Man
Professional
- Messages
- 3,221
- Reaction score
- 1,189
- Points
- 113
Introduction
Email spoofing is generally the forgery of emails from legitimate senders. In this article, we will look at email address spoofing, which involves forging the From header of the email, i.e. how the sender's name and address appear in the user's email client.The SMTP protocol (Simple Mail Transfer Protocol — the main protocol for transmitting email in TCP/IP networks) does not provide any protection against spoofing, so it is quite easy to forge the sender's address. In fact, all an attacker needs is a tool to choose from whose name the letter will be sent. And this can be a mail client, a special utility or a script, of which there are many on the Internet.
Email address spoofing is used in both fraudulent schemes and targeted attacks on organizations. The goal of this technique is to convince the victim that the email came from a trusted sender and to encourage them to perform the actions specified in it: click on a phishing link, transfer money to a specific account, download a malicious file, etc. To be more convincing, attackers can copy the design and style of emails from a specific sender, emphasize the urgency of the task, and use other social engineering techniques.
In some cases, the fake emails are part of a multi-stage attack, and the first stage does not require any suspicious actions from the victim. Examples of such attacks can be found in our article on corporate doxxing.
Legitimate Domain Spoofing
The simplest form of email address spoofing is legitimate domain spoofing. It involves substituting the real domain of the organization that the attacker is masquerading as in the From header. In this case, it is extremely difficult for the user to distinguish a fake letter from a real one.To combat spoofing, several email authentication methods have been created that improve and complement each other: SPF, DKIM, and DMARC . These mechanisms confirm in one way or another that the email was actually sent from the stated address.
- The SPF (Sender Policy Framework) standard allows the owner of a mail domain to limit the set of IP addresses that can send emails from this domain, and the mail server to check that the sender's IP address is authorized by the domain owner. However, SPF does not check the From header, but the sender's domain specified in the SMTP envelope, which is used to transmit information about the email route between the mail client and the server and is not shown to the recipient.
- DKIM solves the problem of sender authentication using a digital signature that is generated based on a private key stored on the sender's server. The public key for verifying the signature is placed on the DNS server responsible for the sender's domain. If the email was actually sent from another domain, the signature will be invalid. However, this technology also has a weak point: an attacker can send a fake email without a DKIM signature, and it will be impossible to verify it.
- DMARC (Domain-basedMessageAuthentication, Reporting and Conformance) allows you to check the domain in the From header against the domain verified using DKIM and/or SPF. Thus, when using DMARC, a letter spoofing a legitimate domain will not pass the check. However, when choosing a strict policy, DMARC can block useful letters as well — in one of our articles, we talked about how our solutions improve this technology and minimize false positives.
Naturally, with the widespread introduction of the technologies described above, attackers are faced with a difficult choice: rely on the fact that the company they are masquerading as does not have mail authentication configured or configured with errors (and, unfortunately, there are still some), or use methods for forging the From header that bypass authentication.
Display Name Spoofing
The display name is the sender's name, which appears in the From header before their address. In the case of corporate email, the sender's name is usually the person's real name, department name, etc.
Display name example
Many email clients hide the sender's address for the recipient's convenience and show only the display name in the letter. This is actively used by attackers, who forge the name but leave their real address in the From header. This address is often even protected by a DKIM signature and SPF, so authentication mechanisms allow the message to pass as legitimate.
Ghost Spoofing
The most popular and common type of display name spoofing is Ghost Spoofing. The idea is that the attacker specifies as a name not only the name of the person or company they are masquerading as, but also the address of the supposed sender, as in the example in the screenshot below.
Ghost Spoofing Example
However, in reality the letter comes from a completely different address.

Real Sender Address in Ghost Spoofing and Email Authentication
AD Spoofing
AD (Active Directory) Spoofing is also a type of display name spoofing, but unlike the Ghost Spoofing technique, it does not involve specifying a fake address as part of the name. In this case, the address of the attackers from which such letters are sent uses the name of the person on whose behalf they are sent.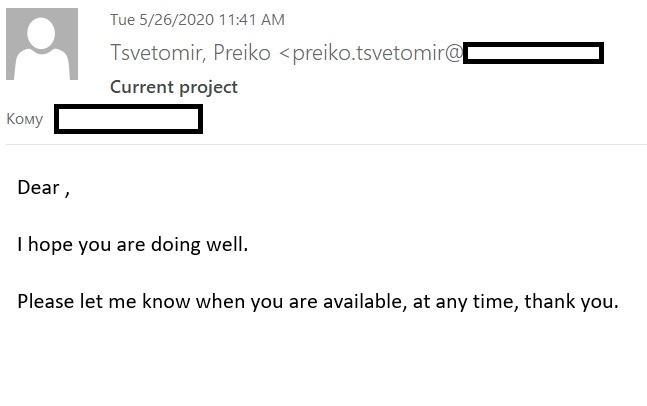
AD Spoofing Example
This method looks more primitive compared to Ghost Spoofing, but scammers may prefer it for several reasons. First, if the recipient's mail agent does display the contents of the From header in full, then the double sender address will arouse more suspicion in the user than the address on a public domain. Second, Ghost Spoofing is technically easier to block with spam filters: it is enough to simply send letters to spam where the sender's displayed name contains the email address. As a rule, it is not possible to block all incoming letters from namesakes of all colleagues and contractors.
Lookalike domain Spoofing
In more complex attacks, attackers use specially registered domains that are similar to the domain of the target organization. This requires a little more effort: after all, finding and buying a specific domain, setting up mail, DKIM and SPF signatures, and DMARC authentication on it is more difficult than simply changing the From header a little. But it is also more difficult to recognize a fake in this case.Primary Lookalike
Lookalike domains are domains that are similar in spelling to the domains of the organization being forged, but differ from them by one or more letters. We talked about them in more detail in the article "Lookalike domains and protection against them"). For example, the letter in the screenshot below came from the domain deutschepots.de, which is very easy to confuse with the domain of the German postal company Deutsche Post (deutschepost.de). If you follow the link in such a letter and try to pay for the delivery of the parcel, you can not only lose 3 euros, but also leave your card details with the scammers.
Example of a letter from a lookalike domain
However, with the proper level of attentiveness, such an error can be noticed. But there are also cases when simple attentiveness is no longer enough.
Unicode Spoofing
Unicode Spoofing is a type of spoofing in which one of the ASCII characters in a domain name is replaced with a similarly written character from the Unicode range. To understand this technique, you need to understand how domains that use non-Latin characters (for example, Cyrillic or umlauts) are encoded. To work with them, the Punycode conversion method was created , according to which Unicode characters are mapped to so-called ACE sequences (ASCII Compatible Encoding - encoding compatible with ASCII), consisting of Latin letters, hyphens and numbers from 0 to 9. At the same time, many browsers and email clients display the Unicode version of the domain.However, in the browser you will most likely see "kaspersky.rf". At the same time, since this technology provides for partial encoding (not the entire line is encoded, but a separate symbol), the domain can contain both ASCII and Unicode symbols, and attackers actively use this.

Example of a letter with Unicode spoofing
In the screenshot above, we see a message that is supposedly sent from the apple.com domain. The spelling is completely identical, the letter has passed mail authentication. The design of the letter is surprising, but the average user rarely receives messages about blocking, so there is nothing to compare it with. If an unsuspecting user clicks on the link, he gets to a fake site and leaves his account details there.
If you look at the headers of this letter (this can be done in most PC email clients), a completely different picture will open up:

Punycode domain record
The thing is that the domain apple.com falls under the rule of encoding Unicode symbols in ASCII - the first three symbols are Cyrillic "a" and "p". But the mail agent that opened the letter, for the convenience of the user, converted the Punycode combination to Unicode and the letter displayed "apple.com".
Note that some email clients warn the user that the domain name contains non-standard characters, or even display Punycode in the From header. However, such protection mechanisms are not provided everywhere, and this plays into the hands of scammers.
Conclusion
There are different ways to convince the recipient of a letter that it came from a trusted sender. Some of them look primitive, but they allow attackers to successfully bypass email authentication. At the same time, spoofing as a technique is used to implement a variety of attacks, from regular phishing to advanced BEC attacks. And they, in turn, can be one of the stages of more complex targeted attacks. Accordingly, the damage from spoofing, even within the framework of a single attack, can vary from theft of personal data to suspension of work, loss of reputation and multi-million dollar losses.There are also a variety of ways to protect against spoofing, from simple but not very reliable attentiveness to special components in business solutions. Kaspersky Lab has included the necessary module in solutions for mail servers on Microsoft Exchange, Linux and in virtual environments, as well as a separate product for Microsoft Office 365.

