award was dedicated to information security. A large company organized this competition and chose me to work in this field. At first I was still hesitant, since there was no special meaning and the reward was small. In the end, I thought about it and agreed. Everything was great. But at one fine moment I realized one interesting thing for myself - managers took it upon themselves to evaluate information security. After I told them what I thought and what I want to present to you now in this post, do you know what they did? They declared me an accomplice of terrorists. After that, in the direction of one of the top IT companies in Germany, a small thought crept into my mind - are they idiots or what? How can people who do not understand anything in their field of activity evaluate someone? They were unable to do this, and then simply simply removed this category from their awards. It’s easier for them to reward some bespectacled nerd who sits and codes useless games or a layout designer, it’s easier for them to do what they do.
Therefore, we will talk to you today about how each of you is sold and used.
The first thing I would like to start with is. Pay attention to the picture:

The principle of the balaclava. What it is? It's like Schrödinger's cat. He is both alive and dead at the same time. The balaclava is the same in every action you take online. You are doing things and not doing things at the same time.
Let's now leave the world of IT and enter the ordinary sphere of life and imagine that one of you goes out into the street and puts on a balaclava. Will you be anonymous? Yes, you will be anonymous. They won't recognize you. It is unknown who this is, some strange dude. But at the same time, if this strange dude in this balaclava walks down the street, then what will happen? People will identify this unknown and incomprehensible dude. How? They will identify him as an asshole in a balaclava. That's all. You walk and each of the people who are on the street will see you, will point a finger and say: “This is an asshole in a balaclava .” That is, you seem to have observed the rules of anonymity, your face is not visible, but at the same time you identify yourself independently due to those actions that you do not understand, that were imposed on you, in which you yourself are just a bug.
What does the balaclava principle mean ? For example, you want to bypass some kind of security system. In principle, the balaclava, you bypass it at the same time , the system does not see you, but at the same time you do not bypass it because the system sees you - for the reason that you are identified by your non-identification.
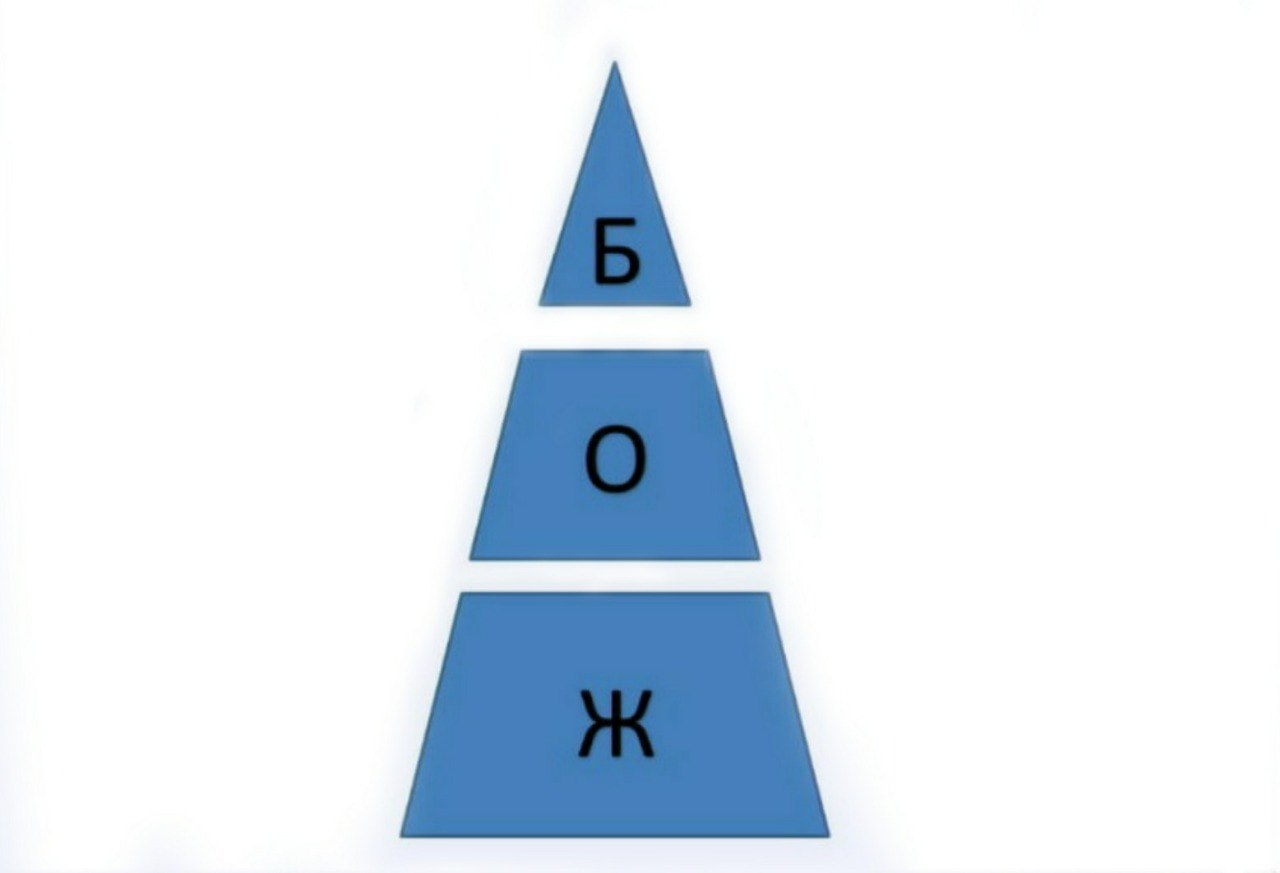
Whatever devices you surf the network from, there are several levels of obtaining information about you, I presented them in the pyramid above. The lowest and simplest level is the hardware level by which you can identify your computer, laptop, tablet, phone, TV, anything, any device with which you surf the Internet:
The next level is the operating system. This is what you use to surf the Internet. In other words, you need something to start your hardware. This is the operating system:

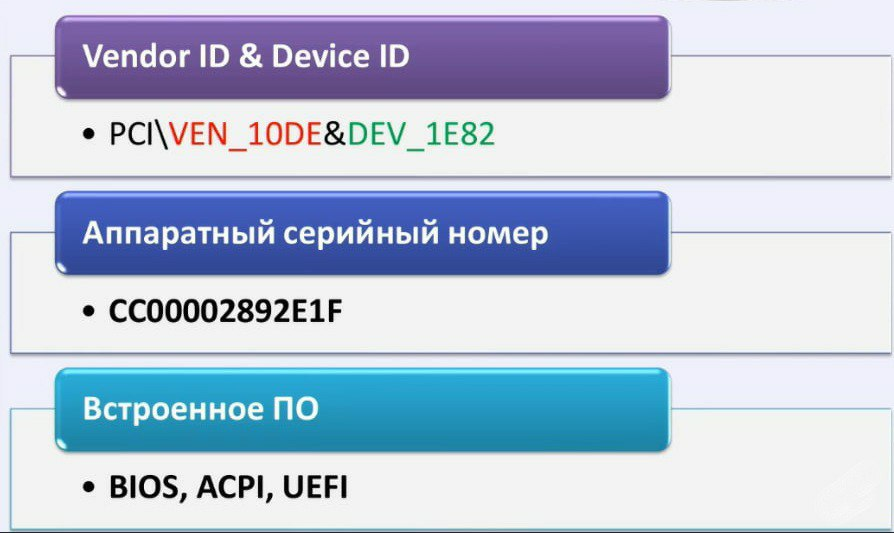
We will talk about the operating system in more detail, but I would like to return a little now to your hardware. Your piece of hardware has several parameters that can be monitored. You can see these parameters now in this picture:
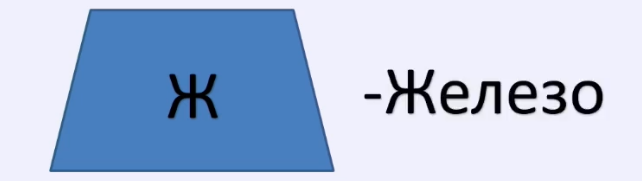
There are three main groups by which you can be identified.
First, pay attention to Vendor ID & Device ID:
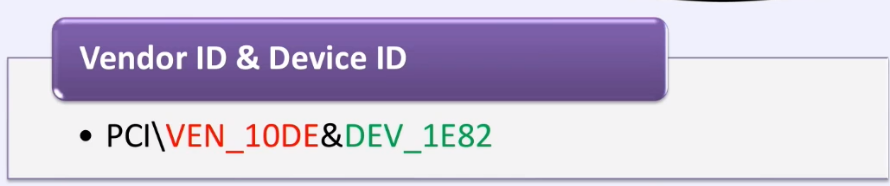
What is it and what does it mean? This means that every piece of hardware inside your PC, laptop, phone and whatever it is has two main identifiers. The first identifier is the identifier of the vendor, that is, the one who produced this equipment. For example, in the picture above I highlighted VEN_10DE in red - this will correspond to the NVIDEO company. The next Device ID
parameter , which we see as DEV_1E82 , will correspond, for example, to your video card, and it will also correspond to your sound card, or any other part of your PC/phone. These are called basic hardware identifiers and they are built into your hardware. As soon as you insert this piece of hardware into your computer, these identifiers go to your BIOS or to your UEFI so that your operating system, your PC, understands what was inserted into it. The second part is the hardware serial number:
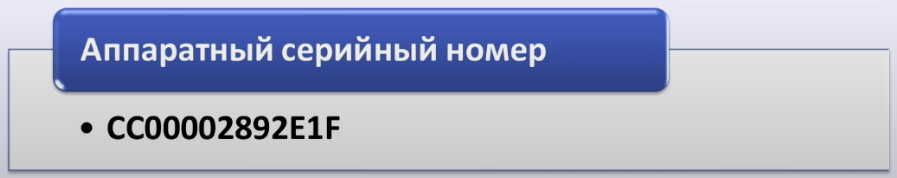
A hardware serial number allows your device to identify itself beyond who made it, in addition to the model of that device. It also allows you to identify your specific device, your unit.
And the third identifier is the firmware:
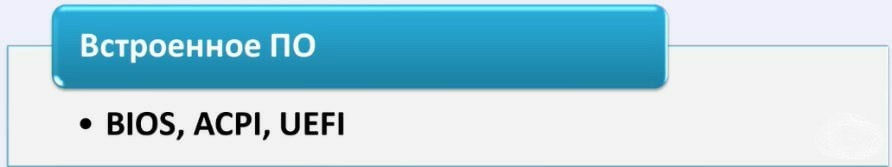
Firmware is mostly specific to the motherboard, but can also be built into your other hardware. In this case, it is simply a BIOS that allows you to read 16 bits.
ACPI tables - tables for your power supply and UEFI. UEFI is actually an upgraded BIOS, and what many of you are using.
Let's move on to our next picture. Operating system:

This great method of tracking users also has 3 main groups of identifiers.
Assignable static ones :
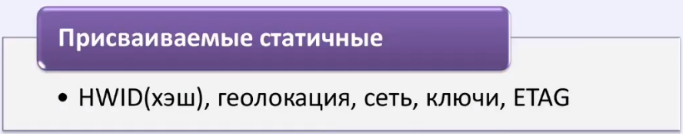
Assigned static identifiers are identifiers that do not depend on the equipment itself.
The first identifier is an identifier that you have probably encountered for a very long time. This is an HWID (Hardware ID), which itself is just a hash function.
The second identifier is the geolocation identifier.
The third identifier is the network identifier.
The fourth identifier is keys that may be present in your equipment.
Well, the last identifier is the ETAG identifier . We will move on to this identifier in more detail when we consider the problem of telemetry a little further and how surveillance of you is organized.
The second group of identifiers are created static identifiers :
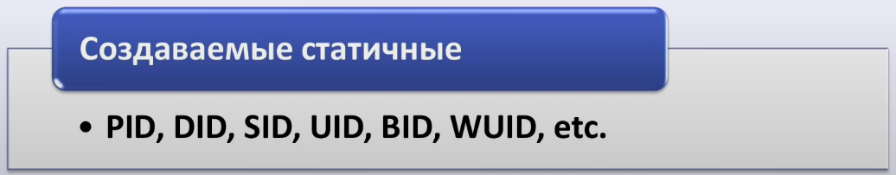
What does it mean that identifiers created are static? Generated static identifiers are identifiers that are created when you install your operating system. There are a lot of them: Product ID, Device ID, Secure ID, USER ID and so on. In total, we can count more than 100 such identifiers in operating systems, each of which is unique for the operating system installation session. After you have installed the operating system, it always remains with you.
And the third group is session identifiers :
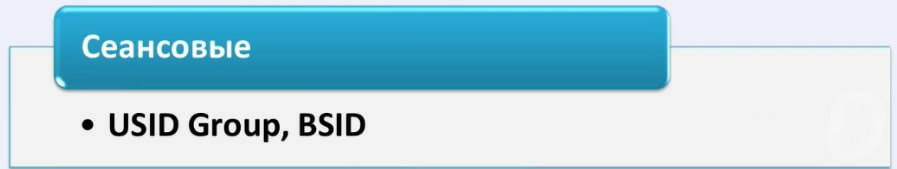
Operating system session identifiers are generated during PC startup. In other words, you start the computer, you have a session, and during this session the first group is formed - this is the USID identifier.
The second group of identifiers are BSIDs. BSIDs are identifiers for your current browser session.
Let's move on to our next picture:
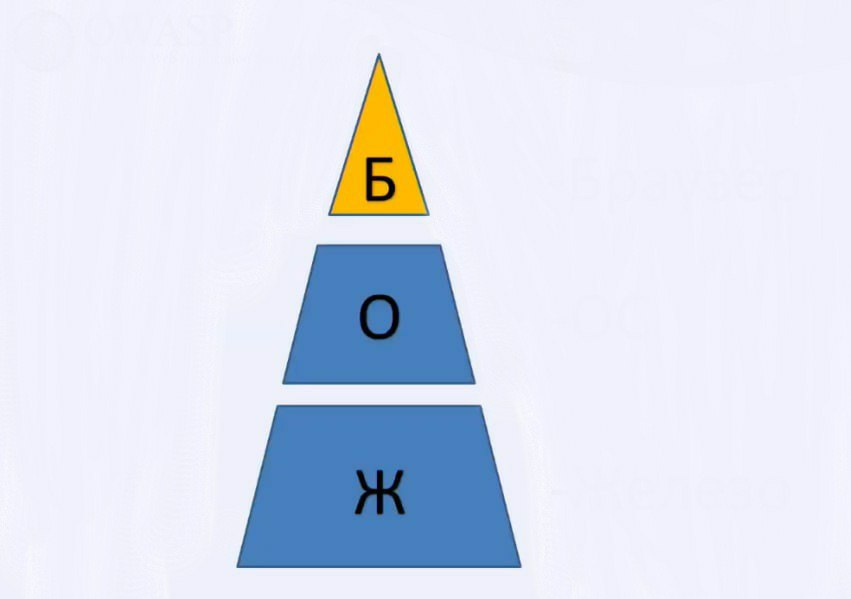
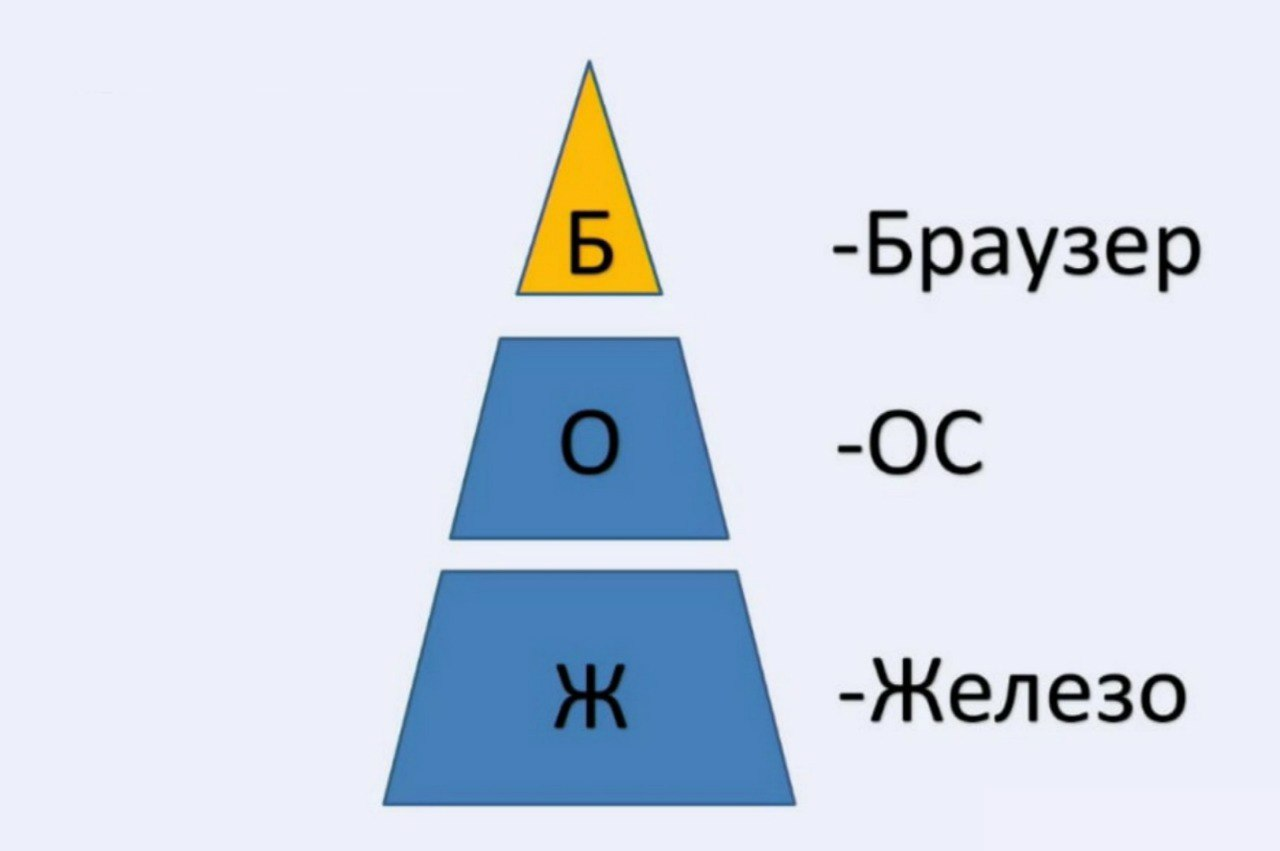
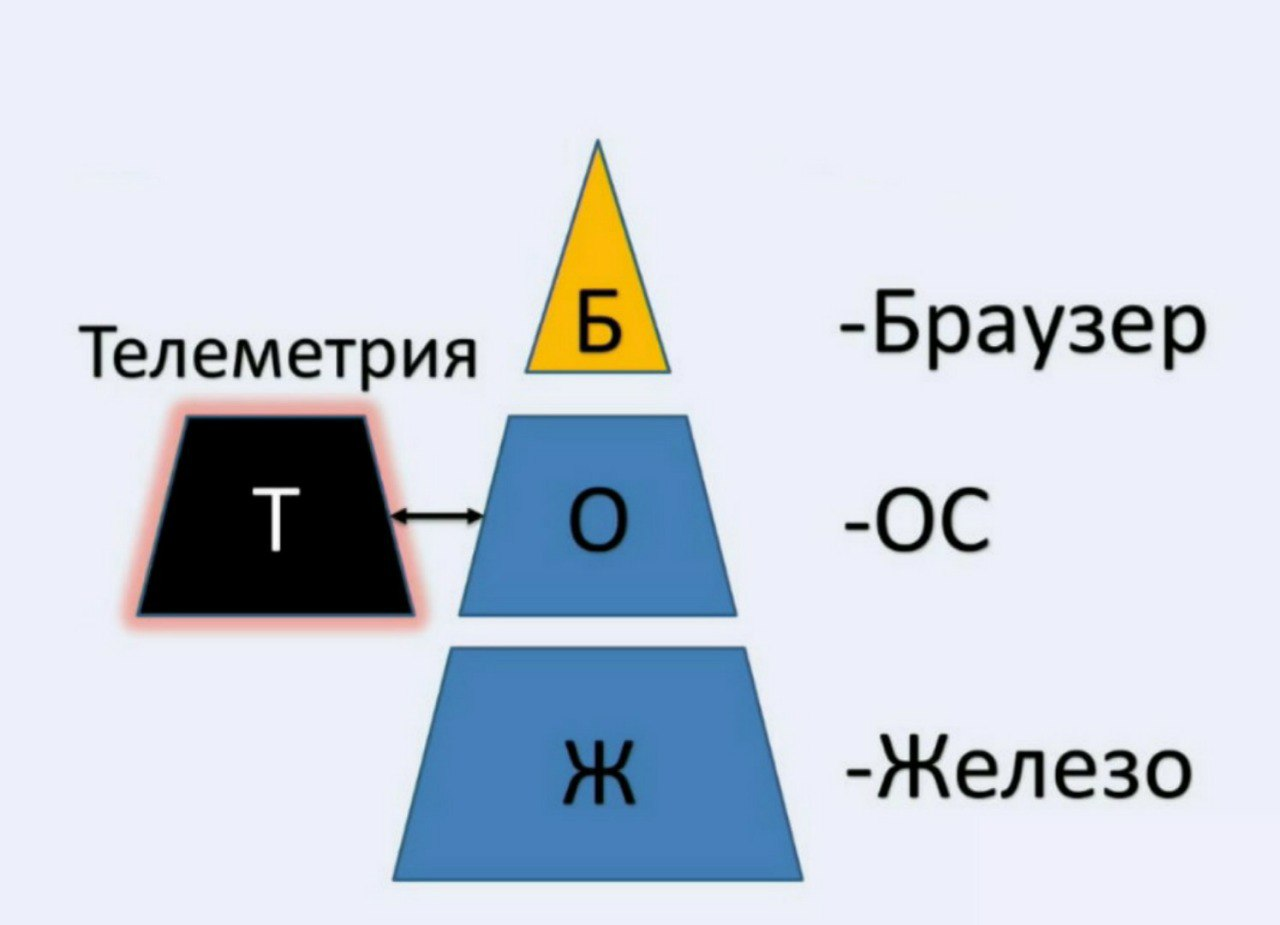
We will present them once again in the form of such a small pyramid.
At its core is your hardware. In the middle is your operating system. And at the very top is your browser - something that will identify you on the network, because not all parameters of the operating system can be obtained through a browser, and not all parameters of our hardware can be obtained in the same way through a browser, but these parameters have a dependency. The first dependence is that when you log on to the network, the browser settings depend on your hardware. Our second part is the identifiers of your operating system, which, when you log in, have a dependency and are transferred to your browser, in which you can be identified:
Why do this at all? Why does anyone need this?
The point is that each of you is a bee.
Why? Because she doesn't understand that a beekeeper exists, she just can't understand it. She doesn't have enough brains to understand that there is a beekeeper. The bee has only her world, she has only her task.
The same goes for the average user. When he enters the network, he thinks only of himself. He doesn't think about how the system sees him. He doesn't think about what they can do to him. But in fact, each user is just a wallet on legs , even without legs - on the network. That is, each of you is a person - a wallet to whom you can sell a product, service, information. But! If you don’t buy a product, service, or information, then you can be sold as traffic and get money from a completely different company.
Your hardware passes information to your operating system, and the operating system already passes this information to your browser. This allows you to track each of you with incredible accuracy, almost 100%, for every action you take.
What is a browser anyway?

Let's take a closer look at absolutely all of the above.
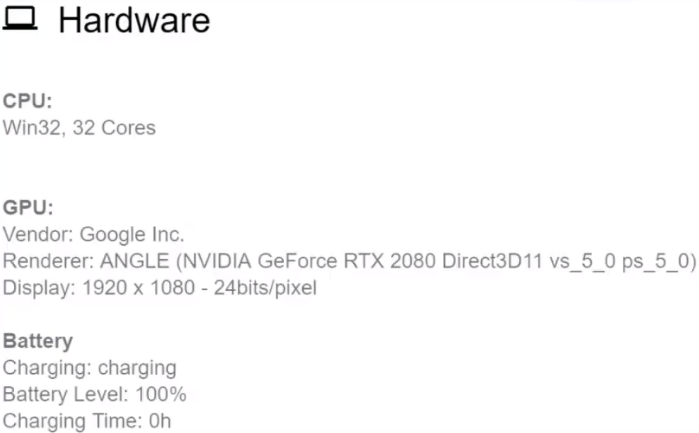
In the picture above you can see that it is possible to look at your processor, not of course find out its brand and so on, but it is possible to find out the number of cores.
The second part is your video card. By your video card, by the string parameter, you can find out which video card you are using.
Well, actually the third parameter is the battery. It applies either to mobile devices or to laptops, tablets, and so on.
How sites see it:
https://webkay.robinlinus.com/

Obtaining information about the speed of your processor and whether the information you provide is reality can be calculated using a very simple technology, when the user is provided with a java script with a very large data parameter, upon execution of which its speed is calculated and, accordingly, it is possible to obtain information about the approximate performance his computer. Accordingly, you must understand that when performing the same operation on a 2-core, 4-core, 8-core, 32-core processor, the results will be different.
Test how sites see it:
http://jcarlosnorte.com/assets/ubercookie/

Font imprint. At first glance, you might think that no one is paying attention to him. Why is this even necessary? It would seem that we have some fonts installed on the system. Let's look at them in a little more detail:
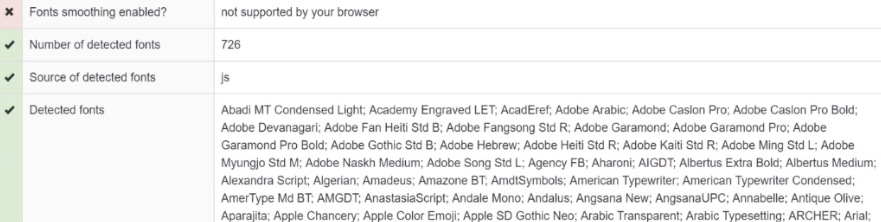
Fonts installed in the operating system allow you to identify your system during its use. In other words, if you take an operating system and just install it, you will always have the same set of fonts. If you additionally install Adobe Pfotoshop or some other program into this system, the set of fonts will change. Using this set of fonts, you can also identify a user of a virtual operating system, a user of a new operating system, or a server user.

This topic is more for layout designers. It allows you to easily identify your browser settings. In fact, this is what they look like:
Here, to say something unique or a principle by which you can be identified is, well, unlikely.
Check how sites see it:
https://browserleaks.com/rects

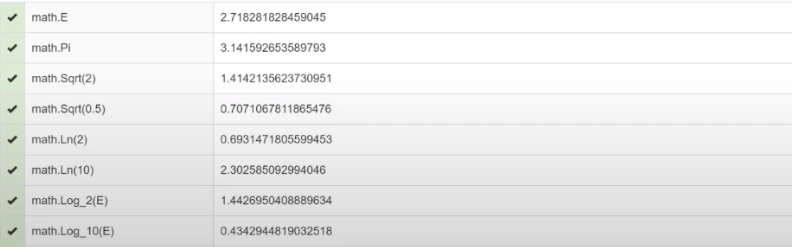
Our next parameter is Math JS . This is an option for processing your java scripts, which are purely browser-dependent. It seems that the parameter is absolutely unimportant; it can be changed simply by simply changing the browser. But at the same time, if you use some software like changing the User Agent, if you change your User Agent in the header, but do not change the Math JS parameter, then the entire change of your User Agent can be identified, and you can also identify your real browser. This is how it happens:
And the fourth parameter. A parameter which, again, is purely software dependent. This is your browser history :

In fact, your browser history can be obtained using non-cookies. We all know that there is an http only flag that prevents other sites from reading your cookies. In other words, all methods regarding some kind of stuffing of cookies and so on are complete nonsense that they want to instill in you.
But many sites recognize and see what you visit. Many sites can look at your browser history, whether from a mobile device or from a desktop computer, it doesn’t matter. The option to get the browser history depends on the history. I'll tell you why - getting your browser history is an extremely simple option. The fact is that when you go to a site and it is saved in your history, the styles of the links on that site change. In this way, you can identify what sites you visit, you can identify what porn you watch, you can identify what you do online, not to mention the same search queries in the same search engines.
This is something that many users try to replace, but in fact they do not always understand how to do it correctly and what it depends on. What is an antifraud system? The antifraud system is formed from two words - “anti”, that is, against and “fraud”, which means fraud.
Now, in our time, go to a butcher shop and pick up a pig's leg there, approach any girl on the street with a pig's leg... They will just send you away. But it satisfied the conditions before, why can’t it work now? The situation has changed. Girls are one of the simplest, but at the same time the most difficult option for working with anti-fraud systems. One of the simplest because you seem to know how to deal with us, but at the same time one of the most difficult, because you can only find out how we work if you get our brains. And without this we will make a brain for you))).

You can approach her, but you don't know what she wants. Let's assume that she herself doesn't know what she wants. You walk up to her and say, "Hold the pig's leg." Maybe she'll let you in, maybe she won't. You will come up and say: “I have a big penis . ” Maybe she'll let you in, or maybe she won't let you in. You will approach her and say: “I have a lot of money . ” Maybe she'll let you in, or maybe she won't. What is the point? The bottom line is that you can never figure out what's going on in any particular girl's head.


Your height, arm length, leg length, head size and everything else. This is your foundation. Just like your computer hardware will be your foundation. Then on this hardware you apply the operating system of the history of this user and his education. And at the very end, you put money on this operating system. Because if you are not interesting to the antifraud system that wants to cooperate with you, then it will not cooperate with you. Therefore, money can be an identifier of your solvency.
If, for example, you have turned yourself into an anonymous person. We got up in the morning, went to the computer and sat there anonymously. You downloaded a bunch of programs, turned on the VPN, passed the traffic through TOR, everything is fine with you, you are sitting and should be accepted directly into anonymity, and then you will go to rob banks. But here again the balaclava principle comes into play. The principle of the balaclava will be that in fact you are moving from the category of a user who can be sold, to the category of a user who is uninteresting and even potentially dangerous .
With any additional anonymization on your part, first of all, you may not be of interest because if you have learned how to defend yourself, then you are no longer suckers. Just a little bit, but no longer ordinary suckers, just a little bit of everything. And if you are even a little bit more than ordinary suckers, then selling you some kind of product or service won’t really work. Or, you can move into an even worse category, this is the category when you are not just insolvent , but when you are potentially dangerous . If you are trying to protect yourself, then, according to the logic of antifraud systems, you have the prerequisites to protect yourself, which means you can be potential scammers. And not only will you not bring profit to this company, but despite your good position, you can also harm it, you can steal money from this company.
1 of the most advertised is the Canvas imprint. What kind of print is this? Canvas technology dates back to 2006, when it was decided that loading pictures or forms into the client’s browser was not effective. It is much easier to give him a script that will build this image on its own on the user’s computer. The Canvas fingerprint is currently the most advertised and its essence is that this fingerprint depends on your hardware, your operating system and your browser. At the same time, three dependencies that identify you on the network as a user of a specific device.
See how sites see you:
https://browserleaks.com/canvas
Our next fingerprint is a WebGL fingerprint:
WebGL technology is a technology for creating 3D graphics on your computer. It is based on the same Canvas technology, but if you can imagine Canvas as a regular 2D sheet of paper, then WebGL technology allows you to build 3D images. These images allow you to play games, watch videos, and so on. It’s not specifically related to video, but specifically to the user’s visualization process. What a WebGL fingerprint looks like:
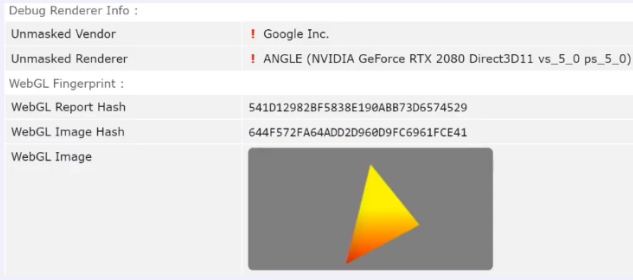
The WebGL fingerprint is now in front of you, above in the picture. It has only four parameters.
The first parameter is your Vendor. The vendor is the one who produces your equipment.
Next comes Renderer, that is, the device that will produce your graphics. In this case, the graphics manufacturer indicates an NVIDIA video card with shaders version 5.0. And for the WebGL fingerprint, we can see two unique hashes:

The first unique hash is the WebGL Report Hash.
WebGL Report Hash is a parameter that you can change yourself, without any special effort. You just need to change any string parameter in the vendor or in the renderer. It is used only to receive a report on the health of the system. And it is not used in any way in user identification systems.
Much more interesting is the second parameter, which is called WebGL Image Hash . How do we get it? We get it in the form of this figure:

In fact, this figure is not flat, but three-dimensional. That is, this figure is formed using vertices, lines and color fill, where again your Canvas is used.
Let's move on. WebGL Const :
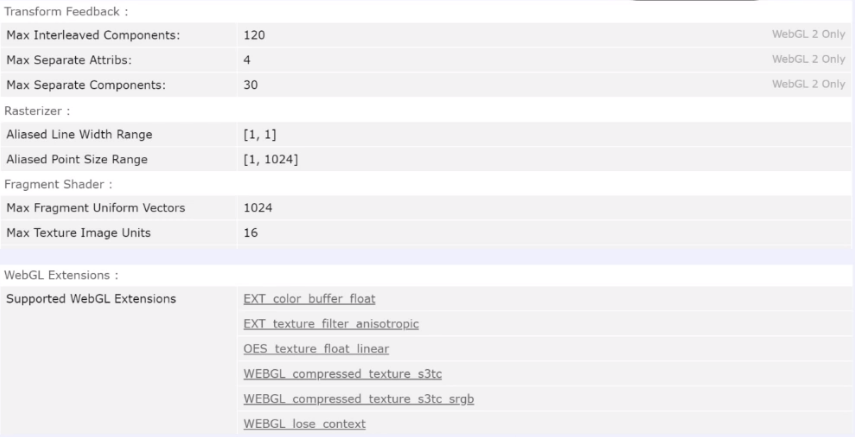
An extremely interesting parameter that is more important than anything before. WebGL Const allows you to define the graphics processing parameters of your video card. When you try to maintain your anonymity and impersonate another user, you simply do not pay attention to it. Well, what kind of uniqueness can there be in the value 1024? What kind of uniqueness can there be in the value 16? And so on. In fact, there are 168 WebGL Const parameters. These parameters provide information and identification about the video card. In other words, if you take and write a string parameter in your browser - just a text parameter you register your video card manually, for example GeForce, when the processing parameters for your graphics belong to the same Nvideo, then you will not be able to deceive the system.
Checked right there:
https://browserleaks.com/webgl
Another interesting WebGL parameter is Extensions :
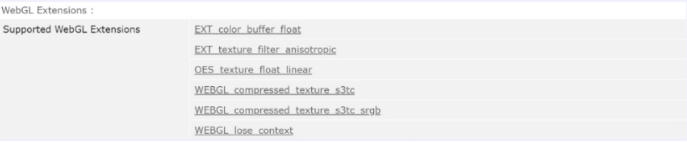
In other words, these are small routines that are supported by your video card. And here, in exactly the same way, we come to the point of identifying the user and his video card due to the capabilities supported by this video card. The following AudioContext parameter:
The AudioContext parameter is used by absolutely all major resources and sites. This parameter allows you to identify the user by checking the audio processing parameters. In other words, your audio card and your audio settings again allow you to be identified as a unique user. This is what it looks like:
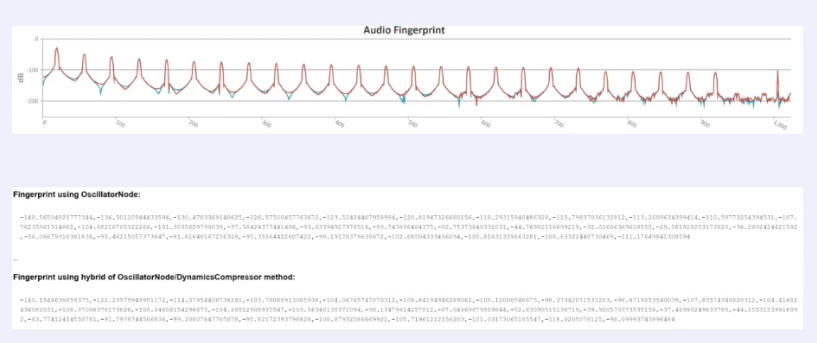
Above we have a purely visual interpretation of it. Below we have its real interpretation using two different methods of obtaining it. As you understand, your audio card and its audio card settings are an excellent means of identifying you on the network.
You can check how websites see your fingerprint here:
https://audiofingerprint.openwpm.com/
Ubercookie fingerprint:
The Ubercookie setting was created by an independent researcher named Robin Linus. This parameter is a clear representative of adjacent codependent imprints. It is a dependence of the audio fingerprint and the ClientTrack fingerprint - the block boundary fingerprint that we talked about earlier.

This fingerprint is actually unique, but replacing it is quite simple. We just need to change the scale of our browser and that’s it - it’s spoofed.
Check how websites see us:
https://ubercookie.robinlinus.com/
The WebRTC parameter migrated to us from Internet Exproler . This browser had ORTC technology . What kind of technology is this? In fact, this technology was not aimed at identifying users in any way; it was created for just one purpose. In order for Internet Exproler users to be able to stream video and streaming audio between browsers. That is, 1 person from Internet Exproler , without Skype and without anything, calls another person from Internet Exproler , and everything is fine with them. After that, due to its lack of widespread use, this technology mutated a little. It mutated into WebRTC technology , which we have seen in our browsers since 2013. This technology also still allows us to talk between our browsers. From Google Chrome, call someone on Mozilla, for example, on social networks, VKontakte, Facebook and somewhere else. WebRTC technology is based on the fact that it is necessary to obtain data about our network connection in order to establish the most powerful and best connection. Therefore, WebRTC technology also makes it possible to obtain our real IP address. If we have several of them on our computer, then it is possible to use this technology to obtain all the IP addresses that are on our computer:
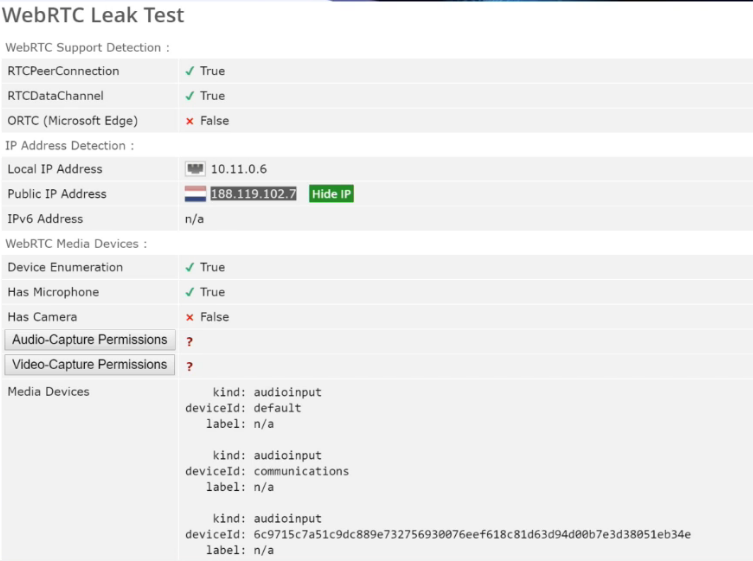
Also, WebRTC technology , since it is used for video and voice communications, allows us to obtain the id of our devices, communication devices, microphone devices, virtual helmet devices, camera devices, and so on, in the form of unique Device IDs. Even our speakers.
How sites see it:
https://browserleaks.com/webrtc
Let's move on:
Our very top part is part of our browser. That is, through which the parameters go into the network, those parameters with the help of which we can be identified and, accordingly, in the future we can either be sold, or a decision be made about whether to allow us to take a certain action or not to allow us. In fact, this is used by the digital needs market, and is used very often. Oddly enough, many will think that probably only terrorists or sophisticated hackers and carders know what I’m telling, but in reality, no. The most basic consumers of this market are ordinary users who simply make money from it. And they make money from this in the following way; I’ll give a few simple examples.
For example, some large poker site gives money to the first client, that is, this is called a welcome bonus. When you come to the site for the first time and the system does not recognize you as a person who has been there before, it gives you a bonus. For example, you deposited $20 and were given another $20 extra to play, you cannot withdraw it in any way, you can only spend it on the game. But a person who knows how to emulate the identifiers that I described above does the following manipulations: he creates 5 accounts for himself, deposits $20 into each of these accounts and receives a $20 bonus into each of these accounts. What will he do next? He will put all his 5 accounts on 1 poker table and lose the money to himself, and then withdraw it in double amount.
It’s the same issue with Forex. Users there are also given a bonus for their first deposit. For example, I deposited $200 and received a $200 deposit on top, for a total of $400. Next, I create a second account and do the same. But now I can’t withdraw them in any way, the system won’t let me do it. How can I win now? One account is betting on a currency increase, and the other is betting on a decrease, and one of these accounts will win in any case, thereby I will increase my capital by 2 times and calmly withdraw it. It's the same with bookmaker companies.
The same situation with Google. There is an even more interesting situation with Google. That is, for example, each user can create a high-frequency query, for example, he will ask the query: “Casino”. In order for him to place an advertisement for his casino on Google, he will spend approximately $4 for each user who follows his link. He creates several accounts for himself, on each of these accounts he creates, for example, a “site selling slippers,” but he no longer pays Google $4, but only 10 cents for each person, and then he takes and dumps all this traffic on casino with an affiliate program for only $1, but he is already in 10-fold profit.

What do I want to lead you to? I want to lead you to the fact that in fact, the user identification technique is used absolutely everywhere in our work on the network.
Our next picture:
Your operating system also has a hidden part that each of you has heard about, but in fact few people understand what it is responsible for and what it looks like. This is telemetry :
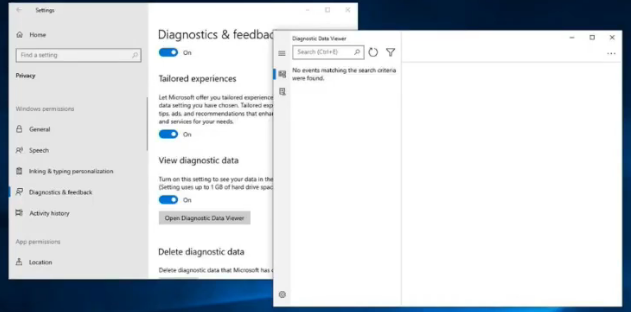
Those who use Windows 10 and do not kick the corpse of Windows 7, then they probably already understand that such a magnificent Trojan is practically impossible to find. What's the point? I have already repeatedly raised the question that the Windows 10 operating system monitors users, monitors each of you. That is, at first she tried to log even our keystrokes, at first she tried to identify us as a user using all the maximum possible parameters. But a little time passed and the US government pressed Microsoft a little and said don’t do this anymore, do it the right way. Then Microsoft made the next knight's move, it said that telemetry is one of the most important factors for software development, for understanding the issue of errors and for understanding what is happening on the user's PC. But did it help us? Each of you, if you have heard about what telemetry is, can simply look it up on your PC. This is done simply through banal operating system settings:
You can additionally install an event viewer from the Microsoft Store and with the help of this event viewer an absolutely interesting, new world of what your Windows 10 operating system sees about you opens up to you.
Well, for example, as soon as you install the Windows 10 operating system. Only you have installed it , as soon as you move on to creating your user profile. You see this when your purple windows 10 reinstall screen changes to blue. After this there is a wonderful connection with telemetry, and then data is generated about you, specifically about your PC. After which this data is exchanged with Microsoft servers and we have a wonderful identifier called ETAG:

The ETAG ID will identify you as an authorizer and will allow future work to be done with you. It will again allow you to be spied on, and will also allow you to install additional software, even if you do not want it, and will collect information about you, for absolutely legal purposes, of course. Microsoft cares about us very much.
But if we move a little towards telemetry, then telemetry currently has 68 unique parameters that are created in the operating system. I have selected several of them, the simplest ones which identify purely groups:
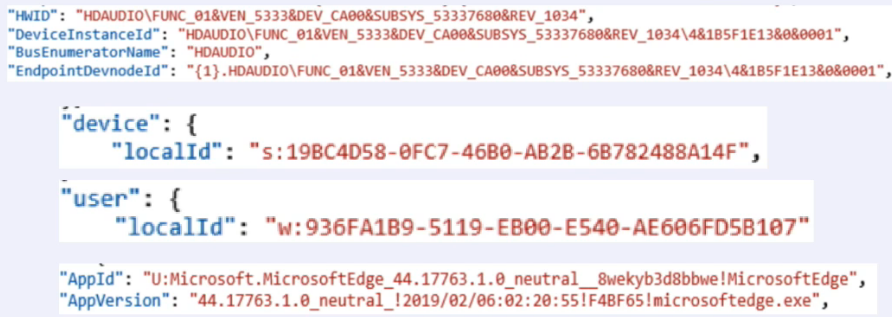
The first group at the very top is the hardware identifier group. Whatever piece of hardware you install in your PC, be it an audio card, a video card, a virtual reality headset or anything else, information about this will leak to Microsoft:

Second part. Device ID. The Device ID part is formed based on the configuration of your computer during the installation of the operating system. It gives out your unique ID with which you can still be tracked:

The third part. User ID :

User ID, maybe some of you know, has an absolutely clear abbreviation on your PC called SID (Secure ID) . The SID is the main one for applying access rules in the operating system. Rules for accessing folders, the registry, and so on. This ID is generated when you create a user and when you install your operating system. Changing it is possible only in three ways.
The first is simply reinstalling the system.
The second is to create a new account.
Third, there is special software to replace it.
And our third group is software identifiers. Regarding software identifiers, in this case I have the identifier of our Microsoft Edge browser shown:
And if we move a little further in the future, I would like to show one interesting point.
Surely many have heard that there is a Tor browser. It's all great, it's all anonymous, it's all great. With the Tor browser you can organize sales of the new Hydra. But pay attention here:
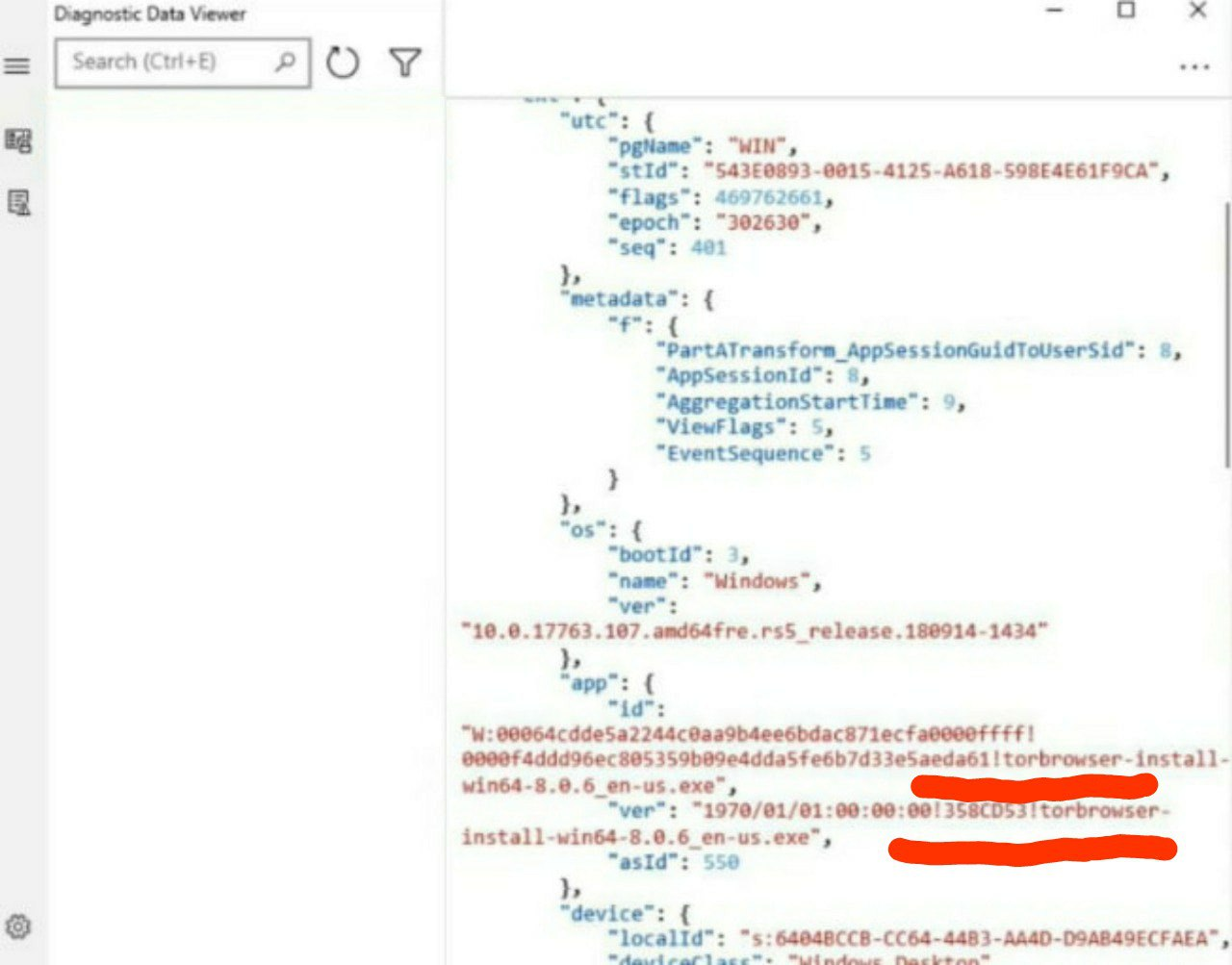
As soon as you download the Tor browser, or some other browser anti-detect, or some other anonymity tool, then, remarkably, information about this will leak to Microsoft. Now think about your anonymity when using Windows 10.
Let's move on. Next point. Our operating system and our browser have another group of identifiers called extra-browser identifiers:
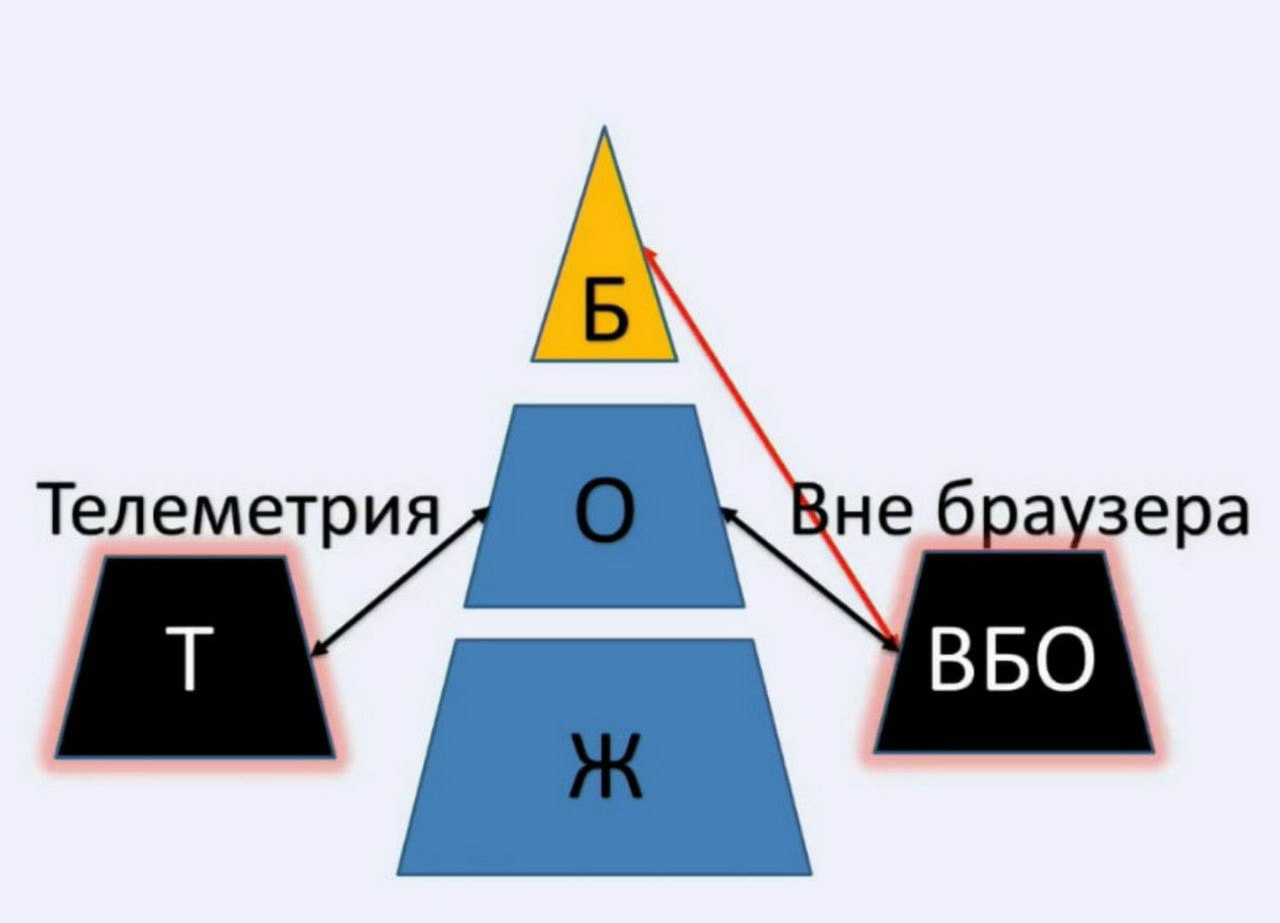
Off-browser identifiers allow us to be identified beyond the browser we use. And even if we want to use some super-anonymous, super-cool and super-super-incomprehensible browser stuffed with us and offered by hucksters, we will still be visible.
We seem to have already figured out how we can be identified, but in fact, in addition to all the software that we can use to hide our identity and in order to again emulate our identity, we need to observe several more interesting parameters. These settings are called out-of-browser fingerprints. Out-of-browser fingerprints are fingerprints that cannot be changed using the browser. Maybe, of course, someone will come up with something interesting, but at the moment I have not seen these technologies.
What it is?

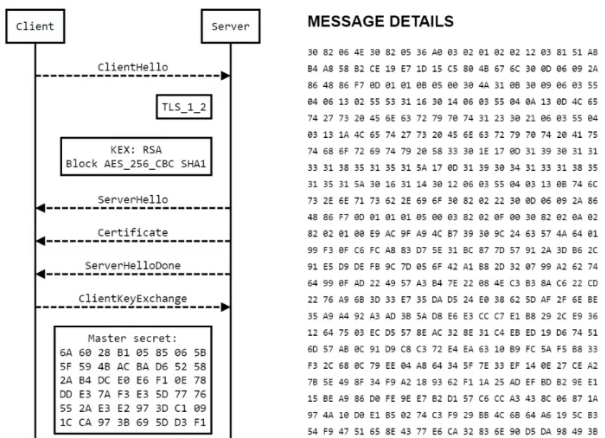
Our first fingerprint is a TLS fingerprint. What does this mean? Every time you go to a site that has https in the address bar, this means that the site is using a security certificate. It can use SSL version 1 security certificate, SSL version 1.1, SSL version 1.2, or it can use other versions. What does this allow you to do? On the part of anti-fraud systems, this allows us to be identified when using an SSL certificate of the third version or another TLS certificate. In other words, every time you visit a site that uses TLS certification technology, it is possible to identify you outside the browser. If you change all your fingerprints, if you change everything possible, then the TLS certificate that remains on your PC can be used to identify you. This is the first out-of-browser fingerprint. It looks like this:
You can study this topic yourself if you want. I have conveyed the essence to you, and then you must decide for yourself how to use this essence.
Let's go further MTU/TTL :

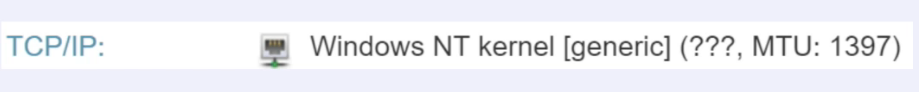
When you go online, you have your packet size and you have the lifetime of your packet. Those who have worked with nmap , which I wrote about in part 5 of the article on Kali Linux, have no questions at all, they all know what it is. That is, in other words, determining the user’s operating system by its IP address. Determining an operating system by IP address is not a 100% accurate indicator and many people use it in different situations. Someone may have a VPN , someone may have some kind of router on which the network is built, and so on. The most basic point is that you cannot change this parameter on your PC. Whatever you do, that is, if your PC is the first entry point into the network, then you can change it, you can change the packet length, you can change the packet lifetime and you can disguise yourself as a different operating system. But if you use a VPN , if you use a proxy, if you use some other intermediary to log into the network, then you can change this parameter only if you are the owner of the intermediate point. If you use a VPN , then be the owner and only then can you change this parameter.
You can test it yourself: https://whoer.net
As you understand, sites have the ability to determine your operating system. Is this critical? When bypassing antifraud systems, this is not a critical parameter because we have a set of parameters, that is, what we take, what we provide to our antifraud system is a certain community, area.
Go ahead. Flash Parameter:

The Flash option is already obsolete. Everyone is familiar with Flash player and Flash player has an interesting feature of two types. The first is to get all the information about your PC. The second possibility is storing information about the sites you visit not on the user’s computer, but on macromedia servers. Flash technology is already morally outdated, even YouTube switched from it a long time ago, they abandoned the use of this technology in favor of html5 . But still, some sites, for example the same bookmaker companies that conduct online broadcasts, use flash technology. And this technology has a good gradation by version. Before version 10.0, it is possible to change the parameters of our PC. After version 10.0 it is not possible to change the parameters of our PC. Therefore, if you use flash, then it is possible to track information about all your hardware.
Further. Java Technology:

Java technology is very interesting, but it is of interest mainly to those who use the banking client. Java technology allows you to get information about all your hardware, as well as what you have inside your PC. Do not confuse this technology with java script .
The following is our FuzzyHash technology :

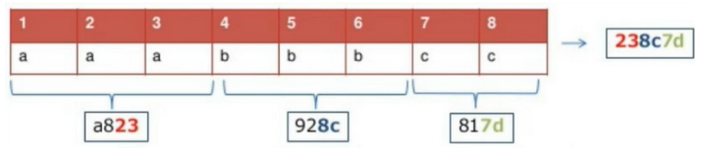
Hash phase technology allows you to ignore changes to your fingerprints. If you want to be very well anonymous, if you use any means of anonymity, then it is possible to roll back these means of anonymity and find out who you are. Pay attention to the picture:
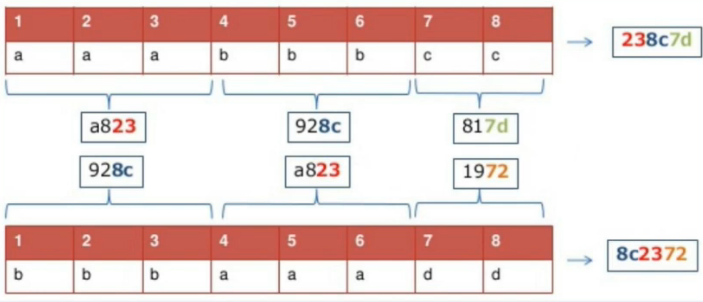
At the very top we have some kind of imprint, let it be the Canvas imprint . Our fingerprint has certain parameters. Here they are:
We also have a second imprint that occurred, was produced, was created after we used the means of anonymity. Here he is:
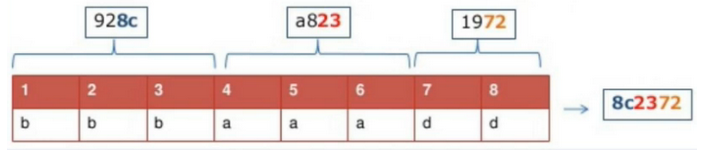
What could happen next? Phase hashing technology or free hashing technology allows you to identify a change in the original data. Imagine, Ivan Ivanovich Ivanov lives at Kontroskaya 5, apartment 68 and his phone number. What will happen if Ivan Ivanovich Ivanov changes his apartment from 68 to 69? That's it, the hash has changed, it seems like there is a completely new person, and in the same way in the browser fingerprints, it seems like a completely new person, but in reality this is not happening. Because we can track changes in the hash itself, in the data from which we get this hash, and lead this to the point that we can identify changes and identify the basis. In other words, if one of you wants to change, for example, your Canvas , someone else wants to change some other parameter, then it is possible to recognize this person if the changes do not exceed 30%. 70% remain static, 30% free hash. If Ivan Ivanovich Ivanov changed his apartment and became Dmitry Ivanovich Ivanov, then we can still find him.
Go ahead. Now, it’s probably not very visible here, but I want to tell you. Technology for obtaining Canvas . The same Canvas print that you can see here:

What exactly is a Canvas imprint? Fingerprint Canvas is a construction of an image on your PC. This is a pure client site script. Look, we have our pixels. Let's imagine that this is the reference image that I posted above. What will happen next to this reference image? This reference image will be converted to binary code to be a Canvas fingerprint. It will then be converted to a Base64 hash. And in fact, we can take 1 of the pixels, change it by half a tone, and we will have a completely different binary code, and from this completely different binary code we will have a completely different Canvas print . But there is a purely statistical problem here. I'll explain what it is.
Imagine that each of you is the owner of Google, everything is fine in your life, you have a lot of money and so on, but you have no brains. You have statistics. And these statistics, thanks to the fact that you, as the owner of Google, have already reached into the pockets of all the people in the world, you already know information about all the people in the world. You are actually not as simple as you seem, you already know everything about all the users in the world. So, you used the simplest method, you didn't invent artificial intelligence, you didn't do anything, you just looked at all the other people in the world. Do you know what it's called? And this is called statistics. You sit and watch who comes to you, and you don’t just sit and watch, you also write it down. You take and write all this down for each person. And then what do you get? Then you get awesome statistics. You get statistics of your users. You understand who comes to you, you understand their identifiers, you understand their fingerprints. What happens if you take these statistics that you make and just look at the systems, for example, of protection from you. There are many systems, they are called Google protection systems, you can find them on the Internet. You will see that it is impossible to protect yourself from you. And I'll tell you how. Here is this pixel and many other pixels:

For example, in forming a fingerprint of the same Canvas, security systems can hide the user, but not hide him in front of you (the owner of Google). How does this happen? When a user uses any software to hide, in order to not identify himself, then this software uses the simplest and most stupid method. This software selects a random number of pixels from our Canvas image and changes their color by as little as half a tone. For example, it selected 7 pixels, 15 pixels, 20 pixels, and changed the color to half a tone. Has the binary code changed? Changed. The hash has also changed. It seems like everything is fine, and it seems cool and you can work, right? Everything is great.
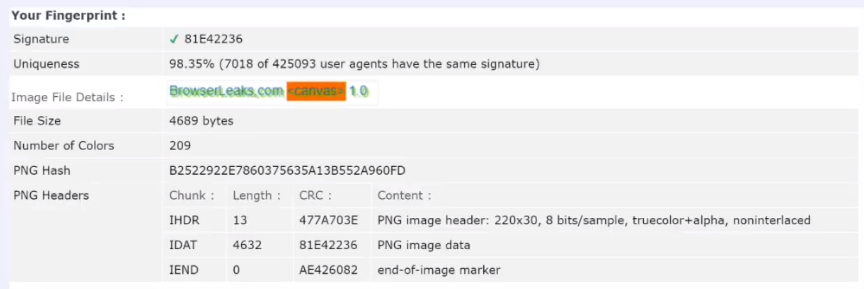
Look here. A striking example of this. Pay attention to the second column Uniqueness , uniqueness. Uniqueness 100%:
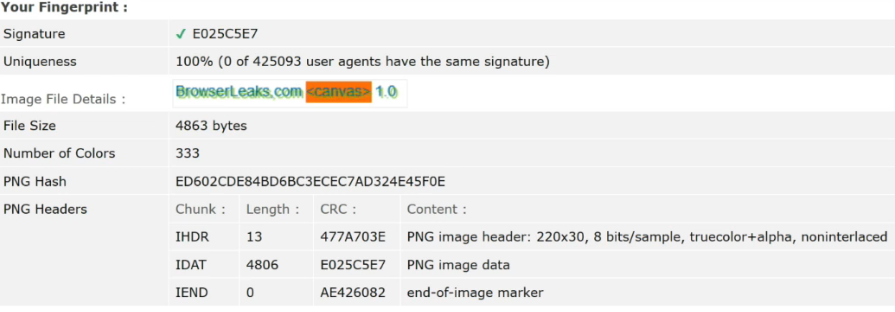
At the moment I am showing an example using one of the most adequate tests at the moment:
https://browserleaks.com
But if we pay attention to this parameter:
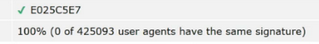
0 users out of 425093 about whom information was entered. 0 users have this Canvas fingerprint. Now let's imagine all this in the size of Google. What will happen if we use such a Canvas fingerprint ? This will be an example of how Google will identify us among all its users. And you and I are returning again to where we started. We return to the balaclava. It seems that we have defended ourselves, it seems that everything is fine with us, it seems that everything is fine, we are walking down the street in a balaclava, but again we will be identified as an asshole in a balaclava . And no other way.
What is the sacred essence? It's that we can't just make the changes we want. So it occurred to us, we want to make changes to Canvas , and just like WebGL , audio fingerprint, UberCookie fingerprint , and so on, we can combine all this into one single database, where, in case of a banal mismatch of these parameters, we can already anti-fraud system, take this user under control at least.
Go ahead. Keyboard :

Well, who's looking at the keyboard? What's there to worry about?

The essence of the keyboard is very underestimated by many in identifying users.
How? The fact is that when you enter any information on your keyboard, there are at least four different options for identifying you.
Let's imagine a login and password input field on Facebook:
We will enter your login. How can we introduce it? We can enter it manually. Cool? Yes, everything is great. We can enter it using the clipboard, we can simply paste this field, or we can paste this field using autofill. And the best result for bypassing anti-fraud systems will be precisely changing our input field in the direction of autofill, but there is another interesting hidden meaning when the user tries to pretend to be a different person. Take for example, someone look at your keyboard. Your keyboard has a qwerty layout. And imagine that you want to emulate a user from the UK, for example. You log into the same Google, Paypal, Amazon, and so on, wherever you enter your data. You enter your email first. What will happen on the English layout as opposed to the American one? It seems to be the same language, but when you try to enter @, you will not enter a dog, you will enter a number sign. What will happen next? And then you press the erase key, delete this number sign and enter the dog accordingly, either manually from the clipboard, or change the layout, but this will already be a signature action to determine your real layout.
Or if, for example, you wanted to be French, you wanted to emulate a Frenchman. Regular users have a qwerty layout, while the French have azerty. When you simply enter, for example, gmail, then the letter a - you will enter a comma, after which you press the erase key and press the letter q on your keyboard because it corresponds to the letter a. And this will already be a signature action to determine your real physical keyboard layout. And even at this absolutely seemingly simple stage, just a keyboard, it is possible to identify you as a real native speaker.
You can test it here: http://ahtcx.github.io/layoutline
Today we will begin to examine the topic of fraud, “human trafficking”, as well as surfing of ordinary people and everything that happens when you log into the network. But before that, I will tell you a little story.Today's topic will be quite specific for several reasons. It affects each of you when you don't even know it. Let's talk about online fingerprints and how companies have been selling people for quite a long time.
2019 Let's go back 4 years. I was offered to participate in a top award ceremony that is held every year in Germany. This is an award for the best specialists in IT. One of the degrees of this award was dedicated to information security. A large company organized this competition and chose me to work in this field. At first I was still hesitant, since there was no special meaning and the reward was small. In the end, I thought about it and agreed. Everything was great. But at one fine moment I realized one interesting thing for myself - managers took it upon themselves to evaluate information security. After I told them what I thought and what I want to present to you now in this post, do you know what they did? They declared me an accomplice of terrorists. After that, in the direction of one of the top IT companies in Germany, a small thought crept into my mind - are they idiots or what? How can people who do not understand anything in their field of activity evaluate someone? They were unable to do this, and then simply simply removed this category from their awards. It’s easier for them to reward some bespectacled nerd who sits and codes useless games or a layout designer, it’s easier for them to do what they do.
Therefore, we will talk to you today about how each of you is sold and used.
But before that, remember. Either they use you, or you will use all these big systems yourself and make money from them.
The first thing I would like to start with is. Pay attention to the picture:

The principle of the balaclava. What it is? It's like Schrödinger's cat. He is both alive and dead at the same time. The balaclava is the same in every action you take online. You are doing things and not doing things at the same time.
Let's now leave the world of IT and enter the ordinary sphere of life and imagine that one of you goes out into the street and puts on a balaclava. Will you be anonymous? Yes, you will be anonymous. They won't recognize you. It is unknown who this is, some strange dude. But at the same time, if this strange dude in this balaclava walks down the street, then what will happen? People will identify this unknown and incomprehensible dude. How? They will identify him as an asshole in a balaclava. That's all. You walk and each of the people who are on the street will see you, will point a finger and say: “This is an asshole in a balaclava .” That is, you seem to have observed the rules of anonymity, your face is not visible, but at the same time you identify yourself independently due to those actions that you do not understand, that were imposed on you, in which you yourself are just a bug.
What does the balaclava principle mean ? For example, you want to bypass some kind of security system. In principle, the balaclava, you bypass it at the same time , the system does not see you, but at the same time you do not bypass it because the system sees you - for the reason that you are identified by your non-identification.
Let's move on to the next picture:

Whatever devices you surf the network from, there are several levels of obtaining information about you, I presented them in the pyramid above. The lowest and simplest level is the hardware level by which you can identify your computer, laptop, tablet, phone, TV, anything, any device with which you surf the Internet:

The next level is the operating system. This is what you use to surf the Internet. In other words, you need something to start your hardware. This is the operating system:

We will talk about the operating system in more detail, but I would like to return a little now to your hardware. Your piece of hardware has several parameters that can be monitored. You can see these parameters now in this picture:

There are three main groups by which you can be identified.
First, pay attention to Vendor ID & Device ID:

What is it and what does it mean? This means that every piece of hardware inside your PC, laptop, phone and whatever it is has two main identifiers. The first identifier is the identifier of the vendor, that is, the one who produced this equipment. For example, in the picture above I highlighted VEN_10DE in red - this will correspond to the NVIDEO company. The next Device ID
parameter , which we see as DEV_1E82 , will correspond, for example, to your video card, and it will also correspond to your sound card, or any other part of your PC/phone. These are called basic hardware identifiers and they are built into your hardware. As soon as you insert this piece of hardware into your computer, these identifiers go to your BIOS or to your UEFI so that your operating system, your PC, understands what was inserted into it. The second part is the hardware serial number:

A hardware serial number allows your device to identify itself beyond who made it, in addition to the model of that device. It also allows you to identify your specific device, your unit.
And the third identifier is the firmware:

Firmware is mostly specific to the motherboard, but can also be built into your other hardware. In this case, it is simply a BIOS that allows you to read 16 bits.
ACPI tables - tables for your power supply and UEFI. UEFI is actually an upgraded BIOS, and what many of you are using.
Let's move on to our next picture. Operating system:

This great method of tracking users also has 3 main groups of identifiers.
Assignable static ones :

Assigned static identifiers are identifiers that do not depend on the equipment itself.
The first identifier is an identifier that you have probably encountered for a very long time. This is an HWID (Hardware ID), which itself is just a hash function.
The second identifier is the geolocation identifier.
The third identifier is the network identifier.
The fourth identifier is keys that may be present in your equipment.
Well, the last identifier is the ETAG identifier . We will move on to this identifier in more detail when we consider the problem of telemetry a little further and how surveillance of you is organized.
The second group of identifiers are created static identifiers :

What does it mean that identifiers created are static? Generated static identifiers are identifiers that are created when you install your operating system. There are a lot of them: Product ID, Device ID, Secure ID, USER ID and so on. In total, we can count more than 100 such identifiers in operating systems, each of which is unique for the operating system installation session. After you have installed the operating system, it always remains with you.
And the third group is session identifiers :

Operating system session identifiers are generated during PC startup. In other words, you start the computer, you have a session, and during this session the first group is formed - this is the USID identifier.
The second group of identifiers are BSIDs. BSIDs are identifiers for your current browser session.
Let's move on to our next picture:

We will present them once again in the form of such a small pyramid.
At its core is your hardware. In the middle is your operating system. And at the very top is your browser - something that will identify you on the network, because not all parameters of the operating system can be obtained through a browser, and not all parameters of our hardware can be obtained in the same way through a browser, but these parameters have a dependency. The first dependence is that when you log on to the network, the browser settings depend on your hardware. Our second part is the identifiers of your operating system, which, when you log in, have a dependency and are transferred to your browser, in which you can be identified:

Why do this at all? Why does anyone need this?
The point is that each of you is a bee.
Why? Because she doesn't understand that a beekeeper exists, she just can't understand it. She doesn't have enough brains to understand that there is a beekeeper. The bee has only her world, she has only her task.
The same goes for the average user. When he enters the network, he thinks only of himself. He doesn't think about how the system sees him. He doesn't think about what they can do to him. But in fact, each user is just a wallet on legs , even without legs - on the network. That is, each of you is a person - a wallet to whom you can sell a product, service, information. But! If you don’t buy a product, service, or information, then you can be sold as traffic and get money from a completely different company.
Your hardware passes information to your operating system, and the operating system already passes this information to your browser. This allows you to track each of you with incredible accuracy, almost 100%, for every action you take.
What is a browser anyway?
In a browser, no matter what browser you use, there are three main groups of identifiers:

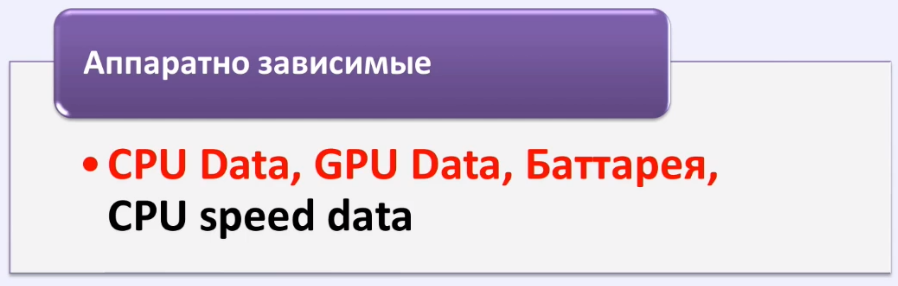
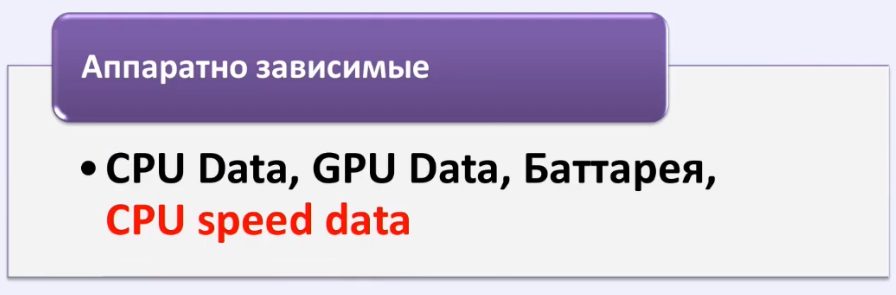
First. Identifiers are hardware dependent.
- CPU Data - information about your processor.
- CPU Speed data - information about the speed of your processor. Even if you replace this identifier, for example, you download some kind of substitution plugin for the browser, maybe you use something else - this will not help you in any way, because you can replace the performance that is checked when providing a java script to the user on a site with high load will still be visible.
- And the third is the battery . By the way, the battery is one of the very interesting identifiers, but we will get to it a little later.
Second part. Software dependent identifiers.
- The first software-dependent identifier is the font fingerprint . Quite an interesting fingerprint, it allows you to find out just the installed fonts. Who might need this? Well, some fonts are installed, what could be interesting about that? Stupidity.
- Block border imprint. Also, it’s like some kind of stupidity that doesn’t deserve any attention at all.
- Math JS . These are just your browser constants.
- And the fourth identifier is your browser history. Interesting point. Do any of you know that it is possible to retrieve your browser history even just by directing you to some link or resource?
The software and hardware identifiers of your browser include identifiers that almost everyone knows. If any of you don’t know them yet, we’ll look at them in more detail. They are precisely those sacred identifiers that allow systems to identify you on the network.The third part. The most extensive component. Software and hardware identifiers of our browser.
Let's take a closer look at absolutely all of the above.

CPU Data, GPU Data and Battery . Let's see what they look like:

In the picture above you can see that it is possible to look at your processor, not of course find out its brand and so on, but it is possible to find out the number of cores.
The second part is your video card. By your video card, by the string parameter, you can find out which video card you are using.
Well, actually the third parameter is the battery. It applies either to mobile devices or to laptops, tablets, and so on.
How sites see it:
https://webkay.robinlinus.com/
Go ahead:

CPU speed data is a rather interesting parameter:

Obtaining information about the speed of your processor and whether the information you provide is reality can be calculated using a very simple technology, when the user is provided with a java script with a very large data parameter, upon execution of which its speed is calculated and, accordingly, it is possible to obtain information about the approximate performance his computer. Accordingly, you must understand that when performing the same operation on a 2-core, 4-core, 8-core, 32-core processor, the results will be different.
Test how sites see it:
http://jcarlosnorte.com/assets/ubercookie/
Further. Software dependent fingerprints:

Font imprint. At first glance, you might think that no one is paying attention to him. Why is this even necessary? It would seem that we have some fonts installed on the system. Let's look at them in a little more detail:

Fonts installed in the operating system allow you to identify your system during its use. In other words, if you take an operating system and just install it, you will always have the same set of fonts. If you additionally install Adobe Pfotoshop or some other program into this system, the set of fonts will change. Using this set of fonts, you can also identify a user of a virtual operating system, a user of a new operating system, or a server user.
Next point. Block borders imprint:

This topic is more for layout designers. It allows you to easily identify your browser settings. In fact, this is what they look like:

Here, to say something unique or a principle by which you can be identified is, well, unlikely.
Check how sites see it:
https://browserleaks.com/rects
Further:

Our next parameter is Math JS . This is an option for processing your java scripts, which are purely browser-dependent. It seems that the parameter is absolutely unimportant; it can be changed simply by simply changing the browser. But at the same time, if you use some software like changing the User Agent, if you change your User Agent in the header, but do not change the Math JS parameter, then the entire change of your User Agent can be identified, and you can also identify your real browser. This is how it happens:

And the fourth parameter. A parameter which, again, is purely software dependent. This is your browser history :

In fact, your browser history can be obtained using non-cookies. We all know that there is an http only flag that prevents other sites from reading your cookies. In other words, all methods regarding some kind of stuffing of cookies and so on are complete nonsense that they want to instill in you.
But many sites recognize and see what you visit. Many sites can look at your browser history, whether from a mobile device or from a desktop computer, it doesn’t matter. The option to get the browser history depends on the history. I'll tell you why - getting your browser history is an extremely simple option. The fact is that when you go to a site and it is saved in your history, the styles of the links on that site change. In this way, you can identify what sites you visit, you can identify what porn you watch, you can identify what you do online, not to mention the same search queries in the same search engines.
Go ahead. The largest group. This is a group of hardware-software dependent fingerprints:

This is something that many users try to replace, but in fact they do not always understand how to do it correctly and what it depends on. What is an antifraud system? The antifraud system is formed from two words - “anti”, that is, against and “fraud”, which means fraud.
The girl is the antifraud system of the oldest option =) I’ll explain what I want to convey to you. Absolutely every girl has certain criteria by which you must approach her, and also figure out how, in addition, to “open” her. So here it is. Previously, in the Stone Age, who did the antifraud system let through? The anti-fraud system let it pass when a guy comes to a girl, gets her a mammoth, gives her a mammoth leg and that’s it. He completed this task, the antifraud system let him in.I thought for a long time what example to give here, in the end I will give you such an example.
Now, in our time, go to a butcher shop and pick up a pig's leg there, approach any girl on the street with a pig's leg... They will just send you away. But it satisfied the conditions before, why can’t it work now? The situation has changed. Girls are one of the simplest, but at the same time the most difficult option for working with anti-fraud systems. One of the simplest because you seem to know how to deal with us, but at the same time one of the most difficult, because you can only find out how we work if you get our brains. And without this we will make a brain for you))).
Let's take a random girl you like:

You can approach her, but you don't know what she wants. Let's assume that she herself doesn't know what she wants. You walk up to her and say, "Hold the pig's leg." Maybe she'll let you in, maybe she won't. You will come up and say: “I have a big penis . ” Maybe she'll let you in, or maybe she won't let you in. You will approach her and say: “I have a lot of money . ” Maybe she'll let you in, or maybe she won't. What is the point? The bottom line is that you can never figure out what's going on in any particular girl's head.
And in the same way, you cannot understand what is in the logic of anti-fraud systems on the network. Imagine that this is your digital portrait, your personality, who you appear to be online:

What can you do? You have your foundation in the form of iron. In this aspect, this will be your skeleton:

Your height, arm length, leg length, head size and everything else. This is your foundation. Just like your computer hardware will be your foundation. Then on this hardware you apply the operating system of the history of this user and his education. And at the very end, you put money on this operating system. Because if you are not interesting to the antifraud system that wants to cooperate with you, then it will not cooperate with you. Therefore, money can be an identifier of your solvency.
If, for example, you have turned yourself into an anonymous person. We got up in the morning, went to the computer and sat there anonymously. You downloaded a bunch of programs, turned on the VPN, passed the traffic through TOR, everything is fine with you, you are sitting and should be accepted directly into anonymity, and then you will go to rob banks. But here again the balaclava principle comes into play. The principle of the balaclava will be that in fact you are moving from the category of a user who can be sold, to the category of a user who is uninteresting and even potentially dangerous .
With any additional anonymization on your part, first of all, you may not be of interest because if you have learned how to defend yourself, then you are no longer suckers. Just a little bit, but no longer ordinary suckers, just a little bit of everything. And if you are even a little bit more than ordinary suckers, then selling you some kind of product or service won’t really work. Or, you can move into an even worse category, this is the category when you are not just insolvent , but when you are potentially dangerous . If you are trying to protect yourself, then, according to the logic of antifraud systems, you have the prerequisites to protect yourself, which means you can be potential scammers. And not only will you not bring profit to this company, but despite your good position, you can also harm it, you can steal money from this company.
Let's move on. Canvas imprint:


1 of the most advertised is the Canvas imprint. What kind of print is this? Canvas technology dates back to 2006, when it was decided that loading pictures or forms into the client’s browser was not effective. It is much easier to give him a script that will build this image on its own on the user’s computer. The Canvas fingerprint is currently the most advertised and its essence is that this fingerprint depends on your hardware, your operating system and your browser. At the same time, three dependencies that identify you on the network as a user of a specific device.
See how sites see you:
https://browserleaks.com/canvas
Our next fingerprint is a WebGL fingerprint:

WebGL technology is a technology for creating 3D graphics on your computer. It is based on the same Canvas technology, but if you can imagine Canvas as a regular 2D sheet of paper, then WebGL technology allows you to build 3D images. These images allow you to play games, watch videos, and so on. It’s not specifically related to video, but specifically to the user’s visualization process. What a WebGL fingerprint looks like:

The WebGL fingerprint is now in front of you, above in the picture. It has only four parameters.
The first parameter is your Vendor. The vendor is the one who produces your equipment.
Next comes Renderer, that is, the device that will produce your graphics. In this case, the graphics manufacturer indicates an NVIDIA video card with shaders version 5.0. And for the WebGL fingerprint, we can see two unique hashes:

The first unique hash is the WebGL Report Hash.
WebGL Report Hash is a parameter that you can change yourself, without any special effort. You just need to change any string parameter in the vendor or in the renderer. It is used only to receive a report on the health of the system. And it is not used in any way in user identification systems.
Much more interesting is the second parameter, which is called WebGL Image Hash . How do we get it? We get it in the form of this figure:

In fact, this figure is not flat, but three-dimensional. That is, this figure is formed using vertices, lines and color fill, where again your Canvas is used.
https://browserleaks.com/webglHow sites see you. Test link:
Let's move on. WebGL Const :


An extremely interesting parameter that is more important than anything before. WebGL Const allows you to define the graphics processing parameters of your video card. When you try to maintain your anonymity and impersonate another user, you simply do not pay attention to it. Well, what kind of uniqueness can there be in the value 1024? What kind of uniqueness can there be in the value 16? And so on. In fact, there are 168 WebGL Const parameters. These parameters provide information and identification about the video card. In other words, if you take and write a string parameter in your browser - just a text parameter you register your video card manually, for example GeForce, when the processing parameters for your graphics belong to the same Nvideo, then you will not be able to deceive the system.
Checked right there:
https://browserleaks.com/webgl
Another interesting WebGL parameter is Extensions :

In other words, these are small routines that are supported by your video card. And here, in exactly the same way, we come to the point of identifying the user and his video card due to the capabilities supported by this video card. The following AudioContext parameter:

The AudioContext parameter is used by absolutely all major resources and sites. This parameter allows you to identify the user by checking the audio processing parameters. In other words, your audio card and your audio settings again allow you to be identified as a unique user. This is what it looks like:

Above we have a purely visual interpretation of it. Below we have its real interpretation using two different methods of obtaining it. As you understand, your audio card and its audio card settings are an excellent means of identifying you on the network.
You can check how websites see your fingerprint here:
https://audiofingerprint.openwpm.com/
Ubercookie fingerprint:

The Ubercookie setting was created by an independent researcher named Robin Linus. This parameter is a clear representative of adjacent codependent imprints. It is a dependence of the audio fingerprint and the ClientTrack fingerprint - the block boundary fingerprint that we talked about earlier.

This fingerprint is actually unique, but replacing it is quite simple. We just need to change the scale of our browser and that’s it - it’s spoofed.
Check how websites see us:
https://ubercookie.robinlinus.com/
Go ahead. WebRTC parameter:

The WebRTC parameter migrated to us from Internet Exproler . This browser had ORTC technology . What kind of technology is this? In fact, this technology was not aimed at identifying users in any way; it was created for just one purpose. In order for Internet Exproler users to be able to stream video and streaming audio between browsers. That is, 1 person from Internet Exproler , without Skype and without anything, calls another person from Internet Exproler , and everything is fine with them. After that, due to its lack of widespread use, this technology mutated a little. It mutated into WebRTC technology , which we have seen in our browsers since 2013. This technology also still allows us to talk between our browsers. From Google Chrome, call someone on Mozilla, for example, on social networks, VKontakte, Facebook and somewhere else. WebRTC technology is based on the fact that it is necessary to obtain data about our network connection in order to establish the most powerful and best connection. Therefore, WebRTC technology also makes it possible to obtain our real IP address. If we have several of them on our computer, then it is possible to use this technology to obtain all the IP addresses that are on our computer:

Also, WebRTC technology , since it is used for video and voice communications, allows us to obtain the id of our devices, communication devices, microphone devices, virtual helmet devices, camera devices, and so on, in the form of unique Device IDs. Even our speakers.
How sites see it:
https://browserleaks.com/webrtc
Let's move on:

Our very top part is part of our browser. That is, through which the parameters go into the network, those parameters with the help of which we can be identified and, accordingly, in the future we can either be sold, or a decision be made about whether to allow us to take a certain action or not to allow us. In fact, this is used by the digital needs market, and is used very often. Oddly enough, many will think that probably only terrorists or sophisticated hackers and carders know what I’m telling, but in reality, no. The most basic consumers of this market are ordinary users who simply make money from it. And they make money from this in the following way; I’ll give a few simple examples.
For example, some large poker site gives money to the first client, that is, this is called a welcome bonus. When you come to the site for the first time and the system does not recognize you as a person who has been there before, it gives you a bonus. For example, you deposited $20 and were given another $20 extra to play, you cannot withdraw it in any way, you can only spend it on the game. But a person who knows how to emulate the identifiers that I described above does the following manipulations: he creates 5 accounts for himself, deposits $20 into each of these accounts and receives a $20 bonus into each of these accounts. What will he do next? He will put all his 5 accounts on 1 poker table and lose the money to himself, and then withdraw it in double amount.
It’s the same issue with Forex. Users there are also given a bonus for their first deposit. For example, I deposited $200 and received a $200 deposit on top, for a total of $400. Next, I create a second account and do the same. But now I can’t withdraw them in any way, the system won’t let me do it. How can I win now? One account is betting on a currency increase, and the other is betting on a decrease, and one of these accounts will win in any case, thereby I will increase my capital by 2 times and calmly withdraw it. It's the same with bookmaker companies.
The same situation with Google. There is an even more interesting situation with Google. That is, for example, each user can create a high-frequency query, for example, he will ask the query: “Casino”. In order for him to place an advertisement for his casino on Google, he will spend approximately $4 for each user who follows his link. He creates several accounts for himself, on each of these accounts he creates, for example, a “site selling slippers,” but he no longer pays Google $4, but only 10 cents for each person, and then he takes and dumps all this traffic on casino with an affiliate program for only $1, but he is already in 10-fold profit.

What do I want to lead you to? I want to lead you to the fact that in fact, the user identification technique is used absolutely everywhere in our work on the network.
Our next picture:

Your operating system also has a hidden part that each of you has heard about, but in fact few people understand what it is responsible for and what it looks like. This is telemetry :

Those who use Windows 10 and do not kick the corpse of Windows 7, then they probably already understand that such a magnificent Trojan is practically impossible to find. What's the point? I have already repeatedly raised the question that the Windows 10 operating system monitors users, monitors each of you. That is, at first she tried to log even our keystrokes, at first she tried to identify us as a user using all the maximum possible parameters. But a little time passed and the US government pressed Microsoft a little and said don’t do this anymore, do it the right way. Then Microsoft made the next knight's move, it said that telemetry is one of the most important factors for software development, for understanding the issue of errors and for understanding what is happening on the user's PC. But did it help us? Each of you, if you have heard about what telemetry is, can simply look it up on your PC. This is done simply through banal operating system settings:

You can additionally install an event viewer from the Microsoft Store and with the help of this event viewer an absolutely interesting, new world of what your Windows 10 operating system sees about you opens up to you.
Well, for example, as soon as you install the Windows 10 operating system. Only you have installed it , as soon as you move on to creating your user profile. You see this when your purple windows 10 reinstall screen changes to blue. After this there is a wonderful connection with telemetry, and then data is generated about you, specifically about your PC. After which this data is exchanged with Microsoft servers and we have a wonderful identifier called ETAG:

The ETAG ID will identify you as an authorizer and will allow future work to be done with you. It will again allow you to be spied on, and will also allow you to install additional software, even if you do not want it, and will collect information about you, for absolutely legal purposes, of course. Microsoft cares about us very much.
But if we move a little towards telemetry, then telemetry currently has 68 unique parameters that are created in the operating system. I have selected several of them, the simplest ones which identify purely groups:

The first group at the very top is the hardware identifier group. Whatever piece of hardware you install in your PC, be it an audio card, a video card, a virtual reality headset or anything else, information about this will leak to Microsoft:

Second part. Device ID. The Device ID part is formed based on the configuration of your computer during the installation of the operating system. It gives out your unique ID with which you can still be tracked:

The third part. User ID :

User ID, maybe some of you know, has an absolutely clear abbreviation on your PC called SID (Secure ID) . The SID is the main one for applying access rules in the operating system. Rules for accessing folders, the registry, and so on. This ID is generated when you create a user and when you install your operating system. Changing it is possible only in three ways.
The first is simply reinstalling the system.
The second is to create a new account.
Third, there is special software to replace it.
And our third group is software identifiers. Regarding software identifiers, in this case I have the identifier of our Microsoft Edge browser shown:

And if we move a little further in the future, I would like to show one interesting point.
Surely many have heard that there is a Tor browser. It's all great, it's all anonymous, it's all great. With the Tor browser you can organize sales of the new Hydra. But pay attention here:

As soon as you download the Tor browser, or some other browser anti-detect, or some other anonymity tool, then, remarkably, information about this will leak to Microsoft. Now think about your anonymity when using Windows 10.
Let's move on. Next point. Our operating system and our browser have another group of identifiers called extra-browser identifiers:

Off-browser identifiers allow us to be identified beyond the browser we use. And even if we want to use some super-anonymous, super-cool and super-super-incomprehensible browser stuffed with us and offered by hucksters, we will still be visible.
We seem to have already figured out how we can be identified, but in fact, in addition to all the software that we can use to hide our identity and in order to again emulate our identity, we need to observe several more interesting parameters. These settings are called out-of-browser fingerprints. Out-of-browser fingerprints are fingerprints that cannot be changed using the browser. Maybe, of course, someone will come up with something interesting, but at the moment I have not seen these technologies.
What it is?

Our first fingerprint is a TLS fingerprint. What does this mean? Every time you go to a site that has https in the address bar, this means that the site is using a security certificate. It can use SSL version 1 security certificate, SSL version 1.1, SSL version 1.2, or it can use other versions. What does this allow you to do? On the part of anti-fraud systems, this allows us to be identified when using an SSL certificate of the third version or another TLS certificate. In other words, every time you visit a site that uses TLS certification technology, it is possible to identify you outside the browser. If you change all your fingerprints, if you change everything possible, then the TLS certificate that remains on your PC can be used to identify you. This is the first out-of-browser fingerprint. It looks like this:

You can study this topic yourself if you want. I have conveyed the essence to you, and then you must decide for yourself how to use this essence.
Let's go further MTU/TTL :

When you go online, you have your packet size and you have the lifetime of your packet. Those who have worked with nmap , which I wrote about in part 5 of the article on Kali Linux, have no questions at all, they all know what it is. That is, in other words, determining the user’s operating system by its IP address. Determining an operating system by IP address is not a 100% accurate indicator and many people use it in different situations. Someone may have a VPN , someone may have some kind of router on which the network is built, and so on. The most basic point is that you cannot change this parameter on your PC. Whatever you do, that is, if your PC is the first entry point into the network, then you can change it, you can change the packet length, you can change the packet lifetime and you can disguise yourself as a different operating system. But if you use a VPN , if you use a proxy, if you use some other intermediary to log into the network, then you can change this parameter only if you are the owner of the intermediate point. If you use a VPN , then be the owner and only then can you change this parameter.
Here's what it looks like:

You can test it yourself: https://whoer.net
As you understand, sites have the ability to determine your operating system. Is this critical? When bypassing antifraud systems, this is not a critical parameter because we have a set of parameters, that is, what we take, what we provide to our antifraud system is a certain community, area.
Go ahead. Flash Parameter:

The Flash option is already obsolete. Everyone is familiar with Flash player and Flash player has an interesting feature of two types. The first is to get all the information about your PC. The second possibility is storing information about the sites you visit not on the user’s computer, but on macromedia servers. Flash technology is already morally outdated, even YouTube switched from it a long time ago, they abandoned the use of this technology in favor of html5 . But still, some sites, for example the same bookmaker companies that conduct online broadcasts, use flash technology. And this technology has a good gradation by version. Before version 10.0, it is possible to change the parameters of our PC. After version 10.0 it is not possible to change the parameters of our PC. Therefore, if you use flash, then it is possible to track information about all your hardware.
Further. Java Technology:

Java technology is very interesting, but it is of interest mainly to those who use the banking client. Java technology allows you to get information about all your hardware, as well as what you have inside your PC. Do not confuse this technology with java script .
The following is our FuzzyHash technology :

Hash phase technology allows you to ignore changes to your fingerprints. If you want to be very well anonymous, if you use any means of anonymity, then it is possible to roll back these means of anonymity and find out who you are. Pay attention to the picture:

At the very top we have some kind of imprint, let it be the Canvas imprint . Our fingerprint has certain parameters. Here they are:

We also have a second imprint that occurred, was produced, was created after we used the means of anonymity. Here he is:

What could happen next? Phase hashing technology or free hashing technology allows you to identify a change in the original data. Imagine, Ivan Ivanovich Ivanov lives at Kontroskaya 5, apartment 68 and his phone number. What will happen if Ivan Ivanovich Ivanov changes his apartment from 68 to 69? That's it, the hash has changed, it seems like there is a completely new person, and in the same way in the browser fingerprints, it seems like a completely new person, but in reality this is not happening. Because we can track changes in the hash itself, in the data from which we get this hash, and lead this to the point that we can identify changes and identify the basis. In other words, if one of you wants to change, for example, your Canvas , someone else wants to change some other parameter, then it is possible to recognize this person if the changes do not exceed 30%. 70% remain static, 30% free hash. If Ivan Ivanovich Ivanov changed his apartment and became Dmitry Ivanovich Ivanov, then we can still find him.
Go ahead. Now, it’s probably not very visible here, but I want to tell you. Technology for obtaining Canvas . The same Canvas print that you can see here:

What exactly is a Canvas imprint? Fingerprint Canvas is a construction of an image on your PC. This is a pure client site script. Look, we have our pixels. Let's imagine that this is the reference image that I posted above. What will happen next to this reference image? This reference image will be converted to binary code to be a Canvas fingerprint. It will then be converted to a Base64 hash. And in fact, we can take 1 of the pixels, change it by half a tone, and we will have a completely different binary code, and from this completely different binary code we will have a completely different Canvas print . But there is a purely statistical problem here. I'll explain what it is.
Imagine that each of you is the owner of Google, everything is fine in your life, you have a lot of money and so on, but you have no brains. You have statistics. And these statistics, thanks to the fact that you, as the owner of Google, have already reached into the pockets of all the people in the world, you already know information about all the people in the world. You are actually not as simple as you seem, you already know everything about all the users in the world. So, you used the simplest method, you didn't invent artificial intelligence, you didn't do anything, you just looked at all the other people in the world. Do you know what it's called? And this is called statistics. You sit and watch who comes to you, and you don’t just sit and watch, you also write it down. You take and write all this down for each person. And then what do you get? Then you get awesome statistics. You get statistics of your users. You understand who comes to you, you understand their identifiers, you understand their fingerprints. What happens if you take these statistics that you make and just look at the systems, for example, of protection from you. There are many systems, they are called Google protection systems, you can find them on the Internet. You will see that it is impossible to protect yourself from you. And I'll tell you how. Here is this pixel and many other pixels:

For example, in forming a fingerprint of the same Canvas, security systems can hide the user, but not hide him in front of you (the owner of Google). How does this happen? When a user uses any software to hide, in order to not identify himself, then this software uses the simplest and most stupid method. This software selects a random number of pixels from our Canvas image and changes their color by as little as half a tone. For example, it selected 7 pixels, 15 pixels, 20 pixels, and changed the color to half a tone. Has the binary code changed? Changed. The hash has also changed. It seems like everything is fine, and it seems cool and you can work, right? Everything is great.
Look here. A striking example of this. Pay attention to the second column Uniqueness , uniqueness. Uniqueness 100%:

At the moment I am showing an example using one of the most adequate tests at the moment:
https://browserleaks.com
But if we pay attention to this parameter:

0 users out of 425093 about whom information was entered. 0 users have this Canvas fingerprint. Now let's imagine all this in the size of Google. What will happen if we use such a Canvas fingerprint ? This will be an example of how Google will identify us among all its users. And you and I are returning again to where we started. We return to the balaclava. It seems that we have defended ourselves, it seems that everything is fine with us, it seems that everything is fine, we are walking down the street in a balaclava, but again we will be identified as an asshole in a balaclava . And no other way.
What is the sacred essence? It's that we can't just make the changes we want. So it occurred to us, we want to make changes to Canvas , and just like WebGL , audio fingerprint, UberCookie fingerprint , and so on, we can combine all this into one single database, where, in case of a banal mismatch of these parameters, we can already anti-fraud system, take this user under control at least.
Go ahead. Keyboard :

Well, who's looking at the keyboard? What's there to worry about?

The essence of the keyboard is very underestimated by many in identifying users.
How? The fact is that when you enter any information on your keyboard, there are at least four different options for identifying you.
Let's imagine a login and password input field on Facebook:

We will enter your login. How can we introduce it? We can enter it manually. Cool? Yes, everything is great. We can enter it using the clipboard, we can simply paste this field, or we can paste this field using autofill. And the best result for bypassing anti-fraud systems will be precisely changing our input field in the direction of autofill, but there is another interesting hidden meaning when the user tries to pretend to be a different person. Take for example, someone look at your keyboard. Your keyboard has a qwerty layout. And imagine that you want to emulate a user from the UK, for example. You log into the same Google, Paypal, Amazon, and so on, wherever you enter your data. You enter your email first. What will happen on the English layout as opposed to the American one? It seems to be the same language, but when you try to enter @, you will not enter a dog, you will enter a number sign. What will happen next? And then you press the erase key, delete this number sign and enter the dog accordingly, either manually from the clipboard, or change the layout, but this will already be a signature action to determine your real layout.
Or if, for example, you wanted to be French, you wanted to emulate a Frenchman. Regular users have a qwerty layout, while the French have azerty. When you simply enter, for example, gmail, then the letter a - you will enter a comma, after which you press the erase key and press the letter q on your keyboard because it corresponds to the letter a. And this will already be a signature action to determine your real physical keyboard layout. And even at this absolutely seemingly simple stage, just a keyboard, it is possible to identify you as a real native speaker.
You can test it here: http://ahtcx.github.io/layoutline
Last edited:

