Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,096
- Points
- 113
How LiveJournal got a second life thanks to hackers.
At the end of July 2024, Kaspersky Lab recorded a surge in cyber attacks on the computers of government organizations and IT companies in Russia. The attackers used sophisticated phishing techniques, sending malicious files to the victims email addresses under the guise of secure documents. As a result of the attacks, computers were infected with Trojans that were managed through popular cloud services, such as Dropbox.
The campaign is called EastWind. One of the most dangerous tools used in the operation was the CloudSorcerer backdoor, which was updated by hackers after its initial version was revealed in early July. CloudSorcerer now uses LiveJournal and Quora profiles to interact with the command server, which makes detection more difficult.
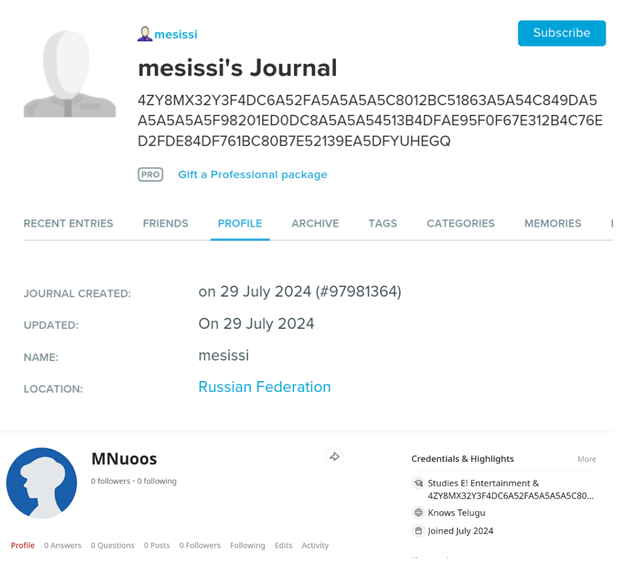
Profiles contain an encrypted authentication token for communicating with the cloud[/CENTER]
A Trojan of the APT31 group called GrewApacha, which has been known since 2021, attracted considerable attention of experts. Malicious software is used to collect information from infected computers and install additional malware.
The new version of GrewApacha includes two management servers, one of which is encrypted using the profile biography on GitHub-it contains a Base64-encoded string that the Trojan reads. GrewApacha decrypts the extracted string and gets the address of the main management server. This new feature makes the attack even more stealthy.
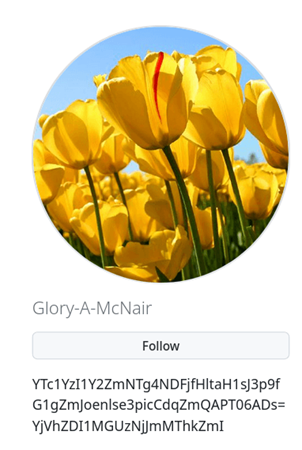
Profile with encoded data
Also, as part of the cyberattack, a new PlugY implant was discovered, which is similar to the tools used by the Chinese-speaking APT27 group. The implant features an extensive set of commands and the ability to communicate with the command center through three different protocols. The code has a lot in common with the DRBControl (Clambling) and PlugX backdoors, which allows us to conclude that there may be cooperation between different APT groups.
The peculiarity of the attack is that cybercriminals used popular Internet services such as GitHub, Dropbox, LiveJournal and Quora to manage infected devices, which made it possible to effectively hide their actions, disguising them as normal network activity.
Recommendations for detecting traces of cyber attacks
Malicious programs involved in attacks vary significantly, so specific indicators of compromise are required to detect them.
Source
At the end of July 2024, Kaspersky Lab recorded a surge in cyber attacks on the computers of government organizations and IT companies in Russia. The attackers used sophisticated phishing techniques, sending malicious files to the victims email addresses under the guise of secure documents. As a result of the attacks, computers were infected with Trojans that were managed through popular cloud services, such as Dropbox.
The campaign is called EastWind. One of the most dangerous tools used in the operation was the CloudSorcerer backdoor, which was updated by hackers after its initial version was revealed in early July. CloudSorcerer now uses LiveJournal and Quora profiles to interact with the command server, which makes detection more difficult.

Profiles contain an encrypted authentication token for communicating with the cloud[/CENTER]
A Trojan of the APT31 group called GrewApacha, which has been known since 2021, attracted considerable attention of experts. Malicious software is used to collect information from infected computers and install additional malware.
The new version of GrewApacha includes two management servers, one of which is encrypted using the profile biography on GitHub-it contains a Base64-encoded string that the Trojan reads. GrewApacha decrypts the extracted string and gets the address of the main management server. This new feature makes the attack even more stealthy.

Profile with encoded data
Also, as part of the cyberattack, a new PlugY implant was discovered, which is similar to the tools used by the Chinese-speaking APT27 group. The implant features an extensive set of commands and the ability to communicate with the command center through three different protocols. The code has a lot in common with the DRBControl (Clambling) and PlugX backdoors, which allows us to conclude that there may be cooperation between different APT groups.
The peculiarity of the attack is that cybercriminals used popular Internet services such as GitHub, Dropbox, LiveJournal and Quora to manage infected devices, which made it possible to effectively hide their actions, disguising them as normal network activity.
Recommendations for detecting traces of cyber attacks
Malicious programs involved in attacks vary significantly, so specific indicators of compromise are required to detect them.
- Backdoor using Dropbox: search for large DLL files (more than 5 MB) in the directory C:\Users\Public and keep track of regular accesses to Dropbox in network traffic.
- GrewApacha Trojan (APT31): can be detected by an unsigned file msedgeupdate.dll several megabytes in size.
- PlugY implant (delivered via CloudSorcerer): monitor the startup process msiexec.exe for each user and creating named channels with a template .\PIPE\Y<number>.
Source

