Man
Professional
- Messages
- 3,225
- Reaction score
- 1,053
- Points
- 113
Hackers have learned how to "blind" protection systems with just one tool.
Trend Micro found that in a number of attacks, attackers used the EDRSilencer tool to disable EDR system alerts. Cybercriminals integrate the tool into their attacks to hide the traces of attacks and evade detection.
EDRSilencer is an open-source tool developed by analogy with MdSec's commercial NightHawk FireBlock solution. The program detects active EDR processes and uses the Windows Filtering Platform (WFP) to monitor and block network traffic using the IPv4 and IPv6 protocols. WFP, which is used in firewalls and antiviruses, allows you to configure strong filters that are used to monitor traffic.
EDRSilencer applies filters to block EDR communication with the management server. During testing, it was possible to block the sending of data, and the devices appeared to be inactive in the management portal. As a result, notifications and detailed telemetry are blocked.
In the new version of the tool, you can block 16 modern EDR solutions, including:
Experiments have also shown that some EDR products continue to transmit reports due to the absence of some executable files in the hardcoded list. However, attackers can add filters for the desired processes, expanding the list of blocked components.
However, after additional processes are added to the block list, EDR tools stop sending logs. This shutdown allows malicious activity to go undetected, increasing the chances of successful attacks without the intervention of specialists.
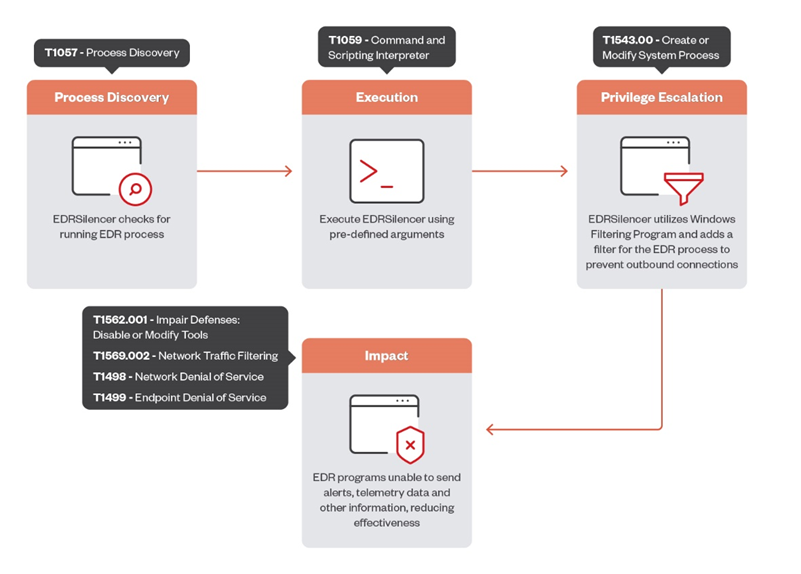
EDRSilencer diagram (source: Trend Micro)
Trend Micro recommends classifying EDRSilencer as malware and blocking it in the early stages of an attack. Experts also advise applying multi-layered security measures to isolate critical systems, use solutions with behavioral analysis and anomaly detection, and monitor indicators of compromise on the network. The principle of least privilege is also a key element of protection against such attacks.
Source
Trend Micro found that in a number of attacks, attackers used the EDRSilencer tool to disable EDR system alerts. Cybercriminals integrate the tool into their attacks to hide the traces of attacks and evade detection.
EDRSilencer is an open-source tool developed by analogy with MdSec's commercial NightHawk FireBlock solution. The program detects active EDR processes and uses the Windows Filtering Platform (WFP) to monitor and block network traffic using the IPv4 and IPv6 protocols. WFP, which is used in firewalls and antiviruses, allows you to configure strong filters that are used to monitor traffic.
EDRSilencer applies filters to block EDR communication with the management server. During testing, it was possible to block the sending of data, and the devices appeared to be inactive in the management portal. As a result, notifications and detailed telemetry are blocked.
In the new version of the tool, you can block 16 modern EDR solutions, including:
- Microsoft Defender;
- SentinelOne;
- FortiEDR;
- Palo Alto Networks Cortex XDR;
- Cisco Secure Endpoint;
- ElasticEDR;
- Carbon Black EDR;
- Trend Micro Apex One.
Experiments have also shown that some EDR products continue to transmit reports due to the absence of some executable files in the hardcoded list. However, attackers can add filters for the desired processes, expanding the list of blocked components.
However, after additional processes are added to the block list, EDR tools stop sending logs. This shutdown allows malicious activity to go undetected, increasing the chances of successful attacks without the intervention of specialists.

EDRSilencer diagram (source: Trend Micro)
Trend Micro recommends classifying EDRSilencer as malware and blocking it in the early stages of an attack. Experts also advise applying multi-layered security measures to isolate critical systems, use solutions with behavioral analysis and anomaly detection, and monitor indicators of compromise on the network. The principle of least privilege is also a key element of protection against such attacks.
Source
