Encryption helps you keep your data private, but at the same time attracts unnecessary attention. If the file can't be opened that easily, then it probably has something valuable in it. Therefore, it may be important to hide the very presence of classified information. The easiest way to do this is by dissolving confidential data inside some harmless file. This problem is solved with the help of steganographic utilities, which we will test.
From the Pharaohs to the present day
If we assume that history develops in a spiral, then modern life seems to have entered the same spiral as Ancient Egypt. People are once again worshiping cats and keeping their images everywhere. At the same time, the cult of secret knowledge is being revived - some hide information, others look for ways to get it. So the ideal way to hide sensitive data is to mix it with trivial content like cat photos.
According to one version, cryptography originated in Ancient Egypt. Her daughter-steganography, or" secret writing", appeared closer to the heyday of the Roman Empire. Some techniques of secret writing were practiced even before our era, but steganography was formed into an independent applied discipline only by the XVI century.

Modern steganography - digital and computer. The latter can be divided into three major areas. The first is actually cryptography, or methods of hiding some files (which are usually called a message) inside others ("container"). After filling in the message, the container changes outwardly imperceptibly and completely retains its functionality.
The second direction studies methods for adding hidden or steg marks to a message. These labels are invisible without special processing and are identical for all files of the same person or device. For example, such steg marks are recorded in digital photos in order to prove their authorship. Crackers sometimes leave steg marks in their license keys. They are protected at the level of the generation algorithm, and therefore they are saved when you try to change the keygen interface and pass it off as your own.
The third direction is the introduction of digital fingerprints in the message. Unlike steg tags, these hidden signs are unique for each message. They serve mainly to protect the interests of copyright holders, allowing you to track the distribution of content. For example, many online stores introduce digital prints in books and music tracks sold. They encode information about the date of sale and the buyer's account (name, IP address, etc.).

Does your favorite online service use steg tags? This is easy to check. It is enough to buy two copies of the same work from different accounts and make a byte-by-byte comparison of files. The difference between them will show hidden placemarks. If the files downloaded are identical (and their hashes completely match), then there are no steg tags inside.
Many books and articles have been written about each of these areas, but there is still no single terminology. Some authors divide the listed branches into dozens of smaller ones, while others do not see a fundamental difference between the large ones. For some, there is a fine line between hidden storage and hidden data transfer, while for others, these are just specifics.
We will not go into the controversy, it is much more interesting to try steganography in practice. First, let's take a closer look at its main application - data hiding. Of the fifty utilities for masking some files inside others, we selected only seven. The review includes only those that are guaranteed to work in Windows 10.
For the test, we will take a picture with a desktop wallpaper. Behind this vegetation, you can fit a lot of interesting things.

Anubis
Anubis - Browse Files at SourceForge.net
Anubis is a superhero of the ancient Egyptians. The Jackal Man, after whom the free program was named six thousand years later. Its first and, unfortunately, last version was written in 2014 in Java. Therefore, the utility turned out to be cross-platform, but requires the installation of a JRE, as well as (in the case of Windows 10) a DOS virtual machine - NTVDM.
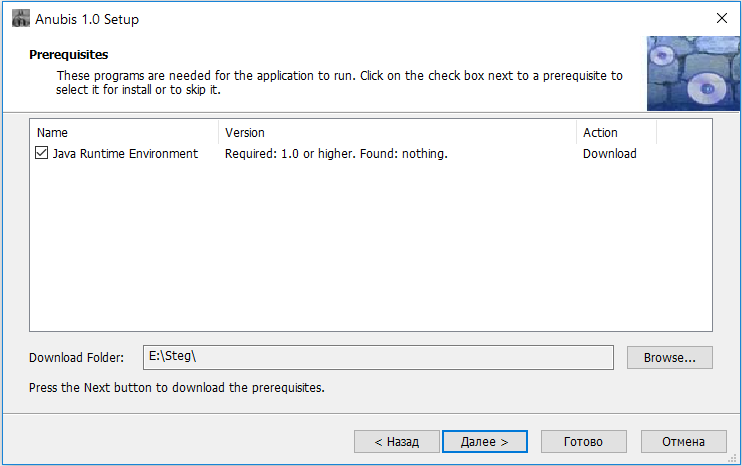
Bring Anubis Java!
The main window of the program looks as austere as possible. Click Encrypt and in the opening tab specify the necessary actions: which file to put inside which one and where to save the result. Only hiding text files inside BMP images is guaranteed to work. Several of these are already available in Windows 10 - these are user icons. It would be interesting to hide a list of passwords or some other confidential information in user. bmp. It has long been noticed that the best caches are in a prominent place.
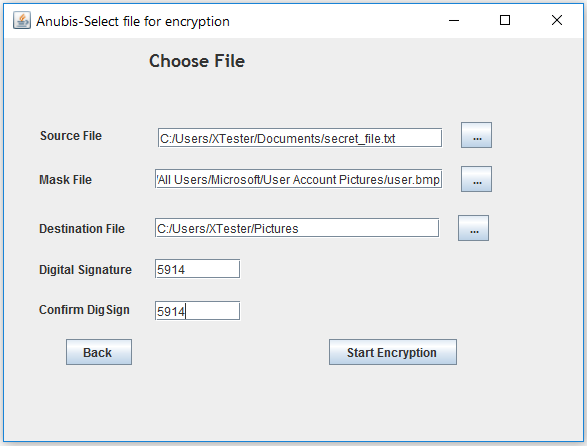
Hiding TXT in BMP
In addition, you can protect the received file with a PIN code - then you will need it for reverse conversion. The utility does not correctly process a string indicating the location of the resulting file. It can be saved at a level higher than the specified one, or even in the source directory.
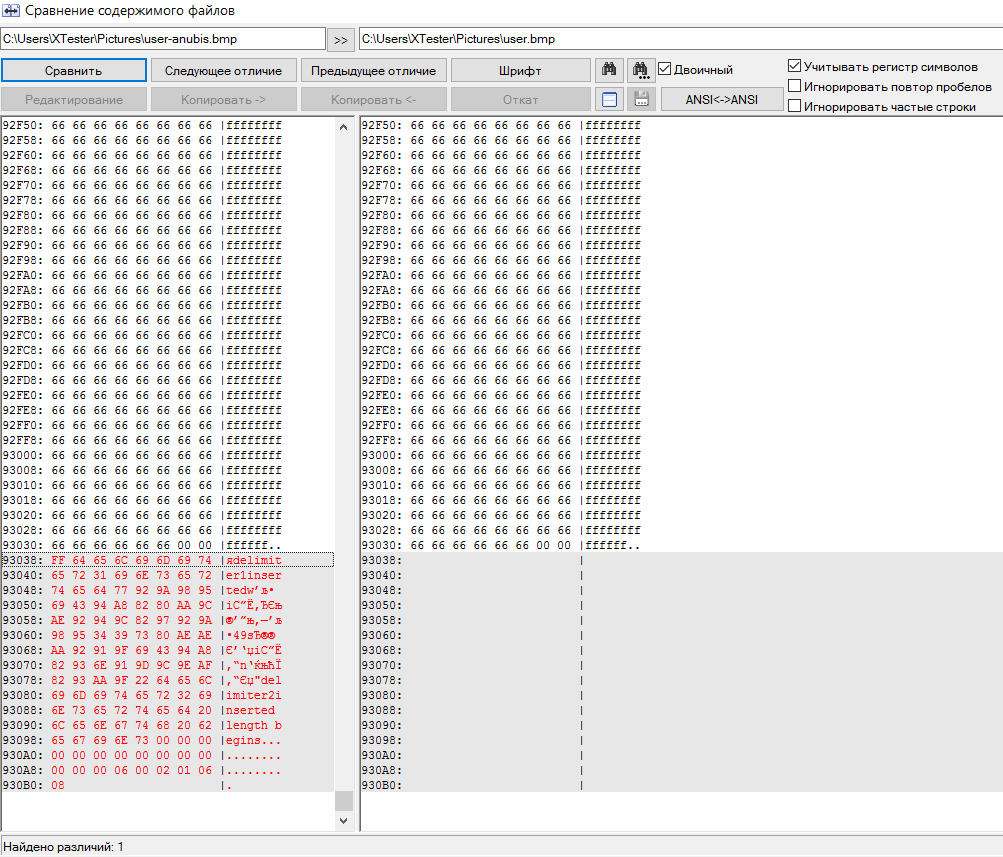
Comparing an empty and filled container
As can be seen from a byte-by-byte comparison of the source BMP file with the hidden text, the program works very primitively. It simply appends data to the end of the file. The data is encrypted, but provided with characteristic pointers: limiter1, limiter2, inserted length begins. By simply searching for files containing such strings, you can easily find all the steg containers. This utility can be used as an illustration of the simplest method of steganography, but it is completely unsuitable for serious tasks.
DeEgger Embedder
DeEgger Embedder Download
DeEgger Embedder is another small steganography program. It has already implemented a larger set of functions, but its use requires installation .NET Framework 3.5. In addition to the rarely used BMP images today, the program supports PNG, JPG, AVI video files and MP3 music as containers. The utility keeps a detailed log of its actions, which is displayed directly in the main window.
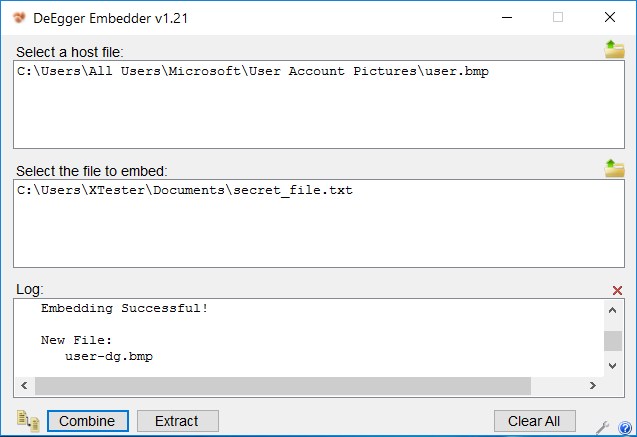
Making Easter eggs!
The algorithm launch button is called Combine, not Encrypt, which more accurately reflects the file injection process. Hidden files (stegs messages) are extracted from multimedia containers by pressing the single Extract button. There is no PIN code protection here.
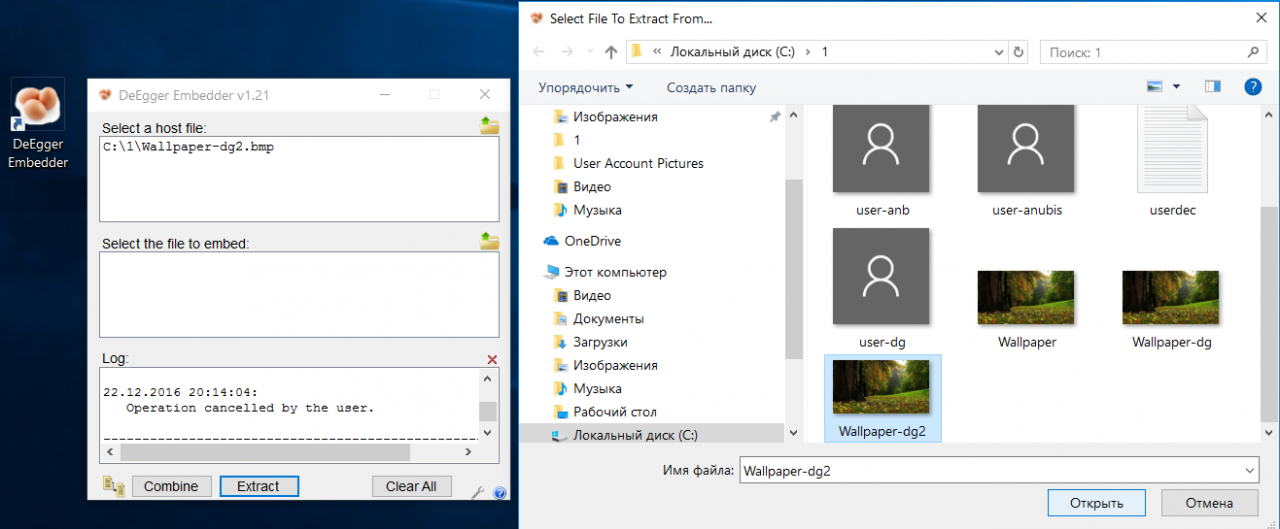
Combine and extract
But the program can process several files at once. You can put multiple messages in one container or one in different containers.
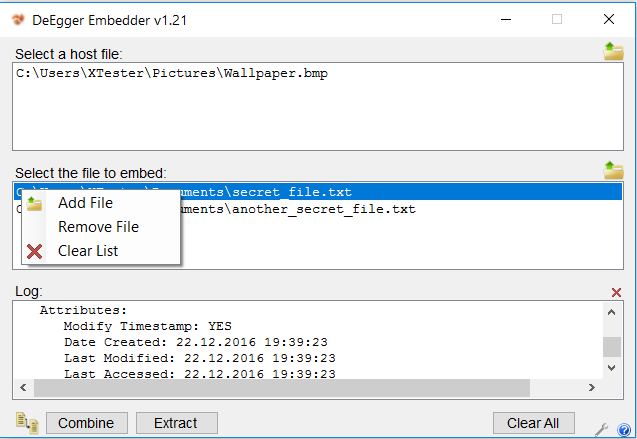
Writing multiple files to a single container
After processing in DeEgger, image comparison utilities consider the source and destination BMP files to be identical. In reality, it is an empty and filled container in the terminology of steganography.
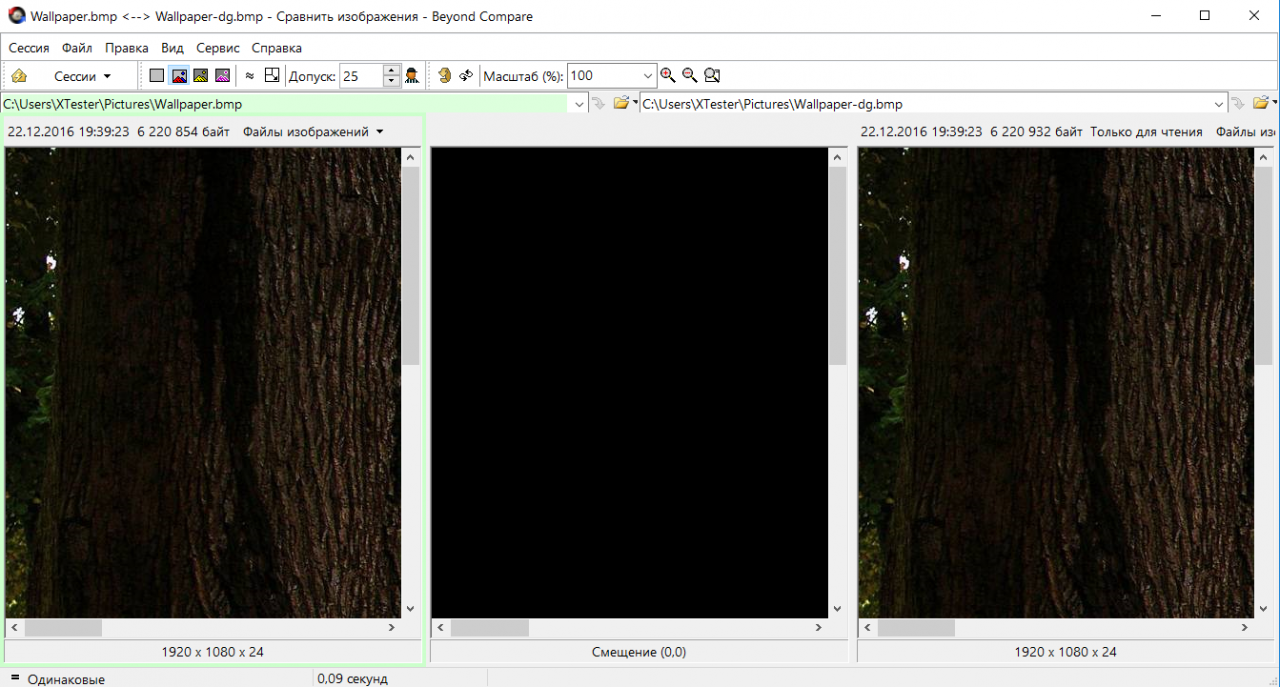
Imaginary identity
Let's make a byte-by-byte comparison. Does it look familiar? Just like Anubis, the DeEgger Embedder utility added a steg message to the end of the container file. The user. bmp image has a lot of monochrome areas, so this appendix looks especially noticeable.
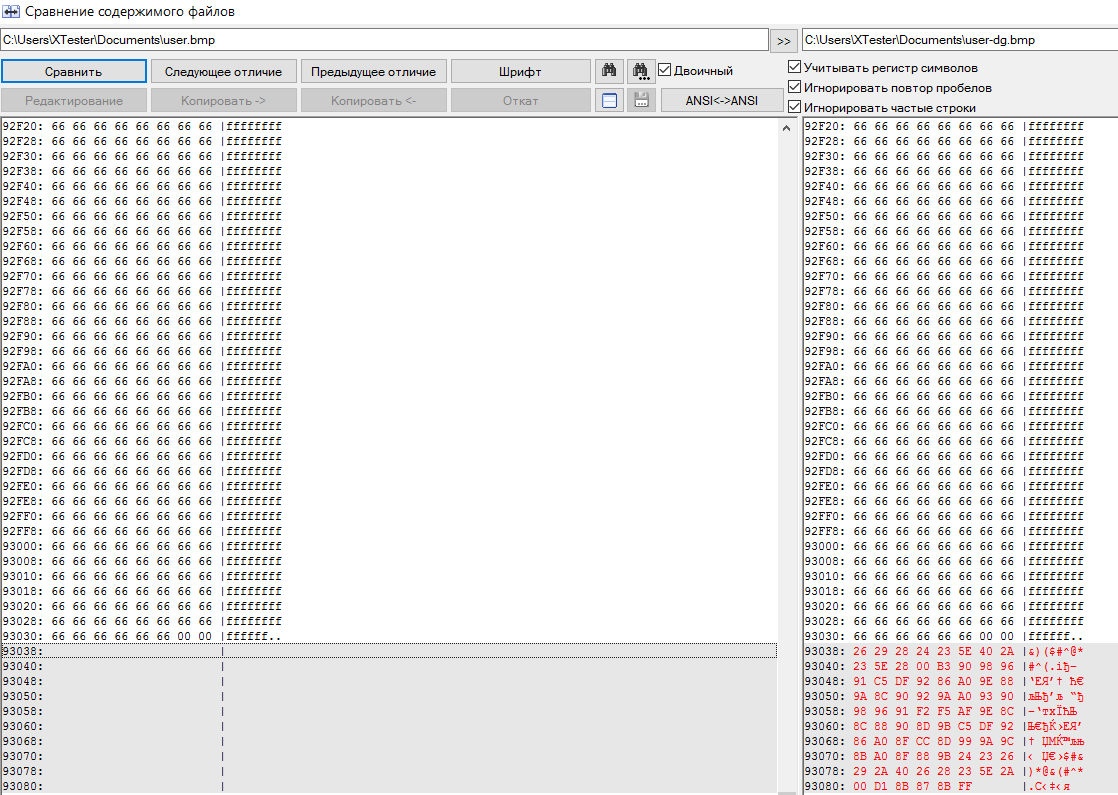
The same Easter eggs, view in the code
At first glance, there are no explicit pointers that can be used to search for files containing a specific string. However, let's take a closer look. To do this, we will create another container with a different message and compare the two already filled containers with each other.
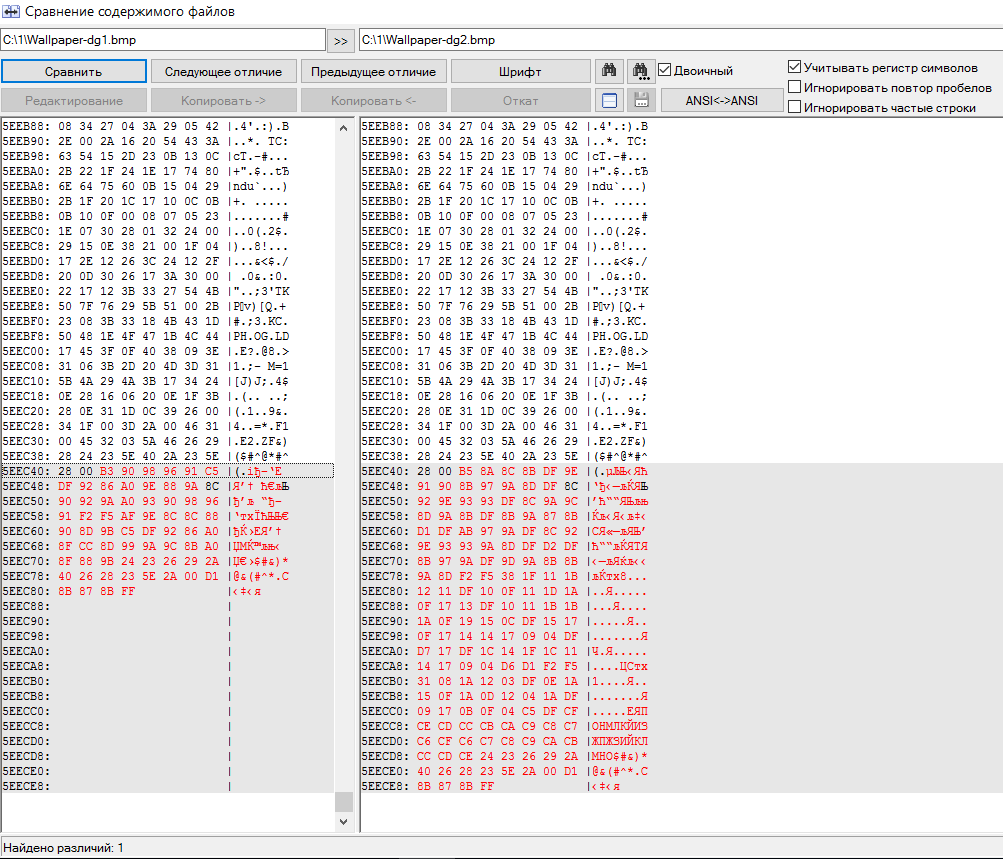
Finding the embedded file pointer
Here is the same section in hexadecimal: 24 23 26 29 2A 40 26 28 23 5E 2A 00 D1 8B 87 8B FF.
As you can see, despite supporting a larger number of formats, DeEgger is not far behind Anubis. Hidden files are also written to the end of the container file and have a distinctive appearance that makes them easy to detect.
DeepSound
DeepSound -> Overview | jpinsoft.net
The latest version of this program was released in November 2015. Unlike the previous utilities in this review, it hides data inside audio files. DeepSound can use WAV (uncompressed only, PCM), as well as MP3, CDA, WMA, APE, and FLAC as containers. DeepSound can embed files of any type and automatically calculates the available space for them depending on the container size and audio quality settings.
When using MP3, the available space for the steg message is shown larger than the container itself, but this is an illusion. Regardless of the original file format, the new container is created in only one of the uncompressed formats: WAV, APE, or FLAC. So the size of the original container doesn't matter. As a result, the message will occupy a certain percentage of the volume of the new (uncompressed) audio file.
Large volume for any files
The program can simply put any file inside the folder, or pre-encrypt it using the AES algorithm with a key length of 256 bits. It was experimentally determined that the maximum password length is only 32 characters. My normal passwords were longer and resulted in an unhandled exception.
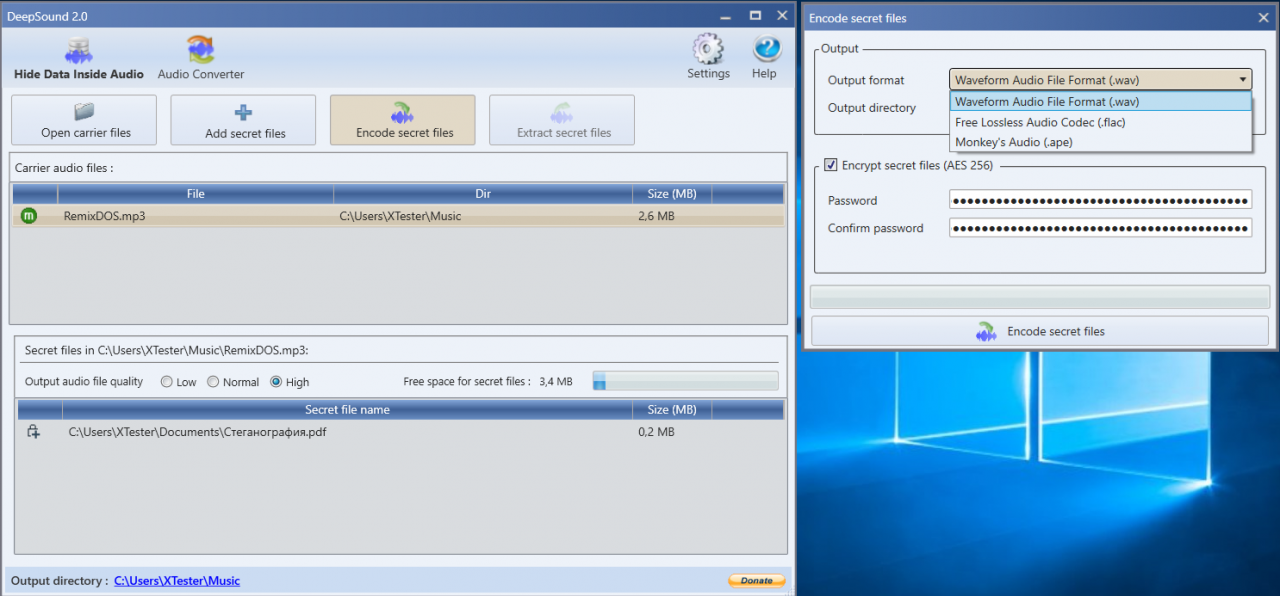
AES Encryption
You can put any number of files in one container until the free space counter is full. Its number depends on the degree of quality (i.e., the distortion introduced in the audio file). There are three settings available in total: high, normal, and low quality. Each of them increases the useful volume of the container twice. However, I recommend not to be greedy and always use the maximum quality - this will make it harder to detect a hidden file.
A stego message is retrieved after selecting the appropriate container manually. If encryption was used, then without entering the password, the program will not even show the name of the hidden file. Cyrillic characters are not supported in file names. When extracted, they are replaced with XXXX, but the contents of the file are not affected in any way.
DeepSound can convert MP3 and CDA, so we can easily convert the source file from MP3 to WAV and compare two containers: empty and filled.
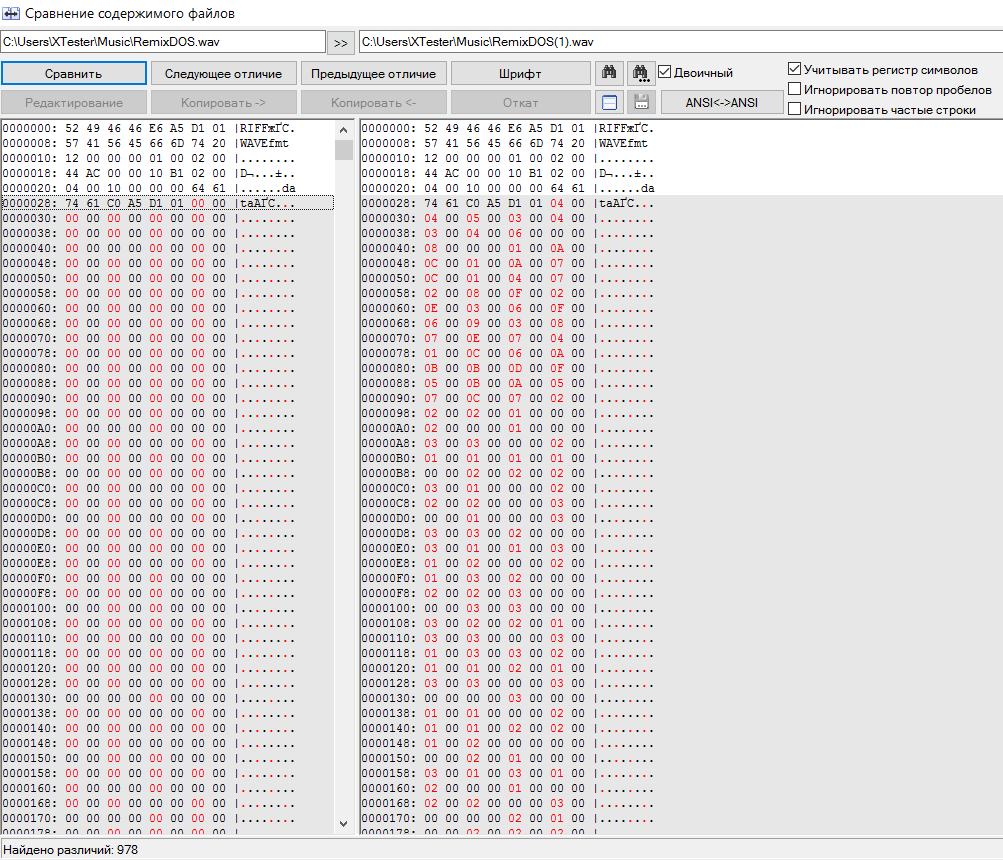
PDF is smeared inside WAV
Here we are waiting for a pleasant surprise: the file sizes are identical, and their contents differ immediately after the header. Bytes differ almost everywhere by one, and by small values. Most likely, this is an implementation of the LSB (Least Significant Bit) algorithm. Its essence is that the hidden file is encoded as changes in the low-order bits in individual bytes of the container. This leads to small distortions (changes in the pixel hue in BMP and the sound frequency in WAV), which a person usually does not perceive.
DeepSound is already quite suitable for hiding important information (except for state secrets, of course). You can also use built-in encryption, but no one knows how well it is implemented, because the program did not have an open audit. Therefore, it is more reliable to first place secret files in some reliable cryptographic container (for example, TrueCrypt or VeraCrypt), and then hide it inside the audio file.
Hallucinate
http://sourceforge.net/projects/hallucinate/
The latest version of Hallucinate (v. 1.2) was released in November 2015. This compact (only 34 KB) utility is written in Java and does not require installation. As a container, it supports BMP and PNG formats, which makes it much more convenient than Anubis. PNG images are much more commonly used today than BMP images. There are plenty of them even in temporary browser directories, so such a container will definitely not be a lone and very noticeable file on disk.
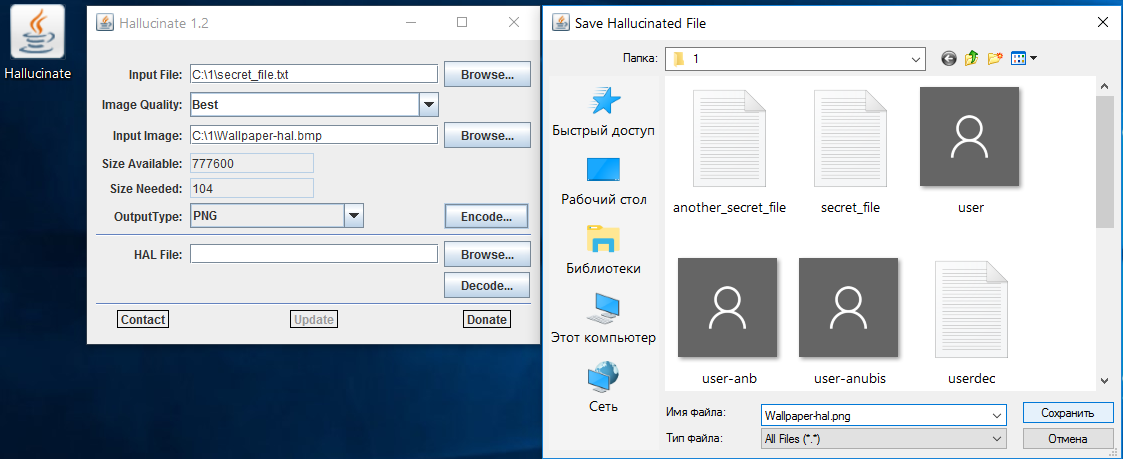
Hallucinations with meaning
The interface of Hallucinate is simple and functional. You need to select a container, specify the file hidden in it and the desired quality level of the final image. There are eight options available. The coarser the original image becomes, the more you can hide in it, but the more visible the artifacts become. Let's choose the best quality in the settings and illustrate this difference by repeating the operation with the BMP file.
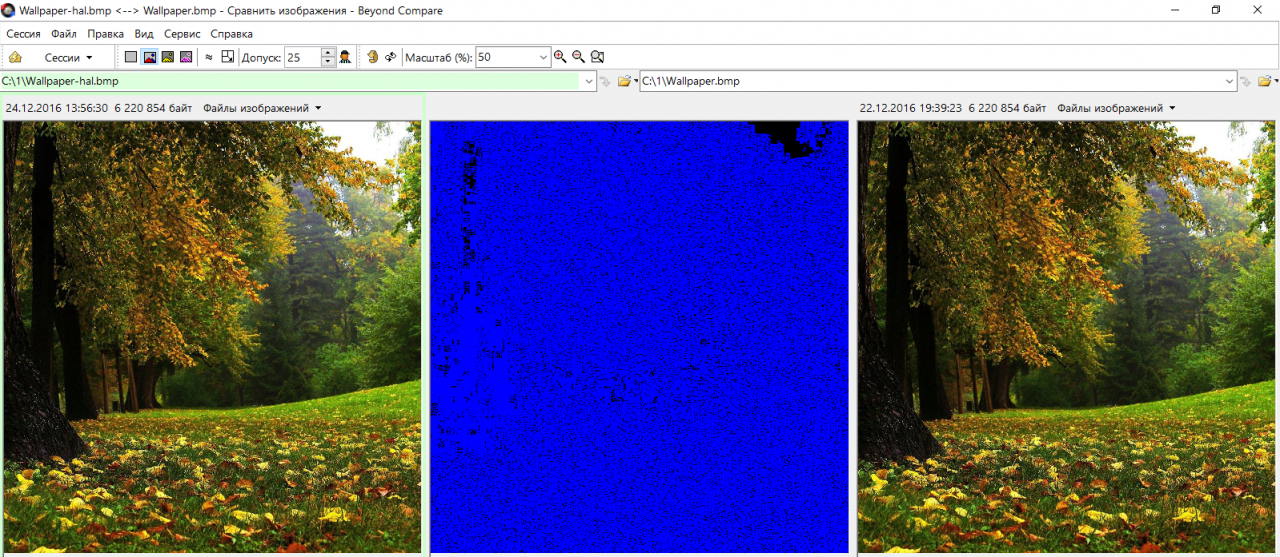
See the differences? And they are!
Visually, the images on the left and right do not differ. However, the Beyond Compare program shows the difference between them in the center frame. The text file is encoded as changes in the brightness of individual pixels that are evenly distributed throughout the frame. Only in the darkest and lightest areas they pile up tightly.
When comparing files byte-by-byte, the same difference in hexadecimal format looks familiar: the same LSB algorithm as DeepSound. A graphic file or an audio file - it doesn't matter in this case. In both formats, minimal distortion is introduced, which is indistinguishable without special comparison methods. It is quite difficult to detect them without the source file (with only the container on hand). It does not contain any explicit pointers to the implementation of a steg message.
The hidden file is extracted in just two clicks. Just select a container (HAL-file in the terminology of the program author), click Decode and specify a place to save the file.
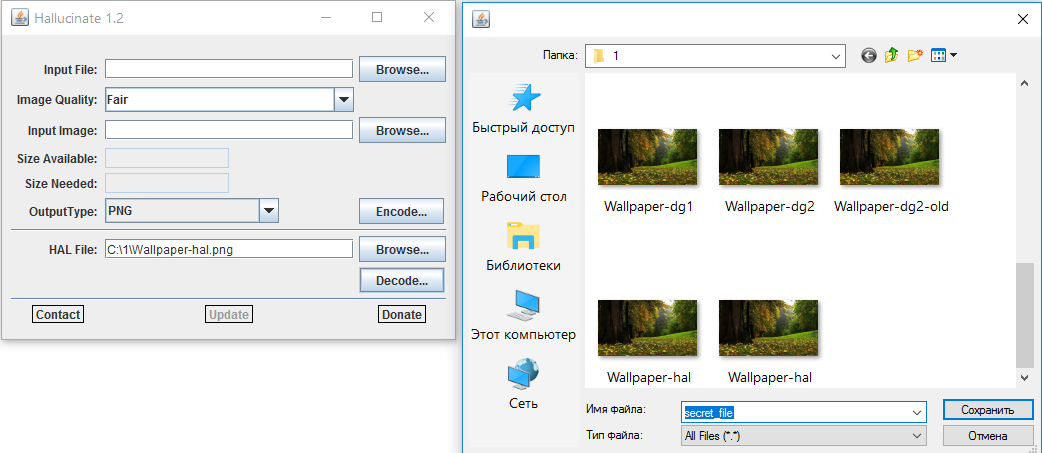
Undressing the matryoshka doll
JHide
JHide
JHide (not to be confused with jihad) is another similar Java program. You can't call it compact, it takes up almost three megabytes. However, unlike Hallucinate, in addition to BMP and PNG, it supports TIFF, and also allows you to use password protection.
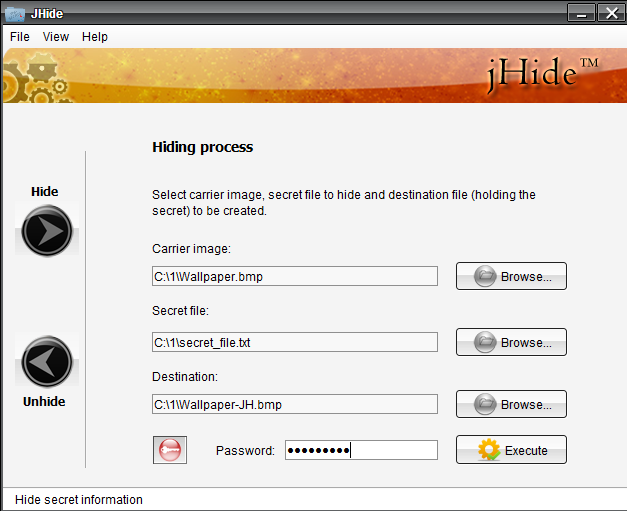
jHide Interface
Comparison with the Beyond Compare utility shows subtle differences. In the first second, they are not visible at all. You need to turn up the brightness and look closely to see evenly scattered dark blue dots on a black background.
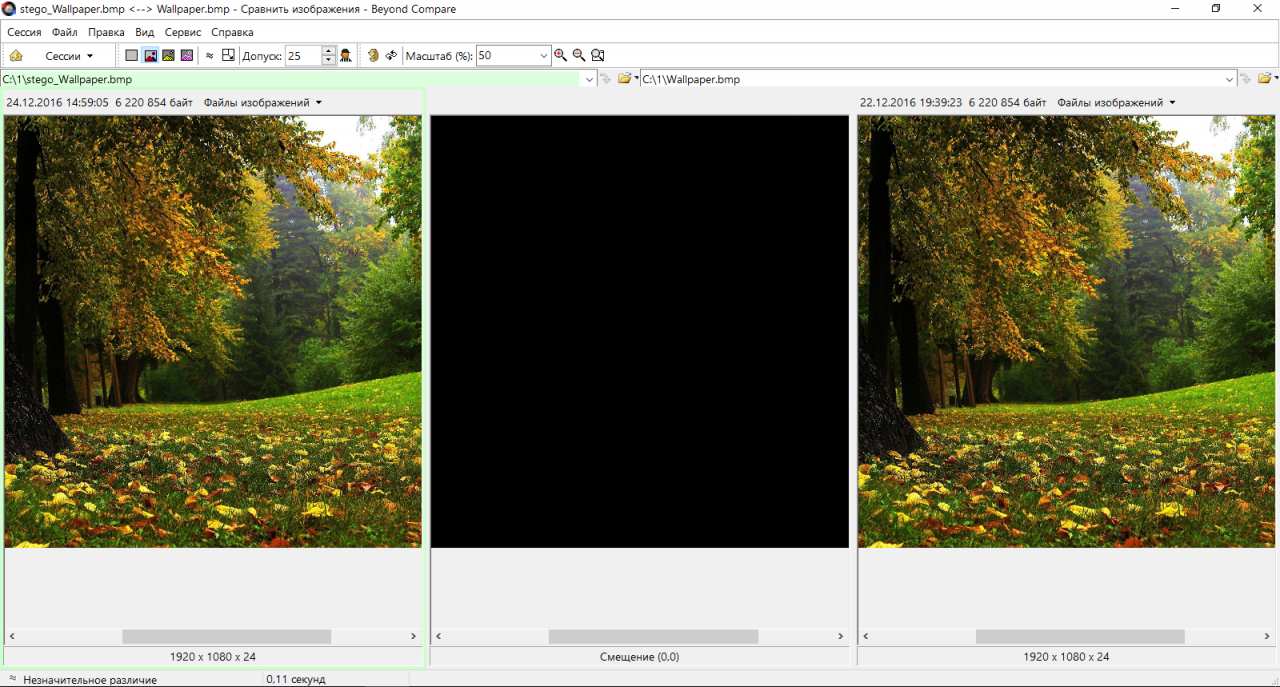
jHide output
A comparison in hex codes shows the same LSB algorithm, but its implementation here is more successful. Modified pixels are not grouped in large blocks from the beginning of the file, but are evenly distributed throughout the container. This makes it much harder to detect a hidden message in an image. If the steg message size is small, this is almost impossible to do without having the original (empty container) to compare.
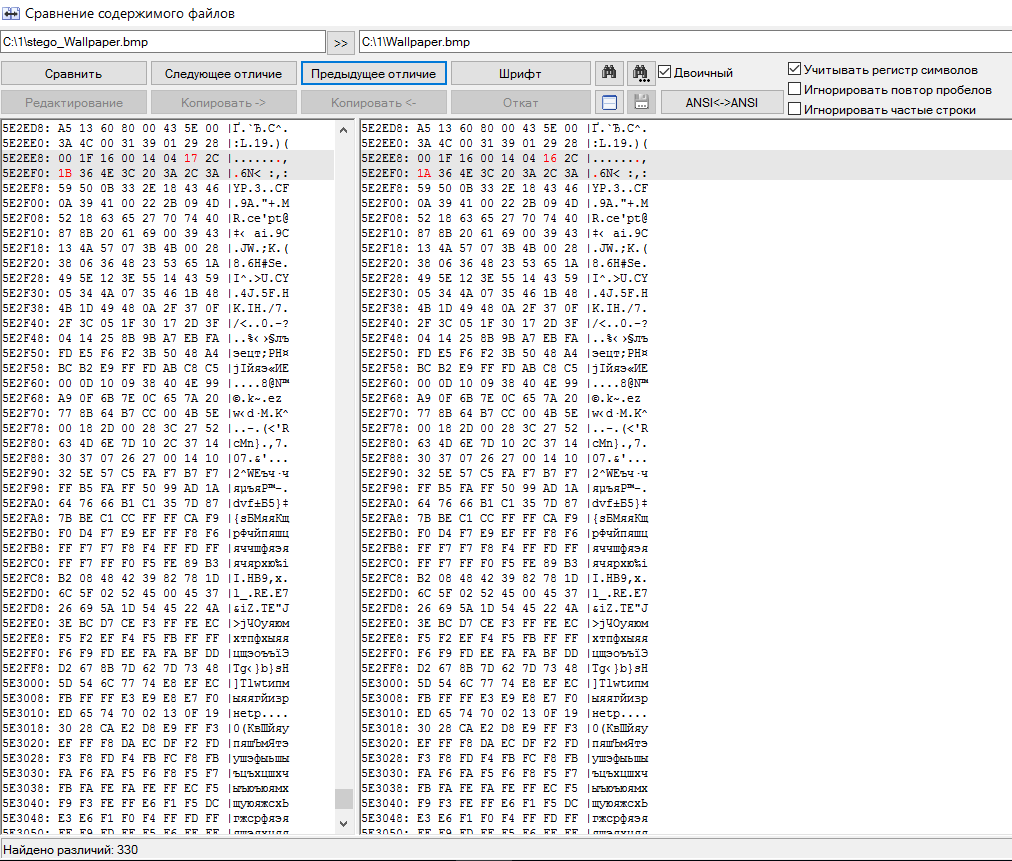
Correct LSB
The program itself tries to compress the hidden file as much as possible before placing it in the container. Therefore, it is always extracted in ZIP format, and the hidden file is already inside this archive. Password protection must be deactivated before unpacking manually — jHide itself will not show whether it is necessary to enter it. This is also a plus, since it eliminates the possibility of using a utility to check images for hidden files.
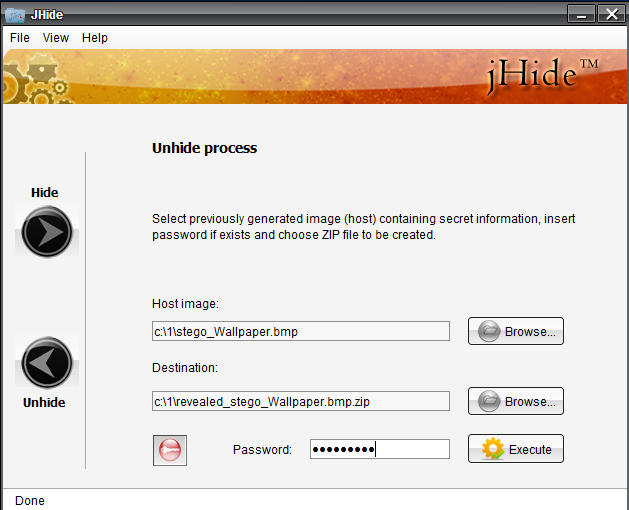
Unpacking a container in jHide
The utility sometimes ignores the entered file name and extracts it with the template name stego_%name%.bmp, however, this flaw can be forgiven. The contents of the file are read to it without distortion.
OpenPuff
OpenPuff team - Download.com
The most complex utility in this review is OpenPuff. Its latest version (4.00) supports not only hiding some files inside others, but also working with steg tags of any format. You can even allocate several processor cores to it if you have a large amount of work to do.
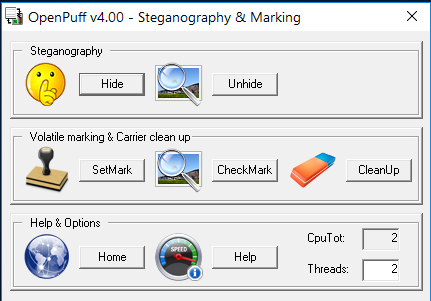
Main OpenPuff window
Unlike other utilities that support password protection of a hidden message, OpenPuff can use a cryptographically secure pseudorandom number generator (CSPRNG) for encryption. If a simple password is not enough, check the boxes next to fields B and C, and then enter three different passwords with a length of 8 to 32 characters. Based on them, CSPRNG will generate a unique key that will be used to encrypt the message.
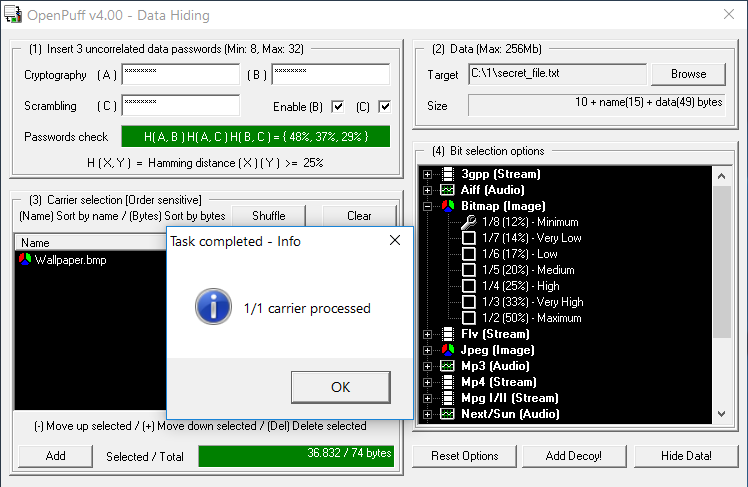
Using CSPRNG
Small files can be stored in pictures and audio recordings, while large ones (for example, cryptographic containers) can be hidden in video recordings. OpenPuff supports MP4, MPG, VOB, and many other formats. The maximum size of the hidden file is 256 MB.
OpenPuff output
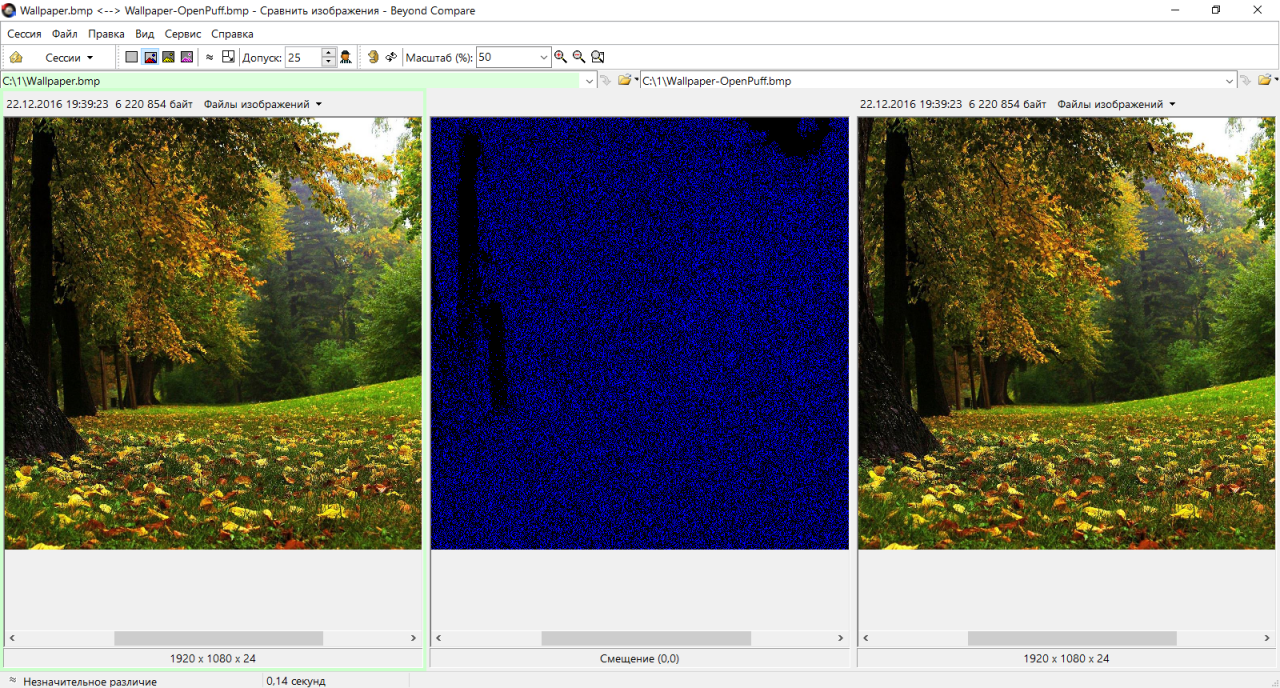
Using CSPRNG on small files greatly increases the total size of the steg message. Therefore, the difference between an empty and a filled container becomes too obvious. Again, we can see that the changed pixels are mostly evenly distributed, but they form large blocks in the lightest and darkest areas. If there were no such blocks, the result would be more like artifacts obtained during JPEG compression.
Byte-by-byte comparison also gives a very characteristic picture. Despite the small size of the hidden file, most pixels in the container have changed their values. If jHide had 330 bytes to write a steg message, then OpenPuff used more than 170 KB for the same task.
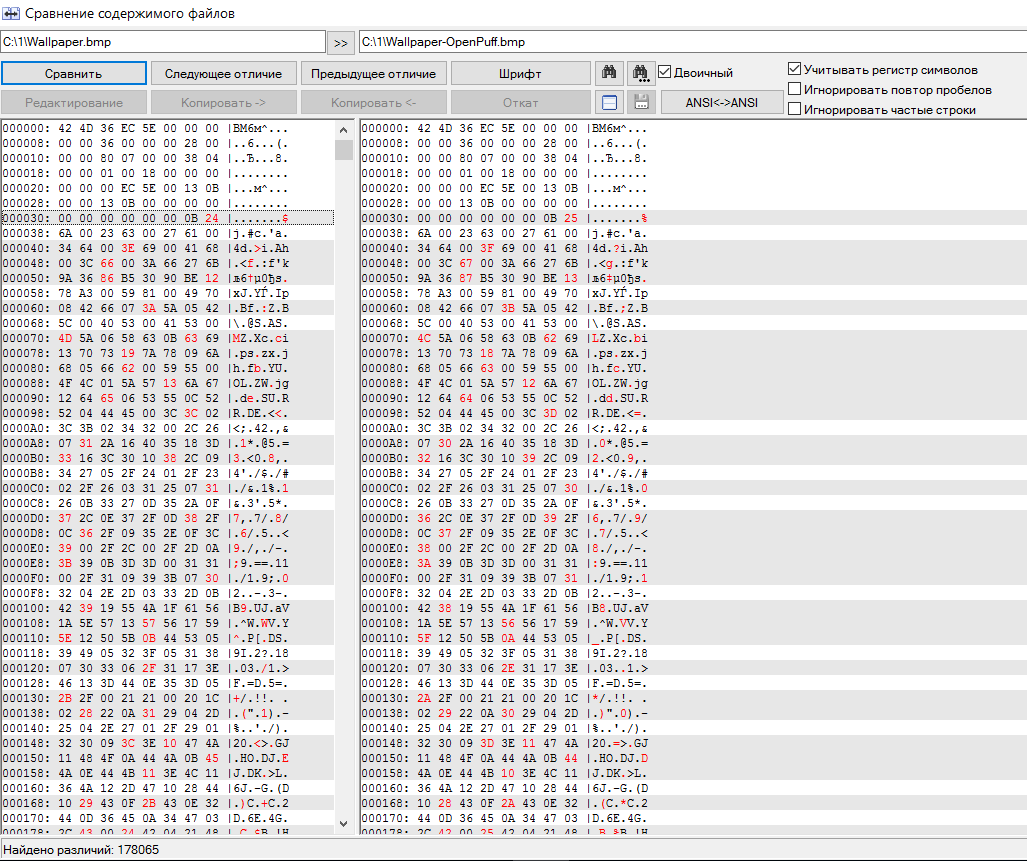
Most pixels were affected by the changes
On the one hand, this is a plus: there is no direct correlation between the message size and the number of pixels changed. The analysis of such a container becomes significantly more complicated. On the other hand, creating a container requires additional effort, which may alienate an unsophisticated user.
Another mode of operation of the program is to write and read steg tags. These are hidden strings up to 32 characters long that can be used for copyright protection. For example, hide the copyright in a photo, music file, or document.
This function works extremely simply. You write an arbitrary steg tag at the top of the window and specify the files to add it to below. The source files will remain intact, and their tagged copies will be saved in the folder you specified.
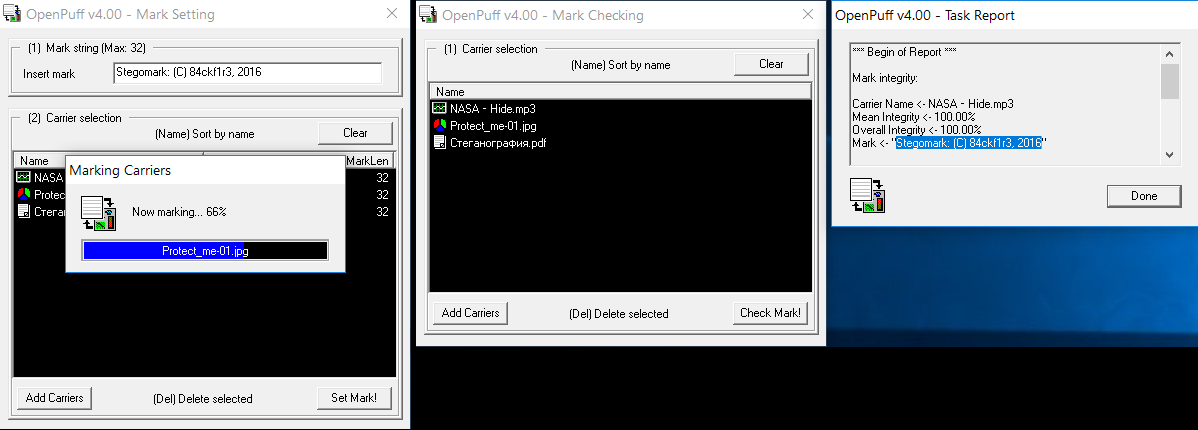
Working with steg tags in OpenPuff
If any legal disputes arise, simply launch OpenPuff and show the previously implemented tag to the surprised opponent.
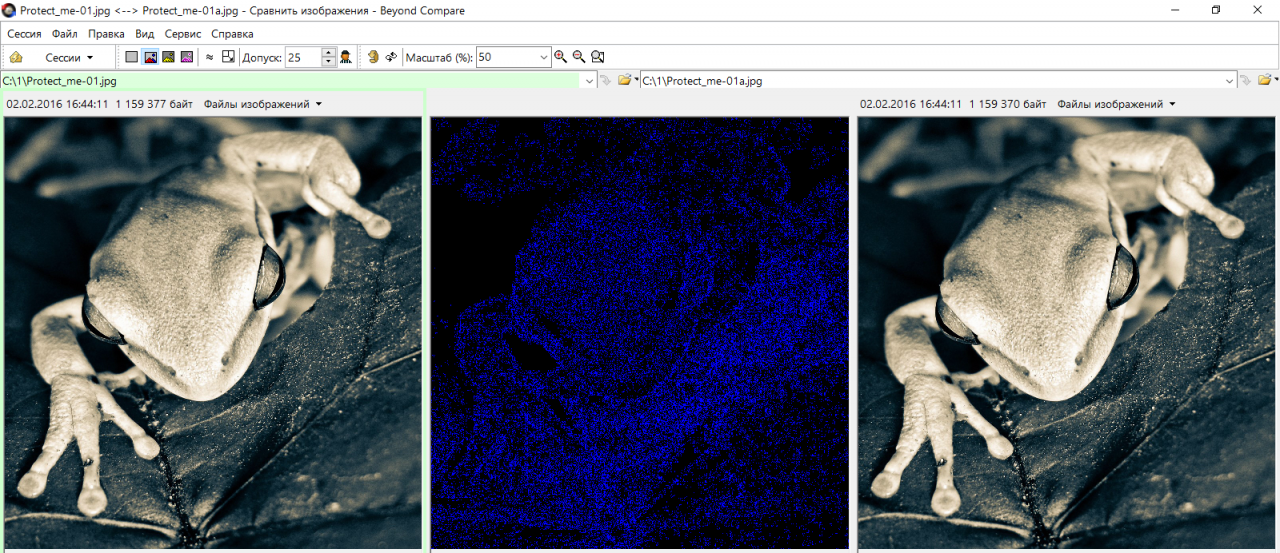
Even a frog can tell who took its picture
Difficulties arise if the file has been modified. Even a simple conversion to another format erases the tag. It can't be read even if the file was converted back to its original format. There are persistent steg tags, but only individual programs can implement them. As a rule, they are linked to a specific piece of equipment (for example, a camera model).
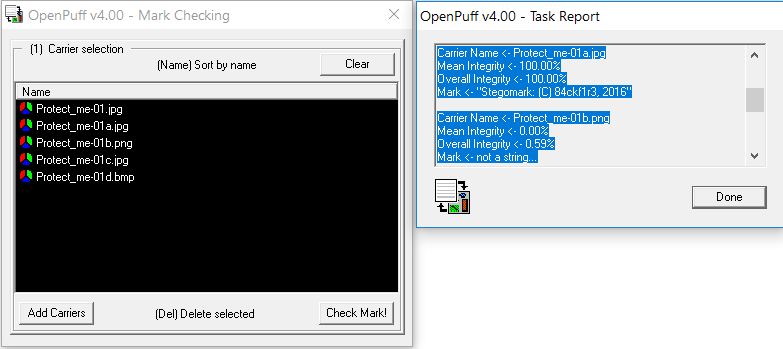
Steg tags disappeared after converting the file
OpenStego
OpenStego
The latest version of OpenStego (0.61) was released in 2014. The program works on Windows and Linux. It supports BMP, PNG, JPG, GIF and WBMP. The filled container is always saved in PNG format.
OpenStego takes up only 203 Kbyte's, but after getting to know Hallucinate, this is no longer impressive. Formally, the utility requires installation, although it can easily be turned into a portable version. OpenStego is attractive because it supports password protection and also knows how to implement steg tags (although this feature still has the "beta" status).
OpenStego Interface
After adding a small text file to the selected image, there are virtually no visual differences between an empty and a filled container.
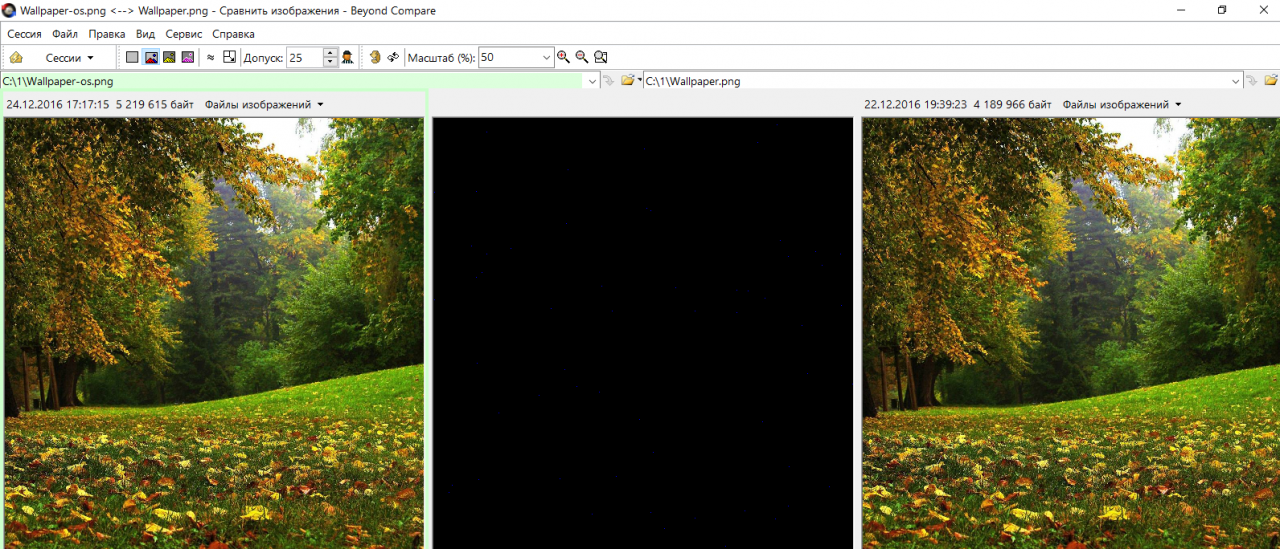
Find ten differences
However, the file size increased by one megabyte, and due to the conversion to PNG with a different compression ratio, it became just a different file. In a byte-by-byte comparison with the original, the differences will be in all values immediately after the header.
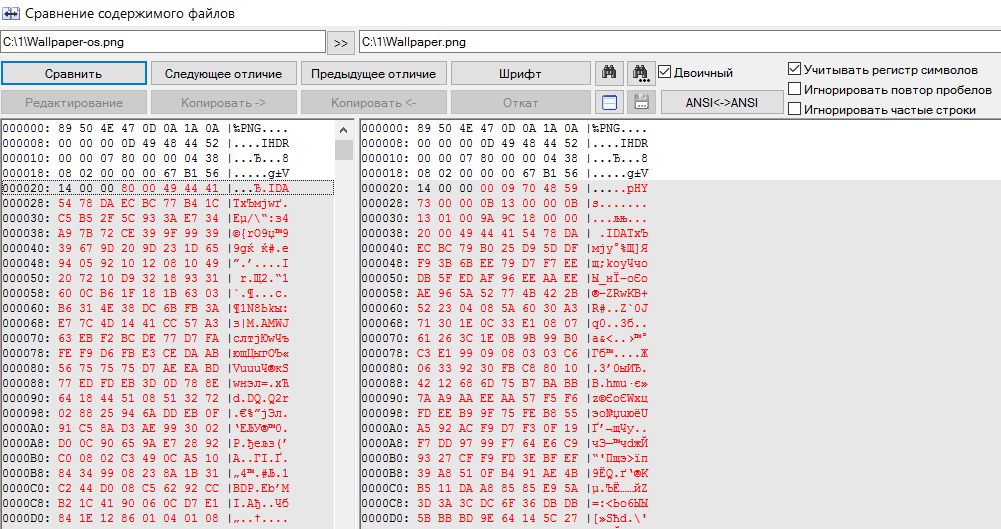
OpenStego: hex comparison
Interestingly, the program does not check the correctness of the entered password when retrieving a steg message from the container. It honestly tries to build the extracted file in any case and always reports that the operation was successful. In reality, the hidden file will be extracted only after entering the correct password. Otherwise, an error will occur and the file will not be written. This approach slightly complicates the use of classic password brute-force methods, in which the next combination is substituted after the previous one failed to check.
The implementation of steg tags in this program is not like in others. First, a signature is generated and stored in a separate file with the SIG extension. You can't write any meaningful information in it - it's just a unique bit set, like a private key.
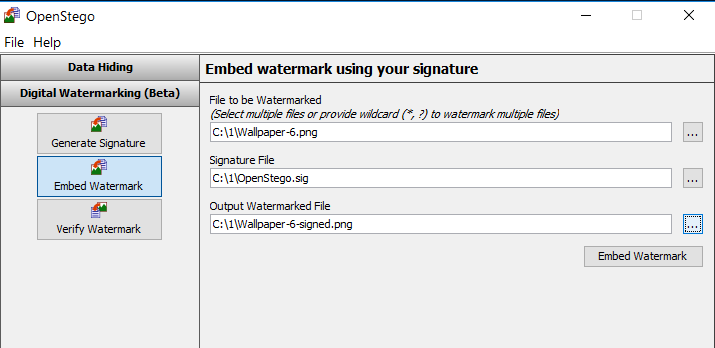
Creating a "watermark"
After embedding the steg tag, a new and visually identical image file is created, in which it "dissolves". The verification process is reduced to checking for the presence of the specified signature inside the file. If it is completely preserved, then the match will be one hundred percent. If the file was modified, the stegemark may be partially lost. The method was conceived as an attempt to implement persistent watermarks, but it is practically useless in the current implementation.
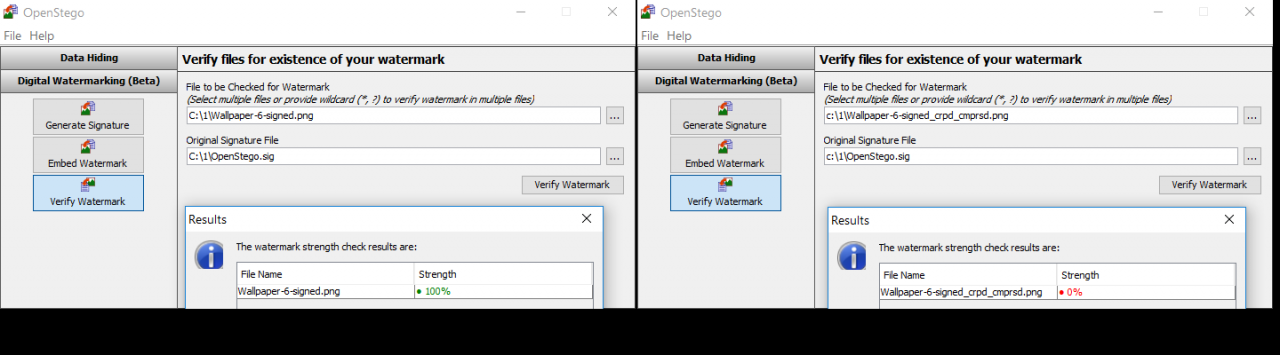
Watermarks evaporate after a little processing
RARJPEG
You can hide some files inside others without any steganographic utilities. Of course, this will not be a neat "dissolution" using the LSB algorithm, but a simple merge, but this method, known in narrow circles, also has its advantages. First, it is available without additional tools. Secondly, it allows you to easily transfer any file by uploading it as a graphic to some site (for example, image hosting or, more often, an imageboard).
The point of this method is that image files (in particular, JPEGs) start being interpreted immediately from the title, while archives are read only from the beginning of the archive label. The label itself can be located anywhere inside the file, since, in addition to regular archives, there are multi-volume and self-extracting ones.
As an experiment, we will pack all the programs from today's review into a ZIP archive and add this archive to the file Wallpaper.jpg by creating a new image: Wallpaper-x.jpg. Just launch the Windows console and write:
type Wallpaper.jpg Steg.zip > wallpaper-x.jpg
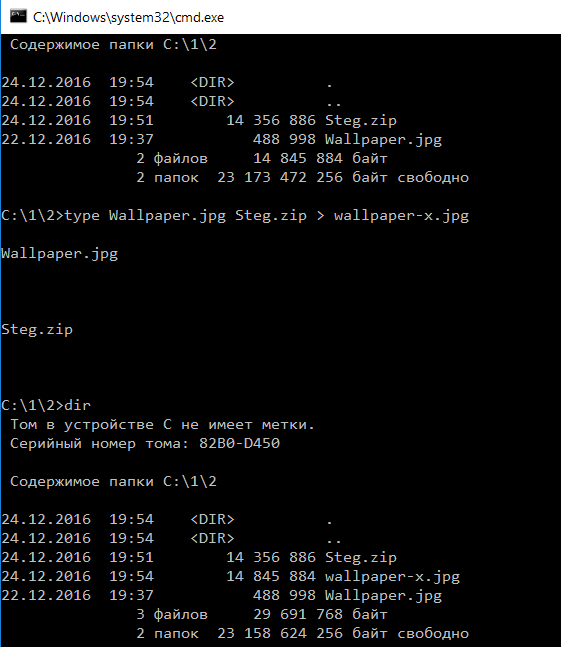
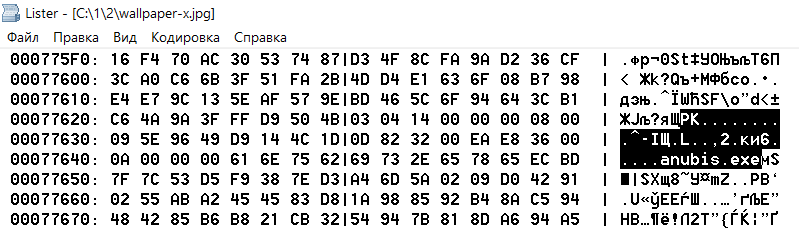
Adding ZIP to JPG
The output is a combined file wallpaper-x.jpg. You can view it as an image or open it with any archiver that supports the ZIP format. If you change the file extension to ZIP, the file manager opens it as a directory. You can even do without renaming, and immediately use the archive plugin via the quick unpack command (for example, {ALT}+{F9} in Total Commander). All files from this "picture" will be extracted without any problems.
This trick has been known for a long time and also works with some other file formats (both graphic and archive), but the most popular combination is RAR + JPEG.
Pics: cryptoworld.su

From the Pharaohs to the present day
If we assume that history develops in a spiral, then modern life seems to have entered the same spiral as Ancient Egypt. People are once again worshiping cats and keeping their images everywhere. At the same time, the cult of secret knowledge is being revived - some hide information, others look for ways to get it. So the ideal way to hide sensitive data is to mix it with trivial content like cat photos.
According to one version, cryptography originated in Ancient Egypt. Her daughter-steganography, or" secret writing", appeared closer to the heyday of the Roman Empire. Some techniques of secret writing were practiced even before our era, but steganography was formed into an independent applied discipline only by the XVI century.

Modern steganography - digital and computer. The latter can be divided into three major areas. The first is actually cryptography, or methods of hiding some files (which are usually called a message) inside others ("container"). After filling in the message, the container changes outwardly imperceptibly and completely retains its functionality.
The second direction studies methods for adding hidden or steg marks to a message. These labels are invisible without special processing and are identical for all files of the same person or device. For example, such steg marks are recorded in digital photos in order to prove their authorship. Crackers sometimes leave steg marks in their license keys. They are protected at the level of the generation algorithm, and therefore they are saved when you try to change the keygen interface and pass it off as your own.
The third direction is the introduction of digital fingerprints in the message. Unlike steg tags, these hidden signs are unique for each message. They serve mainly to protect the interests of copyright holders, allowing you to track the distribution of content. For example, many online stores introduce digital prints in books and music tracks sold. They encode information about the date of sale and the buyer's account (name, IP address, etc.).

Does your favorite online service use steg tags? This is easy to check. It is enough to buy two copies of the same work from different accounts and make a byte-by-byte comparison of files. The difference between them will show hidden placemarks. If the files downloaded are identical (and their hashes completely match), then there are no steg tags inside.
Many books and articles have been written about each of these areas, but there is still no single terminology. Some authors divide the listed branches into dozens of smaller ones, while others do not see a fundamental difference between the large ones. For some, there is a fine line between hidden storage and hidden data transfer, while for others, these are just specifics.
We will not go into the controversy, it is much more interesting to try steganography in practice. First, let's take a closer look at its main application - data hiding. Of the fifty utilities for masking some files inside others, we selected only seven. The review includes only those that are guaranteed to work in Windows 10.
For the test, we will take a picture with a desktop wallpaper. Behind this vegetation, you can fit a lot of interesting things.

Anubis
Anubis - Browse Files at SourceForge.net
Anubis is a superhero of the ancient Egyptians. The Jackal Man, after whom the free program was named six thousand years later. Its first and, unfortunately, last version was written in 2014 in Java. Therefore, the utility turned out to be cross-platform, but requires the installation of a JRE, as well as (in the case of Windows 10) a DOS virtual machine - NTVDM.

Bring Anubis Java!
The main window of the program looks as austere as possible. Click Encrypt and in the opening tab specify the necessary actions: which file to put inside which one and where to save the result. Only hiding text files inside BMP images is guaranteed to work. Several of these are already available in Windows 10 - these are user icons. It would be interesting to hide a list of passwords or some other confidential information in user. bmp. It has long been noticed that the best caches are in a prominent place.

Hiding TXT in BMP
In addition, you can protect the received file with a PIN code - then you will need it for reverse conversion. The utility does not correctly process a string indicating the location of the resulting file. It can be saved at a level higher than the specified one, or even in the source directory.

Comparing an empty and filled container
As can be seen from a byte-by-byte comparison of the source BMP file with the hidden text, the program works very primitively. It simply appends data to the end of the file. The data is encrypted, but provided with characteristic pointers: limiter1, limiter2, inserted length begins. By simply searching for files containing such strings, you can easily find all the steg containers. This utility can be used as an illustration of the simplest method of steganography, but it is completely unsuitable for serious tasks.
DeEgger Embedder
DeEgger Embedder Download
DeEgger Embedder is another small steganography program. It has already implemented a larger set of functions, but its use requires installation .NET Framework 3.5. In addition to the rarely used BMP images today, the program supports PNG, JPG, AVI video files and MP3 music as containers. The utility keeps a detailed log of its actions, which is displayed directly in the main window.

Making Easter eggs!
The algorithm launch button is called Combine, not Encrypt, which more accurately reflects the file injection process. Hidden files (stegs messages) are extracted from multimedia containers by pressing the single Extract button. There is no PIN code protection here.

Combine and extract
But the program can process several files at once. You can put multiple messages in one container or one in different containers.

Writing multiple files to a single container
After processing in DeEgger, image comparison utilities consider the source and destination BMP files to be identical. In reality, it is an empty and filled container in the terminology of steganography.

Imaginary identity
Let's make a byte-by-byte comparison. Does it look familiar? Just like Anubis, the DeEgger Embedder utility added a steg message to the end of the container file. The user. bmp image has a lot of monochrome areas, so this appendix looks especially noticeable.

The same Easter eggs, view in the code
At first glance, there are no explicit pointers that can be used to search for files containing a specific string. However, let's take a closer look. To do this, we will create another container with a different message and compare the two already filled containers with each other.

Finding the embedded file pointer
Here is the same section in hexadecimal: 24 23 26 29 2A 40 26 28 23 5E 2A 00 D1 8B 87 8B FF.
As you can see, despite supporting a larger number of formats, DeEgger is not far behind Anubis. Hidden files are also written to the end of the container file and have a distinctive appearance that makes them easy to detect.
DeepSound
DeepSound -> Overview | jpinsoft.net
The latest version of this program was released in November 2015. Unlike the previous utilities in this review, it hides data inside audio files. DeepSound can use WAV (uncompressed only, PCM), as well as MP3, CDA, WMA, APE, and FLAC as containers. DeepSound can embed files of any type and automatically calculates the available space for them depending on the container size and audio quality settings.
When using MP3, the available space for the steg message is shown larger than the container itself, but this is an illusion. Regardless of the original file format, the new container is created in only one of the uncompressed formats: WAV, APE, or FLAC. So the size of the original container doesn't matter. As a result, the message will occupy a certain percentage of the volume of the new (uncompressed) audio file.

Large volume for any files
The program can simply put any file inside the folder, or pre-encrypt it using the AES algorithm with a key length of 256 bits. It was experimentally determined that the maximum password length is only 32 characters. My normal passwords were longer and resulted in an unhandled exception.

AES Encryption
You can put any number of files in one container until the free space counter is full. Its number depends on the degree of quality (i.e., the distortion introduced in the audio file). There are three settings available in total: high, normal, and low quality. Each of them increases the useful volume of the container twice. However, I recommend not to be greedy and always use the maximum quality - this will make it harder to detect a hidden file.
A stego message is retrieved after selecting the appropriate container manually. If encryption was used, then without entering the password, the program will not even show the name of the hidden file. Cyrillic characters are not supported in file names. When extracted, they are replaced with XXXX, but the contents of the file are not affected in any way.
DeepSound can convert MP3 and CDA, so we can easily convert the source file from MP3 to WAV and compare two containers: empty and filled.

PDF is smeared inside WAV
Here we are waiting for a pleasant surprise: the file sizes are identical, and their contents differ immediately after the header. Bytes differ almost everywhere by one, and by small values. Most likely, this is an implementation of the LSB (Least Significant Bit) algorithm. Its essence is that the hidden file is encoded as changes in the low-order bits in individual bytes of the container. This leads to small distortions (changes in the pixel hue in BMP and the sound frequency in WAV), which a person usually does not perceive.
DeepSound is already quite suitable for hiding important information (except for state secrets, of course). You can also use built-in encryption, but no one knows how well it is implemented, because the program did not have an open audit. Therefore, it is more reliable to first place secret files in some reliable cryptographic container (for example, TrueCrypt or VeraCrypt), and then hide it inside the audio file.
Hallucinate
http://sourceforge.net/projects/hallucinate/
The latest version of Hallucinate (v. 1.2) was released in November 2015. This compact (only 34 KB) utility is written in Java and does not require installation. As a container, it supports BMP and PNG formats, which makes it much more convenient than Anubis. PNG images are much more commonly used today than BMP images. There are plenty of them even in temporary browser directories, so such a container will definitely not be a lone and very noticeable file on disk.

Hallucinations with meaning
The interface of Hallucinate is simple and functional. You need to select a container, specify the file hidden in it and the desired quality level of the final image. There are eight options available. The coarser the original image becomes, the more you can hide in it, but the more visible the artifacts become. Let's choose the best quality in the settings and illustrate this difference by repeating the operation with the BMP file.

See the differences? And they are!
Visually, the images on the left and right do not differ. However, the Beyond Compare program shows the difference between them in the center frame. The text file is encoded as changes in the brightness of individual pixels that are evenly distributed throughout the frame. Only in the darkest and lightest areas they pile up tightly.
When comparing files byte-by-byte, the same difference in hexadecimal format looks familiar: the same LSB algorithm as DeepSound. A graphic file or an audio file - it doesn't matter in this case. In both formats, minimal distortion is introduced, which is indistinguishable without special comparison methods. It is quite difficult to detect them without the source file (with only the container on hand). It does not contain any explicit pointers to the implementation of a steg message.
The hidden file is extracted in just two clicks. Just select a container (HAL-file in the terminology of the program author), click Decode and specify a place to save the file.

Undressing the matryoshka doll
JHide
JHide
JHide (not to be confused with jihad) is another similar Java program. You can't call it compact, it takes up almost three megabytes. However, unlike Hallucinate, in addition to BMP and PNG, it supports TIFF, and also allows you to use password protection.

jHide Interface
Comparison with the Beyond Compare utility shows subtle differences. In the first second, they are not visible at all. You need to turn up the brightness and look closely to see evenly scattered dark blue dots on a black background.

jHide output
A comparison in hex codes shows the same LSB algorithm, but its implementation here is more successful. Modified pixels are not grouped in large blocks from the beginning of the file, but are evenly distributed throughout the container. This makes it much harder to detect a hidden message in an image. If the steg message size is small, this is almost impossible to do without having the original (empty container) to compare.

Correct LSB
The program itself tries to compress the hidden file as much as possible before placing it in the container. Therefore, it is always extracted in ZIP format, and the hidden file is already inside this archive. Password protection must be deactivated before unpacking manually — jHide itself will not show whether it is necessary to enter it. This is also a plus, since it eliminates the possibility of using a utility to check images for hidden files.

Unpacking a container in jHide
The utility sometimes ignores the entered file name and extracts it with the template name stego_%name%.bmp, however, this flaw can be forgiven. The contents of the file are read to it without distortion.
OpenPuff
OpenPuff team - Download.com
The most complex utility in this review is OpenPuff. Its latest version (4.00) supports not only hiding some files inside others, but also working with steg tags of any format. You can even allocate several processor cores to it if you have a large amount of work to do.

Main OpenPuff window
Unlike other utilities that support password protection of a hidden message, OpenPuff can use a cryptographically secure pseudorandom number generator (CSPRNG) for encryption. If a simple password is not enough, check the boxes next to fields B and C, and then enter three different passwords with a length of 8 to 32 characters. Based on them, CSPRNG will generate a unique key that will be used to encrypt the message.

Using CSPRNG
Small files can be stored in pictures and audio recordings, while large ones (for example, cryptographic containers) can be hidden in video recordings. OpenPuff supports MP4, MPG, VOB, and many other formats. The maximum size of the hidden file is 256 MB.

OpenPuff output
Using CSPRNG on small files greatly increases the total size of the steg message. Therefore, the difference between an empty and a filled container becomes too obvious. Again, we can see that the changed pixels are mostly evenly distributed, but they form large blocks in the lightest and darkest areas. If there were no such blocks, the result would be more like artifacts obtained during JPEG compression.
Byte-by-byte comparison also gives a very characteristic picture. Despite the small size of the hidden file, most pixels in the container have changed their values. If jHide had 330 bytes to write a steg message, then OpenPuff used more than 170 KB for the same task.

Most pixels were affected by the changes
On the one hand, this is a plus: there is no direct correlation between the message size and the number of pixels changed. The analysis of such a container becomes significantly more complicated. On the other hand, creating a container requires additional effort, which may alienate an unsophisticated user.
Another mode of operation of the program is to write and read steg tags. These are hidden strings up to 32 characters long that can be used for copyright protection. For example, hide the copyright in a photo, music file, or document.
This function works extremely simply. You write an arbitrary steg tag at the top of the window and specify the files to add it to below. The source files will remain intact, and their tagged copies will be saved in the folder you specified.

Working with steg tags in OpenPuff
If any legal disputes arise, simply launch OpenPuff and show the previously implemented tag to the surprised opponent.

Even a frog can tell who took its picture
Difficulties arise if the file has been modified. Even a simple conversion to another format erases the tag. It can't be read even if the file was converted back to its original format. There are persistent steg tags, but only individual programs can implement them. As a rule, they are linked to a specific piece of equipment (for example, a camera model).

Steg tags disappeared after converting the file
OpenStego
OpenStego
The latest version of OpenStego (0.61) was released in 2014. The program works on Windows and Linux. It supports BMP, PNG, JPG, GIF and WBMP. The filled container is always saved in PNG format.
OpenStego takes up only 203 Kbyte's, but after getting to know Hallucinate, this is no longer impressive. Formally, the utility requires installation, although it can easily be turned into a portable version. OpenStego is attractive because it supports password protection and also knows how to implement steg tags (although this feature still has the "beta" status).

OpenStego Interface
After adding a small text file to the selected image, there are virtually no visual differences between an empty and a filled container.

Find ten differences
However, the file size increased by one megabyte, and due to the conversion to PNG with a different compression ratio, it became just a different file. In a byte-by-byte comparison with the original, the differences will be in all values immediately after the header.

OpenStego: hex comparison
Interestingly, the program does not check the correctness of the entered password when retrieving a steg message from the container. It honestly tries to build the extracted file in any case and always reports that the operation was successful. In reality, the hidden file will be extracted only after entering the correct password. Otherwise, an error will occur and the file will not be written. This approach slightly complicates the use of classic password brute-force methods, in which the next combination is substituted after the previous one failed to check.
The implementation of steg tags in this program is not like in others. First, a signature is generated and stored in a separate file with the SIG extension. You can't write any meaningful information in it - it's just a unique bit set, like a private key.

Creating a "watermark"
After embedding the steg tag, a new and visually identical image file is created, in which it "dissolves". The verification process is reduced to checking for the presence of the specified signature inside the file. If it is completely preserved, then the match will be one hundred percent. If the file was modified, the stegemark may be partially lost. The method was conceived as an attempt to implement persistent watermarks, but it is practically useless in the current implementation.

Watermarks evaporate after a little processing
RARJPEG
You can hide some files inside others without any steganographic utilities. Of course, this will not be a neat "dissolution" using the LSB algorithm, but a simple merge, but this method, known in narrow circles, also has its advantages. First, it is available without additional tools. Secondly, it allows you to easily transfer any file by uploading it as a graphic to some site (for example, image hosting or, more often, an imageboard).
The point of this method is that image files (in particular, JPEGs) start being interpreted immediately from the title, while archives are read only from the beginning of the archive label. The label itself can be located anywhere inside the file, since, in addition to regular archives, there are multi-volume and self-extracting ones.
As an experiment, we will pack all the programs from today's review into a ZIP archive and add this archive to the file Wallpaper.jpg by creating a new image: Wallpaper-x.jpg. Just launch the Windows console and write:
type Wallpaper.jpg Steg.zip > wallpaper-x.jpg

Adding ZIP to JPG
The output is a combined file wallpaper-x.jpg. You can view it as an image or open it with any archiver that supports the ZIP format. If you change the file extension to ZIP, the file manager opens it as a directory. You can even do without renaming, and immediately use the archive plugin via the quick unpack command (for example, {ALT}+{F9} in Total Commander). All files from this "picture" will be extracted without any problems.
This trick has been known for a long time and also works with some other file formats (both graphic and archive), but the most popular combination is RAR + JPEG.

Pics: cryptoworld.su
